Policies in Deep Security can include a Context value. Which of the following statements re-garding Context is correct?
A. The Context provides Deep Security Agents with location awareness and are associated with Anti-Malware and Web Reputation Rules.
B. The Context provides Deep Security Agents with location awareness and are associated with Firewall and Intrusion Prevention Rules.
C. The Context provides Deep Security Agents with location awareness and are associated with Web Reputation Rules only.
D. The Context provides Deep Security Agents with location awareness and are associated with Log Inspection and Integrity Monitoring Rules.
Which of the following correctly identifies the order of the steps used by the Web Reputation Protection Module to determine if access to a web site should be allowed?
A. Checks the cache. 2. Checks the Deny list. 3. Checks the Approved list. 4. If not found in any of the above, retrieves the credibility score from Rating Server. 5. Evaluates the credibility score against the Security Level to determine if access to the web site should be allowed.
B. Checks the cache. 2. Checks the Approved list. 3. Checks the Deny list. 4. If not found in any of the above, retrieves the credibility score from the Rating Server. 5. Evaluates the credibility score against the Security Level to determine if access to the web site should be allowed.
C. Checks the Deny list. 2. Checks the Approved list. 3. Checks the cache. 4. If not found in any of the above, retrieves the credibility score from Rating Server. 5. Evaluates the credibility score against the Security Level to determine if access to the web site should be allowed.
D. Checks the Approved list. 2. Checks the Deny list. 3. Checks the cache. 4. If not found in any of the above, retrieves the credibility score from the Rating Server. 5. Evaluates the credibility score against the Security Level to determine if access to the web site should be allowed.
Your organization would like to implement a mechanism to alert administrators when files on a protected servers are modified or tampered with. Which Deep Security Protection Module should you enable to provide this functionality?
A. The Integrity Monitoring Protection Module
B. The File Inspection Protection Module
C. Deep Security can not provide this type of functionality
D. The Intrusion Prevention Protection Module
Which Protection Modules can make use of a locally installed Smart Protection Server?
A. The Anti-Malware and Web Reputation Protection Modules can make use of the locally installed Smart Protection Server.
B. All Protection Modules can make use of the locally installed Smart Protection Server
C. Anti-Malware is the only Protection Modules that can use the locally installed Smart Protection Server.
D. The Anti-Malware, Web Reputation and Intrusion Prevention Protection Modules can make use of the locally installed Smart Protection Server.
Which of the following statements is true regarding Deep Security Manager-todatabase com-munication?
A. Deep Security Manager-to-database traffic is not encrypted by default, but can be enabled by modifying settings in the ssl.properties file.
B. Deep Security Manager-to-database traffic is encrypted by default, but can be disabled by modifying settings in the dsm.properties file.
C. Deep Security Manager-to-database traffic is encrypted by default but can be disabled by modifying settings in the db.properties file.
D. Deep Security Manager-to-database traffic is not encrypted by default, but can be enabled by modifying settings in the dsm.properties file.
Which of the following statements is true regarding Maintenance Mode in the Application Control protection Module?
A. While in Maintenance Mode, all Block and Allow rules are ignored while new or updated applications are added to the software inventory
B. When in Maintenance Mode, the Application Control Protection Module will continue to block software identified in Block rules, but will allow new and changed applications to be added to the software inventory.
C. When enabled, Maintenance Mode rescans the protected computer to rebuild the software inventory. Any new or changed software will be included in this rebuilt inventory.
D. Maintenance Mode can be configured as a Scheduled Event. In this scenario, all software upgrades will be performed at the same time every day to avoid creating Alerts for normal software updates.
The Intrusion Prevention Protection Module is enabled, its Behavior is set to Prevent and rules are assigned. When viewing the events, you notice that one of Intrusion Prevention rules is being triggered and an event is being logged but the traffic is not being blocked. What is a possible reason for this?
A. The Deep Security Agent is experiencing a system problem and is not processing packets since the "Network Engine System Failure" mode is set to "Fail Open".
