Which of the following is the best way to prevent an unauthorized user from plugging a laptop into an employee's phone network port and then using tools to scan for database servers?
A. MAC filtering
B. Segmentation
C. Certification
D. Isolation
Explanation:
Why A is Correct:
MAC filtering is a network access control technique that allows or denies network access based on the physical (MAC) address of a device. By configuring the network switch to only allow specific, authorized MAC addresses (like the employee's phone) on that port, an unauthorized laptop would be prevented from connecting and scanning the network. This directly addresses the physical access threat described.
Why B is Incorrect:
Segmentation involves dividing the network into smaller subnetworks to limit lateral movement. While it could help contain the damage if an attacker did gain access, it does not prevent the initial unauthorized connection to the network port. MAC filtering is a more direct preventive measure for this scenario.
Why C is Incorrect:
Certification typically refers to verifying the authenticity of devices or users through digital certificates (e.g., 802.1X). While it is a stronger method than MAC filtering (which can be spoofed), it is more complex to implement. The question asks for the "best way," and MAC filtering is a simpler, effective first line of defense for physical port security. However, note that 802.1X (which uses certification) would be even more robust, but it is not listed as an option.
Why D is Incorrect:
Isolation usually refers to techniques like port isolation or private VLANs that prevent devices on the same switch from communicating with each other. This could limit what the attacker could scan, but it does not prevent the unauthorized device from connecting to the network and potentially scanning other segments.
Reference:
This question falls under Domain 2.0: Architecture and Design, specifically covering network access control methods. MAC filtering is a basic but effective measure to prevent unauthorized devices from connecting to physical network ports, aligning with the principle of controlling physical network access. For the SY0-701 exam, understanding the role of MAC filtering in port security is key.
Which of the following threat actors would most likely deface the website of a high-profile music group?
A. Unskilled attacker
B. Organized crime
C. Nation-state
D. Insider threat
Explanation:
Unskilled attacker (often referred to as a "script kiddie") is the most likely threat actor in this scenario. These individuals lack advanced technical skills but use pre-written scripts and tools to launch attacks. Their motivations are often notoriety, fame, or expressing a personal grievance (e.g., not liking the music group). Defacing a high-profile website is a very public way to gain attention and demonstrate their "capabilities" to peers, which aligns perfectly with the typical goals of an unskilled attacker.
Why the other options are incorrect:
B. Organized crime:
These threat actors are primarily financially motivated. Their activities focus on monetization through ransomware, data theft for fraud, or extortion. Defacing a website does not typically generate direct financial gain and could draw unwanted law enforcement attention, making it an unlikely action for a profit-driven group.
C. Nation-state:
These are highly sophisticated actors sponsored by governments. Their goals are typically espionage, intellectual property theft, or disruption of critical national infrastructure to achieve geopolitical objectives. Defacing a music group's website would be considered trivial, low-impact, and not aligned with their strategic missions. It would be an inefficient use of their advanced resources.
D. Insider threat:
An insider threat involves a current or former employee, contractor, or business partner. While a disgruntled insider could deface a website, the scenario does not provide any context to suggest the actor has internal access. The most common and likely actor for a high-profile, reputation-focused attack like website defacement is an external unskilled attacker seeking attention.
Reference:
This question tests knowledge of threat actor attributes and motivations, a key part of threat modeling.
This falls under Domain 1.5: Explain different threat actor types and attributes of the CompTIA Security+ SY0-701 exam objectives.
Understanding that different threat actors have distinct motivations (e.g., financial, ideological, espionage, notoriety) is crucial for prioritizing defenses and anticipating attacks. Website defacement is a classic hallmark of hacktivists and unskilled attackers.
Which of the following is a common, passive reconnaissance technique employed by penetration testers in the early phases of an engagement?
A. Open-source intelligence
B. Port scanning
C. Pivoting
D. Exploit validation
Explanation:
The correct answer is A. Open-source intelligence (OSINT).
In the context of penetration testing and cyber attacks, the initial phase is almost always reconnaissance. This phase is focused on gathering as much information as possible about the target without directly interacting with its systems, making it a passive technique.
Open-source intelligence (OSINT) is the collection and analysis of information that is publicly available. A penetration tester uses OSINT to build a profile of the target without sending a single packet to the target's network. This is the quintessential passive reconnaissance technique.
Common OSINT activities include:
Searching for employee names, email addresses, and organizational structure on LinkedIn and company websites.
Reviewing job postings to identify technologies and software stacks in use.
