An administrator assists the legal and compliance team with ensuring information about customer transactions is archived for the proper time period. Which of the following data policies is the administrator carrying out?
A. Compromise
B. Retention
C. Analysis
D. Transfer
E. Inventory
Explanation:
The administrator is carrying out a data retention policy. This policy defines how long specific types of data (e.g., customer transactions) must be kept archived to meet legal, regulatory, or business requirements. Ensuring that information is stored for the proper time period directly aligns with retention rules, which often specify minimum and maximum durations for holding data before it can be securely disposed of.
Analysis of Incorrect Options:
A. Compromise:
This refers to a data breach or unauthorized access incident, not the archival of data for compliance.
C. Analysis:
Data analysis involves examining data to extract insights, not ensuring it is archived for a required duration.
D. Transfer:
Data transfer policies govern how data is moved between systems or locations (e.g., encryption during transit), not how long it is retained.
E. Inventory:
Data inventory involves cataloging what data exists, where it is stored, and how it is used, but it does not specify retention periods.
Reference:
This question falls under Domain 5.0: Security Program Management and Oversight, specifically data governance and compliance. Retention policies are critical for adhering to regulations like GDPR, HIPAA, or SOX, which mandate how long certain records must be preserved. NIST SP 800-53 (Control MP-6) and other frameworks emphasize the importance of proper data retention and disposal.
You are security administrator investigating a potential infection on a network. Click on each host and firewall. Review all logs to determine which host originated the Infecton and then deny each remaining hosts clean or infected.
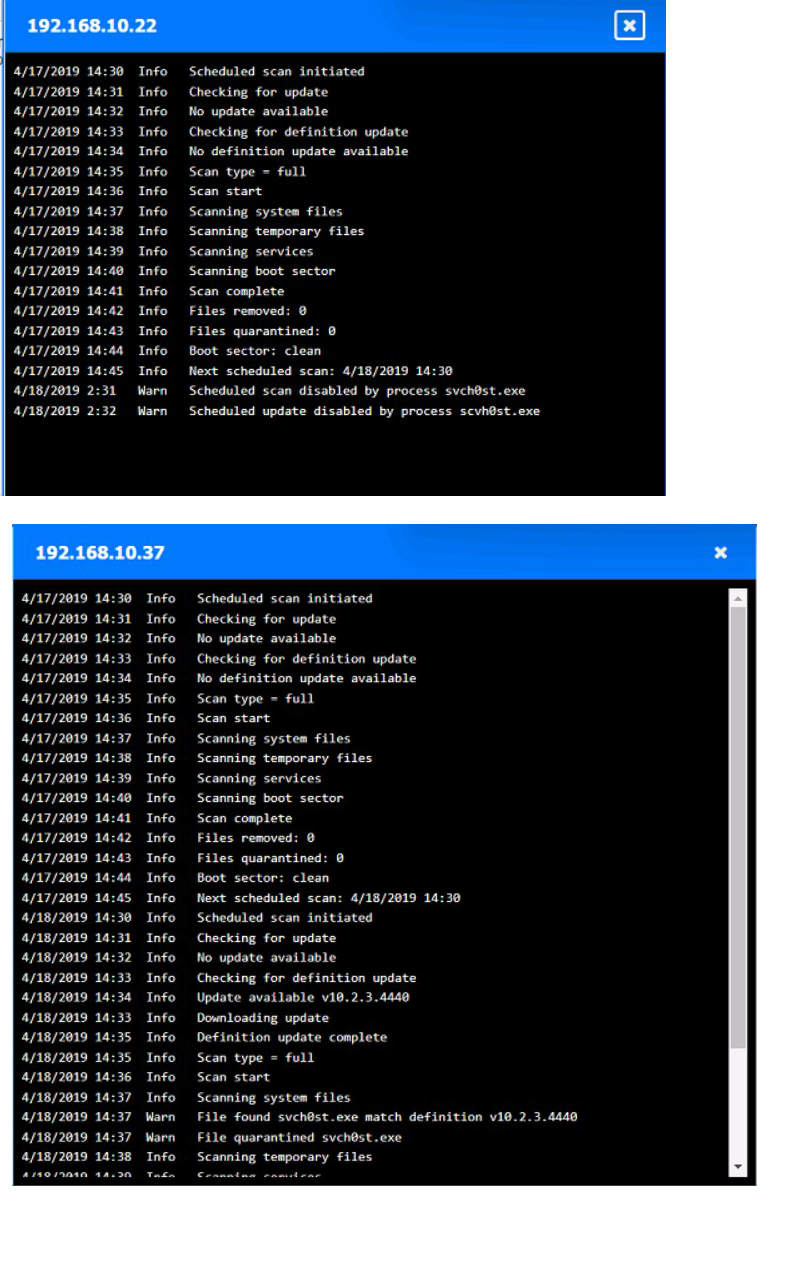
Explanation: Based on the logs, it seems that the host that originated the infection is 192.168.10.22. This host has a suspicious process named svchost.exe running on port 443, which is unusual for a Windows service. It also has a large number of outbound connections to
different IP addresses on port 443, indicating that it is part of a botnet. The firewall log shows that this host has been communicating with 10.10.9.18, which is another infected host on the engineering network. This host also has a suspicious process named svchost.exe running on port 443, and a large number of outbound connections to different IP addresses on port 443.
