The Security Level for Web Reputation in a policy is set to High. A server assigned this policy attempts to access a Web site with a credibility score of 78. What is the result?
A. The Deep Security Agent allows access to the Web site, and logs the connection attempt as an Event.
B. The Deep Security Agent allows access as the credibility score for the Web site is above the allowed threshold.
C. The Deep Security Agent blocks access as the credibility score for the Web site is below the allowed threshold. An error page is displayed in the Web browser.
D. The Deep Security Agent displays a warning message as the site is unrated.
What is the purpose of the Deep Security Notifier?
A. The Deep Security Notifier is a application in the Windows System Tray that displays the Status of Deep Security Manager during policy and software updates.
B. The Deep Security Notifier is a server components that collects log entries from managed computers for delivery to a configured SIEM device.
C. The Deep Security Notifier is a server component used in agentless configurations to allow Deep Security Manager to notify managed computers of pending updates.
D. The Deep Security Notifier is a application in the Windows System Tray that communicates the state of Deep Security Agents and Relays to endpoint computers.
Multi-tenancy is enabled in Deep Security and new tenants are created. Where does the new tenant data get stored when using SQL Server as the Deep Security database?
A. The new tenant data is added to the existing SQL Server database.
B. An additional table is created for each new tenant in the existing database in the SQL Server database to store its data.
C. An additional database is created in SQL Server for each new tenant to store its data.
D. An additional user is created for each new tenant in the SQL Server database to store its data.
Based on the details of event displayed in the exhibit, which of the following statements is false?
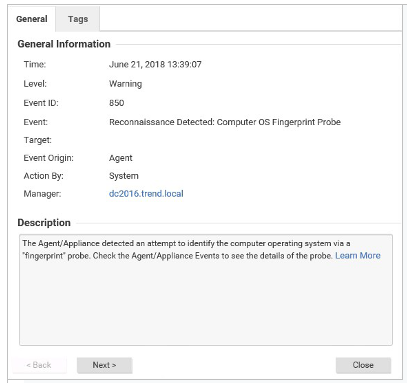
A. You can instruct the Deep Security Agents and Appliances to block traffic from the source IP address for a period of time.
B. You can create a firewall rule to permanently block traffic from the originating IP address.
C. The scan may be generated from an IP address which may be known to you. If so, the source IP address can be added to the reconnaissance whitelist.
D. The Intrusion Prevention Protection Modules must be enabled to detect reconnaissance scans.
The Intrusion Prevention Protection Module is enabled and a Recommendation Scan is run to identify vulnerabilities on a Windows Server 2016 computer. How can you insure that the list of recommendations is always kept up to date?
A. Disabling, then re-enabling the Intrusion Prevention Protection Module will trigger a new Recommendation Scan to be run. New rules will be included in the results of this new scan.
B. Recommendation Scans are only able to suggest Intrusion Prevention rules when the Protection Module is initially enabled.
C. Enable "Ongoing Scans" to run a recommendation scan on a regular basis. This will identify new Intrusion Prevention rules to be applied.
D. New rules are configured to be automatically sent to Deep Security Agents when Recommendation Scans are run.
Which of the following statements is false regarding the Log Inspection Protection Module?
A. Custom Log Inspections rules can be created using the Open Source Security (OSSEC) standard.
B. Deep Security Manager collects Log Inspection Events from Deep Security Agents at every heartbeat.
C. The Log Inspection Protection Module is supported in both agent-based and agentless environments.
D. Scan for Recommendations identifies Log Inspection rules that Deep Security should implement.
Multiple Application Control Events are being displayed in Deep Security after a series of ap-plication updates and the administrator would like to reset Application Control. How can this be done?
A. On the Deep Security Agent computer, type the following command to reset Application Control: dsa_control -r
B. Click "Clear All" on the Actions tab in the Deep Security Manager Web console to reset the list of Application Control events.
C. Application Control can be reset by disabling the Protection Module, then enabling it once again. This will cause local rulesets to be rebuilt.
D. Application Control can not be reset.
An administrator enables Multi-Tenancy in Deep Security and creates multiple tenants. After a period of time, the administrator would like to review the usage and resource consumption by a specific tenant. How can the administrator retrieve this information?
A. The administrator could check the Multi-Tenancy log file for resource consumption details.
B. The administrator could generate a Tenant report from within the Deep Security Manager Web console.
C. The administrator will not be able retrieve this information without licensing and enabling the Multi-Tenancy Chargeback module in the Deep Security Manager Web con-sole.
D. The administrator downloads the Tenant usage details from the Deep Security Agent on the Tenant computer.
Which of the following statements correctly identifies the purpose of the Integrity Monitoring Protection Module?
A. The Integrity Monitoring Protection Module monitors traffic to verify the integrity of incoming traffic to identify protocol deviations, packets fragments and other protocol anomalies.
B. The Integrity Monitoring Protection Module monitors critical operating system objects such as services, processes, registry keys and ports to detect and report malicious or unexpected changes.
C. The Integrity Monitoring Protection Module monitors incoming traffic to confirm the integrity of header information including packet source and destination details.
D. The Integrity Monitoring Protection Module monitors and analyzes the integrity of application logs to identify tampering, corruption and other suspicious modifications to the logs.
What is the effect of the Firewall rule displayed in the following exhibit?
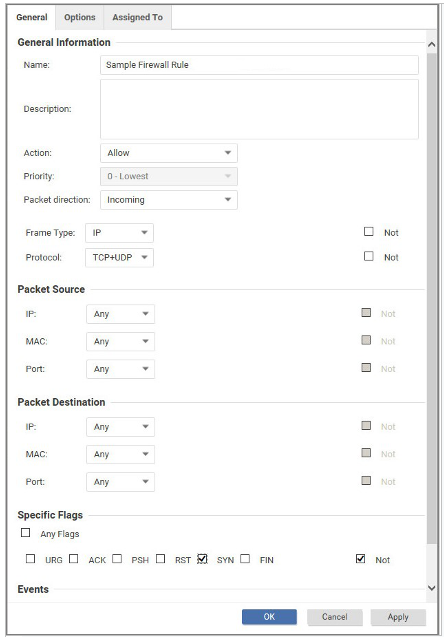
A. This rule will allow incoming TCP and UPD communication to this
B. This rule will allow outgoing TCP and UPD communication from this server.
C. This rule will allow TCP and UPD replies to requests originating on this server.
D. This rule will allow incoming communication to this server, but not TCP and UPD.
Which of the following statements is true regarding Intrusion Prevention protection?
A. Intrusion Prevention protection can drop malicious packets but cannot reset the connection.
B. Intrusion Prevention protection only works in conjunction with the Anti-Malware Protection Module.
C. Intrusion Prevention protection can only work on computers where a Deep Security Agent is installed; agentless protection is not supported.
D. Intrusion Prevention protection can drop or reset a connection.
Which of the following VMware components is not required to enable agentless protection using Deep Security.
A. VMware NSX
B. VMware ESXi
C. VMware vRealize
D. VMware vCenter
| Page 2 out of 7 Pages |
| Previous |