Searching public code repositories (e.g., GitHub) for accidentally exposed API keys or code.
Using tools like theHarvester to find email accounts and subdomains.
Looking at social media posts from employees for information about corporate culture or systems.
Examining DNS records (using public whois databases) to map out the target's network footprint.
Because this information is gathered from public, third-party sources, the target organization has no way of detecting that this reconnaissance is taking place.
Why the other options are incorrect:
B. Port scanning:
Port scanning (e.g., using tools like Nmap) is a form of active reconnaissance. It involves sending packets directly to the target's systems to discover open ports and running services. This interaction is detectable by the target's security systems (IDS/IPS) and firewalls, and is therefore not passive.
C. Pivoting:
Pivoting is an technique used after a initial compromise. It involves using a breached system as a "jump host" to attack other systems on a network that are not directly accessible from the internet. This occurs in later phases of an attack (like lateral movement), not during the initial passive reconnaissance.
D. Exploit validation:
Exploit validation is the process of actively testing and confirming that a vulnerability can be successfully exploited to gain access to a system. This is a core activity in the exploitation phase, which comes long after reconnaissance. It is a highly active and intrusive process, not a passive one.
Reference:
This distinction between passive and active reconnaissance is a fundamental concept in security testing and is covered in the CompTIA Security+ SY0-701 objectives, particularly under Domain 1.1: Given a scenario, analyze indicators of malicious activity.
The penetration testing process is often broken into phases, with the first being passive reconnaissance (information gathering):
Passive Reconnaissance (OSINT)
Active Reconnaissance (Scanning)
Gaining Access (Exploitation)
Maintaining Access
Covering Tracks
Which of the following is an example of a data protection strategy that uses tokenization?
A. Encrypting databases containing sensitive data
B. Replacing sensitive data with surrogate values
C. Removing sensitive data from production systems
D. Hashing sensitive data in critical systems
Explanation:
Tokenization is a data protection strategy where sensitive data (like a credit card number) is replaced with a non-sensitive equivalent, called a token. This token is a randomly generated surrogate value that has no mathematical relationship to the original data. The original data is stored securely in a separate token vault. The token can be used in business processes and systems (e.g., for transactions or analytics) without exposing the real sensitive data, significantly reducing the risk of data breaches.
Why the others are incorrect:
A) Encrypting databases containing sensitive data:
This describes encryption, not tokenization. Encryption transforms data into ciphertext using a key and algorithm, and the original data can be decrypted with the correct key. Tokenization uses substitution, not mathematical transformation.
C) Removing sensitive data from production systems:
This describes data masking or redaction, where sensitive data is obscured or deleted. Tokenization doesn't remove the data; it replaces it with a token that stands in for the original data, which is stored elsewhere.
D) Hashing sensitive data in critical systems:
This describes hashing, which is a one-way cryptographic function that produces a fixed-size output (hash). Unlike tokenization, hashing is not reversible and is primarily used for data integrity verification, not for protecting data while retaining its usability for business processes.
Reference:
This aligns with SY0-701 Objective 2.2 ("Summarize cryptography fundamentals") and data protection strategies. Tokenization is often contrasted with encryption and hashing as a method for securing data at rest, especially in payment processing environments (e.g., PCI DSS compliance), where tokens replace primary account numbers (PANs) to reduce the scope of sensitive data in systems.
Which of the following would be the greatest concern for a company that is aware of the consequences of non-compliance with government regulations?
A. Right to be forgotten
B. Sanctions
C. External compliance reporting
D. Attestation
Explanation:
B) Sanctions is the correct answer.
Sanctions refer to penalties imposed by regulatory bodies for non-compliance with government regulations. These can include:
Fines:
Monetary penalties that can be substantial.
Legal action:
Lawsuits or criminal charges.
Operational restrictions:
Loss of licenses or permits necessary for business operations.
Reputational damage:
Loss of public trust and customer confidence.
For a company focused on the consequences of non-compliance, sanctions represent the most direct and severe impact, as they can result in financial loss, legal trouble, and even business closure.
Why the others are incorrect:
A) Right to be forgotten:
This is a data privacy principle (e.g., under GDPR) that allows individuals to request the deletion of their personal data. While non-compliance with this right could lead to sanctions, it is a specific requirement rather than the overarching consequence of non-compliance.
C) External compliance reporting:
This is a process where organizations report their compliance status to regulators. While inaccurate reporting can lead to sanctions, it is not the consequence itself—it is an activity that, if done improperly, might result in sanctions.