The other hosts on the R&D network (192.168.10.37 and 192.168.10.41) are clean, as they do not have any suspicious processes or connections.
A security administrator is deploying a DLP solution to prevent the exfiltration of sensitive customer data. Which of the following should the administrator do first?
A. Block access to cloud storage websites.
B. Create a rule to block outgoing email attachments.
C. Apply classifications to the data.
D. Remove all user permissions from shares on the file server.
Explanation: Data classification is the process of assigning labels or tags to data based on its sensitivity, value, and risk. Data classification is the first step in a data loss prevention (DLP) solution, as it helps to identify what data needs to be protected and how. By applying classifications to the data, the security administrator can define appropriate policies and rules for the DLP solution to prevent the exfiltration of sensitive customer data. References: CompTIA Security+ Study Guide: Exam SY0-701, 9th Edition, Chapter 8: Data Protection, page 323. CompTIA Security+ Practice Tests: Exam SY0-701, 3rd Edition, Chapter 8: Data Protection, page 327.
A systems administrator is configuring a site-to-site VPN between two branch offices. Some of the settings have already been configured correctly. The systems administrator has been provided the following requirements as part of completing the configuration:
• Most secure algorithms should be selected
• All traffic should be encrypted over the VPN
• A secret password will be used to authenticate the two VPN concentrators
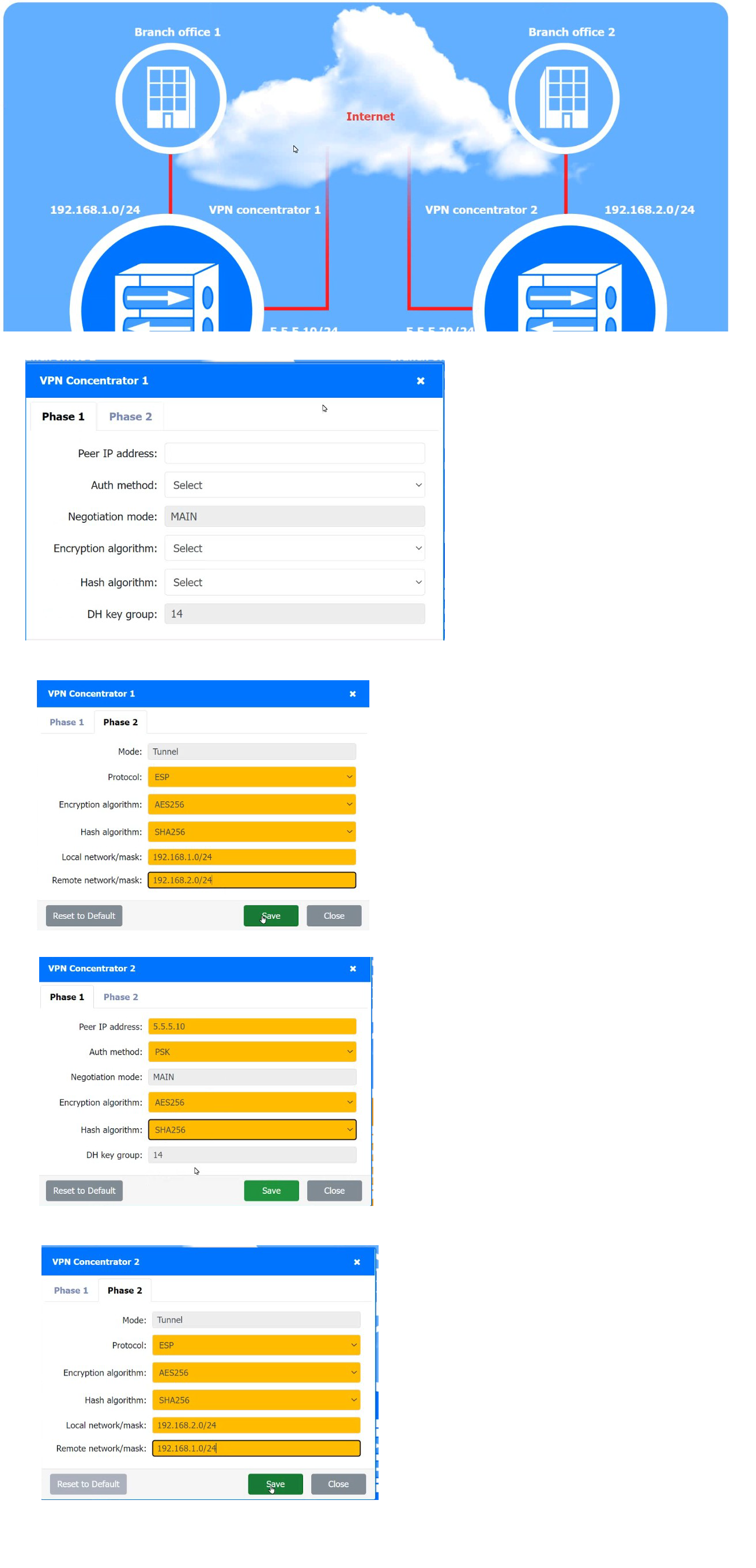
Answer: See the Explanation part for all the Solution.
Explanation:
To configure the site-to-site VPN between the two branch offices according to the provided requirements, here are the detailed steps and settings that need to be applied to the VPN
concentrators:
Requirements:
Most secure algorithms should be selected.
All traffic should be encrypted over the VPN.
A secret password will be used to authenticate the two VPN concentrators.
VPN Concentrator 1 Configuration:
Phase 1:
Peer IP address: 5.5.5.10 (The IP address of VPN Concentrator 2)
Auth method: PSK (Pre-Shared Key)
Negotiation mode: MAIN
Encryption algorithm: AES256
Hash algorithm: SHA256
DH key group: 14
Phase 2:
Mode: Tunnel
Protocol: ESP (Encapsulating Security Payload)
Encryption algorithm: AES256
Hash algorithm: SHA256
Local network/mask: 192.168.1.0/24
