Which of the following best describes the practice of researching laws and regulations related to information security operations within a specific industry?
A. Compliance reporting
B. GDPR
C. Due diligence
D. Attestation
Explanation:
Due diligence is the proactive, ongoing process of researching, understanding, and complying with laws, regulations, and standards that apply to an organization's operations. In the context of information security, this involves continuously identifying and analyzing legal and regulatory requirements (such as GDPR, HIPAA, PCI DSS, etc.) that are relevant to the organization's specific industry and ensuring that security practices are aligned to meet those obligations.
Why not A?
Compliance reporting: This is the act of demonstrating adherence to laws and regulations through reports, audits, or certifications. It is an output or result of performing due diligence, not the research process itself.
Why not B?
GDPR: The General Data Protection Regulation (GDPR) is a specific regulation governing data privacy in the European Union. It is an example of a law that might be researched as part of due diligence, but it is not the term that describes the overall practice of researching all applicable laws and regulations.
Why not D?
Attestation: This is a formal declaration or verification (often by a third party) that certain controls or processes are in place and effective. Like reporting, it is a method for proving compliance, not the research process behind it.
Reference:
Domain 5.5: "Explain the importance of compliance." The SY0-701 objectives emphasize the need for organizations to understand their legal and regulatory requirements. Due diligence is the foundational practice that ensures an organization is aware of these obligations and can build its security program accordingly.
A security analyst reviews domain activity logs and notices the following:
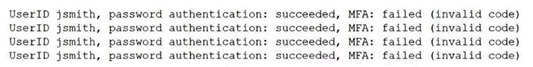
Which of the following is the best explanation for what the security analyst has discovered?
A. The user jsmith's account has been locked out.
B. A keylogger is installed on [smith's workstation
C. An attacker is attempting to brute force ismith's account.
D. Ransomware has been deployed in the domain.
Explanation:
The log entries show a pattern highly indicative of a brute force attack:
Multiple repeated login attempts using the same username (jsmith) and password (password).
Each attempt results in successful authentication (likely because the password is correct, suggesting the attacker has compromised the password).
However, each attempt fails at the MFA (Multi-Factor Authentication) stage due to an "invalid code."
This pattern suggests that an attacker has obtained jsmith's password (e.g., via phishing, a data breach, or credential stuffing) but is now trying to bypass the MFA protection by repeatedly guessing or submitting invalid MFA codes. The goal is to eventually guess a valid MFA code or exploit a weakness in the MFA implementation.
Why not A?
The account does not appear locked out, as authentication continues to succeed (password is accepted). Lockouts typically prevent further authentication attempts entirely.
Why not B?
A keylogger might explain how the password was stolen initially, but the logs show active ongoing attacks from an external source (repeated MFA failures), not local keylogging activity.
Why not D?
There is no evidence of ransomware in these logs (e.g., file encryption, ransom notes). The activity is focused on authentication attempts.
Reference:
Domain 1.3: "Given a scenario, analyze potential indicators associated with application attacks." Brute force attacks (including MFA bypass attempts) are a common attack vector. The pattern of successful password authentication followed by MFA failures is a classic sign of an attacker trying to compromise an account protected by MFA.
Which of the following is the primary purpose of a service that tracks log-ins and time spent using the service?
A. Availability
B. Accounting
C. Authentication
D. Authorization
Explanation:
The question describes a service that tracks user activity, specifically log-ins and time spent. This is a classic function of monitoring and recording user actions for the purposes of auditing, billing, and accountability.
B. Accounting is correct.
In the context of AAA (Authentication, Authorization, and Accounting) security services, accounting is the process of tracking and logging user activities and resource usage. This includes recording when users log in, how long they are connected, what commands they execute, and the data they access. The primary purpose is to create an audit trail for security reviews, compliance, billing (e.g., for paid services), and monitoring for suspicious behavior.
A. Availability is incorrect.
Availability ensures that systems and data are accessible to authorized users when needed. It is a core security objective (part of the CIA triad: Confidentiality, Integrity, Availability) but is not related to tracking user log-ins or usage time.
C. Authentication is incorrect.
Authentication is the process of verifying a user's identity (e.g., with a password or biometric scan). It answers the question, "Who are you?" While authentication is necessary for a user to gain access, it does not involve tracking their activity after they are logged in.