D) Attestation:
This is a formal declaration or verification of compliance (e.g., by an auditor). Like reporting, it is part of the compliance process, but the greatest concern is the penalty (sanctions) for failing to comply or provide accurate attestations.
Reference:
This question tests knowledge of Domain 5.3: Explain the importance of policies to organizational security and Domain 5.1: Explain the importance of risk management processes. Sanctions are a key element of regulatory risk, and the SY0-701 objectives emphasize the need for organizations to understand and mitigate the legal and financial repercussions of non-compliance.
Company A jointly develops a product with Company B, which is located in a different country. Company A finds out that their intellectual property is being shared with unauthorized companies. Which of the following has been breached?
A. SLA
B. AUP
C. SOW
D. MOA
Explanation:
A Memorandum of Agreement (MOA) is a formal document that outlines a cooperative relationship between two or more parties. It defines the terms, details, and responsibilities of each party in a partnership or joint venture. A key aspect of an MOA covering joint development would be the clauses regarding the handling and protection of Intellectual Property (IP). Since the core issue is the unauthorized sharing of jointly developed IP, the specific agreement governing that partnership (the MOA) has been breached.
Analysis of Incorrect Options:
A. SLA (Service Level Agreement):
An SLA is a contract between a service provider and a customer that defines the specific, measurable levels of service expected (e.g., uptime, performance, response time). It is focused on service metrics and remedies for not meeting them, not on protecting intellectual property in a development partnership.
B. AUP (Acceptable Use Policy):
An AUP is a set of rules applied by the owner, creator, or administrator of a network, website, or service that restricts the ways in which the resource may be used. It is an internal policy for employees or users, not a binding agreement between two separate companies for a joint venture.
C. SOW (Statement of Work):
An SOW is a document that defines the specific activities, deliverables, timelines, and requirements for a particular project. While a joint development project would have an SOW, its breach would relate to failing to deliver the work as specified. The unauthorized sharing of IP is a broader breach of the trust and terms of the overall partnership agreement itself (the MOA), not just the project's work details.
Reference:
This question falls under Domain 5.0: Security Program Management and Oversight, specifically objective 5.3: Explain elements of effective security governance. This includes understanding the purpose and legal implications of various agreements (e.g., BPA, NDA, SLA, ISA, MOU/MOA) and their role in managing third-party risk and protecting organizational assets like intellectual property. An MOA (or its close relative, an MOU - Memorandum of Understanding) is the appropriate agreement for this type of collaborative endeavor.
While a user reviews their email, a host gets infected by malware from an external hard drive plugged into the host. The malware steals all the user's credentials stored in the browser. Which of the following training topics should the user review to prevent this situation from reoccurring?
A. Operational security
B. Removable media and cables
C. Password management
D. Social engineering
This scenario highlights the need for training on the secure use of removable media. Users should learn to avoid using untrusted external storage devices to prevent malware infections.
A legacy device is being decommissioned and is no longer receiving updates or patches. Which of the following describes this scenario?
A. End of business
B. End of testing
C. End of support
D. End of life
Explanation:
The scenario describes a device that has reached the final stage of its usable lifespan from the vendor's perspective.
D. End of life (EOL) is correct.
When a vendor declares a product has reached its "end of life," it means the product is officially obsolete and will no longer be sold, marketed, or, most importantly, supported. This includes no longer providing security patches, software updates, or technical assistance. The device being decommissioned because it "is no longer receiving updates or patches" is the direct consequence of it having reached its end-of-life status.
A. End of business is incorrect.
"End of business" typically refers to the time a company closes its operations for the day. It is not a standard term in the technology lifecycle and does not describe a product's status.
B. End of testing is incorrect.
This is not a standard industry term for a product lifecycle phase. Testing is a phase during development, and its "end" does not relate to the long-term support status of a released product.
C. End of support (EOS) is incorrect.
This is a very common distractor. "End of support" is often used interchangeably with "end of life," but there is a subtle technical difference in some vendor models:
End of Life (EOL):
The announcement that a product will no longer be sold or supported after a future date.
End of Support (EOS):
The specific date after which support, including patches and updates, actually ends.
In practice, for CompTIA exam purposes, the scenario of a device "no longer receiving updates or patches" is the hallmark of both states. However, the more encompassing term that describes the scenario of the device being obsolete and unpatched is End of Life (EOL).
Reference:
CompTIA Security+ SY0-701 Objective 2.2: "Explain the importance of applicable regulations, standards, or frameworks that impact organizational security posture." Managing assets and understanding technology lifecycles, including End-of-Life (EOL), is a critical part of organizational security policy and risk management. Operating EOL systems poses a significant security risk.
