An important patch for a critical application has just been released, and a systems administrator is identifying all of the systems requiring the patch. Which of the following must be maintained in order to ensure that all systems requiring the patch are updated?
A. Asset inventory
B. Network enumeration
C. Data certification
D. Procurement process
Explanation:
An asset inventory is a comprehensive and up-to-date record of all hardware and software assets within an organization. To ensure all systems requiring the critical patch are identified and updated, the systems administrator must rely on an accurate asset inventory. This inventory should include details such as:
The types and versions of applications installed on each system.
Operating system versions.
Device ownership and location.
Without a maintained asset inventory, the administrator might miss systems (e.g., offline devices, rarely used systems, or virtual machines), leading to unpatched vulnerabilities.
Why not the others?
B. Network enumeration:
This involves actively scanning the network to discover devices and services. While useful, it may not reliably identify all systems (e.g., offline devices) or specific application versions, and it is reactive rather than proactive like a maintained inventory.
C. Data certification:
This refers to validating data integrity or compliance (e.g., for sensitive data), not tracking hardware/software assets.
D. Procurement process:
This governs how assets are purchased and onboarded but does not maintain a real-time record of deployed systems and their software.
Reference:
Domain 5.1: "Explain the importance of security concepts in an enterprise environment." The SY0-701 objectives emphasize asset management and inventory as critical for vulnerability management, patching, and compliance. A maintained asset inventory ensures visibility and control over all systems requiring updates.
Which of the following describes the maximum allowance of accepted risk?
A. Risk indicator
B. Risk level
C. Risk score
D. Risk threshold
Explanation:
In risk management, a risk threshold is the predefined level of risk that an organization is willing to accept. It is the boundary between acceptable and unacceptable risk.
It is a key component of the risk appetite (the amount of risk an organization is willing to pursue) and risk tolerance (the acceptable deviation from the risk appetite).
Once risks are assessed and given a value (e.g., a risk score or level), they are compared against this threshold.
Risks that fall below the threshold are deemed acceptable and are typically monitored.
Risks that rise above the threshold require action, such as implementing a security control to mitigate the risk, transferring the risk (e.g., via insurance), or avoiding the risk altogether.
The phrase "maximum allowance of accepted risk" is a direct description of this concept.
Why the other options are incorrect:
A. Risk indicator:
A risk indicator (or key risk indicator - KRI) is a metric used to provide an early warning signal of increasing risk. It is a measurable value that points to a potential risk, not the maximum level of accepted risk itself. For example, a rising number of failed login attempts is a risk indicator.
B. Risk level:
This is a general term for the magnitude of a risk, often determined by its impact and likelihood. It is the result of a risk assessment (e.g., "high," "medium," "low"), not the predefined boundary of what is acceptable.
C. Risk score:
A risk score is a quantitative or qualitative value assigned to a risk, typically calculated by a formula (e.g., Risk = Likelihood x Impact). Like risk level, it is an output of an assessment that must then be compared to the risk threshold to determine if it requires action.
Exam Objective Reference:
This question relates to Domain 5.0: Governance, Risk, and Compliance, specifically the concepts of risk management and risk assessment. Understanding the difference between risk threshold, appetite, tolerance, and assessment outputs is a key learning objective.
Which of the following security controls is most likely being used when a critical legacy server is segmented into a private network?
A. Deterrent
B. Corrective
C. Compensating
D. Preventive
Explanation: When a critical legacy server is segmented into a private network, the security control being used is compensating. Compensating controls are alternative measures put in place to satisfy a security requirement when the primary control is not feasible or practical. In this case, segmenting the legacy server into a private network
serves as a compensating control to protect it from potential vulnerabilities that cannot be mitigated directly.
Compensating: Provides an alternative method to achieve the desired security outcome when the primary control is not possible.
Deterrent: Aims to discourage potential attackers but does not directly address segmentation.
Corrective: Used to correct or mitigate the impact of an incident after it has occurred.
