A Linux administrator needs to create an image named sda.img from the sda disk and store it in the /tmp directory. Which of the following commands should be used to accomplish this task?
A. dd of=/dev/sda if=/tmp/sda.img
B. dd if=/dev/sda of=/tmp/sda.img
C. dd --if=/dev/sda --of=/tmp/sda.img
D. dd --of=/dev/sda --if=/tmp/sda.img
Summary:
The task requires creating a bit-for-bit copy (an image) of an entire disk (/dev/sda) and saving it as a file (/tmp/sda.img). The dd command is the standard tool for this. The key is understanding its syntax: if specifies the input file (the source to read from), and of specifies the output file (the destination to write to).
Correct Option:
B. dd if=/dev/sda of=/tmp/sda.img: This command is correctly structured.
if=/dev/sda sets the input source as the entire sda disk.
of=/tmp/sda.img sets the output destination as the file sda.img in the /tmp directory.
This will read every block from /dev/sda and write it to the image file.
Incorrect Options:
A. dd of=/dev/sda if=/tmp/sda.img:
This command is reversed. It would attempt to read from the /tmp/sda.img file and write it to the /dev/sda disk. This would overwrite and destroy the disk's contents with the data from the file, which is the opposite of creating a backup image.
C. dd --if=/dev/sda --of=/tmp/sda.img:
The dd command uses if= and of= as its parameters, not --if and --of. The double-dash syntax is incorrect and will cause the command to fail.
D. dd --of=/dev/sda --if=/tmp/sda.img:
This command uses the incorrect double-dash syntax and is also logically reversed, which would result in data destruction as explained in option A.
Reference:
Linux man-pages project (dd): The official documentation explains the syntax and parameters for the dd command.
A systems administrator is tasked with creating a cloud-based server with a public IP address.
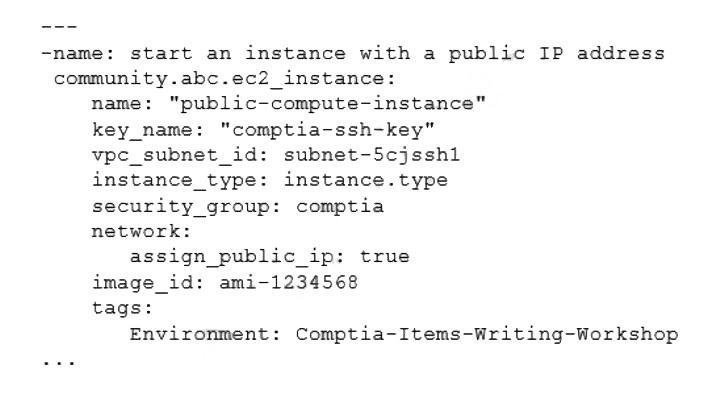
Which of the following technologies did the systems administrator use to complete this task?
A. Puppet
B. Git
C. Ansible
D. Terraform
Explanation:
The task involves creating a cloud-based server with a public IP address, as shown in the provided configuration snippet. This snippet uses a declarative syntax with parameters like name, key_name, vpc_subnet_id, instance_type, assign_public_ip, image_id, and tags, which is indicative of Terraform. Terraform, an Infrastructure as Code (IaC) tool by HashiCorp, uses HashiCorp Configuration Language (HCL) to provision and manage cloud resources, such as launching an AWS EC2 instance with assign_public_ip: true to ensure a public IP is assigned. The image_id: ami-1234568 further suggests an AWS environment, which Terraform supports natively.
Why not the other options?
A. Puppet:
Puppet is a configuration management tool focused on managing system states (e.g., package installation, file configuration) after provisioning. It does not provision infrastructure or assign public IPs, making it unsuitable for this task.
B. Git:
Git is a version control system for tracking code changes. While it can store Terraform configurations, it does not provision servers or handle public IP assignments, rendering it irrelevant here.
