Topic 3: Exam Pool C
A security analyst b concerned about traffic initiated to the dark web from the corporate LAN. Which of the following networks should he analyst monitor?
A.
SFTP
B.
AS
C.
Tor
D.
IoC
Tor
An attacker is attempting, to harvest user credentials on a client's website. A security
analyst notices multiple attempts of random usernames and passwords. When the analyst
types in a random username and password. the logon screen displays the following
message:
Which of the following should the analyst recommend be enabled?
A.
Input validation
B.
Obfuscation
C.
Error handling
D.
Username lockout
Obfuscation
A financial analyst has been accused of violating the company’s AUP and there is forensic
evidence to substantiate the allegation. Which of the following would dispute the analyst’s
claim of innocence?
A.
Legal hold
B.
Order of volatility
C.
Non-repudiation
D.
Chain of custody
Chain of custody
A security operations analyst is using the company's SIEM solution to correlate alerts.
Which of the following stages of the incident response process is this an example of?
A.
Eradication
B.
Recovery
C.
Identification
D.
Preparation
Identification
A company's help desk received several AV alerts indicating Mimikatz attempted to run on
the remote systems. Several users also reported that the new company flash drives they
picked up in the
break room only have 512KB of storage. Which of the following is MOST likely the cause?
A.
The GPO prevents the use of flash drives, which triggers a false positive AV indication
and restricts the drives to only 512KB of storage.
B.
The new flash drives need a driver that is being blocked by the AV software because the
flash drives are not on the application's allow list, temporarily restricting the drives to
512KB of storage.
C.
The new flash drives are incorrectly partitioned, and the systems are automatically trying
to use an unapproved application to repartition the drives.
D.
The GPO blocking the flash drives is being bypassed by a malicious flash drive that is
attempting to harvest plaintext credentials from memory.
The GPO blocking the flash drives is being bypassed by a malicious flash drive that is
attempting to harvest plaintext credentials from memory.
A customer called a company's security team to report that all invoices the customer has
received over the last five days from the company appear to have fraudulent banking
details. An investigation
into the matter reveals the following
* The manager of the accounts payable department is using the same password across
multiple external websites and the corporate account.
* One of the websites the manager used recently experienced a data breach.
* The manager's corporate email account was successfully accessed in the last five days
by an IP address located in a foreign country
Which of the following attacks has MOST likely been used to compromise the manager's
corporate account?
A.
Remote access Trojan
B.
Brute-force
C.
Dictionary
D.
Credential stuffing
E.
Password spraying
Credential stuffing
The spread of misinformation surrounding the outbreak of a novel virus on election day led to eligible voters choosing not to take the risk of going to the polls This is an example of:
A.
prepending.
B.
an influence campaign
C.
a watering-hole attack
D.
intimidation
E.
information elicitation
intimidation
A security analyst is investigating a vulnerability in which a default file permission was set
incorrectly. The company uses non-credentialed scanning for vulnerability management.
Which of the following tools can the analyst use to verify the permissions?
A.
ssh
B.
chmod
C.
1s
D.
setuid
E.
nessus
F.
nc
chmod
Which of the following would be BEST for a technician to review to determine the total risk
an organization can bear when assessing a "cloud-first" adoption strategy?
A.
Risk matrix
B.
Risk tolerance
C.
Risk register
D.
Risk appetite
Risk appetite
A500 is implementing an insider threat detection program, The primary concern is that users may be accessing confidential data without authorization. Which of the fallowing should be deployed to detect a potential insider threat?
A.
A honeyfile
B.
A DMZ
C.
ULF
D.
File integrity monitoring
A honeyfile
A company just developed a new web application for a government agency. The
application must be assessed and authorized prior to being deployed. Which of the following is required to assess the vulnerabilities resident in the application?
A.
Repository transaction logs
B.
Common Vulnerabilities and Exposures
C.
Static code analysis
D.
Non-credentialed scans
Common Vulnerabilities and Exposures
A security analyst was deploying a new website and found a connection attempting to authenticate on the site's portal. While Investigating The incident, the analyst identified the following Input in the username field:
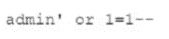
Which of the following BEST explains this type of attack?
A.
DLL injection to hijack administrator services
B.
SQLi on the field to bypass authentication
C.
Execution of a stored XSS on the website
D.
Code to execute a race condition on the server
Execution of a stored XSS on the website
| Page 25 out of 74 Pages |
| Previous |