Remote network/mask: 192.168.2.0/24
VPN Concentrator 2 Configuration:
Phase 1:
Peer IP address: 5.5.5.5 (The IP address of VPN Concentrator 1)
Auth method: PSK (Pre-Shared Key)
Negotiation mode: MAIN
Encryption algorithm: AES256
Hash algorithm: SHA256
DH key group: 14
Phase 2:
Mode: Tunnel
Protocol: ESP (Encapsulating Security Payload)
Encryption algorithm: AES256
Hash algorithm: SHA256
Local network/mask: 192.168.2.0/24
Remote network/mask: 192.168.1.0/24
Summary:
Peer IP Address: Set to the IP address of the remote VPN concentrator.
Auth Method: PSK for using a pre-shared key.
Negotiation Mode: MAIN for the initial setup.
Encryption Algorithm: AES256, which is a strong and secure algorithm.
Hash Algorithm: SHA256, which provides strong hashing.
DH Key Group: 14 for strong Diffie-Hellman key exchange.
Phase 2 Protocol: ESP for encryption and integrity.
Local and Remote Networks: Properly configure the local and remote network addresses to match each branch office subnet.
By configuring these settings on both VPN concentrators, the site-to-site VPN will meet the requirements for strong security algorithms, encryption of all traffic, and authentication using a pre-shared key.
Which of the following automation use cases would best enhance the security posture of an organization by rapidly updating permissions when employees leave a company?
A. Provisioning resources
B. Disabling access
C. Reviewing change approvals
D. Escalating permission requests
Explanation:
The scenario specifically describes enhancing security by rapidly updating permissions when employees leave. The most critical action in this situation is to immediately disable the former employee's access to all systems, applications, and data to prevent any potential unauthorized access. Automating this process ensures it happens instantly upon termination, eliminating the delay and potential oversight of manual deprovisioning, which is a significant security risk.
Why the others are incorrect:
A) Provisioning resources:
This refers to the automated granting of access and setup of resources for new employees. It is the opposite of what is needed when an employee leaves.
C) Reviewing change approvals:
This automation would streamline the process for evaluating and approving requests to modify permissions or systems. While important for governance, it does not directly address the urgent need to remove access entirely when an employee departs.