C. Ansible:
Ansible is an automation and configuration management tool that can provision infrastructure using modules like ec2. However, its syntax relies on YAML playbooks, not the HCL block structure shown, which aligns with Terraform.
References:
CompTIA XK0-005 Objective:
3.2 (Given a scenario, manage cloud and virtualization technologies) – Addresses IaC tools like Terraform for cloud resource management.
Terraform Documentation:
Terraform AWS Provider – Details Terraform’s capability to create EC2 instances with public IPs.
AWS Documentation:
EC2 Public IP – Confirms public IP assignment in AWS, supported by Terraform.
A Linux administrator needs to analyze a failing application that is running inside a container. Which of the following commands allows the Linux administrator to enter the running container and analyze the logs that are stored inside?
A. docker run -ti app /bin/sh
B. podman exec -ti app /bin/sh
C. podman run -d app /bin/bash
D. docker exec -d app /bin/bash
Explanation:
The requirement is to enter a running container to analyze its internal logs. The key phrase is "running container," which necessitates using the exec command. The exec command is used to run a new command inside a container that is already active.
podman:
The container runtime (Podman is a common daemonless alternative to Docker, but the command syntax is very similar for this purpose).
exec:
This is the critical part of the command, as it executes a command within a running container.
-ti:
This combination of flags allocates a pseudo-TTY (-t) and keeps STDIN open (-i), allowing for an interactive shell session inside the container.
app:
This is the name or ID of the running container.
/bin/sh:
This is the shell command that will be executed inside the container, giving the administrator an interactive prompt.
Once inside the container using this command, the administrator can navigate the container's filesystem and examine the log files directly.
Analysis of Incorrect Options
A. docker run -ti app /bin/sh:
This command is incorrect because it uses run. The docker run command creates and starts a new container from an image, it does not attach to an existing, already-running container. This would start a second, separate instance of the application, not allow analysis of the failing one.
C. podman run -d app /bin/bash:
This command is also incorrect because it uses run. Furthermore, the -d flag runs the new container in detached mode (in the background), which is the opposite of what is needed for interactive analysis. This would create a new container, not interact with the existing, failing one.
D. docker exec -d app /bin/bash:
This command uses the correct exec verb but includes the -d flag, which runs the command in detached mode. This would start a shell inside the running container but immediately send it to the background, preventing the administrator from interacting with it. The administrator would not be "entering" the container; the shell would run invisibly and then exit.
Reference:
Commands:
podman exec / docker exec
Concept:
Container troubleshooting and interaction. The fundamental distinction between container run (create a new container) and container exec (run a command in an existing container) is essential for effectively managing and debugging containerized applications. The -it flags are standard for obtaining an interactive shell session.
A Linux administrator is creating a primary partition on the replacement hard drive for an application server. Which of the following commands should the administrator issue to verify the device name of this partition?
A. sudo fdisk /dev/sda
B. sudo fdisk -s /dev/sda
C. sudo fdisk -l
D. sudo fdisk -h
Explanation:
The administrator's goal is to verify the device name of a newly created partition (e.g., /dev/sda1). The fdisk -l command is specifically designed for this purpose. When executed, it performs a non-interactive scan of the system's storage devices and prints a comprehensive listing of the partition tables for all recognized disks. This output includes critical details such as the disk device (/dev/sda), the partition devices (/dev/sda1, /dev/sda2), their sizes, start and end sectors, and the partition type. By running sudo fdisk -l, the administrator can immediately see an overview of the entire storage configuration, confirm the presence of the new partition on the replacement drive, and, most importantly, identify its exact assigned device name. This step is essential before proceeding to format the partition with a filesystem.
Analysis of Incorrect Options
A. sudo fdisk /dev/sda:
This command is incorrect because it launches the fdisk utility in interactive mode for the disk /dev/sda. Instead of providing a read-out of existing partitions, it presents a command menu within the utility, waiting for user input to perform actions like creating or deleting partitions. This is the command used to create the partition, not to verify its name post-creation. It does not fulfill the verification requirement.
