A systems administrator is enabling LUKS on a USB storage device with an ext4 filesystem format. The administrator runs dmesg and notices the following output:

Given this scenario, which of the following should the administrator perform to meet these requirements? (Select three).
A. gpg /dev/sdcl
B. pvcreate /dev/sdc
C. mkfs . ext4 /dev/mapper/LUKSCJ001 - L ENCRYPTED
D. umount / dev/ sdc
E. fdisk /dev/sdc
F. mkfs . vfat /dev/mapper/LUKS0001 — L ENCRYPTED
G. wipefs —a/dev/sdbl
H. cryptsetup IuksFormat /dev/ sdcl
Summary:
The administrator needs to encrypt a USB storage device using LUKS. The dmesg output shows the device was detected as /dev/sdc1 and is currently mounted. The correct procedure involves unmounting the device, formatting it with LUKS encryption, creating a filesystem on the encrypted mapper device, and then mounting the mapper device to use it.
Correct Options:
D. umount /dev/sdc1:
This is the first and essential step. The filesystem must be unmounted before it can be encrypted or have its partition table modified. The dmesg output shows it was mounted at /run/media/root/ENCRYPTED.
H. cryptsetup luksFormat /dev/sdc1:
This command initializes the partition (/dev/sdc1) and creates the LUKS encryption header. It formats the partition as a LUKS volume, which will prompt for a passphrase to secure the volume.
C. mkfs.ext4 /dev/mapper/LUKS0001 -L ENCRYPTED:
After the LUKS container is created and opened (which creates a mapper device like /dev/mapper/LUKS0001), a filesystem must be created inside the encrypted container. This command creates an ext4 filesystem on the mapper device, meeting the requirement for an ext4 format. The -L flag labels the filesystem "ENCRYPTED".
Incorrect Options:
A. gpg /dev/sdc1:
GPG is used for file encryption, not for full-disk or partition encryption like LUKS.
B. pvcreate /dev/sdc:
This command is for LVM (Logical Volume Manager) to initialize a physical volume, not for LUKS encryption.
E. fdisk /dev/sdc:
While fdisk could be used to manage partitions, the dmesg output already shows a valid partition (/dev/sdc1). Repartitioning is not necessary for LUKS; it can use an existing partition.
F. mkfs.vfat /dev/mapper/LUKS0001 -L ENCRYPTED:
This would create a VFAT filesystem, but the requirement specifies an ext4 filesystem.
G. wipefs -a /dev/sdb1:
This command wipes filesystem signatures. The device in question is /dev/sdc1, not /dev/sdb1. More importantly, the cryptsetup luksFormat command will overwrite the necessary areas, making this a redundant and potentially dangerous step if pointed at the wrong device.
Reerence:
Official CompTIA Linux+ (XK0-005) Certification Exam Objectives: This scenario falls under Objective 3.2: "Given a scenario, manage storage, files, and directories in a Linux environment," which includes implementing and configuring encrypted storage. The cryptsetup command is the standard tool for managing LUKS encryption.
A User on a Linux workstation needs to remotely start an application on a Linux server and then forward the graphical display of that application back to the Linux workstation. Which of the following would enable the user to perform this action?
A. ssh -X user@server application
B. ssh -y user@server application
C. ssh user@server application
D. ssh -D user@server application
Summary:
A user needs to run a graphical application on a remote server but have the application's windows displayed on their local workstation. This requires a technology called "X11 forwarding," which tunnels the graphical data from the remote X server (on the application machine) to the local X server (on the user's workstation) over the secure SSH connection. The SSH client has a specific option to enable this feature.
Correct Option:
A. ssh -X user@server application:
This is the correct command. The -X option enables trusted X11 forwarding. When the user runs this command and starts a graphical application on the remote server, the application's windows will securely open and display on the user's local desktop.