Preventive: Aims to prevent security incidents but is not specific to the context of segmentation.
Reference: CompTIA Security+ SY0-701 Exam Objectives, Domain 1.1 - Compare and contrast various types of security controls (Compensating controls).
A security analyst finds a rogue device during a monthly audit of current endpoint assets that are connected to the network. The corporate network utilizes 002.1X for access control. To be allowed on the network, a device must have a Known hardware address, and a valid user name and password must be entered in a captive portal. The following is the audit report:
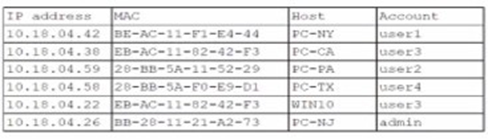
Which of the following is the most likely way a rogue device was allowed to connect?
A. A user performed a MAC cloning attack with a personal device.
B. A DMCP failure caused an incorrect IP address to be distributed
C. An administrator bypassed the security controls for testing.
D. DNS hijacking let an attacker intercept the captive portal traffic.
Explanation:
The key to solving this question lies in analyzing the provided audit log and comparing it against the stated security policy (802.1X + captive portal requiring a known MAC address and valid credentials).
The policy requires:
A Known Hardware Address (MAC address)
A Valid Username and Password (via captive portal)
The audit log reveals a critical anomaly:
The MAC address EB-AC-11-02-42-F3 appears twice, assigned to two different IP addresses and two different hosts:
10.10.04.36 on host FC-CA
10.10.04.22 on host WIH10
This is impossible under normal circumstances, as a MAC address should be unique to a single network interface controller (NIC). This duplication is a clear indicator of a MAC cloning attack.
A is correct.
A user likely took the known, authorized MAC address from a corporate device (in this case, the device FC-CA) and "cloned" or spoofed it on their personal, rogue device (WIH10). This would satisfy the first requirement of the network access control: a known hardware address. The user then presumably used their own valid credentials (user3) on the captive portal to satisfy the second requirement, successfully gaining network access for the unauthorized device.
B is incorrect.
A DHCP failure would not cause a MAC address to be duplicated in the ARP table (which is what this audit log represents). DHCP assigns IP addresses, and a failure might lead to an APIPA address (e.g., 169.254.x.x) or no address, but it would not clone a MAC address onto a second device.
C is incorrect.
While possible, this is not the most likely scenario given the specific technical evidence (the duplicated MAC address). If an administrator bypassed controls, they would likely not need to clone an existing MAC address; they could simply add the new device's legitimate MAC to the authorized list.
D is incorrect.
DNS hijacking redirects a user to a malicious website by resolving a legitimate domain name to a malicious IP address. It would not be effective against a captive portal, which typically uses the device's IP or MAC address to trigger the redirect. Furthermore, DNS hijacking would not explain the cloned MAC address present in the log.
Reference:
CompTIA Security+ SY0-701 Objective 1.4: "Given a scenario, analyze indicators of malicious activity." MAC address spoofing/cloning is a common technique to bypass network access control and is a key indicator of a malicious actor (or a rogue user) attempting to gain unauthorized access to a network.
Which of the following strategies should an organization use to efficiently manage and analyze multiple types of logs?
A. Deploy a SIEM solution
B. Create custom scripts to aggregate and analyze logs
C. Implement EDR technology
D. Install a unified threat management appliance
Explanation:
A SIEM (Security Information and Event Management) solution is specifically designed to efficiently manage and analyze multiple types of logs from various sources (e.g., firewalls, servers, endpoints, applications). It centralizes log collection, normalizes data into a common format, correlates events, and provides tools for analysis, alerting, and reporting. This enables security teams to identify patterns, detect anomalies, and respond to threats across the entire environment.