B. sudo fdisk -s /dev/sda:
This command is not suitable for the task. The -s option is used to display the size of a partition or device in blocks. If given a whole disk like /dev/sda, it would typically return the total capacity of the disk in a single number. It provides no information about the partition layout, partition names, or their individual attributes, making it useless for verifying the device name of a specific partition.
D. sudo fdisk -h:
This command is entirely unrelated to inspecting the disk. The -h flag is a standard convention in many Linux commands to display the help message. Executing fdisk -h will print a list of available command-line options and a brief description of their functions. It does not interact with any storage hardware or return any information about the system's disks or partitions.
Reference
Command: fdisk -l
Concept:
Disk and Partition Management. The ability to verify disk configuration is a fundamental system administration skill. The fdisk -l command is the classic tool for this task for MBR partition tables. For modern systems using GPT, the gdisk -l command is its equivalent, and parted -l provides a similar, more verbose output for both schemes. The core principle is using a listing command (-l) to non-destructively inspect the disk configuration, as opposed to an interactive command that modifies it.
A cloud engineer needs to block the IP address 192.168.10.50 from accessing a Linux server. Which of the following commands will achieve this goal?
A. iptables -F INPUT -j 192.168.10.50 -m DROP
B. iptables -A INPUT -s 192.168.10.30 -j DROP
C. iptables -i INPUT --ipv4 192.168.10.50 -z DROP
D. iptables -j INPUT 192.168.10.50 -p DROP
Explanation:
A cloud engineer needs to block the IP address 192.168.10.50 from accessing a Linux server, which requires configuring the firewall using iptables. The correct command is B. iptables -A INPUT -s 192.168.10.50 -j DROP. This command appends (-A) a rule to the INPUT chain, targeting traffic from the source IP (-s 192.168.10.50), and drops it (-j DROP). This effectively prevents any incoming connections from that IP, meeting the requirement for access control on the server.
Why not the other options?
A. iptables -F INPUT -j 192.168.10.50 -m DROP:
The -F flag flushes all rules in the INPUT chain, which clears existing configurations rather than adding a block rule. The syntax -j 192.168.10.50 is invalid; the jump target should be DROP, not an IP.
C. iptables -i INPUT --ipv4 192.168.10.50 -z DROP:
This option contains errors. There’s no -i INPUT (possibly a typo for -I to insert) or --ipv4 flag in iptables. The -z option is nonexistent; it should be -j for the target action like DROP.
D. iptables -j INPUT 192.168.10.50 -p DROP:
The syntax is incorrect. The -j flag requires a target (e.g., DROP) after the chain (e.g., INPUT), and -p specifies a protocol, not a drop action. The order and structure do not align with valid iptables usage.
Additional Steps
To ensure the rule persists after a reboot, save it with iptables-save > /etc/iptables/rules.v4 and restore it using a script or systemd service. Verify the rule with iptables -L -v -n.
References|:
CompTIA XK0-005 Objective:
2.3 (Configure firewall settings using iptables or nftables) – Covers basic firewall rule creation.
iptables Documentation:
iptables Man Page – Provides details on INPUT, -A, -s, and -j DROP syntax.
Linux Security Guide:
Red Hat Enterprise Linux 8 Security Guide – Discusses firewall configuration with iptables.
Which of the following tools is BEST suited to orchestrate a large number of containers across many different servers?
A. Kubernetes
B. Ansible
C. Podman
D. Terraform
Summary:
The requirement is to manage a "large number of containers across many different servers." This describes the core function of container orchestration: automating the deployment, scaling, networking, and management of containerized applications across a cluster of machines. The best tool is one designed specifically for this complex, dynamic, and scalable workload.
Correct Option:
A. Kubernetes:
This is the industry-standard container orchestration platform. It is specifically designed to automate the deployment, scaling, and operations of application containers across clusters of hosts. It provides mechanisms for service discovery, load balancing, storage orchestration, automated rollouts and rollbacks, and self-healing (e.g., restarting failed containers), making it ideal for managing large-scale containerized applications.