D. Authorization is incorrect.
Authorization determines what an authenticated user is allowed to do or access (e.g., read a file, run a program). It answers the question, "What are you allowed to do?" Like authentication, it is a prerequisite for access but does not involve logging or tracking the user's actions during their session.
Reference:
CompTIA Security+ SY0-701 Objective 3.8: "Explain authentication and authorization concepts." The AAA framework (Authentication, Authorization, Accounting) is a key concept. Accounting is explicitly defined as the process that audits and logs what users do and how long they use resources, which aligns perfectly with the service described in the question.
A company needs to provide administrative access to internal resources while minimizing the traffic allowed through the security boundary. Which of the following methods is most secure?
A. Implementing a bastion host
B. Deploying a perimeter network
C. Installing a WAF
D. Utilizing single sign-on
Explanation:
A bastion host is a specialized server designed to withstand attacks and provide a secure gateway for administrative access to internal resources from external networks (e.g., the internet). It is heavily hardened (minimized attack surface, strict access controls, extensive logging) and serves as a single point of entry for administrative traffic. By funneling all administrative access through this dedicated host, the company can:
Minimize traffic through the security boundary: Only traffic directed to the bastion host is allowed, reducing the exposure of internal resources.
Enforce strict security policies:
The bastion host can be configured with rigorous authentication (e.g., multi-factor authentication) and monitoring.
Isolate internal systems:
Direct access to internal resources is blocked; administrators must first access the bastion host, which then proxies or relays connections to internal systems under controlled conditions.
This approach is more secure than opening multiple administrative pathways into the network.
Analysis of Incorrect Options:
B. Deploying a perimeter network (DMZ):
A DMZ is a segmented network that hosts publicly accessible services (e.g., web servers, email servers). While it isolates these services from the internal network, it does not specifically secure administrative access to internal resources. Administrative access should not be provided from the DMZ; it should be further controlled via a bastion host or similar secure method.
C. Installing a WAF (Web Application Firewall):
A WAF protects web applications from attacks (e.g., SQL injection, XSS). It is irrelevant to securing general administrative access (e.g., SSH, RDP, database admin tools) unless the administrative interface is web-based. Even then, a WAF alone does not minimize traffic or provide the centralized control of a bastion host.
D. Utilizing single sign-on (SSO):
SSO improves usability and security by allowing users to authenticate once to access multiple applications. However, it does not restrict or minimize traffic through the security boundary; it only simplifies authentication. SSO could be used in conjunction with a bastion host for stronger access control but is not a substitute for it.
Reference:
This question falls under Domain 3.0: Security Architecture, specifically network design and secure access methodologies. Bastion hosts are a best practice for providing secure remote administrative access, aligning with principles of defense-in-depth and network segmentation. They are often part of a zero-trust architecture, where access is tightly controlled and monitored.
An organization is required to maintain financial data records for three years and customer data for five years. Which of the following data management policies should the organization implement?
A. Retention
B. Destruction
C. Inventory
D. Certification
Explanation: The organization should implement a retention policy to ensure that financial data records are kept for three years and customer data for five years. A retention policy specifies how long different types of data should be maintained and when they should be deleted. Retention: Ensures that data is kept for a specific period to comply with legal, regulatory, or business requirements. Destruction: Involves securely deleting data that is no longer needed, which is part of the retention lifecycle but not the primary focus here. Inventory: Involves keeping track of data assets, not specifically about how long to retain data. Certification: Ensures that processes and systems meet certain standards, not directly related to data retention periods.
A company is expanding its threat surface program and allowing individuals to security test the company’s internet-facing application. The company will compensate researchers based on the vulnerabilities discovered. Which of the following best describes the program the company is setting up?
A. Open-source intelligence
B. Bug bounty
C. Red team
D. Penetration testing
Explanation: A bug bounty is a program that rewards security researchers for finding and reporting vulnerabilities in an application or system. Bug bounties are often used by companies to improve their security posture and incentivize ethical hacking. A bug bounty program typically defines the scope, rules, and compensation for the researchers. References = CompTIA Security+ Study Guide with over 500 Practice Test Questions: Exam SY0-701, 9th Edition, Chapter 1, page 10. CompTIA Security+ (SY0-701) Certification Exam Objectives, Domain 1.1, page 2.