Why the others are incorrect:
B) Create custom scripts to aggregate and analyze logs:
While custom scripts can be written for specific tasks, they are not scalable or efficient for managing multiple types of logs across a large organization. Scripts require ongoing maintenance, lack advanced correlation capabilities, and are prone to errors compared to a dedicated SIEM platform.
C) Implement EDR technology:
EDR (Endpoint Detection and Response) focuses specifically on monitoring and protecting endpoints (e.g., workstations, servers). It is excellent for endpoint visibility and response but does not centrally manage logs from network devices, applications, or other infrastructure components like a SIEM does.
D) Install a unified threat management appliance:
A UTM (Unified Threat Management) appliance combines multiple security features (e.g., firewall, IPS, antivirus) into a single device. While it generates logs, it is not designed to aggregate and analyze logs from other systems across the organization. It primarily manages its own logs and threats.
Reference:
This aligns with SY0-701 Objective 4.3 ("Given an incident, utilize appropriate data sources to support an investigation"). SIEM systems are a core tool for log management and analysis, as emphasized in the CompTIA objectives and security best practices (e.g., NIST SP 800-92, Guide to Computer Security Log Management). They provide the centralized visibility needed for effective threat detection and incident response.
A security analyst is reviewing the source code of an application in order to identify misconfigurations and vulnerabilities. Which of the following kinds of analysis best describes this review?
A. Dynamic
B. Static
C. Gap
D. Impact
Explanation: Reviewing the source code of an application to identify misconfigurations and vulnerabilities is best described as static analysis. Static analysis involves examining the code without executing the program. It focuses on finding potential security issues, coding errors, and vulnerabilities by analyzing the code itself.
Static analysis: Analyzes the source code or compiled code for vulnerabilities without executing the program.
Dynamic analysis: Involves testing and evaluating the program while it is running to identify vulnerabilities.
Gap analysis: Identifies differences between the current state and desired state, often used for compliance or process improvement.
Impact analysis: Assesses the potential effects of changes in a system or process.
Reference: CompTIA Security+ SY0-701 Exam Objectives, Domain 4.3 - Explain various activities associated with vulnerability management (Static analysis).
A company is adding a clause to its AUP that states employees are not allowed to modify the operating system on mobile devices. Which of the following vulnerabilities is the organization addressing?
A. Cross-site scripting
B. Buffer overflow
C. Jailbreaking
D. Side loading
Explanation:
Jailbreaking (on iOS devices) or rooting (on Android devices) is the process of removing software restrictions imposed by the operating system manufacturer. This gives the user elevated privileges (root access) to modify the OS, install unauthorized apps, and change system settings. The AUP clause explicitly forbidding OS modification is directly aimed at preventing this practice, as it introduces significant security risks.
Why the others are incorrect:
A) Cross-site scripting (XSS):
This is a web application vulnerability where an attacker injects malicious scripts into a legitimate website. It is not related to modifying the operating system on a mobile device.
B) Buffer overflow:
This is a software coding vulnerability that occurs when a program writes more data to a block of memory than it is allocated to hold. It is a low-level exploit that can lead to remote code execution but is not a user action like modifying an OS. An AUP clause is a policy for users, not a fix for a software bug.
D) Side loading:
This refers to installing applications from sources other than the official app store (e.g., downloading an APK file from a website). While side loading is a security concern and is often enabled after jailbreaking/rooting, the clause specifically addresses modifying the operating system itself, which is the definition of jailbreaking. Side loading modifies the application environment, not the core OS.
Reference:
This maps to SY0-701 Objective 5.5 ("Explain the importance of policies to organizational security"). The Acceptable Use Policy (AUP) is a key document that defines rules for using organizational resources. This scenario demonstrates using the AUP to enforce mobile device security by explicitly prohibiting high-risk actions like jailbreaking, which undermines device integrity and security controls.
Which of the following is the best way to provide secure remote access for employees while minimizing the exposure of a company's internal network?