D) Escalating permission requests:
This automation would route requests for additional access to the appropriate approving authority. Like option C, it deals with the granting or modification of access, not the revocation of access required during offboarding.
Reference:
This aligns with SY0-701 Objective 5.1 ("Explain the importance of personnel management policies"). A key element of these policies is the user account review and revocation process part of the offboarding procedure. Automating the disabling of access is a critical security control to enforce the principle of least privilege and immediately mitigate the risk posed by former employees. This is often part of Identity and Access Management (IAM) automation.
Which of the following phases of an incident response involves generating reports?
A. Recovery
B. Preparation
C. Lessons learned
D. Containment
Explanation:
The correct answer is C. Lessons learned. This is the final phase of the incident response process, as defined by frameworks like NIST SP 800-61 (Computer Security Incident Handling Guide). The primary activities in this phase involve a thorough review of the entire incident. This includes:
What happened:
The timeline of the incident.
How well the team responded:
What went right and what went wrong during the response.
What can be improved:
Identifying gaps in tools, processes, or training.
Documenting these findings:
This documentation is formalized into reports.
These reports are crucial for several reasons. They are used to update incident response plans, refine security controls, provide evidence for legal or compliance purposes, and train staff to handle future incidents more effectively. The act of "generating reports" is a defining output of the Lessons Learned phase.
Why the other options are incorrect:
A. Recovery:
This phase focuses on actions taken to restore systems to normal operation. This includes restoring data from clean backups, rebuilding compromised systems, removing malware, and re-enabling production services. While documentation occurs here (e.g., what steps were taken to restore a server), the primary goal is restoration, not comprehensive report generation for process improvement.
B. Preparation:
This is the foundational phase where an organization gets ready to handle incidents. Activities include creating the Incident Response Plan (IRP), assembling a team (CSIRT), acquiring tools, and providing training. While reports like the IRP itself are created in this phase, the question refers to generating reports about a specific incident that just occurred, which happens after the fact in the Lessons Learned phase.
D. Containment:
This phase is about stopping the incident from causing further damage. It involves short-term containment (e.g., isolating a network segment) and long-term containment (e.g., applying patches while the system is offline). The focus is on immediate, tactical action. Documentation in this phase is about logging the actions taken, but the formal, after-action reporting is saved for the Lessons Learned phase.
Reference:
This structure aligns with the incident response lifecycle as detailed in the NIST Special Publication 800-61, Revision 2, which is a key reference point for the CompTIA Security+ exam. The four common phases are often listed as:
Preparation
Detection and Analysis
Containment, Eradication, and Recovery
Post-Incident Activity (Lessons Learned)
An organization is struggling with scaling issues on its VPN concentrator and internet circuit due to remote work. The organization is looking for a software solution that will allow it to reduce traffic on the VPN and internet circuit, while still providing encrypted tunnel access to the data center and monitoring of remote employee internet traffic. Which of the following will help achieve these objectives?
A. Deploying a SASE solution to remote employees
B. Building a load-balanced VPN solution with redundant internet
C. Purchasing a low-cost SD-WAN solution for VPN traffic
D. Using a cloud provider to create additional VPN concentrators
Explanation:
Secure Access Service Edge (SASE) is a cloud-native architecture that combines comprehensive networking and security services (e.g., VPN, firewall as a service, zero-trust network access, secure web gateway, data loss prevention) into a single, scalable solution. By deploying SASE:
Reduces VPN traffic:
Remote employees can access cloud services and the internet directly through the SASE provider's global network, rather than backhauling all traffic through the organization's VPN concentrator and internet circuit. Only traffic destined for the data center would use an encrypted tunnel.
Provides encrypted tunnel access to the data center:
SASE includes zero-trust principles, ensuring secure, encrypted access to internal resources without requiring traditional VPNs.
Monitors remote employee internet traffic:
Integrated security services (like a secure web gateway) inspect and filter internet traffic for threats, regardless of the employee's location, ensuring compliance and security.
This addresses all the organization's goals:
scaling issues, reduced VPN/internet circuit traffic, secure data center access, and internet traffic monitoring.
Analysis of Incorrect Options:
B. Building a load-balanced VPN solution with redundant internet:
This might improve VPN availability and performance but does not reduce traffic—it adds infrastructure cost and complexity. All remote traffic still flows through the organization's internet circuit, exacerbating the scaling issue.