Incorrect Options:
B. ssh -Y user@server application:
The -Y option enables trusted X11 forwarding, which is less secure than -X because it bypasses some of the X11 security extensions. While it would work, it is not the default or recommended option due to potential security implications. The standard and safer option is -X.
C. ssh user@server application:
This command will log in to the server and run the application, but it will not forward the graphical display. If the application is graphical, it will likely fail with an error because it cannot find a display.
D. ssh -D user@server application:
The -D option is used to set up a dynamic application-level port forwarding (a SOCKS proxy). It is used for tunneling web traffic and other protocols, not for forwarding X11 graphical applications.
Reference:
Official CompTIA Linux+ (XK0-005) Certification Exam Objectives: This scenario falls under Objective 4.2: "Given a scenario, implement and configure Linux firewalls and access control options," which includes using secure methods like SSH for remote access. X11 forwarding (-X) is a specific and common feature of SSH for remote graphical application management.
A systems administrator is tasked with changing the default shell of a system account in order to disable iterative logins. Which of the following is the best option for the administrator to use as the new shell?
A. /sbin/nologin
B. /bin/ sh
C. /sbin/ setenforce
D. /bin/bash
Summary:
This question involves modifying a system account on a Linux system to disable iterative logins, requiring the systems administrator to change the default shell. The task focuses on selecting a shell that prevents login access while maintaining system integrity, typically used for security purposes on accounts that shouldn’t allow interactive sessions, such as service accounts.
Correct Option:
A. /sbin/nologin
The /sbin/nologin shell prevents users from logging in interactively, displaying a message and terminating the session, which aligns with disabling iterative logins.
It’s designed for system accounts (e.g., nobody) that need to exist but not allow user access, making it the best choice for this security requirement.
The change can be made with usermod -s /sbin/nologin username.
Incorrect Option:
B. /bin/sh
The /bin/sh shell (often a symlink to another shell like bash) allows interactive logins, which contradicts the goal of disabling them.
This would enable the user to log in, making it an unsuitable option.
C. /sbin/setenforce
The /sbin/setenforce command is used to manage SELinux enforcement modes, not a shell, and cannot be set as a user’s default shell.
Attempting to use it would result in login failures or errors, rendering it incorrect.
D. /bin/bash
The /bin/bash shell is a full-featured interactive shell, allowing users to log in and execute commands.
Setting this as the default shell would enable iterative logins, which is the opposite of the desired outcome.
Reference:
https://www.comptia.org/training/resources/exam-objectives (CompTIA Linux+ XK0-005 objectives)
A systems administrator creates a public key for authentication. Which of the following tools is most suitable to use when uploading the key to the remote servers?
A. scp
B. ssh-copy-id
C. ssh-agent
D. ssh-keyscan
Summary:
A systems administrator has created a public key for authentication and needs to upload it to remote servers for SSH access. The tool must securely transfer and append the public key to the remote user's ~/.ssh/authorized_keys file. The ideal tool should automate this process while ensuring proper permissions and security.
Correct Option:
B. ssh-copy-id
ssh-copy-id securely copies the local public key to the remote server's ~/.ssh/authorized_keys file.
It handles key installation, sets correct permissions (e.g., 600 for .ssh, 644 for authorized_keys), and prompts for the remote password if needed.
This is the most suitable and user-friendly tool for this task.
Incorrect Option:
A. scp
scp (secure copy) transfers files but requires manual placement of the key into ~/.ssh/authorized_keys and permission adjustments, making it less efficient and error-prone for this purpose.
C. ssh-agent
ssh-agent manages private keys for authentication but does not upload public keys to remote servers. It’s used locally to handle key usage, not key distribution.
D. ssh-keyscan
ssh-keyscan retrieves a remote host's public key for verification but does not upload the local public key to the server, making it unsuitable for this task.
Reference:
CompTIA XK0-005 exam objectives: https://www.comptia.org/certifications/linux
(Red Hat SSH configuration: https://access.redhat.com/documentation)
Which of the following directories contains binaries that only a root user should run?
