A Linux system is failing to boot. The following error is displayed in the serial console:
[[1;33mDEPEND[Om] Dependency failed for /data.
[[1;33mDEPEND[Om] Dependency failed for Local File Systems
...
Welcome to emergency mode! After logging in, type "journalctl -xb" to viewsystem logs,
"systemctl reboot" to reboot, "systemctl default" to try again to boot into default mode.
Give root password for maintenance (or type Control-D to continue}
Which of the following files will need to be modified for this server to be able to boot again?
A.
/etc/mtab
B.
/dev/sda
C.
/etc/fstab
D.
/ete/grub.conf
/etc/fstab
Summary:
The system has failed to boot and has entered emergency mode. The specific error messages indicate a "Dependency failed for /data" and "Dependency failed for Local File Systems." This state is almost always caused by a problem defined in the /etc/fstab file, which contains the instructions for what filesystems to mount at boot. If a device listed in this file is unavailable, incorrectly configured, or has errors, the boot process will halt.
Correct Option:
C. /etc/fstab:
This is the file that needs to be modified. The /etc/fstab (file systems table) is read by the system during the boot process to automatically mount filesystems. The error explicitly states that the mount for /data failed. The administrator must log in via emergency mode, check the /etc/fstab file for the entry corresponding to /data, and correct the device path, filesystem type, or other options. Alternatively, they could temporarily comment out the line to allow the system to boot.
Incorrect Options:
A. /etc/mtab:
This file dynamically lists the filesystems that are currently mounted. It is maintained by the mount command and is a reflection of the system's state, not a configuration file. Modifying it would not fix the underlying configuration error causing the boot failure.
B. /dev/sda:
This is a device file representing the first disk drive. It is not a configuration file that can be edited to solve a boot dependency issue. Modifying a raw block device would corrupt data, not fix a boot problem.
D. /ete/grub.conf:
This path is incorrect and contains a typo (/ete instead of /etc). The correct GRUB configuration file is typically /boot/grub2/grub.cfg or /etc/grub2.cfg. While GRUB issues can prevent booting, the specific error message about filesystem dependencies points directly to fstab, not the bootloader.
Reference:
Official CompTIA Linux+ (XK0-005) Certification Exam Objectives: This scenario falls under Objective 1.3: "Given a scenario, conduct a Linux boot process and troubleshooting," which includes troubleshooting boot issues and managing the fstab file. Understanding that emergency mode is often entered due to fstab errors is a critical troubleshooting skill.
A cloud engineer needs to change the secure remote login port from 22 to 49000. Which of the following files should the engineer modify to change the port number to the desired value?
B.
/etc/hostname
C.
/etc/services
D.
/etc/ssh/sshd_config
/etc/ssh/sshd_config
Summary:
The engineer needs to change the port on which the SSH daemon (sshd) listens for incoming connections. This is a service-specific configuration change, not a system-wide network or hostname setting. The configuration must be modified in the file that controls the behavior of the SSH server itself.
Correct Option:
D. /etc/ssh/sshd_config:
This is the primary configuration file for the SSH daemon. It contains directives that control the operation of the server, including the port number. The engineer would edit this file and change the Port directive (or add it if it doesn't exist) to 49000, then restart the sshd service for the change to take effect.
Incorrect Options:
A. /etc/host.conf:
This file determines the order in which hostnames are resolved (e.g., via hosts file or DNS). It has no control over service ports.
B. /etc/hostname:
This file contains the system's hostname. Changing this file would affect how the system identifies itself on the network, not the port SSH listens on.
C. /etc/services:
This file is a static database that maps well-known service names to their assigned port numbers and protocols (e.g., ssh 22/tcp). It is used for informational purposes by network utilities but does not control which ports services actually bind to. Changing a port here would not reconfigure the SSH daemon.
Reference:
OpenSSH Manual (sshd_config): The official documentation for the SSH daemon configuration file, which describes the Port directive.
A systems administrator is compiling a report containing information about processes that are listening on the network ports of a Linux server. Which of the following commands will allow the administrator to obtain the needed information?
A.
ss -pint
B.
tcpdump -nL
C.
netstat -pn
D.
lsof -It
ss -pint
Summary:
The administrator needs to generate a report of processes that are actively listening for network connections. The command must show which network ports are open and which process has each port open. The tool should provide a clear, list-based output suitable for a report, showing port numbers, the listening process, and its PID.