C. Purchasing a low-cost SD-WAN solution for VPN traffic:
SD-WAN optimizes network connectivity between sites (e.g., branches) but is not designed for remote employees. It does not inherently reduce VPN traffic or provide internet traffic monitoring for individual remote users.
D. Using a cloud provider to create additional VPN concentrators:
This scales VPN capacity but does not reduce traffic on the organization's internet circuit. All remote traffic still routes through the organization's network, and it adds cost without solving the fundamental inefficiency of backhauling internet traffic.
Reference:
This aligns with Domain 3.0: Security Architecture, specifically modern remote work solutions. SASE is endorsed by Gartner and frameworks like NIST SP 800-46 (Guide to Enterprise Telework and Remote Access Security) for its ability to consolidate security and networking while reducing reliance on traditional VPNs. It supports scalability, direct-to-cloud access, and consistent security policies for distributed users.
Which of the following are cases in which an engineer should recommend the decommissioning of a network device? (Select two).
A. The device has been moved from a production environment to a test environment.
B. The device is configured to use cleartext passwords.
C. The device is moved to an isolated segment on the enterprise network.
D. The device is moved to a different location in the enterprise.
E. The device's encryption level cannot meet organizational standards.
F. The device is unable to receive authorized updates.
Explanation:
E. The device's encryption level cannot meet organizational standards:
If a device cannot support the required encryption protocols (e.g., TLS 1.2+, AES-256), it poses a significant security risk. Data transmitted or stored by the device could be vulnerable to interception or theft. Decommissioning is necessary to maintain compliance and protect sensitive information.
F. The device is unable to receive authorized updates:
Devices that no longer receive security patches (e.g., end-of-life hardware/software) are exposed to unmitigated vulnerabilities. This makes them easy targets for attackers and could compromise the entire network. Decommissioning eliminates this risk.
Why the others are incorrect:
A. The device has been moved from a production environment to a test environment:
This does not require decommissioning; repurposing devices for testing is common and acceptable if properly isolated.
B. The device is configured to use cleartext passwords:
This is a security misconfiguration that should be fixed (e.g., by enabling encryption), not a reason to decommission the device outright.
C. The device is moved to an isolated segment on the enterprise network:
Isolation (e.g., network segmentation) is a risk mitigation strategy, not a reason for decommissioning.
D. The device is moved to a different location in the enterprise:
Relocation does not inherently justify decommissioning; devices are often moved for operational reasons.
Reference:
This aligns with SY0-701 Objective 3.4 ("Given a scenario, implement secure network designs") and risk management principles. Devices that cannot meet security standards (e.g., encryption, patch compliance) should be decommissioned to prevent vulnerabilities, as recommended by frameworks like NIST SP 800-53 (Security and Privacy Controls) and industry best practices.
A vendor needs to remotely and securely transfer files from one server to another using the command line. Which of the following protocols should be Implemented to allow for this type of access? (Select two).
A. SSH
B. SNMP
C. RDP
D. S/MIME
E. SMTP
F. SFTP
Explanation:
The requirement is to remotely and securely transfer files via the command line. The protocols must provide encryption for security and be suitable for command-line use:
A. SSH (Secure Shell):
This protocol provides encrypted remote command-line access to servers. While it is primarily used for secure remote administration, it can also facilitate secure file transfers when combined with tools like scp (Secure Copy Protocol), which runs over SSH.
F. SFTP (SSH File Transfer Protocol):
This is a secure file transfer protocol that operates over SSH. It is designed specifically for encrypted file transfers and is commonly used in command-line environments (e.g., via sftp commands).
Together, SSH and SFTP enable secure remote access and file transfers from the command line.
Why the others are incorrect:
B. SNMP (Simple Network Management Protocol):
Used for monitoring and managing network devices, not for file transfers.
C. RDP (Remote Desktop Protocol):
Provides graphical remote access to Windows systems, not command-line file transfers.
D. S/MIME (Secure/Multipurpose Internet Mail Extensions):
Used for encrypting email messages, not file transfers between servers.
E. SMTP (Simple Mail Transfer Protocol):
Used for sending email, not for secure file transfers.
Reference:
This aligns with Domain 3.1: Given a scenario, implement secure protocols. SSH and SFTP are standard protocols for secure remote access and file transfers, emphasizing confidentiality and integrity in data exchange.
A security engineer at a large company needs to enhance IAM to ensure that employees can only access corporate systems during their shifts. Which of the following access controls should the security engineer implement?
