Topic 1: Exam Pool A
How does NETCONF YANG represent data structures?
A. as strict data structures defined by RFC 6020
B. in an XML tree format
C. In an HTML format
D. as modules within a tree
Which technology collects location information through data packets received by the APs instead of using mobile device probes?
A. detect and locate
B. FastLocate
C. hyperlocation
D. RF fingerprinting
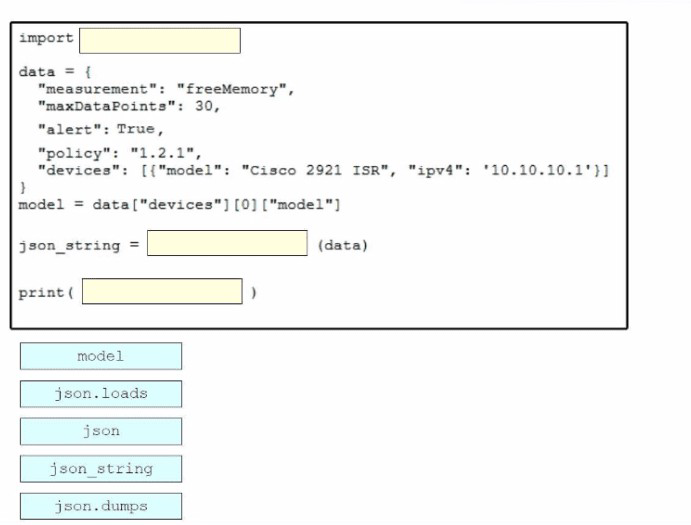
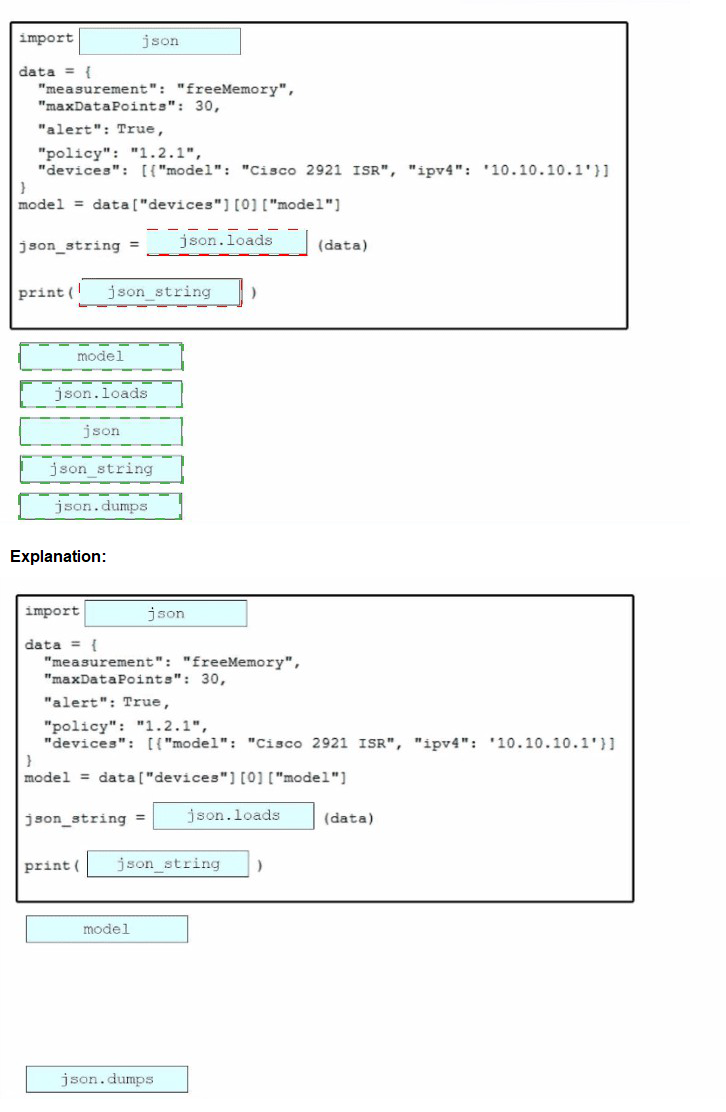
Drag and drop the code snippets from the bottom onto the blanks in the Python script to convert a Python object into a JSON string. Not all options are used.