B. The network engine is running in Inline mode. In Inline mode, Deep Security provides no protection beyond a record of events.
C. The Intrusion Prevention rule is being triggered as a result of the packet sanity check failing and the packet is being allowed to pass.
D. The default Prevention Behavior in this particular rule may be set to Detect. This logs the triggering of the rule, but does not actually enforce the block.
What is IntelliScan?
A. IntelliScan is a method of identifying which files are subject to malware scanning as determined from the file content. It uses the file header to verify the true file type.
B. IntelliScan is a mechanism that improves scanning performance. It recognizes files that have already been scanned based on a digital fingerprint of the file.
C. IntelliScan reduces the risk of viruses entering your network by blocking real-time compressed executable files and pairs them with other characteristics to improve mal-ware catch rates.
D. IntelliScan is a malware scanning method that monitors process memory in real time. It can identify known malicious processes and terminate them.
Which of the following statements is true regarding Firewall Rules?
A. Firewall Rules applied to Policy supersede similar rules applied to individuals computers.
B. When traffic is intercepted by the network filter, Firewall Rules in the policy are always applied before any other processing is done.
C. Firewall Rules applied through a parent-level Policy cannot be unassigned in a child level policy.
D. Firewall Rules are always processed in the order in which they appear in the rule list, as displayed in the Deep Security manager Web console.
A Recommendation Scan is run to determine which Intrusion Prevention rules are appropriate for a Server. The scan is configured to apply the suggested rules automatically and ongoing scans are enabled. Some time later, an operating system patch is applied. How can you de-termine which Intrusion Prevention rules are no longer needed on this Server?
A. The READ ME file provided with the software patch will indicate which issues were addressed with this release. Compare this list to the rules that are applied to determine which rules are no longer needed and can be disabled.
B. Since the rules are being applied automatically, when the next Intrusion Prevention Recommendation Scan is run automatically, any rules that are no longer needed will be automatically unassigned. These are rules that are no longer needed as the vulnerability was corrected with the patch.
C. Since there is no performance effect when multiple Intrusion Prevention rules are applied, there is no need to determine which rules are no longer needed. The original recommended rules can remain in place without affecting the system.
D. Since the rules are being applied automatically, when the next Intrusion Prevention Recommendation Scan is run automatically, any rules that are no longer needed will be displayed on the Recommended for Unassignment tab in the IPS Rules. These are rules that are no longer needed and can be disabled as the vulnerability was corrected with the patch.
As the administrator in a multi-tenant environment, you would like to monitor the usage of security services by tenants? Which of the following are valid methods for monitoring the usage of the system by the tenants?
A. Generate a Chargeback report in Deep Security manager Web console.
B. All the choices listed here are valid.
C. Use the Representational State Transfer (REST) API to collect usage data from the tenants.
D. Monitor usage by the tenants from the Statistics tab in the tenant Properties window.
Which of the following statements is correct regarding the policy settings displayed in the exhibit?
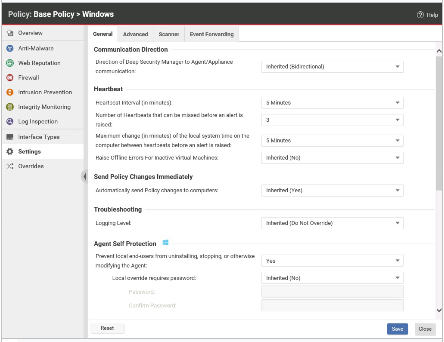
A. The Heartbeat interval value displayed in this policy is inherited from the parent policy
B. Deep Security Agents using the displayed policy will send event details to Deep Security Manager every 5 minutes.
C. All Deep Security Agents will send event details to Deep Security Manager every 5 minutes.
D. Deep Security Manager will refresh the policy details on the Deep Security Agents using this policy every 5 minutes.
| Page 1 out of 7 Pages |