A Linux administrator created the directory /project/access2all. By creating this directory, the administrator is trying to avoid the deletion or modification of files from non-owners. Which of the following will accomplish this goal?
A.
chmod +t /project/access2all
B.
chmod +rws /project/access2all
C.
chmod 2770 /project/access2all
D.
chmod ugo+rwx /project/access2all
chmod +t /project/access2all
Summary:
The goal is to protect files in a directory from being deleted or modified by users who are not the file's owner. This is a classic use case for the "sticky bit" on a directory. When the sticky bit is set on a directory, it restricts file deletion so that only the file's owner, the directory's owner, or the root user can remove or rename the files within it, even if other users have write permission to the directory.
Correct Option:
A. chmod +t /project/access2all:
This command sets the sticky bit on the directory. The +t flag is the symbolic method for applying this special permission. This ensures that users cannot delete or rename each other's files within /project/access2all, achieving the stated goal.
Incorrect Options:
B. chmod +rws /project/access2all:
This command sets the read (r), write (w), and setuid/setgid (s) permissions. The setgid bit (s on a directory) causes new files to inherit the directory's group, but it does not prevent users with write access from deleting any file in the directory. The setuid bit (s on a file) is a security risk for directories and is not used for this purpose.
C. chmod 2770 /project/access2all:
The 2 in the mode 2770 sets the setgid bit (not the sticky bit). This is useful for ensuring group collaboration (files inherit the parent directory's group), but it does not prevent members of the directory's owning group from deleting each other's files.
D. chmod ugo+rwx /project/access2all:
This command gives read, write, and execute permissions to the owner (u), group (g), and others (o). This is the opposite of the goal; it gives the broadest possible permissions, allowing any user on the system to delete any file in the directory.
Reference:
Linux man-pages project (chmod): The official documentation explains the special permissions, including the sticky bit (t).
A Linux administrator needs to expand a volume group using a new disk. Which of the following options presents the correct sequence of commands to accomplish the task?
A.
partprobe
vgcreate
lvextend
B.
lvcreate
fdisk
partprobe
C.
fdisk
partprobe
mkfs
D.
fdisk
pvcreate
vgextend
fdisk
pvcreate
vgextend
Summary:
To expand a volume group in LVM (Logical Volume Manager) using a new physical disk, the administrator must first prepare the disk, then integrate it into the LVM subsystem, and finally add it to the existing volume group. The correct sequence involves partitioning (or preparing the whole disk), marking it as an LVM physical volume, and then using the volume group tool to extend the group's capacity with this new physical volume.
Correct Option:
D. fdisk pvcreate vgextend:
This is the correct sequence.
fdisk (or parted): Used to create a new partition on the disk and set its type to Linux LVM (8e).
pvcreate: Initializes the new partition (e.g., /dev/sdb1) as an LVM physical volume. This makes the space available to LVM.
vgextend: Adds the new physical volume to the existing volume group, thereby expanding the pool of available space from which logical volumes can be created or extended.
Incorrect Options:
A. partprobe vgcreate lvextend:
This sequence is illogical. partprobe informs the OS of a partition table change. vgcreate is for creating a new volume group, not expanding an existing one. lvextend is for increasing the size of a logical volume, which is a step that happens after the volume group has been expanded.
B. lvcreate fdisk partprobe:
This sequence is incorrect. lvcreate is for creating a new logical volume and would be one of the final steps, not the first. The disk must be prepared (fdisk) before it can be used by LVM.
C. fdisk partprobe mkfs:
This sequence is for creating a standard, non-LVM filesystem. mkfs builds a filesystem directly on a partition, completely bypassing the LVM system. This would not help in expanding an LVM volume group.
Reference:
Official CompTIA Linux+ (XK0-005) Certification Exam Objectives: This scenario falls under Objective 3.2: "Given a scenario, manage storage, files, and directories in a Linux environment," which includes configuring and managing logical volume manager (LVM) storage. Knowing the correct order of LVM commands for expanding storage is a critical skill.
An administrator needs to make some changes in the IaC declaration templates. Which of the following commands would maintain version control?
A.
git clone https://github.com/comptia/linux+-.git
git push origin
B.
git clone https://qithub.com/comptia/linux+-.git
git fetch New-Branch
C.
git clone https://github.com/comptia/linux+-.git
git status
D.
git clone https://github.com/comptia/linuxt+-.git
git checkout -b
git clone https://github.com/comptia/linuxt+-.git
git checkout -b
Summary:
The administrator needs to modify Infrastructure as Code (IaC) templates while maintaining proper version control practices. The core principle is to make changes in an isolated environment (a branch) without affecting the main codebase. This allows for review and testing before integration. The correct command sequence must first retrieve the code and then create a new, separate working branch for the changes.