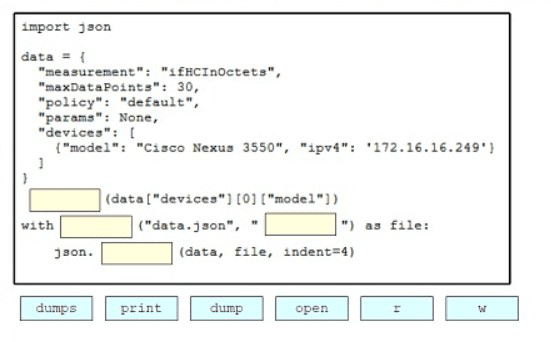
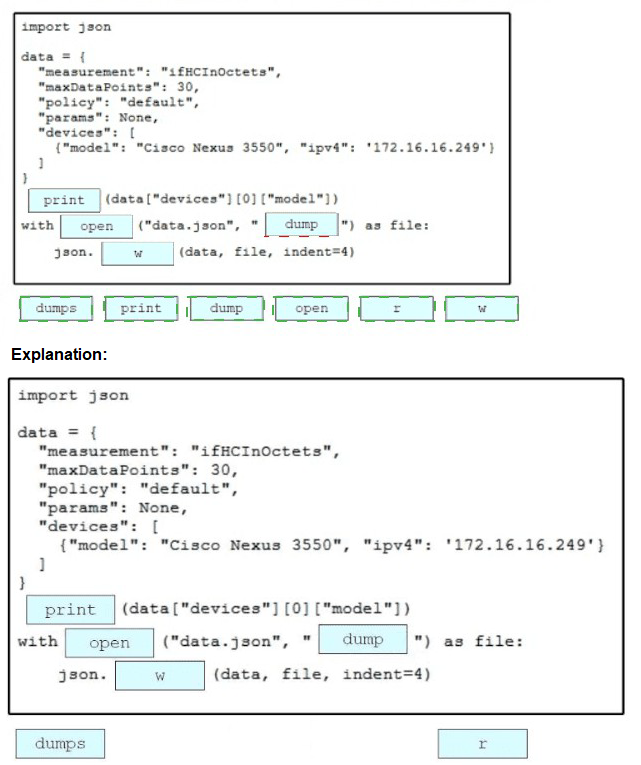
Drag and drop the code snippets from the bottom onto the blanks in the Python script to print the device model to the screen and write JSON data to a file. Not all options are used
A corporate policy mandates that a certificate-based authentication system must be implemented on the wireless infrastructure. All corporate clients will contain a certificate that will be used in conjunction with ISE and user credentials to perform authentication before the clients are allowed to connect to the corporate Wi-Fi. Which authentication key option must be selected to ensure that this authentication can take place?
A. none
B. PSK
C. 802.1x
D. CCKM
An engineer must create a new SSID on a Cisco 9800 wireless LAN controller. The client has asked to use a pre-shared key for authentication. Which profile must the engineer edit to achieve this requirement?
A. RF
B. WLAN
C. Policy
D. Flex
What is required for a VXLAN tunnel endpoint to operate?
A. a VXLAN tunnel endpoint identifier
B. at least one Layer 2 interface and one Layer 3 interlace
C. at least one IP for the transit network and one IP for endpoint connectivity
D. a VXLAN network identifier
Refer to the exhibit. An engineer must adjust the configuration so that Router A becomes the active router. Which commands should be applied to router A? (Choose two)

A. vrrp 1 priority 90
B. vrrp 1 timers advertise 1
C. vrrp lip 10.1.0.11
D. ip address 10.1.0.11 255.0.0.0
E. vrrp 1 priority 120
Which nodes require VXLAN encapsulation support In a Cisco SD-Access deployment?
A. core nodes
B. distribution nodes
C. border nodes
D. aggregation nodes
What is two characteristic of Cisco DNA Center and vManage northbound APIs?
A. They exchange XML-formatted content
B. They exchange JSON-kxmatted content.
C. They implement the RESTCONF protocol.
D. They implement the NETCONF protocol.
E. They exchange protobuf-formatted content.
Refer to the exhibit.
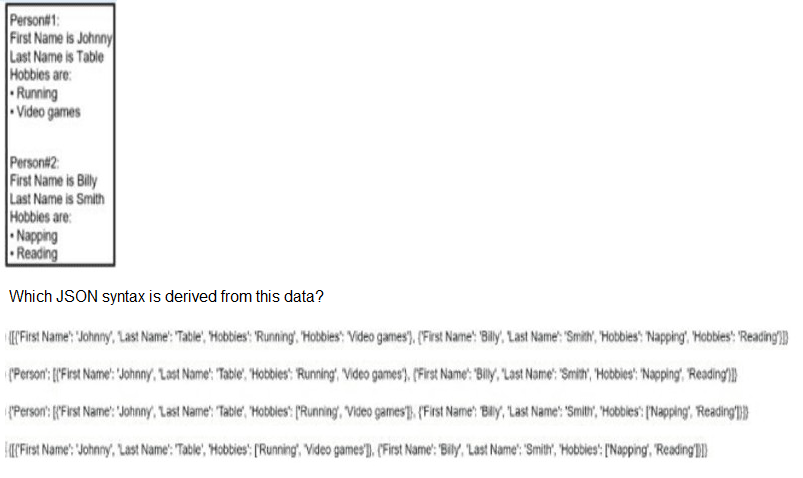
A. Option A
B. Option B
C. Option C
D. Option D
When should the MAC authentication bypass feature be used on a switch port?
A. when authentication is required, but the attached host does not support 802.1X
B. when the attached host supports 802.1X and must authenticate itself based on its MAC address instead of user credentials
C. when authentication should be bypassed for select hosts based on their MAC address
D. when the attached host supports limited 802.1X
| Page 13 out of 30 Pages |
| Previous |