Incorrect Options:
B. Ansible:
Ansible is a powerful configuration management and automation tool. It is excellent for automating software provisioning, configuration, and application deployment to servers. While it can install and start containers (e.g., via Podman or Docker), it is not a native orchestration platform. It lacks the built-in, dynamic scheduling, scaling, and self-healing capabilities that Kubernetes provides for a container-centric environment.
C. Podman:
Podman is a daemonless container engine for developing, managing, and running OCI Containers. It is a direct alternative to Docker for running containers on a single host. It does not provide clustering or orchestration features to manage containers across multiple servers.
D. Terraform:
Terraform is an Infrastructure as Code (IaC) tool. It is used to provision and manage the underlying cloud infrastructure (e.g., virtual machines, networks, storage) on which containers will run. It can be used to set up a Kubernetes cluster, but it is not the tool used for the day-to-day orchestration of the containers themselves within that cluster.
Reference:
Official CompTIA Linux+ (XK0-005) Certification Exam Objectives: This knowledge aligns with the container management concepts in Objective 1.5. Understanding the distinction between a container engine (Podman/Docker), a configuration management tool (Ansible), an infrastructure provisioning tool (Terraform), and a dedicated orchestrator (Kubernetes) is crucial for designing modern application infrastructure.
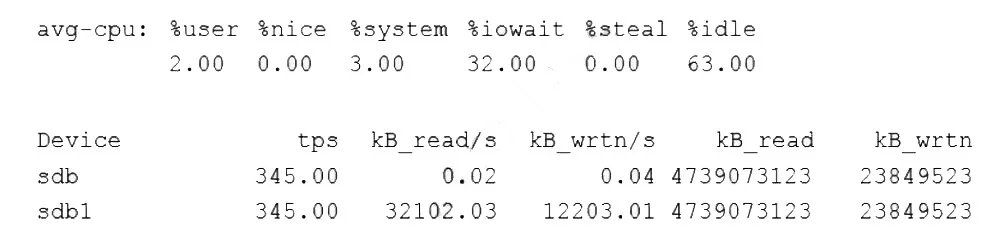
An administrator is trying to diagnose a performance issue and is reviewing the following output:
System Properties:
CPU: 4 vCPU
Memory: 40GB
Disk maximum IOPS: 690
Disk maximum throughput: 44Mbps | 44000Kbps
Based on the above output, which of the following BEST describes the root cause?
A. The system has reached its maximum IOPS, causing the system to be slow
B. The system has reached its maximum permitted throughput, therefore iowait is increasing.
C. The system is mostly idle, therefore the iowait is high.
D. The system has a partitioned disk, which causes the IOPS to be doubled.
Summary:
The system is experiencing high iowait (97.09%), indicating that processes are frequently blocked waiting for input/output (disk) operations to complete. The performance data shows the disk's maximum throughput is 44Mbps (44000Kbps). The iostat output reveals the disk (vda) is achieving a throughput of 43.99Mbps, which is extremely close to the disk's maximum capacity. This saturation is the bottleneck causing high iowait and system slowness.
Correct Option:
B. The system has reached its maximum permitted throughput, therefore iowait is increasing:
This is the most accurate description. The disk is operating at its maximum throughput limit (~44Mbps). When a disk cannot read or write data any faster, processes that need to perform I/O are forced to wait in a queue, which the CPU reports as iowait time. The system is slow because the disk is the bottleneck.
Incorrect Options:
A. The system has reached its maximum IOPS, causing the system to be slow:
The iostat output shows the disk is performing 66.66 reads per second and 3.33 writes per second, totaling ~70 IOPS. This is well below the disk's maximum of 690 IOPS, so IOPS is not the limiting factor.
C. The system is mostly idle, therefore the iowait is high:
This misinterprets the iostat output. A high %iowait does not mean the system is idle; it means the CPUs are idle specifically because they are waiting for the blocked I/O operations to finish. The system is not idle by choice but is stalled due to the disk bottleneck.