A. VPN
B. LDAP
C. FTP
D. RADIUS
Explanation:
Why A is Correct:
A Virtual Private Network (VPN) is specifically designed to provide secure remote access. It creates an encrypted tunnel between the remote user's device and the company's internal network. This encryption protects all data in transit from eavesdropping. Furthermore, a properly configured VPN provides access only to authorized users and typically limits that access to specific network segments, thereby minimizing the overall exposure of the internal network to the public internet. It is the standard and most effective solution for this purpose.
Why B is Incorrect:
LDAP (Lightweight Directory Access Protocol) is a protocol used for accessing and maintaining distributed directory information services (like user accounts). It is an authentication mechanism, not a remote access solution. While a VPN might use LDAP to authenticate users, LDAP by itself does not provide secure network connectivity.
Why C is Incorrect:
FTP (File Transfer Protocol) is an unsecure method for transferring files. It sends credentials and data in clear text, making it highly vulnerable to interception. It is not a remote access solution and would significantly increase the exposure of the network if used for this purpose.
Why D is Incorrect:
RADIUS (Remote Authentication Dial-In User Service) is a centralized protocol for authenticating and authorizing users who connect to a network. Like LDAP, it is an authentication and authorization service, not a remote access method. A VPN server would often act as a RADIUS client to validate user credentials, but RADIUS itself does not create a secure network tunnel.
Reference:
This question falls under Domain 3.0: Implementation, specifically covering the implementation of secure remote access methods and common network protocols. Understanding the distinct roles of connectivity solutions (VPN), file transfer protocols (FTP), and authentication services (LDAP, RADIUS) is crucial for the SY0-701 exam.
A security operations center determines that the malicious activity detected on a server is normal. Which of the following activities describes the act of ignoring detected activity in the future?
A. Tuning
B. Aggregating
C. Quarantining
D. Archiving
Explanation:
Tuning is the process of adjusting a security system, like a SIEM (Security Information and Event Management) or an IDS/IPS (Intrusion Detection/Prevention System), to improve its accuracy. When the SOC determines that a specific detected activity is actually normal (a false positive), they can "tune" the system's rules or alerts to ignore that specific activity in the future. This reduces alert fatigue and allows analysts to focus on genuine threats.
Why not B?
Aggregating refers to the process of combining multiple log entries or alerts into a single, summarized record. This is done to reduce data volume and see correlated events, but it does not describe the act of ignoring specific activity.
Why not C?
Quarantining is an active response action where a file, email, or system is isolated to prevent potential malware from spreading. It is a containment step, not a step for managing alert rules.
Why not D?
Archiving is the process of moving data to long-term storage for retention and compliance purposes. It is unrelated to the process of managing and refining alert rules.
Reference:
Domain 4.4: "Given an incident, apply mitigation techniques or controls to secure an environment." Incident response handling often involves tuning security systems based on the findings of an investigation to prevent future false positives. This is a key function of a Security Operations Center (SOC).
After a recent vulnerability scan, a security engineer needs to harden the routers within the corporate network. Which of the following is the most appropriate to disable?
A. Console access
B. Routing protocols
C. VLANs
D. Web-based administration
Explanation:
Why D is Correct:
When hardening network devices like routers, the principle is to reduce the attack surface by disabling unnecessary services. Web-based administration (a graphical user interface accessed via HTTP/HTTPS) is a common service that is often enabled by default but is not required for operation.
It is more prone to vulnerabilities (e.g., cross-site scripting, authentication bypass) compared to command-line interfaces (CLI).
It exposes an additional network service that could be targeted by attackers.
Disabling it and using CLI-based administration (e.g., SSH) is a standard hardening step, as SSH is generally considered more secure and robust for device management.
Why A is Incorrect:
Console access (physical access via a console cable) is a critical method for out-of-band management and recovery, especially if network-based access fails. It should be secured (e.g., with authentication) but not disabled entirely, as it is often the last resort for accessing the device.