A company that is located in an area prone to hurricanes is developing a disaster recovery plan and looking at site considerations that allow the company to immediately continue operations. Which of the following is the best type of site for this company?
A. Cold
B. Tertiary
C. Warm
D. Hot
Explanation: For a company located in an area prone to hurricanes and needing to immediately continue operations, the best type of site is a hot site. A hot site is a fully operational offsite data center that is equipped with hardware, software, and network connectivity and is ready to take over operations with minimal downtime. Hot site: Fully operational and can take over business operations almost immediately after a disaster. Cold site: A basic site with infrastructure in place but without hardware or data, requiring significant time to become operational. Tertiary site: Not a standard term in disaster recovery; it usually refers to an additional backup location but lacks the specifics of readiness. Warm site: Equipped with hardware and connectivity but requires some time and effort to become fully operational, not as immediate as a hot site.
A security administrator identifies an application that is storing data using MD5. Which of the following best identifies the vulnerability likely present in the application?
A. Cryptographic
B. Malicious update
C. Zero day
D. Side loading
Explanation: The vulnerability likely present in the application that is storing data using MD5 is a cryptographic vulnerability. MD5 is considered to be a weak hashing algorithm due to its susceptibility to collision attacks, where two different inputs produce the same hash output, compromising data integrity and security. Cryptographic: Refers to vulnerabilities in cryptographic algorithms or implementations, such as the weaknesses in MD5. Malicious update: Refers to the intentional injection of harmful updates, not related to the use of MD5. Zero day: Refers to previously unknown vulnerabilities for which no patch is available, not specifically related to MD5. Side loading: Involves installing software from unofficial sources, not directly related to the use of MD5. Reference: CompTIA Security+ SY0-701 Exam Objectives, Domain 1.4 - Explain the importance of using appropriate cryptographic solutions (MD5 vulnerabilities).
Which of the following is the most likely to be included as an element of communication in a security awareness program?
A. Reporting phishing attempts or other suspicious activities
B. Detecting insider threats using anomalous behavior recognition
C. Verifying information when modifying wire transfer data
D. Performing social engineering as part of third-party penetration testing
Explanation:
A security awareness program is designed to educate and empower employees to become active participants in an organization's security. A fundamental element of this is establishing clear, simple, and well-communicated channels for employees to report security concerns. Teaching employees how to recognize and, most importantly, immediately report phishing attempts and other suspicious activities is a cornerstone of any effective security awareness program. This turns the human layer into a defensive asset.
Why the others are incorrect:
B) Detecting insider threats using anomalous behavior recognition:
This describes a technical control (e.g., User and Entity Behavior Analytics - UEBA software) or a task for the security operations center (SOC), not a communicative element of an awareness program aimed at general employees.
C) Verifying information when modifying wire transfer data:
This is a specific procedure or action that would be taught during training (e.g., for accounting staff), often as part of a response to Business Email Compromise (BEC) scams. However, it is a specific policy compliance item, not the broad, foundational element of communication itself (like a reporting mechanism) that is central to the entire awareness program.
D) Performing social engineering as part of third-party penetration testing:
This is an activity conducted by security professionals or ethical hackers to test the effectiveness of the awareness program. It is not an element of communication within the program for employees.
Reference:
This aligns with SY0-701 Objective 5.5 ("Explain the importance of policies to organizational security"), specifically the requirement for a security awareness and training policy. This policy mandates programs that include communication elements such as reporting procedures for incidents, which is a primary method for engaging employees and improving the organization's overall security posture.
An analyst is reviewing an incident in which a user clicked on a link in a phishing email. Which of the following log sources would the analyst utilize to determine whether the connection was successful?
A. Network
B. System
C. Application
D. Authentication
Explanation:
To determine whether the connection to the link in the phishing email was successful, the analyst should review network logs. These logs capture details about network connections, such as:
Outbound HTTP/HTTPS requests from the user's device.
DNS queries resolving the phishing domain.
Successful establishment of TCP/IP connections to the external server.