A. /sbin
B. /bin
C. /root
D. /lib
Summary:
The administrator needs to identify the directory containing binaries intended exclusively for the root user. Linux uses specific directories to organize system files, with some reserved for administrative tasks. The correct directory must house commands and utilities that require root privileges, ensuring they are inaccessible or unnecessary for regular users.
Correct Option:
A. /sbin
The /sbin directory contains system binaries like reboot, fdisk, and iptables, which are typically executable only by the root user.
These commands manage system-level operations (e.g., hardware, networking) requiring elevated privileges, aligning with the requirement for root-only access.
Regular users do not need or have permission to run these tools.
Incorrect Option:
B. /bin
The /bin directory holds essential user binaries like ls, cp, and cat, which are accessible to all users, not just root. It is not restricted to root-only execution.
C. /root
The /root directory is the home directory for the root user, containing personal files and settings, not binaries for root-only execution. It serves a different purpose.
D. /lib
The /lib directory stores shared libraries needed by binaries in /bin and /sbin, but it contains no executable binaries itself, making it irrelevant to the question.
Reference:
CompTIA XK0-005 exam objectives: https://www.comptia.org/certifications/linux
(Red Hat filesystem hierarchy: https://access.redhat.com/documentation)
A Linux systems administrator is working to obtain the installed kernel version of several hundred systems. Which of the following utilities should the administrator use for this task?
A. Ansible
B. Git
C. Docker
D. Bash
Summary:
The administrator needs to obtain the installed kernel version from several hundred systems. Performing this task manually on each system via SSH would be incredibly time-consuming and inefficient. The requirement calls for an automation tool that can connect to all these systems in parallel, execute a single command (like uname -r), and return the results in an organized manner.
Correct Option:
A. Ansible:
This is the correct tool. Ansible is a configuration management and automation platform designed specifically for managing large numbers of servers. The administrator can create a simple Ansible playbook or use an ad-hoc command (e.g., ansible all -i inventory -m command -a "uname -r") to run the uname -r command on all several hundred systems at once and collect the output.
Incorrect Options:
B. Git:
Git is a distributed version control system used for tracking changes in source code during software development. It has no functionality for executing commands on remote servers.
C. Docker:
Docker is a platform for developing, shipping, and running applications in containers. It is used to package applications, not to gather system information from hundreds of physical or virtual machines.
D. Bash:
Bash is a command-line shell and scripting language. While the administrator could write a Bash script to loop through a list of servers and SSH into each one, this would be a custom, less efficient, and more error-prone solution compared to using a dedicated automation tool like Ansible, which is built for this exact purpose.
Reference:
Official CompTIA Linux+ (XK0-005) Certification Exam Objectives: This scenario falls under Objective 4.1: "Given a scenario, implement and configure automation," which includes using configuration management tools like Ansible. Using Ansible for ad-hoc command execution is a fundamental use case for gathering information or making quick changes across a server fleet.
A Linux administrator deployed a large-scale application service as a containerized pod. The Linux administrator needs to continually send the application's log file to the company’s central log store. Which of the following should the Linux administrator do to efficiently perform this task?
A. Configure a sidecar to perform log shipping
B. Run docker exec to access the logs within the container
C. Execute docker inspect and run a log rsync replication
D. Set up a custom task scheduler via kubectl
Summary:
The requirement is to continually send an application's log file from a containerized pod to a central log store. The application itself is running in one container. The most efficient and cloud-native pattern for this is to use a sidecar container. A sidecar is an auxiliary container that runs in the same pod as the main application container and provides a supporting function, such as log shipping, without modifying the main application.
Correct Option:
A. Configure a sidecar to perform log shipping:
This is the correct and most efficient approach. A sidecar container in the same pod can share a volume with the main application container, allowing it to access the log file. The sidecar can then run a dedicated log shipper (like Fluentd, Filebeat, or Logstash) that is specifically configured to read the log file and continuously stream it to the central log store. This decouples the logging logic from the application and is a standard Kubernetes pattern.