A. Role-based
B. Time-of-day restrictions
C. Least privilege
D. Biometric authentication
Explanation:
Time-of-day restrictions are a type of access control that limits when users can access systems or resources based on specific times or schedules. This directly addresses the requirement to ensure employees can only access corporate systems during their shifts. For example, access can be automatically granted at the start of a shift and revoked at the end.
Why the others are incorrect:
A. Role-based access control (RBAC):
This assigns permissions based on a user's role in the organization (e.g., manager, analyst). While RBAC controls what users can access, it does not inherently restrict when they can access it.
C. Least privilege:
This principle ensures users have only the minimum permissions necessary to perform their job functions. It focuses on limiting the scope of access (what resources), not the timing of access.
D. Biometric authentication:
This is a method for verifying identity (e.g., fingerprints, facial recognition) during login. It enhances security but does not control access based on time schedules.
Reference:
This aligns with SY0-701 Objective 3.3 ("Given a scenario, implement secure identity and access management"). Time-based access controls are a specific feature of IAM systems (e.g., in Active Directory or identity solutions) used to enforce temporal restrictions, as recommended for shift-based workers or compliance requirements.
Various company stakeholders meet to discuss roles and responsibilities in the event of a security breach affecting offshore offices. Which of the following is this an example of?
A. Tabletop exercise
B. Penetration test
C. Geographic dispersion
D. Incident response
Explanation:
A tabletop exercise is a discussion-based session where key stakeholders meet to walk through a simulated emergency scenario, such as a security breach. Participants review and discuss their roles, responsibilities, and the steps outlined in the incident response plan. This helps identify gaps, improve coordination, and ensure everyone understands their duties without the pressure of a real incident. The scenario described—stakeholders meeting to discuss roles and responsibilities for a breach affecting offshore offices—is a classic example of a tabletop exercise.
Why the others are incorrect:
B. Penetration test:
This is a hands-on, simulated attack on systems to identify vulnerabilities. It involves technical testing, not a discussion-based meeting about roles and responsibilities.
C. Geographic dispersion:
This refers to the strategic distribution of resources (e.g., data centers, offices) across different locations to reduce risk (e.g., from natural disasters). It is a design principle, not an exercise or meeting.
D. Incident response:
This is the overall process of handling a security breach, but the scenario describes a preparatory discussion (an exercise), not the actual response to an incident.
Reference:
This aligns with SY0-701 Objective 4.4 ("Given an incident, apply mitigation techniques or controls to secure an environment"). Tabletop exercises are a key part of incident response preparedness, as recommended by frameworks like NIST SP 800-61 ("Computer Security Incident Handling Guide"). They ensure stakeholders are ready to act effectively during a real incident.
Which of the following is a possible consequence of a VM escape?
A. Malicious instructions can be inserted into memory and give the attacker elevated permissions.
B. An attacker can access the hypervisor and compromise other VMs.
C. Unencrypted data can be read by a user in a separate environment.
D. Users can install software that is not on the manufacturer's approved list.
Explanation:
A VM (Virtual Machine) escape is one of the most severe attacks in a virtualized environment.It occurs when an attacker breaks out of the isolated environment of a virtual machine to interact directly with the hypervisor.
B. An attacker can access the hypervisor and compromise other VMs is correct.
This is the definition and primary consequence of a VM escape. The hypervisor is the software, firmware, or hardware that creates and runs virtual machines. If an attacker escapes a VM, they gain unauthorized access to the hypervisor. From this privileged position, they can potentially control, monitor, or attack any other VM running on the same host, completely bypassing the isolation that is the foundation of virtualization security.
A. Malicious instructions can be inserted into memory and give the attacker elevated permissions.
This describes a buffer overflow attack, where code is executed in memory to elevate privileges within a single system (either a VM or a physical machine). It does not describe the specific action of breaking out of a virtualized environment to attack the hypervisor.
C. Unencrypted data can be read by a user in a separate environment.
This describes a data confidentiality breach, which could happen in many ways (e.g., misconfigured storage, insider threat). It is not a specific consequence of a VM escape, though it could be a result of one if the attacker uses their hypervisor access to read data from other VMs.
D. Users can install software that is not on the manufacturer's approved list.
This describes a policy violation or potentially sideloading on a mobile device. It is unrelated to virtualization and hypervisor security.
Reference:
CompTIA Security+ SY0-701 Objective 3.2: "Explain security implications of embedded and specialized systems." Virtualization security is a key topic under this objective. Understanding hypervisor vulnerabilities and attacks like VM escape is critical for securing modern data center environments.
| Page 25 out of 60 Pages |
| Previous |