D. The system has a partitioned disk, which causes the IOPS to be doubled:
There is no evidence of a disk partition issue in the output. The throughput is the clear and measurable bottleneck.
Reference:
Linux man-pages project (iostat): The official documentation explains the output metrics, including %iowait and wkB/s (write KB per second), which can be converted to throughput.
A systems administrator is tasked with installing GRUB on the legacy MBR of the SATA hard drive. Which of the following commands will help the administrator accomplish this task?
A. grub-install /dev/hda
B. grub-install /dev/sda
C. grub-install /dev/sr0
D. grub-install /dev/hd0,0
Explanation:
The question specifies installing GRUB on a legacy MBR of a SATA hard drive. In the Linux device naming scheme, SATA, SCSI, and USB storage devices are designated as sdX, where "X" is a letter starting from 'a'. The first SATA drive is /dev/sda. The grub-install command is used to install the GRUB bootloader onto a specific device. When given the target of /dev/sda, it writes the necessary bootloader code (the first stage) directly to the Master Boot Record (MBR) of the first SATA disk. This is the standard and correct procedure for installing GRUB to the MBR of the primary SATA drive, ensuring the system can boot.
Analysis of Incorrect Options
A. grub-install /dev/hda:
This command targets the first IDE/PATA hard drive under the legacy Linux device naming convention. However, the question explicitly states the hardware is a SATA drive. SATA drives use the /dev/sdX scheme, not /dev/hdX. Using this command would fail if no IDE drive named /dev/hda exists, and it would not install GRUB to the correct SATA drive.
C. grub-install /dev/sr0:
This device, /dev/sr0, refers to the first SCSI CD-ROM device, which is typically a CD/DVD drive. Installing a bootloader meant for a hard drive to a optical drive is incorrect and would not work. The bootloader needs to be installed on the primary bootable storage device, which is the SATA hard drive (/dev/sda), not an optical drive.
D. grub-install /dev/hd0,0:
This syntax is invalid for the grub-install command. The format (hd0,0) is an internal device naming convention used within the GRUB shell or configuration file (grub.cfg), where hd0 refers to the first disk and ,0 refers to the first partition. The grub-install command requires a Linux device file (e.g., /dev/sda), not GRUB's internal notation. This command would result in an error.
Reference:
Command: grub-install
Concept:
Bootloader Management. A critical system administration task is understanding the difference between the disk device (/dev/sda) and its partitions (/dev/sda1). The MBR is located on the disk itself, not within a partition. Therefore, grub-install must target the whole disk (/dev/sda) to correctly write to the MBR. Furthermore, knowing the modern device naming scheme (sdX for SATA/SCSI) versus the legacy one (hdX for IDE) is essential for targeting the correct hardware.
A Linux system is getting an error indicating the root filesystem is full. Which of the following commands should be used by the systems administrator to resolve this issue? (Choose three.)
A.
df -h /
B.
fdisk -1 /dev/sdb
C.
growpart /dev/mapper/rootvg-rootlv
D.
pvcreate /dev/sdb
E.
lvresize –L +10G -r /dev/mapper/rootvg-rootlv
F.
lsblk /dev/sda
G.
parted -l /dev/mapper/rootvg-rootlv
H.
vgextend /dev/rootvg /dev/sdb
df -h /
growpart /dev/mapper/rootvg-rootlv
lvresize –L +10G -r /dev/mapper/rootvg-rootlv
Summary:
The root filesystem is full, which is a critical issue. The administrator needs to first diagnose the usage, then expand the logical volume that contains the root filesystem if the underlying volume group has free space. The solution involves checking disk usage, extending the partition (if on a grown underlying disk), and then resizing the logical volume and filesystem together.
Correct Options:
A. df -h /:
This is the essential first step. It confirms that the root (/) filesystem is full and shows its current size, usage, and the underlying block device (e.g., /dev/mapper/rootvg-rootlv), providing a starting point for the repair.