Incorrect Options:
B. Run docker exec to access the logs within the container:
The docker exec command is a manual, interactive tool for executing a command inside a running container. It is not a solution for automated, continuous log shipping and does not scale for a "large-scale application service."
C. Execute docker inspect and run a log rsync replication:
docker inspect provides low-level information about a container. rsync is a tool for synchronizing files and is not designed for continuous log streaming. This approach would be a complex, custom, and inefficient script, not a native container solution.
D. Set up a custom task scheduler via kubectl:
kubectl is the command-line tool for Kubernetes. While Kubernetes has a CronJob resource for scheduling tasks, setting up a scheduled job to periodically copy logs is less efficient than a real-time, continuous sidecar and would introduce delays in log delivery.
Reference:
Official CompTIA Linux+ (XK0-005) Certification Exam Objectives: This knowledge aligns with the container management concepts in Objective 1.5. Understanding common container patterns, like the sidecar pattern for auxiliary tasks (logging, monitoring, proxying), is part of designing and managing modern, cloud-native applications.
An administrator would like to mirror the website files on the primary web server, www1, to the backup web server, www2. Which of the following commands should the administrator use to most efficiently accomplish this task?
A. [wwwl ] rsync —a —e ssh /var/www/html/ user1@www2 : /var/www/html
B. [ wwwl ] scp —r /var/www/html user1@www2 : / var/www/html
C. [www2 ] cd /var/www/html; wget —m http: //wwwl/
D. [wwwl ] cd /var/www/html && tar cvf —
Summary:
The administrator needs to efficiently synchronize (mirror) the website files from the primary server (www1) to the backup server (www2). The ideal solution should be efficient for subsequent runs by copying only changed files, preserve all file attributes (permissions, timestamps), and work securely over the network. The command should be initiated from the source server.
Correct Option:
A. [www1] rsync -a -e ssh /var/www/html/ user1@www2:/var/www/html:
This is the most efficient and correct command.
rsync is designed for efficient file synchronization. After the initial copy, it only transfers files that have changed, saving time and bandwidth.
The -a (archive) flag preserves permissions, timestamps, and other attributes, which is crucial for web files.
The -e ssh flag ensures the data is transferred over an encrypted SSH connection.
The trailing slash on the source (/var/www/html/) means the contents of the directory are synced into the target directory, which is the desired behavior for mirroring.
Incorrect Options:
B. [www1] scp -r /var/www/html user1@www2:/var/www/html:
While scp works, it is less efficient. It copies all files every time, regardless of whether they have changed. It also does not have the same robust ability as rsync to preserve all file attributes perfectly over the network.
C. [www2] cd /var/www/html; wget -m http://www1/:
The wget -m (mirror) command is used to download files from a web server via the HTTP protocol. This would only copy files that are publicly accessible through the web server and would not copy important files like configuration scripts, files with restricted permissions, or files outside the web root. It is not a reliable method for full server-to-server synchronization.
D. [www1] cd /var/www/html && tar cvf - . | ssh user1@www2 "cd /var/www/html && tar xvf -":
This command uses tar over ssh to copy the files. While this works and preserves attributes, it is less efficient than rsync because it transfers the entire directory structure every time, rather than just the differences.
Reference:
Official CompTIA Linux+ (XK0-005) Certification Exam Objectives: This scenario falls under Objective 3.2: "Given a scenario, manage storage, files, and directories in a Linux environment," which includes using commands to copy files between systems. rsync is the industry-standard tool for efficient and reliable file synchronization.
Which of the following is the best tool for dynamic tuning of kernel parameters?
A. tuned
B. tune2fs
C. tuned-adm
D. turbostat
Summary:
Dynamic tuning of kernel parameters involves adjusting system settings on-the-fly to optimize performance for specific workloads (e.g., high throughput, low latency, virtualized environments) without requiring a reboot. This requires a service that can monitor the system and apply pre-defined or custom profiles that change various kernel parameters dynamically based on the current performance needs.