Data transfers (e.g., indicating a payload was downloaded).
Network logs (e.g., from firewalls, proxies, or IDS/IPS) provide direct evidence of whether the user's device communicated with the malicious server.
Why not the others?
B. System logs:
Focus on OS-level events (e.g., logons, process creation) but may not explicitly show successful external connections.
C. Application logs:
Record application-specific actions (e.g., browser activity) but might not be as comprehensive for network-level verification.
D. Authentication logs:
Track login attempts and access controls, unrelated to outbound connections.
Reference:
Domain 4.3: "Given an incident, utilize appropriate data sources to support an investigation." Network logs are critical for tracing communication with external entities, a key step in phishing incident analysis. The SY0-701 objectives emphasize using diverse log sources for forensic investigations.
An administrator notices that several users are logging in from suspicious IP addresses. After speaking with the users, the administrator determines that the employees were not logging in from those IP addresses and resets the affected users’ passwords. Which of the following should the administrator implement to prevent this type of attack from succeeding in the future?
A. Multifactor authentication
B. Permissions assignment
C. Access management
D. Password complexity
Explanation:
The scenario describes a likely credential theft attack (e.g., phishing, keylogging, or password reuse) where an attacker obtained user passwords and logged in from suspicious locations. Resetting passwords addresses the immediate breach but does not prevent future attacks if credentials are stolen again.
Multifactor authentication (MFA) adds an extra layer of security by requiring users to provide two or more verification factors (e.g., something they know [password] + something they have [authenticator app code] or something they are [biometrics]). Even if a password is compromised, the attacker cannot authenticate without the second factor, effectively preventing unauthorized logins from suspicious IP addresses.
Why the others are incorrect:
B. Permissions assignment:
This involves granting users appropriate access rights (principle of least privilege). While important for security, it does not prevent initial unauthorized access via stolen credentials.
C. Access management:
This is a broad term encompassing policies and tools for controlling user access. MFA is a specific component of access management, but the other options are less direct. Permissions assignment (B) is part of access management but does not solve the credential theft issue.
D. Password complexity:
Enforcing strong passwords is a good practice, but complex passwords can still be stolen through phishing, malware, or data breaches. MFA provides stronger protection beyond password strength.
Reference:
This aligns with SY0-701 Objective 3.3 ("Given a scenario, implement secure identity and access management"). Multifactor authentication (MFA) is a critical defense against credential theft and unauthorized access, as emphasized in security frameworks like NIST SP 800-63B and compliance standards (e.g., PCI DSS, GDPR). It is specifically recommended to mitigate risks from stolen passwords.
A client demands at least 99.99% uptime from a service provider's hosted security services. Which of the following documents includes the information the service provider should return to the client?
A. MOA
B. SOW
C. MOU
D. SLA
Explanation:
D) SLA (Service Level Agreement) is the correct answer.
An SLA is a formal document between a service provider and a client that defines the level of service expected, including specific metrics like uptime guarantees (e.g., 99.99%). It outlines:
Service performance standards (availability, responsiveness).
Responsibilities of both parties.
Remedies or penalties if the service provider fails to meet the agreed-upon levels (e.g., service credits).
In this scenario, the client's demand for 99.99% uptime is a key performance indicator (KPI) that should be documented in the SLA.
Why the others are incorrect:
A) MOA (Memorandum of Agreement):
An MOA is a non-binding document that expresses a common line of action between parties. It is less formal and does not typically include detailed performance metrics like uptime.
B) SOW (Statement of Work):
An SOW defines the specific tasks, deliverables, and timeline for a project. It focuses on the "what" and "when" of work to be performed, not ongoing service levels like uptime.
C) MOU (Memorandum of Understanding):
An MOU is a preliminary agreement that outlines the intent to collaborate. It is often used before formal contracts are drafted and does not include enforceable service levels.
Reference:
This question tests knowledge of Domain 5.3: Explain the importance of policies to organizational security. SLAs are critical for managing relationships with third-party providers and ensuring accountability, as emphasized in the SY0-701 objectives. They are legally binding and specifically address measurable service standards like uptime, which aligns with the client’s demand.
| Page 17 out of 60 Pages |
| Previous |