Topic 1: Exam Pool A
What is the name of the numerical relationship of the wireless signal compared to the noise floor?
A. SNR
B. RSSI
C. EIRP
D. gain
What occurs during a Layer 2 inter-controller roam?
A. A new security context is applied for each controller to which the client is associated, but the IP address remains the same.
B. The client must be associated to a new controller where a new IP address and security context are applied.
C. The client retains the same IP address and security context.
D. The client is marked as foreign in the database of each new controller to which it is connected.
Which character formatting is required for DHCP Option 43 to function with current AP models?
A. ASCII
B. Hex
C. Base64
D. MD5
What is the API keys option for REST API authentication?
A. a credential that is transmitted unencrypted
B. one-time encrypted token
C. a username that is stored in the local router
D. a predetermined string that is passed from client to server.
In a virtual environment, what is a VMDK file?
A. A file containing information about snapshots of a virtual machine.
B. A zip file connecting a virtual machine configuration file and a virtual disk. A configuration file containing settings for a virtual machine such as a guest OS. A file containing a virtual machine disk drive.
C. A configuration file containing settings for a virtual machine such as a guest OS.
D. A file containing a virtual machine disk drive.
What are two characteristics of Cisco Catalyst SD-WAN? (Choose two.)
A. control plane operates over DTLS/TLS authenticated and secured tunnels
B. time-consuming configuration and maintenance
C. distributed control plane
D. unified data plane and control plane
E. centralized reachability, security, and application policies
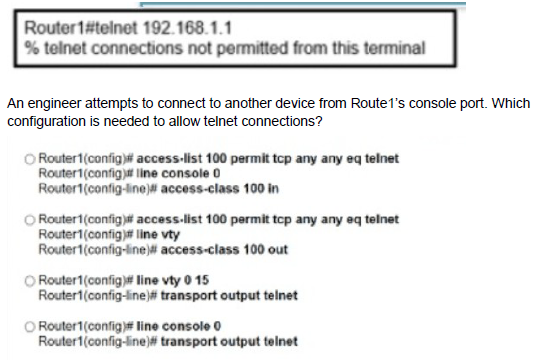
A. Option A
B. Option B
C. Option C
D. Option D
Which statement describes the Cisco SD-Access plane functionality for fabricenabled wireless?
A. Control plane traffic and data plane traffic are sent to the WLC through VXLAN.
B. The control plane traffic is sent to the WLC through CAPWAP tunnels, and the data plane traffic is sent from the AP to the fabric edge switch through VXLAN.
C. The control plane traffic is sent to the WLC through VXLAN, and the data plane traffic is sent to the WLC through CAPWAP tunnels.
D. Control plane traffic and data plane traffic are sent to the WLC through CAPWAP tunnels.
A wireless network engineer must configure a WPA2+WPA3 policy with the Personal security type. Which action meets this requirement?
A. Configure the GCMP256 encryption cipher.
B. Configure the CCMP128 encryption cipher.
C. Configure the GCMP128 encryption cipher.
D. Configure the CCMP256 encryption cipher.
A client device roams between wireless LAN controllers that are mobility peers, Both controllers have dynamic interface on the same client VLAN which type of roam is described?
A. intra-VLAN
B. inter-controller
C. intra-controller
D. inter-subnet
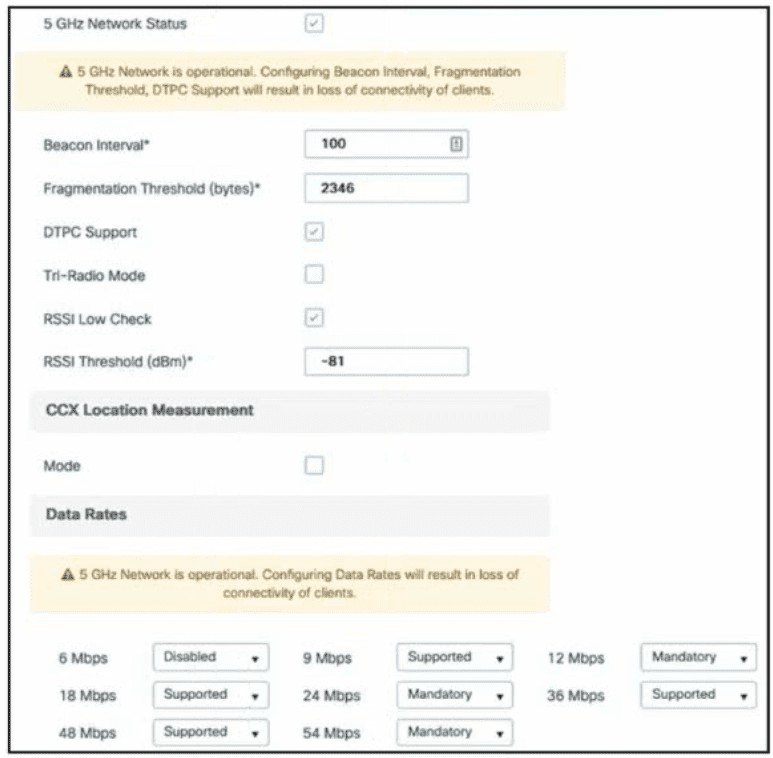
A. Set the 24 Mbps and 54 Mbps data rates to Supported.
B. Set the RSSI Threshold to -67dBm.
C. Set the Fragmentation Threshold to 1250 bytes
D. Disable RSSI Low Check.
In which forms can Cisco Catalyst SD-WAN routers be deployed at the perimeter of a site to provide SD-WAN services?
A. virtualized instances
B. hardware, software, cloud, and virtualized instances
C. hardware, virtualized. and cloud instances
D. hardware and virtualized instances
| Page 12 out of 30 Pages |
| Previous |