Correct Option:
A. tuned:
This is the correct tool. tuned is a system service specifically designed for dynamic, automated performance tuning of a Linux system. It uses profiles (like throughput-performance, latency-performance, virtual-guest) that adjust a wide range of kernel parameters (related to CPU, disk I/O, power management, etc.) to optimize the system for a particular use case. The service runs in the background and applies these tunings dynamically.
Incorrect Options:
B. tune2fs:
This utility is used to adjust tunable parameters on an ext2, ext3, or ext4 filesystem. It operates on the filesystem metadata on disk and is not used for dynamic, system-wide kernel parameter tuning.
C. tuned-adm:
This is the administrative command-line interface for the tuned service. While it is used to activate, list, and manage tuning profiles (tuned-adm profile throughput-performance), the tool that performs the actual dynamic tuning in the background is the tuned daemon/service itself.
D. turbostat:
This is a diagnostic tool for reporting processor topology, frequency, idle power state statistics, and temperature. It is used for monitoring and analysis, not for actively tuning kernel parameters.
Reference:
Official CompTIA Linux+ (XK0-005) Certification Exam Objectives: This knowledge aligns with performance optimization concepts that are part of managing a Linux system. While not explicitly listed in a single objective, understanding tools like tuned for automated performance tuning falls under the broader scope of system optimization and administration covered in the exam.
A systems administrator is investigating a service that is not starting up. Given the following information:
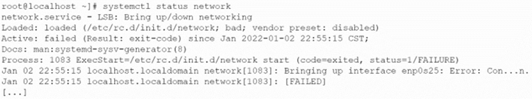
Which of the following systemd commands should the administrator use in order to obtain more details about the failing service?
A. systemct1 analyze network
B. systemct1 info network
C. sysctl -a network
D. journalctl -xu network
Summary:
A systemd service (network) is failing to start. The systemctl status command provides a brief overview but often requires more detailed logs to diagnose the root cause. The correct command must be one that retrieves and displays the detailed, chronological log messages specifically related to this service unit from the system's journal.
Correct Option:
D. journalctl -xu network:
This is the correct command for detailed troubleshooting.
journalctl is the command to query the systemd journal.
The -x flag provides more explanatory and catalog information in the output.
The -u flag filters the logs to show messages only for a specific unit (in this case, the network service).
This combination will display a detailed, chronological log of all messages related to the network service's startup attempts and failures.
Incorrect Options:
A. systemctl analyze network:
This is not a valid systemctl command. The correct command for analyzing system startup performance is systemd-analyze, but it is not used for diagnosing a specific service's failure logs.
B. systemctl info network:
The systemctl command uses status (systemctl status) to show service information, not info. The info subcommand does not exist.
C. sysctl -a network:
The sysctl command is used to view and modify kernel parameters at runtime. The -a flag displays all parameters. This command is unrelated to troubleshooting a systemd service.
Reference:
Official CompTIA Linux+ (XK0-005) Certification Exam Objectives: This scenario falls under Objective 3.1: "Given a scenario, use the appropriate system and service management commands to accomplish administrative tasks," which includes managing and troubleshooting systemd services. Using journalctl -xu [service] is the standard method for obtaining detailed logs for a failing systemd unit.
A Linux administrator needs to expose port 9000 for a container to listen during runtime. The Linux administrator creates a Dockerfile with the following entries:
sql
FROM node:9-alpine
WORKDIR /usr/src/app
COPY package.json ./
RUN npm install
COPY . .
EXPOSE 9000
CMD ["npm", "start"]
Which of the following commands should the administrator use to accomplish this task?
(Select two).