Which of the following best describes the concept of information being stored outside of its country of origin while still being subject to the laws and requirements of the country of origin?
A. Data sovereignty
B. Geolocation
C. Intellectual property
D. Geographic restrictions
Explanation:
Data sovereignty refers to the concept that digital data is subject to the laws and governance structures of the country in which it is collected or originated, regardless of where it is physically stored. This means that even if an organization stores data in a cloud server located in another country, that data must still comply with the legal and regulatory requirements (e.g., privacy laws, access controls, disclosure rules) of its country of origin.
Why the others are incorrect:
B) Geolocation:
This is a technology used to identify or estimate the real-world geographic location of an object, such as a device or user. While it can be used to enforce policies based on location (like geographic restrictions), it does not describe the legal concept of which laws apply to the data.
C) Intellectual property:
This refers to creations of the mind (e.g., inventions, literary works, designs) that are protected by law through patents, copyrights, and trademarks. While data might include intellectual property, the question is specifically about the legal jurisdiction governing stored information, not the type of information.
D) Geographic restrictions:
These are controls that limit access to content or services based on the user's geographic location. For example, a streaming service restricting content by region. This is a technical implementation of policy, not the legal principle defining which laws apply to data stored abroad.
Reference:
This aligns with SY0-701 Objective 5.2 ("Explain elements of effective security governance"). Data sovereignty is a critical consideration in risk management and data governance, especially with the rise of cloud computing and global data storage. Regulations like the GDPR (General Data Protection Regulation) in the EU enforce strict rules on data sovereignty, requiring that data belonging to EU citizens is protected according to EU laws, even if processed or stored outside the EU.
Which of the following most accurately describes the order in which a security engineer should implement secure baselines?
A. Deploy, maintain, establish
B. Establish, maintain, deploy
C. Establish, deploy, maintain
D. Deploy, establish, maintain
The correct sequence is to first establish secure baselines by determining the required configurations, deploy those configurations across systems, and finally maintain the configurations through regular updates and auditing.
A security analyst receives an alert from a corporate endpoint used by employees to issue
visitor badges. The alert contains the following details: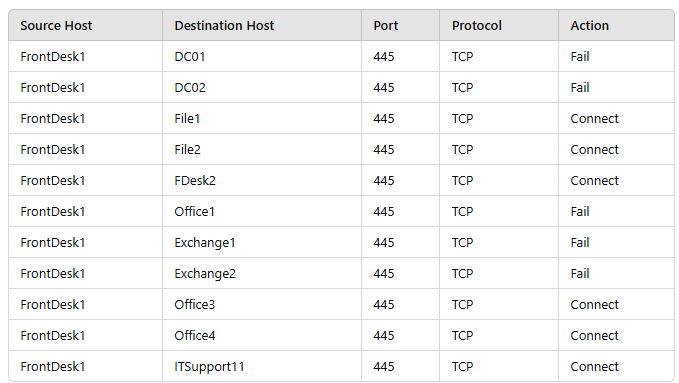
Which of the following best describes the indicator that triggered the alert?
A. Blocked content
B. Brute-force attack
C. Concurrent session usage
D. Account lockout
Explanation:
The alert details (not fully visible in your message, but typically including multiple failed login attempts in a short timeframe) indicate a brute-force attack. This is a common attack where an attacker tries numerous username/password combinations to gain unauthorized access. On an endpoint used for issuing visitor badges, such an attack could aim to compromise the system to create fraudulent badges or access sensitive areas.
Why not A?
"Blocked content" usually refers to prevented access to malicious websites or files, not repeated login attempts.
Why not C?
"Concurrent session usage" involves multiple active sessions for a single account, which might be suspicious but doesn't align with failed login patterns.
Why not D?
"Account lockout" is a defensive response to multiple failed attempts (possibly due to brute-forcing), but it is the result, not the indicator itself. The alert likely triggered on the failed attempts leading to lockout.
Reference:
Domain 1.3: "Given a scenario, analyze potential indicators of malicious activity." Brute-force attacks are characterized by rapid, repeated authentication failures, often detected by IDS/IPS or endpoint security tools. The SY0-701 objectives emphasize recognizing such patterns to mitigate unauthorized access attempts.
Which of the following would be the best way to test resiliency in the event of a primary power failure?
A. Parallel processing
B. Tabletop exercise
C. Simulation testing
D. Production failover
| Page 26 out of 60 Pages |
| Previous |