Why B is Incorrect:
Routing protocols (e.g., OSPF, BGP) are essential for the core function of a router—directing traffic between networks. Disabling them would render the router non-functional for its primary purpose. Instead, these protocols should be secured (e.g., with authentication) rather than disabled.
Why C is Incorrect:
VLANs (Virtual Local Area Networks) are a fundamental security and network segmentation tool. Disabling VLANs would weaken network security by removing the ability to isolate traffic and enforce policies between different network segments. This is the opposite of hardening.
Reference:
This question falls under Domain 2.0: Architecture and Design and Domain 3.0: Implementation, covering secure network architecture and system hardening techniques. Hardening routers involves minimizing enabled services to reduce vulnerabilities, and disabling web-based administration is a common best practice.
During a recent company safety stand-down, the cyber-awareness team gave a presentation on the importance of cyber hygiene. One topic the team covered was best practices for printing centers. Which of the following describes an attack method that relates to printing centers?
A. Whaling
B. Credential harvesting
C. Prepending
D. Dumpster diving
Explanation:
Dumpster diving is an attack method that involves physically searching through an organization's trash or recycling bins to find sensitive information that has been discarded without being properly destroyed. This attack method directly relates to printing centers because these areas are often where documents containing sensitive data (e.g., financial reports, employee records, internal communications) are printed and, if not managed correctly, discarded. An attacker could retrieve these documents to gain valuable information.
Why not A?
Whaling: This is a type of phishing attack specifically targeting high-profile individuals like executives. It is a digital social engineering attack and does not relate to the physical security of a printing center.
Why not B?
Credential harvesting: This is the process of collecting usernames and passwords, typically through phishing sites, keyloggers, or data breaches. It is a digital attack method and is not specifically tied to the physical printing process.
Why not C?
Prepending: This is a technique where attackers add something to the beginning of a communication (e.g., adding "SAFE" to a subject line) to evade filters or gain trust. It is a digital tactic used in phishing emails and does not relate to physical documents from a printer.
Reference:
Domain 2.5: "Explain the importance of physical security controls." Physical security controls include measures for secure disposal of sensitive information (e.g., shredders, locked bins for documents awaiting destruction). The topic of securing printing centers and preventing dumpster diving falls under this domain, as it is a key aspect of organizational cyber hygiene and physical security awareness.
A systems administrator set up a perimeter firewall but continues to notice suspicious connections between internal endpoints. Which of the following should be set up in order to mitigate the threat posed by the suspicious activity?
A. Host-based firewall
B. Web application firewall
C. Access control list
D. Application allow list
Explanation:
A) Host-based firewall is the correct answer.
A perimeter firewall controls traffic between the internal network and external networks (e.g., the internet), but it does not monitor or restrict traffic between internal endpoints. If suspicious connections are occurring between devices inside the network (e.g., lateral movement by an attacker), a host-based firewall (HBF) can
Filter traffic at the individual host level.
Block unauthorized internal communications.
Provide granular control based on applications, ports, and IP addresses.
This helps contain threats that originate or spread within the network.
Why the others are incorrect:
B) Web application firewall (WAF):
A WAF protects web applications from attacks (e.g., SQL injection, XSS) by filtering HTTP traffic. It is not designed to control general network traffic between internal endpoints.
C) Access control list (ACL):
While ACLs can filter traffic on network devices (e.g., routers), they are typically applied at the perimeter or between network segments. They are less effective for fine-grained control at the host level.
D) Application allow list:
This restricts which applications can run on a system (e.g., allowing only approved software). It does not directly control network connections between devices.
Reference:
This question tests knowledge of Domain 3.3: Given a scenario, implement secure network designs and Domain 3.2: Implement security hardening strategies. Host-based firewalls are a critical layer of defense-in-depth, especially for mitigating internal threats, as emphasized in the SY0-701 objectives. They complement perimeter firewalls by protecting endpoints from insider threats and lateral movement.
| Page 6 out of 60 Pages |
| Previous |