A. docker build -t Test-Container
B. docker tag Test-Container
C. docker inspect Test-Container
D. docker run -p 5000:80 Test-Container
E. docker push Test-Container
F. docker run -p 80:9000 Test-Container
Summary:
The Linux administrator needs to expose port 9000 for a container built from a Dockerfile to listen during runtime. The Dockerfile uses EXPOSE 9000 to document the port, but runtime port mapping requires the docker run command to bind it to a host port. The process involves building the container image and running it with the correct port mapping to enable external access.
Correct Option:
A. docker build -t Test-Container
docker build -t Test-Container builds the Docker image from the Dockerfile, tagging it as Test-Container.
This step is necessary to create the image containing the application and the EXPOSE 9000 instruction before it can be run.
The . specifies the build context (current directory with the Dockerfile).
F. docker run -p 80:9000 Test-Container
docker run -p 80:9000 Test-Container starts a container from the Test-Container image, mapping port 80 on the host to port 9000 in the container.
The -p flag enables runtime port binding, allowing external access to the container’s port 9000 via host port 80.
This fulfills the requirement to expose port 9000 for runtime listening.
Incorrect Option:
B. docker tag Test-Container
docker tag Test-Container renames an existing image but requires a target tag (e.g., docker tag Test-Container new-name). Without a target, it’s incomplete and doesn’t build or run the container.
C. docker inspect Test-Container
docker inspect Test-Container provides metadata about the image or container but does not expose or map ports for runtime use. It’s a diagnostic tool, not a solution.
D. docker run -p 5000:80 Test-Container
docker run -p 5000:80 maps host port 5000 to container port 80, which does not match the required port 9000 exposed in the Dockerfile. This misconfiguration prevents the intended functionality.
E. docker push Test-Container
docker push Test-Container uploads the image to a registry but does not expose ports or run the container locally, making it irrelevant to the task.
Reference:
CompTIA XK0-005 exam objectives: https://www.comptia.org/certifications/linux
(Docker documentation: https://docs.docker.com/)
An application developer received a file with the following content:
##This is a sample Image ##
FROM ubuntu:18.04
MAINTAINER demohut@gtmail.com.hac
COPY . /app
RUN make /app
CMD python /app/app.py
RUN apt-get update
RUN apt-get install -y nginx
CMD ["echo","Image created"]
The developer must use this information to create a test bed environment and identify the
image (myimage) as the first version for testing a new application before moving it to production. Which of the following commands will accomplish this task?
A. docker build -t myimage:1.0 .
B. docker build -t myimage: .
C. docker build -t myimage-1.0 .
D. docker build -i myimage:1.0 .
Summary:
The developer has a file that contains instructions for building a Docker image (this file is a Dockerfile). The task is to use this file to build an image, tag it with the name myimage and the version 1.0 for identification, and create the test bed environment. The correct command must use the build command with the proper syntax for tagging.
Correct Option:
A. docker build -t myimage:1.0 .: This is the correct command.
docker build is the command to build an image from a Dockerfile.
The -t (tag) flag is used to assign a name and optionally a tag to the built image.
myimage:1.0 specifies the image name as myimage and the tag as 1.0, clearly identifying it as the first version.
The . at the end specifies the build context is the current directory, which is where the Dockerfile is expected to be located.
Incorrect Options:
B. docker build -t myimage: .:
This command is incomplete. The -t flag requires a value. The colon : without a subsequent tag name is invalid syntax and will cause an error.
C. docker build -t myimage-1.0 .:
This command creates an image with the single tag myimage-1.0. While this might seem similar, it does not follow the standard name:tag convention. The requirement is to identify the image as myimage and the version as 1.0, which is best represented by the name:tag format.
D. docker build -i myimage:1.0 .:
The -i flag is not a valid option for the docker build command. The correct flag for tagging is -t.
Reference:
Official CompTIA Linux+ (XK0-005) Certification Exam Objectives: This scenario falls under Objective 1.5: "Given a scenario, manage and configure containers," which includes using Docker commands to build images from a Dockerfile. The docker build -t
| Page 18 out of 40 Pages |
| Previous |