Topic 1: Exam Pool A
What is one main REST security design principle?
A. separation of privilege
B. password hashing
C. Confidential algorithms
D. OAuth
Which two conditions occur when the primary route processor fails on a switch thatisusing dual route processors with stateful switchover? (Choose two.)
A. Data forwarding is stopped until the routing protocols reconverge after the switchover.
B. The standby route processor initialization is started when the primary router processor fails.
C. The standby route processor is fully initialed and state information is maintained.
D. User sessions are immediately recreated on the new active route processor.
E. Data forwarding can continue along known paths until routing protocol information is restored.
Why are stateless calls executed by REST API useful in cloud applications?
A. They use HTTPS to implement all calls.
B. They control URL decoding.
C. They are easy to redeploy and to scale.
D. They rely on data stored on the server for calls.
What is a characteristic of VRRP?
A. It inherently balances load amongst the available gateways.
B. It ensures symmetric traffic flow upstream and downstream.
C. It Is a Cisco proprietary protocol.
D. It uses a virtual IP address and a virtual MAC address to achieve redundancy
Which measurement is used from a post wireless survey to depict the cell edge of the access points?
A. RSSI
B. SNR
C. Noise
D. CCI
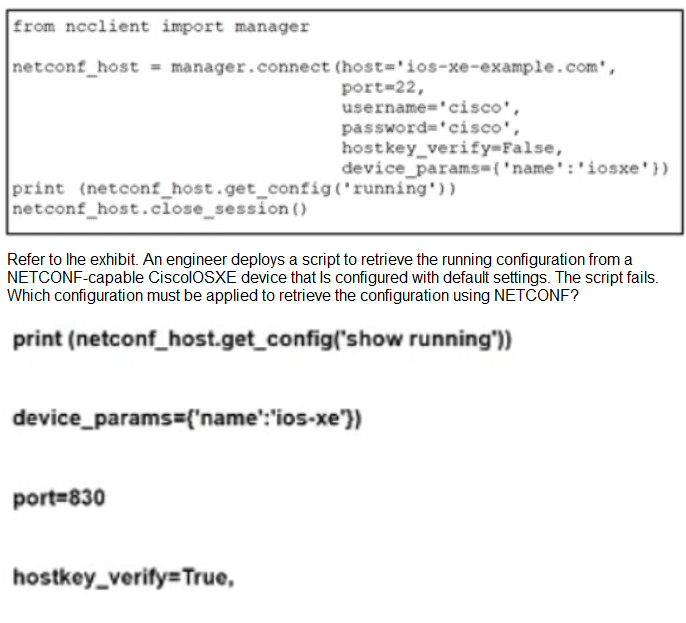
A. Option A
B. Option B
C. Option C
D. Option D
Which unit of measure is used to measure wireless RF SNR?
A. mw
B. dbm
C. db
D. dBi
What is a characteristic of VXLAN?
A. It extends Layers 2 and Layer 3 overlay network over a Layer 2 underly.
B. It has a 12-byte packet header.
C. Its frame encapsulation is performed by MAC-in-UDP.
D. It uses TCP for transport
What does a next-generation firewall that is deployed at the data center protect against?
A. signature-based malware
B. DMZ web server vulnerabilities
C. zero-day attacks
D. DDoS
Which two characteristics apply to Type 1 hypervisors? (Choose two.)
A. They are widely available to license for free.
B. They provide a platform for running bare metal operating systems.
C. They can be used to create and manage virtual storage
D. They are a software layer that runs on top of a virtual server.
E. They provide a platform for running guest operating systems.
What are two benefits of using Cisco TrustSec? (Choose two.)
A. unknown file analysis using sandboxing
B. advanced endpoint protection against malware
C. end-to-end traffic encryption
D. simplified management of network access
E. consistent network segmentation
Which two southbound interfaces originate from Cisco Catalyst Center (formerly DNA Center) and terminate at fabric underlay switches'? (Choose two.)
A. ICMP Discovery
B. UDP67 DHCP
C. TCP 23 Telnet
D. UDP6007 NetFlow
E. UDP 162 SNMP
| Page 11 out of 30 Pages |
| Previous |