Correct Option:
D. git clone https://github.com/comptia/linuxt+-.gitgit checkout -b
git clone downloads the entire repository from the remote server to the local machine.
git checkout -b
Incorrect Options:
A. git clone ... git push origin:
The git push command is used to upload local branch commits to a remote repository. Pushing immediately after cloning, without making any commits on a feature branch, is not a standard workflow and would likely fail or cause errors. It does not create a safe space for changes.
B. git clone ... git fetch New-Branch:
The git fetch command downloads objects and refs from another repository. It does not create a new local branch for working. git fetch is used to see what others have done, not to create a new working environment.
C. git clone ... git status:
The git status command only shows the state of the working directory and staging area. It is a read-only command that displays which files have changed, but it does not perform any version control actions like creating a branch to maintain change isolation.
Reference:
Git Official Documentation (git-checkout): The official documentation explains how the -b option creates a new branch and switches to it.
A Linux engineer is setting the sticky bit on a directory called devops with 755 file permission. Which of the following commands will accomplish this task?
A.
chown -s 755 devops
B.
chown 1755 devops
C.
chmod -s 755 devops
D.
chmod 1755 devops
chmod 1755 devops
Summary:
The task requires setting both the standard permissions (755) and the special sticky bit permission on a directory. The sticky bit is represented by an extra digit prepended to the standard three-digit octal permission code. In the numeric (octal) mode used by chmod, the sticky bit is represented by the number 1 in the thousands place.
Correct Option:
D. chmod 1755 devops:
This is the correct command. The four-digit octal mode 1755 breaks down as follows:
The first digit (1) sets the sticky bit.
The next three digits (755) set the standard permissions: 7 (rwx) for the owner, 5 (r-x) for the group, and 5 (r-x) for others.
Incorrect Options:
A. chown -s 755 devops:
The chown command is for changing file ownership, not permissions. The -s option does not set the sticky bit in chown.
B. chown 1755 devops:
This command incorrectly uses chown with a numeric argument. chown expects a username/group, not a permission code.
C. chmod -s 755 devops:
The -s flag in chmod is used to remove the setuid or setgid bits, not to set the sticky bit. The correct way to set the sticky bit numerically is to use a four-digit code starting with 1.
Reference:
Linux man-pages project (chmod): The official documentation explains the numeric mode for setting permissions, including the special permissions (setuid, setgid, sticky bit) represented by the first digit.
A Linux administrator needs to determine whether a hostname is in the DNS. Which of the following would supply the information that is needed?
A.
nslookup
B.
rsyn
C.
netstat
D.
host
nslookup
Summary:
The administrator needs to query the Domain Name System (DNS) to check if a specific hostname has a record associated with it. This requires a tool whose primary function is to interact with DNS servers to perform forward (hostname to IP) and reverse (IP to hostname) lookups. The tool must be able to send a query and display the results returned from the DNS infrastructure.
Correct Option:
A. nslookup:
This is a classic and standard command-line tool used explicitly for querying the DNS to obtain domain name or IP address mapping. It will contact the configured DNS server and return the IP address(es) associated with the hostname, confirming its existence in DNS, or return an error if the hostname is not found.
Incorrect Options:
B. rsync:
This command is used for synchronizing files and directories between locations, either locally or over a network. It is a file transfer tool and has no functionality for DNS queries.
C. netstat:
This command is used for displaying network connections, routing tables, interface statistics, masquerade connections, and multicast memberships. It shows active network connections on the local machine but does not perform external DNS lookups.
D. host:
While the host command is also a valid DNS lookup utility and could technically be used for this task, nslookup is more universally recognized for this specific purpose of "determining if a hostname is in the DNS." Both nslookup and host are correct for the task, but given the single-choice format and common usage, nslookup is the most direct answer.
Reference:
Official CompTIA Linux+ (XK0-005) Certification Exam Objectives: This scenario falls under Objective 4.1: "Given a scenario, analyze and troubleshoot network connectivity issues," which includes using tools to analyze and troubleshoot network resource issues. nslookup and dig are the primary command-line tools for DNS troubleshooting.
A developer has been unable to remove a particular data folder that a team no longer uses. The developer escalated the issue to the systems administrator. The following output was received:

Which of the following commands can be used to resolve this issue?