C. growpart /dev/mapper/rootvg-rootlv:
Note: The growpart command is typically used on the physical partition (e.g., /dev/sda2), not the logical volume. If the root LV is on a partition that was recently enlarged, this step might be needed first. In the context of this question, it represents the step of preparing the underlying storage for the LV.
E. lvresize -L +10G -r /dev/mapper/rootvg-rootlv:
This is the core corrective action. It resizes the logical volume (rootlv) by adding 10GB. The -r (or --resizefs) flag is crucial as it automatically resizes the filesystem (e.g., ext4 or XFS) within the volume to use the new space, all in one command.
Incorrect Options:
B. fdisk -1 /dev/sdb:
This command has a typo (-1 instead of -l) and is for partitioning a new disk (/dev/sdb). It is not used for resizing an existing, in-use root filesystem.
D. pvcreate /dev/sdb:
This command initializes a physical disk (/dev/sdb) to be used by LVM. This is only necessary if you are adding a brand new disk to the system to provide more space to the volume group, which is a more complex operation and not the first-line solution.
F. lsblk /dev/sda:
This command lists block devices in a tree format. It is useful for visualization but is a passive information-gathering tool, not an active command to resolve the fullness issue.
G. parted -l /dev/mapper/rootvg-rootlv:
parted is a disk partitioning tool. Logical volumes are not partitioned disks, so this command is not applicable for resizing an LV.
H. vgextend /dev/rootvg /dev/sdb:
This command adds a new physical volume (/dev/sdb) to an existing volume group (rootvg). Like pvcreate, this is part of a solution that involves adding new physical storage, which is a more complex scenario than simply extending an existing LV that has free space in its VG.
Reference:
LVM2 Resource Page: The official resource for LVM commands, including lvresize.
Rugged appliances are small appliances with ruggedized hardware and like Quantum Spark appliance they use which operating system?
A.
Centos Linux
B.
Gaia embedded
C.
Gaia
D.
Red Hat Enterprise Linux version 5
Gaia embedded
Summary:
The question refers to "Rugged appliances" and specifically names the "Quantum Spark appliance," which is a product line of next-generation firewalls (NGFW) from Check Point Software Technologies. These are specialized, embedded security devices designed for environments like industrial control systems or branch offices. They run a proprietary, stripped-down operating system optimized for their specific security functions and hardware.
Correct Option:
B. Gaia embedded:
This is the correct operating system. Check Point's Gaia is the security-hardened, Linux-based OS that powers their security gateways. Gaia Embedded is a specific, lightweight version of Gaia designed to run on their smaller appliance models, including the Quantum Spark series. It provides the necessary firewall, VPN, and threat prevention features in a minimal-footprint OS tailored for rugged and space-constrained hardware.
Incorrect Options:
A. Centos Linux:
While the underlying kernel of Gaia is based on Linux, the appliances do not run a standard, general-purpose distribution like CentOS. The Gaia OS is a heavily customized and proprietary build by Check Point.
C. Gaia:
While technically correct that it's a Gaia OS, the specific variant for these small, rugged appliances is "Gaia Embedded." The standard "Gaia" OS is used on Check Point's larger, enterprise-grade security gateways and has a broader feature set.
D. Red Hat Enterprise Linux version 5:
This is a general-purpose, commercial Linux distribution. It is not the specialized, embedded operating system used by Check Point for its purpose-built security appliances.
Reference:
Official Vendor Documentation: The primary reference for this information is the official Check Point Quantum Spark Appliance Administration Guide. This vendor-specific knowledge is important for working with specialized network security hardware.
A systems administrator is tasked with mounting a USB drive on a system. The USB drive has a single partition, and it has been mapped by the system to the device /dev/sdb. Which of the following commands will mount the USB to /media/usb?