Correct Option:
A. ss -pint:
This is the most efficient and modern command for this task. The ss (socket statistics) command is designed to dump socket statistics and replaces the older netstat.
-p shows the process name and PID using the socket.
-i shows internal TCP information.
-n prevents service name resolution, showing port numbers instead (faster and better for reports).
-t shows only TCP sockets.
-l shows only listening sockets.
Incorrect Options:
B. tcpdump -nL:
tcpdump is a network packet analyzer, not a socket lister. The -L flag lists the data link types for an interface, it does not list processes listening on network ports. This command is for capturing or analyzing network traffic, not for reporting on listening services.
C. netstat -pn:
While netstat can provide this information and was the traditional tool, it is now considered obsolete and is replaced by ss. The -p shows the PID/program, and -n shows numerical addresses. However, it is missing the -l flag to show only listening ports, so it would show all network connections, making the output less focused for a report on listening services.
D. lsof -It:
The lsof command lists open files, and network connections are considered files in Linux. However, the flags are incorrect. -I is for selecting by IP version, and -t produces a terse (PID-only) output, which is not suitable for a detailed report. The correct lsof syntax would be more complex, such as lsof -iTCP -sTCP:LISTEN -P -n.
Reference:
Linux man-pages project (ss): The official documentation for the ss command, which is the recommended tool for showing socket statistics.
A user is asking the systems administrator for assistance with writing a script to verify whether a file exists. Given the following:
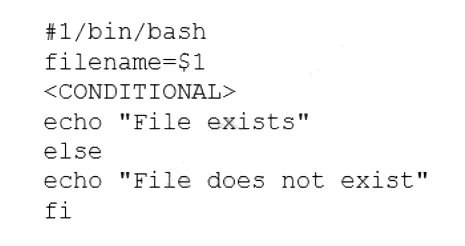
Which of the following commands should replace the
A.
if [ -f "$filename" ]; then
B.
if [ -d "$filename" ]; then
C.
if [ -f "$filename" ] then
D.
if [ -f "$filename" ]; while
if [ -f "$filename" ]; then
Summary:
The script snippet is a Bash script designed to check if a file exists. The script takes a filename as an argument ($1). The
Correct Option:
A. if [ -f "$filename" ]; then: This is the correct and complete syntax.
if starts the conditional statement.
[ -f "$filename" ] is the test command. The -f flag checks if the path exists and is a regular file. The variable $filename is quoted to handle filenames with spaces.
; terminates the test command, allowing then to be on the same line.
then begins the block of code to execute if the condition is true.
Incorrect Options:
B. if [ -d "$filename" ]; then:
This uses the -d flag, which checks if the path exists and is a directory. The requirement is to check for a file, so this operator is incorrect for the stated goal.
C. if [ -f "$filename" ] then:
This is missing the semicolon (;) or a newline before the then keyword. In Bash, the then must be a separate command, which requires either being on a new line or being separated from the test bracket with a semicolon. This syntax would cause a syntax error.
D. if [ -f "$filename" ]; while:
This incorrectly uses the while loop keyword after the conditional test. The if statement must be followed by then to start the conditional block, not by another loop keyword.
Reference:
Bash Reference Manual (Conditional Constructs): The official documentation explains the syntax for the if statement.
A Linux administrator booted up the server and was presented with a non-GUI terminal. The administrator ran the command systemctl isolate graphical.target and rebooted the system by running systemctl reboot, which fixed the issue. However, the next day the administrator was presented again with a non-GUI terminal. Which of the following is the issue?
A.
The administrator did not reboot the server properly.
B.
The administrator did not set the default target to basic.target.
C.
The administrator did not set the default target to graphical.target.
D.
The administrator did not shut down the server properly.
The administrator did not set the default target to graphical.target.
Summary:
The administrator temporarily fixed the issue by using systemctl isolate graphical.target, which switched the current session to the graphical interface. The systemctl reboot command then restarted the system. However, because the change was not made permanent, the server reverted to its default boot target upon the next startup. The core issue is that the system's default target was not set to start the GUI environment automatically on boot.