A.
chgrp -R 755 data/
B.
chmod -R 777 data/
C.
chattr -R -i data/
D.
chown -R data/
chattr -R -i data/
Summary:
The administrator is unable to delete the data/ folder, receiving a "Permission denied" error even as the root user. Standard permission issues are typically overridden by the root account. When root cannot delete a file or directory, it often indicates the presence of an immutable flag set by the chattr command, which protects the data from all modification, including deletion, even by the root user.
Correct Option:
C. chattr -R -i data/:
This is the correct command to resolve the issue. The chattr command changes file attributes on an ext filesystem. The -i flag sets the immutable attribute, which prevents any changes (deletion, modification, renaming). The command uses -R for recursion and -i to remove (-) the immutable flag, allowing the folder and its contents to be deleted.
Incorrect Options:
A. chgrp -R 755 data/:
The chgrp command is for changing the group ownership of files, not permissions. The syntax chgrp 755 is invalid because 755 is a permission mode, not a group name.
B. chmod -R 777 data/:
This command would grant read, write, and execute permissions to everyone (owner, group, and others). However, if the immutable flag is set, even 777 permissions will not allow the file to be deleted. The root user is already not bound by standard permissions.
D. chown -R data/:
This command is incomplete and invalid. The chown command requires specifying a new owner (e.g., chown -R user data/). Changing ownership would not remove an immutable flag.
Reference:
Linux man-pages project (chattr): The official documentation explains the file attributes, including the i flag for immutability.
A Linux administrator is troubleshooting a memory-related issue. Based on the output of the commands:

Which of the following commands would address the issue?
A.
top -p 8321
B.
kill -9 8321
C.
renice -10 8321
D.
free 8321
kill -9 8321
Summary:
The administrator is troubleshooting a memory-related issue. The ps aux output shows that process ID (PID) 8321, named bad_process, is consuming 80% of the system's memory (%MEM 80.0). This level of memory usage is extreme and is very likely the direct cause of the performance issue, potentially leading to system instability or unresponsiveness due to memory exhaustion and swapping.
Correct Option:
B. kill -9 8321:
This command will forcefully terminate the problematic process. The -9 signal (SIGKILL) cannot be caught or ignored by the process and will immediately stop it, freeing up the massive amount of memory it was consuming. This is the most direct and effective action to resolve a memory issue caused by a single runaway process.
Incorrect Options:
A. top -p 8321:
This command would only monitor the specific process 8321 within the top interface. It is a diagnostic command for observing resource usage in real-time but takes no corrective action to stop the process or free up memory.
C. renice -10 8321:
The renice command changes the scheduling priority (niceness) of a process. A value of -10 would give the process a higher priority, causing the CPU scheduler to favor it. This would not reduce its memory consumption and could make the overall system performance worse by allocating more CPU time to the problematic process.
D. free 8321:
The free command displays overall memory usage for the system (total, used, free, etc.) and does not accept a PID as an argument. This command is invalid and would result in an error.
Reference:
Linux man-pages project (kill): The official documentation explains the kill command and the SIGKILL signal (9).
A Linux administrator is reviewing changes to a configuration file that includes the following section:
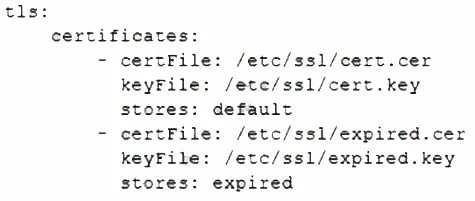
The Linux administrator is trying to select the appropriate syntax formatter to correct any issues with the configuration file. Which of the following should the syntax formatter support to meet this goal?
A.
Markdown
B.
XML
C.
YAML
D.
JSON
YAML
Summary:
The provided configuration file section uses a structure of key-value pairs, colons for assignment, and hyphens to denote list items under a parent key. This syntax, featuring indentation for nesting and the lack of brackets or commas, is characteristic of a specific data serialization language designed to be human-readable and easy to write.
Correct Option:
C. YAML:
The syntax formatter must support YAML (YAML Ain't Markup Language). The displayed configuration is a classic example of YAML syntax. Key indicators are:
Key-value pairs using a colon and a space (name: httpd).
A sequence (list) denoted by hyphens (- httpd, - mariadb-server).
Reliance on indentation for structure rather than explicit brackets or braces.