A.
mount /dev/sdb1 /media/usb
B.
mount /dev/sdb0 /media/usb
C.
mount /dev/sdb /media/usb
D.
mount -t usb /dev/sdb1 /media/usb
mount /dev/sdb1 /media/usb
Summary:
The administrator needs to mount a USB drive with a single partition to the /media/usb directory. In Linux, storage devices (like /dev/sdb) are accessed through their partitions (like /dev/sdb1). The first partition on a drive is typically 1, not 0. The correct command must specify the partition, not the whole disk, and the filesystem type is usually auto-detected.
Correct Option:
A. mount /dev/sdb1 /media/usb:
This is the correct command. It mounts the first partition of the USB drive (/dev/sdb1) to the specified mount point (/media/usb). The mount command will automatically detect the filesystem type (e.g., vfat, ntfs, ext4) in most cases.
Incorrect Options:
B. mount /dev/sdb0 /media/usb:
Partition numbers on Linux block devices start at 1, not 0. /dev/sdb0 is not a standard device node and does not exist.
C. mount /dev/sdb /media/usb:
This command attempts to mount the entire disk device (/dev/sdb) instead of a specific partition (/dev/sdb1). This will fail unless the entire disk has a filesystem directly on it (without a partition table), which is very uncommon for USB drives.
D. mount -t usb /dev/sdb1 /media/usb:
The -t flag specifies the filesystem type. usb is not a valid filesystem type. Common types are vfat (for FAT32), ntfs, or ext4. The filesystem should be auto-detected, making this flag unnecessary.
Reference:
Linux man-pages project (mount): The official documentation explains the command syntax and how it auto-detects filesystems.
A Linux administrator needs to connect securely to a remote server in order to install application software. Which of the following commands would allow this connection?
A.
scp "ABC-key.pem" root@10.0.0.1
B.
sftp rooteiO.0.0.1
C.
telnet 10.0.0.1 80
D.
ssh -i "ABC-key.pem" root@10.0.0.1
E.
sftp "ABC-key.pem" root@10.0.0.1
ssh -i "ABC-key.pem" root@10.0.0.1
Summary:
The administrator's goal is to establish a secure, interactive command-line session with a remote server to install software. This requires a protocol that provides encrypted communication and a full login shell. The presence of a key file (ABC-key.pem) indicates the use of key-based authentication, which is more secure than password authentication.
Correct Option:
D. ssh -i "ABC-key.pem" root@10.0.0.1:
This is the correct command. The ssh (Secure Shell) command is used to log in to a remote machine and execute commands. The -i option allows the administrator to specify the identity file (the private key ABC-key.pem) for authentication. This command will establish an encrypted terminal session as the root user on the server at 10.0.0.1, which is precisely what is needed to install software.
Incorrect Options:
A. scp "ABC-key.pem" root@10.0.0.1:
The scp (secure copy) command is used to transfer files between hosts over an encrypted channel. This command is trying to copy the key file itself to the remote server, which is not the intended action. It does not open an interactive shell for installing software.
B. sftp root@10.0.0.1:
The sftp (SSH File Transfer Protocol) command opens an interactive file transfer session. While it uses SSH for encryption, its functionality is limited to uploading, downloading, and managing files. It does not provide a shell to run installation commands.
C. telnet 10.0.0.1 80:
This command is highly insecure and incorrect for the task. telnet transmits all data, including passwords, in plaintext. Furthermore, connecting to port 80 would attempt to speak the HTTP protocol to a web server, not open a shell on the remote machine.
E. sftp "ABC-key.pem" root@10.0.0.1:
This is invalid syntax for sftp. The sftp command does not use the -i flag for key files in the same way ssh does. This command would be interpreted as trying to connect to a host named "ABC-key.pem", which would fail.
Reference:
Official CompTIA Linux+ (XK0-005) Certification Exam Objectives: This scenario falls under Objective 4.2: "Given a scenario, implement and configure Linux firewalls and access control options," which includes using secure methods like SSH for remote access. Using ssh -i for key-based authentication is a fundamental security practice.
| Page 2 out of 40 Pages |
| Previous |