Correct Option:
C. The administrator did not set the default target to graphical.target:
The systemctl isolate command only changes the active target for the current session; it is a temporary state. To make this change permanent across reboots, the administrator needed to run systemctl set-default graphical.target. This command creates a symlink from the default target to graphical.target, ensuring the system boots into the GUI environment every time.
Incorrect Options:
A. The administrator did not reboot the server properly:
The systemctl reboot command is a standard and proper way to restart a Linux system. The issue persisted after a full reboot cycle, confirming the reboot itself was not the problem.
B. The administrator did not set the default target to basic.target:
basic.target is a minimal system initialization target that serves as a foundation for other targets. Setting the default to basic.target would not enable the graphical user interface and is not the desired state for a system requiring a GUI.
D. The administrator did not shut down the server properly:
There is no indication of an improper shutdown. The issue is consistent and reproducible: the system consistently boots into a non-GUI terminal, which points directly to a misconfigured default boot target, not a filesystem or state error caused by a bad shutdown.
Reference:
systemd Official Documentation (systemctl): The official man page explains the set-default command for permanently changing the default target.
At what point is the Internal Certificate Authority (ICA) created?
A.
During the primary Security Management Server installation process.
B.
Upon creation of a certificate
C.
When an administrator decides to create one
D.
When an administrator initially logs into SmartConsole.
When an administrator decides to create one
Summary:
An SSH private key file can be encrypted with a passphrase for an additional layer of security. If this passphrase is weak and gets cracked, the user needs a way to change it to a stronger one without generating a whole new key pair. The tool used to create SSH keys also has the functionality to change the passphrase on an existing private key.
Correct Option:
C. ssh-keygen:
This is the correct command. The ssh-keygen tool, which is used to generate new SSH key pairs, can also change the passphrase of an existing private key. The command ssh-keygen -p -f /path/to/private_key will prompt the user for the old passphrase and then for a new, stronger one, thereby re-encrypting the private key file with the new password.
Incorrect Options:
A. passwd:
This command is used to change the login password of a user account on the Linux system. It has no effect on the passphrase of an SSH key file, which is a separate form of encryption on the key file itself.
B. ssh:
This command is used to initiate SSH connections to remote servers. It does not have a sub-command or functionality for managing or changing key passphrases.
D. pwgen:
This is a utility for generating random passwords. It can be used to create a strong password, but it cannot set that password on the SSH key file. The user would still need to use ssh-keygen to apply the newly generated password to the key.
Reference:
Official CompTIA Linux+ (XK0-005) Certification Exam Objectives: This scenario falls under Objective 4.2: "Given a scenario, implement and configure Linux firewalls and access control options," which includes managing SSH and key-based authentication. Knowing how to use ssh-keygen to manage key passphrases is a fundamental security practice.
A Linux administrator is trying to remove the ACL from the file /home/user/data. txt but receives the following error message:
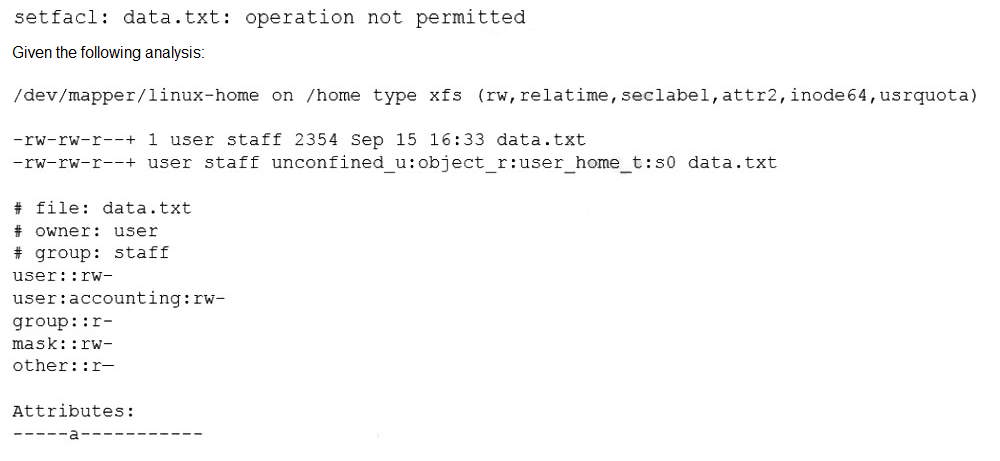
Which of the following is causing the error message?