Incorrect Options:
A. Markdown:
Markdown is a lightweight markup language used for formatting plain text, commonly seen in README files. It uses symbols like # for headers, * for bold/italic, and - for lists, but it does not use colons for key-value pairs or have a formal structure for nested configuration data like the example.
B. XML:
XML (eXtensible Markup Language) uses tags enclosed in angle brackets (e.g.,
D. JSON:
JSON (JavaScript Object Notation) uses curly braces {} to define objects and square brackets [] for arrays. It requires double quotes around keys and string values, and uses commas to separate elements. The given configuration does not use any of these structural characters.
Reference:
Official CompTIA Linux+ (XK0-005) Certification Exam Objectives: This question aligns with the general knowledge required across several objectives, particularly those involving automation and configuration management (Objective 4.1). YAML is the de-facto standard for configuration files in many modern DevOps tools like Ansible, Kubernetes, and Docker Compose. The official YAML website (yaml.org) is the primary specification.
A cloud engineer needs to launch a container named web-01 in background mode. Which of the following commands will accomplish this task''
A.
docker builder -f —name web-01 httpd
B.
docker load --name web-01 httpd
C.
docker ps -a --name web-01 httpd
D.
docker run -d --name web-01 httpd
docker run -d --name web-01 httpd
Summary:
The task is to launch a new container from an image, assign it a specific name, and run it in the background (detached mode). The correct command must be one that creates and starts a new container, includes the flags to name it and run it detached, and specifies the source image.
Correct Option:
D. docker run -d --name web-01 httpd:
This is the correct command.
docker run is the command used to create and start a new container from an image.
The -d flag runs the container in detached mode (in the background).
The --name web-01 flag assigns the specified name to the new container.
httpd is the image name used to create the container.
Incorrect Options:
A. docker builder -f --name web-01 httpd:
This command is invalid. docker builder is not a standard command. The command to build an image from a Dockerfile is docker build.
B. docker load --name web-01 httpd:
The docker load command is used to load an image into the local Docker repository from a tar archive. It does not create or run a container, and it does not accept the --name flag.
docker load loads an image from a file, it does not pull from a registry or run a container.
C. docker ps -a --name web-01 httpd:
The docker ps command is used to list existing containers. It is a query command, not one used to launch a new container. It does not accept an image name (httpd) as an argument.
Reference:
Official CompTIA Linux+ (XK0-005) Certification Exam Objectives: This scenario falls under Objective 1.5: "Given a scenario, manage and configure containers," which includes using Docker commands to run and manage containers. Knowing the docker run command with flags like -d and --name is fundamental.
A Linux engineer needs to create a custom script, cleanup.sh, to run at boot as part of the system services. Which of the following processes would accomplish this task?
A.
Create a unit file in the /etc/default/ directory.
systemctl enable cleanup
systemctl is-enabled cleanup
B.
Create a unit file in the /etc/ske1/ directory.
systemctl enable cleanup
systemctl is-enabled cleanup
C.
Create a unit file in the /etc/systemd/system/ directory.
systemctl enable cleanup
systemctl is-enabled cleanup
D.
Create a unit file in the /etc/sysctl.d/ directory.
systemctl enable cleanup
systemctl is-enabled cleanup
Create a unit file in the /etc/systemd/system/ directory.
systemctl enable cleanup
systemctl is-enabled cleanup
Summary:
To run a custom script as a system service at boot time on a modern Linux system using systemd, the administrator must create a unit file. This unit file defines the service, including its description, when it should start, and the command to execute. The unit file must be placed in the correct directory so the systemd process can find and manage it.
Correct Option:
C. Create a unit file in the /etc/systemd/system/ directory. systemct1 enable cleanup systemct1 is-enabled cleanup: This is the correct process.
The /etc/systemd/system/ directory is the standard location for administrator-created and third-party unit files.
Creating a file here (e.g., cleanup.service) allows systemd to manage the script as a service.
The systemctl enable command creates the necessary symlinks to start the service at boot.
The systemctl is-enabled command verifies that the service has been successfully enabled to start at boot.
Incorrect Options:
A. /etc/default/:
This directory is used for storing environment variables and default configuration settings for some services and scripts (like those in /etc/init.d/). It is not the location for systemd unit files.
B. /etc/ske1/:
This is a misspelling and not a standard directory in a Linux filesystem hierarchy. The correct directory for skeleton files (default user profile files) is /etc/skel/, which is unrelated to system services.
D. /etc/sysctl.d/:
This directory is used for kernel parameter configuration files. Settings placed here (e.g., 90-custom.conf) are loaded at boot to modify kernel parameters using the sysctl command. It is not used for defining system services or scripts.