A.
The administrator is not using a highly privileged account
B.
The filesystem is mounted with the wrong options.
C.
SELinux file context is denying the ACL changes
D.
File attributes are preventing file modification
The filesystem is mounted with the wrong options.
Summary:
The task requires enabling IPv4 packet forwarding and making the change persistent across reboots. Packet forwarding is a kernel parameter controlled by the net.ipv4.ip_forward setting. The correct command must change this runtime parameter and ensure the change is written to the system's configuration so it survives a restart.
Correct Option:
B. sysctl -w net.ipv4.ip_forward=1:
This is the correct command. The sysctl command is used to modify kernel parameters at runtime. The -w flag writes the value. More importantly, to make it persistent, the administrator must also add net.ipv4.ip_forward = 1 to the /etc/sysctl.conf file or a file in /etc/sysctl.d/. The sysctl command itself is the standard tool for this task, and using it is the first step in the persistent configuration process.
Incorrect Options:
A. echo 1 > /proc/sys/net/ipv4/ip_forward:
This command will enable packet forwarding immediately by writing directly to the virtual file in /proc/sys/. However, this change is only temporary and will be lost after a system reboot. It does not accomplish the "persistent" requirement.
C. firewall-cmd --enable ipv4_forwarding:
This is not a valid firewall-cmd command. firewall-cmd is used to configure firewalld zones and rules, not to set core kernel networking parameters like IP forwarding. The correct flag for masquerading or forwarding in firewalld is different (--add-masquerade).
D. systemctl start ipv4_forwarding:
There is no systemd service called ipv4_forwarding. IP forwarding is a kernel parameter, not a service that can be started or stopped.
Reference:
Linux man-pages project (sysctl): The official documentation explains how to use sysctl to configure kernel parameters.
In order to copy data from another VLAN, a systems administrator wants to temporarily assign IP address 10.0.6 5/24 to the newly added network interface enp1s0f1. Which of the following commands should the administrator run to achieve the goal?
A.
ip addr add 10.0.6.5/24 dev enpls0f1
B.
echo "IPV4_ADDRESS=10.0.6.5/24" > /etc/sysconfig/network-scripts/ifcfg-enplsOfl
C.
ifconfig 10.0.6.5/24 enpsIs0f1
D.
nmcli conn add lpv4.address-10.0.6.5/24 ifname enpls0f1
ip addr add 10.0.6.5/24 dev enpls0f1
Summary:
The administrator's goal is to temporarily assign an IP address to a network interface. A temporary assignment is one that is effective only for the current session and will be lost upon a system reboot. This requires using a command that makes a runtime change to the network interface's configuration without writing the change to a persistent configuration file.
Correct Option:
A. ip addr add 10.0.6.5/24 dev enp1s0f1:
This is the correct command. The ip addr add command from the iproute2 toolkit is the modern standard for making runtime changes to network interfaces. It immediately assigns the IP address 10.0.6.5/24 to the interface enp1s0f1 without saving the configuration to disk. This change is purely temporary and meets the requirement exactly.
Incorrect Options:
B. echo "IPV4_ADDRESS=10.0.6.5/24" > /etc/sysconfig/network-scripts/ifcfg-enplsOfl:
This command writes the IP address to a persistent configuration file. Any change made by writing to a file in /etc/sysconfig/network-scripts/ will not take effect immediately and will persist after a reboot. The administrator would need to run a separate command like ifup or restart NetworkManager to apply it, which contradicts the "temporary" requirement.
C. ifconfig 10.0.6.5/24 enpsIs0f1:
The ifconfig command is considered deprecated and its syntax is often incorrect for modern use. The standard syntax for a temporary assignment with the older ifconfig would be ifconfig enp1s0f1 10.0.6.5 netmask 255.255.255.0. Even if syntactically corrected, ip addr is the tool recommended for new scripts and configurations.
D. nmcli conn add ipv4.address-10.0.6.5/24 ifname enpls0f1:
This nmcli command has a syntax error (it should be ipv4.addresses, not ipv4.address-). More importantly, nmcli conn add creates a new persistent connection profile in NetworkManager. This profile is saved to disk and will be active across reboots, which is the opposite of a temporary assignment.
Reference:
Official CompTIA Linux+ (XK0-005) Certification Exam Objectives: This scenario falls under Objective 4.1: "Given a scenario, configure and manage networking and storage," which includes using command-line utilities to configure network interfaces. Knowing the difference between temporary (ip addr) and persistent (nmcli, config files) configuration methods is a key skill.
A Linux administrator is tasked with adding users to the system. However, the administrator wants to ensure the users’ access will be disabled once the project is over. The expiration date should be 2021-09-30. Which of the following commands will accomplish this task?
A.
sudo useradd -e 2021-09-30 Project_user
B.
sudo useradd -c 2021-09-30 Project_user
C.
sudo modinfo -F 2021-09-30 Project_uses
D.
sudo useradd -m -d 2021-09-30 Project_user
sudo useradd -e 2021-09-30 Project_user
Summary:
The administrator needs to create a user account with a specific expiration date, after which the account will be automatically disabled and unable to log in. The useradd command is used for this purpose, and it has a specific option to set an account expiration date. The correct command must use this option with the specified date in the correct format.
Correct Option:
A. sudo useradd -e 2021-09-30 Project_user:
This is the correct command. The -e (expire) flag is used to set the account expiration date. The date must be in the format YYYY-MM-DD. After 2021-09-30, the Project_user account will be locked and inaccessible.
Incorrect Options:
B. sudo useradd -c 2021-09-30 Project_user:
The -c flag is used to set a comment, typically the user's full name or a description. It does not set an expiration date.
C. sudo modinfo -F 2021-09-30 Project_uses:
The modinfo command is used to display information about kernel modules and is completely unrelated to user account management. The syntax is also incorrect.
D. sudo useradd -m -d 2021-09-30 Project_user:
The -d flag is used to specify the user's home directory path. The -m flag tells useradd to create the home directory. This command would incorrectly try to use the date string as a directory path.
Reference:
Linux man-pages project (useradd): The official documentation explains the -e option for setting the account expiration date.
A Linux administrator was asked to run a container with the httpd server inside. This container should be exposed at port 443 of a Linux host machine while it internally listens on port 8443. Which of the following commands will accomplish this task?
A.
podman run -d -p 443:8443 httpd
B.
podman run -d -p 8443:443 httpd
C.
podman run –d -e 443:8443 httpd
D.
podman exec -p 8443:443 httpd
podman run -d -p 443:8443 httpd
Summary:
The task requires mapping a container's internal port to a different port on the host. The -p (publish) flag in Podman/Docker is used for this purpose. The syntax is -p
Correct Option:
A. podman run -d -p 443:8443 httpd: This command is correctly structured.
-d runs the container in detached (background) mode.
-p 443:8443 correctly maps host port 443 to the container's internal port 8443.
httpd is the image name.
This allows users to connect to https://hostname (port 443) and have the traffic routed to the web server inside the container on port 8443.
Incorrect Options:
B. podman run -d -p 8443:443 httpd:
This command has the port mapping reversed. It maps host port 8443 to the container's port 443. This would mean the service inside the container would need to be listening on port 443, and users would have to connect to the host on port 8443, which does not meet the requirement.
C. podman run –d -e 443:8443 httpd:
The -e flag is used to set environment variables inside the container, not to publish ports. This syntax is invalid for port mapping and the command will not work as intended. The long double-dash before d is also a typo.
D. podman exec -p 8443:443 httpd:
The podman exec command is used to run a command inside an already running container. It is not used to create and start a new container, and it does not support the -p flag for port publishing.
Reference:
Podman Documentation (podman-run): The official documentation explains the -p flag for publishing container ports to the host.
A systems administrator is receiving tickets from users who cannot reach the application app that should be listening on port 9443/tcp on a Linux server. To troubleshoot the issue, the systems administrator runs netstat and receives the following output:
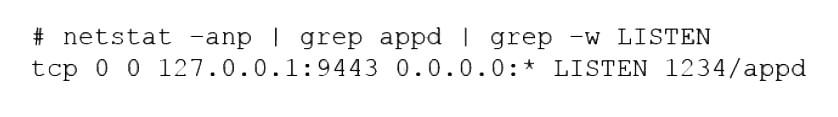
Based on the information above, which of the following is causing the issue?