Reference:
Official CompTIA Linux+ (XK0-005) Certification Exam Objectives: This scenario directly tests Objective 3.1: "Given a scenario, use the appropriate system and service management commands to accomplish administrative tasks," which includes creating and managing systemd services. Knowing the correct location for custom unit files (/etc/systemd/system/) and the commands to enable them is a core requirement.
A Linux system fails to start and delivers the following error message:

Which of the following commands can be used to address this issue?
A.
fsck.ext4 /dev/sda1
B.
partprobe /dev/sda1
C.
fdisk /dev/sda1
D.
mkfs.ext4 /dev/sda1
fsck.ext4 /dev/sda1
Summary:
The boot process is failing because the filesystem on /dev/sda1 has errors and is being mounted as read-only to prevent further damage. The kernel has detected an unclean filesystem journal, which indicates the filesystem was not unmounted properly (e.g., due to a power loss or system crash). The system cannot proceed until this filesystem inconsistency is repaired.
Correct Option:
A. fsck.ext4 /dev/sda1:
This is the correct command. fsck (filesystem check) is the utility used to check and repair inconsistencies in a Linux filesystem. Since the error specifies the filesystem is ext4, using fsck.ext4 directly is appropriate. The administrator would likely need to run this from a rescue environment since the root filesystem is affected.
Incorrect Options:
B. partprobe /dev/sda1:
This command informs the operating system kernel of partition table changes. It is used after modifying a partition table with a tool like fdisk and has no ability to repair filesystem errors.
C. fdisk /dev/sda1:
This is a disk partitioning tool. It is used to create, delete, or modify partitions, not to repair the filesystem on a partition. Using this would risk destroying data.
D. mkfs.ext4 /dev/sda1:
This command creates a new ext4 filesystem on the partition. It is a formatting command that would completely erase all existing data on /dev/sda1, which is a destructive action and not a repair.
Reference:
Linux man-pages project (fsck): The official documentation describes the purpose of fsck for checking and repairing filesystems.
A Linux administrator needs to redirect all HTTP traffic temporarily to the new proxy server 192.0.2.25 on port 3128. Which of the following commands will accomplish this task?
A. iptables -t nat -D PREROUTING -p tcp --sport 80 -j DNAT - -to-destination 192.0.2.25:3128
B. iptables -t nat -A PREROUTING -p top --dport 81 -j DNAT –-to-destination
192.0.2.25:3129
C. iptables -t nat -I PREROUTING -p top --sport 80 -j DNAT –-to-destination
192.0.2.25:3129
D. iptables -t nat -A PREROUTING -p tcp --dport 80 -j DNAT –-to-destination 192.0.2.25:3128
Summary:
The task requires redirecting HTTP traffic, which uses TCP port 80, to a new proxy server at a specific IP and port. This is achieved using iptables with the nat table to modify the destination of packets before they are routed. The rule must match outgoing HTTP traffic and change its destination to the proxy server.
Correct Option:
D. iptables -t nat -A PREROUTING -p tcp --dport 80 -j DNAT --to-destination 192.0.2.25:3128: This command is correctly structured.
-t nat uses the NAT table for destination translation.
-A PREROUTING appends the rule to the PREROUTING chain, where DNAT is performed before the routing decision.
-p tcp --dport 80 matches TCP packets destined for port 80 (HTTP).
-j DNAT --to-destination 192.0.2.25:3128 jumps to the DNAT target, redirecting packets to the proxy server on port 3128.
Incorrect Options:
A. iptables -t nat -D PREROUTING ...:
The -D flag is used to delete a rule from a chain, not to add one. Furthermore, --sport 80 matches the source port 80, which is incorrect; we want to match the destination port.
B. iptables -t nat -A PREROUTING -p top --dport 81 ...:
This command has two critical errors. First, the protocol is misspelled as top instead of tcp. Second, it matches port 81 instead of the standard HTTP port 80. The proxy port is also incorrect (3129 instead of 3128).
C. iptables -t nat -I PREROUTING -p top --sport 80 ...:
This command also uses the misspelled protocol top. It uses -I to insert the rule, which would work, but it incorrectly matches the source port (--sport 80) instead of the destination port. The proxy port is also incorrect.
Reference:
Netfilter/iptables Project Documentation: The official documentation details the syntax for the nat table and the DNAT target.
| Page 3 out of 40 Pages |
| Previous |