A.
The IP address 0.0.0.0 is not valid.
B.
The application is listening on the loopback interface.
C.
The application is listening on port 1234.
D.
The application is not running.
The application is listening on the loopback interface.
Summary:
Users cannot connect to an application that should be listening on port 9443. The netstat output shows that a process is indeed listening on port 9443, but the "Local Address" column reveals it is bound to 127.0.0.1:9443. The IP address 127.0.0.1 is the loopback interface, which is only accessible from the server itself. This configuration prevents any remote connections from other machines on the network.
Correct Option:
B. The application is listening on the loopback interface:
This is the direct cause of the issue. The application is bound to 127.0.0.1 (localhost), which restricts connections to the local machine only. For the application to be reachable from other hosts, it needs to be bound to the server's external IP address or to 0.0.0.0 (which means all interfaces).
Incorrect Options:
A. The IP address 0.0.0.0 is not valid:
The address 0.0.0.0 is valid and has a specific meaning; it indicates that a service is listening on all available network interfaces. The problem is that the service is not using 0.0.0.0.
C. The application is listening on port 1234:
The netstat output shows a process listening on port 1234, but this is unrelated to the application in question, which is specified to use port 9443. The application on port 9443 is running, but on the wrong interface.
D. The application is not running:
The netstat output proves the application is running and listening on port 9443. The issue is its network binding, not its execution state.
Reference:
Linux man-pages project (netstat): The official documentation explains the output, including the meaning of the Local Address column.
A Linux system is failing to start due to issues with several critical system processes. Which of the following options can be used to boot the system into the single user mode? (Choose two.)
A.
Execute the following command from the GRUB rescue shell: mount -o remount,
ro/sysroot.
B.
Interrupt the boot process in the GRUB menu and add systemd.unit=single in the kernel line.
C.
Interrupt the boot process in the GRUB menu and add systemd.unit=rescue.target in the kernel line.
D.
Interrupt the boot process in the GRUB menu and add single=user in the kernel line.
E.
Interrupt the boot process in the GRUB menu and add init=/bin/bash in the kernel line.
F.
Interrupt the boot process in the GRUB menu and add systemd.unit=single.target in the kernel line.
Interrupt the boot process in the GRUB menu and add systemd.unit=rescue.target in the kernel line.
Interrupt the boot process in the GRUB menu and add systemd.unit=single.target in the kernel line.
Summary:
The system is failing to start due to issues with critical processes, and the administrator needs to boot into a minimal, single-user environment for troubleshooting. This mode provides a root shell with a minimal set of started services, allowing for repair operations. On modern systems using systemd, this is achieved by specifying a specific target at the bootloader.
Correct Options:
C. Interrupt the boot process in the GRUB menu and add systemd.unit=rescue.target in the kernel line:
This boots the system into the rescue target. It is a more basic state than multi-user, mounting the root filesystem read-only and starting only a few essential services, providing a single-user root shell for emergency repair.
F. Interrupt the boot process in the GRUB menu and add systemd.unit=single.target in the kernel line:
This is the direct systemd equivalent of traditional single-user mode. It starts the system with a minimal set of services and provides a root shell, which is ideal for system recovery when multi-user boot fails.
Incorrect Options:
A. Execute the following command from the GRUB rescue shell: mount -o remount,ro /sysroot:
This command is used after booting into a rescue environment to remount the root filesystem as read-only. It is not a method to boot into single-user mode.
B. Interrupt the boot process in the GRUB menu and add systemd.unit=single in the kernel line:
The correct target name is single.target, not just single. This syntax is incomplete and would not work.
D. Interrupt the boot process in the GRUB menu and add single=user in the kernel line:
This is an older SysVinit-style parameter. While some systems might translate it for compatibility, the correct and modern method for systemd systems is to use the systemd.unit= syntax.
E. Interrupt the boot process in the GRUB menu and add init=/bin/bash in the kernel line:
This tells the kernel to run /bin/bash as the first process (init) instead of systemd. This bypasses the entire init system, which can be useful but is more drastic and may not properly set up the environment (like virtual consoles) compared to the rescue or single targets.
Reference:
systemd Official Documentation (systemd.target): The official man page describes the special targets, including rescue.target and single.target.
| Page 9 out of 40 Pages |
| Previous |