Topic 4: Exam Pool D (NEW)
A SECURITY ANALYST NEEDS TO FIND REAL-TIME DATA ON THE LATEST
MALWARE AND loCs WHICH OF THE FOLLOWING BEST DESCRIBE THE SOLUTION
THE ANALYST SHOULD PERSUE?
A.
ADVISORIES AND BULLETINS
B.
THREAT FEEDS
C.
SECURITY NEWS ARTICLES
D.
PEER-REVIEWED CONTENT
THREAT FEEDS
A Chief Executive Officer (CEO) is dissatisfied with the level of service from the company's
new service provider. The service provider is preventing the CEO from sending email from
a work account to a personal account. Which of the following types of service providers is
being used?
A.
Telecommunications service provider
B.
Cloud service provider
C.
Master managed service provider
D.
Managed security service provider
Cloud service provider
When implementing automation with loT devices, which of the following should be
considered FIRST to keep the network secure?
A.
Z-Wave compatibility
B.
Network range
C.
Zigbee configuration
D.
Communication protocols
Communication protocols
An information security officer at a credit card transaction company is conducting a framework-mapping exercise with the internal controls. The company recently established a new office in Europe. To which of the following frameworks should the security officer map the existing controls?
(Select TWO).
A.
ISO
B.
PCI DSS
C.
SOC
D.
GDPR
E.
CSA
F.
NIST
PCI DSS
GDPR
A security engineer is installing a WAF to protect the company’s website from malicious
web requests over SSL. Which of the following is needed to meet the objective?
A.
A reverse proxy
B.
A decryption certificate
C.
A split-tunnel VPN
D.
Load-balanced servers
A reverse proxy
While reviewing the wireless router, the systems administrator of a small business determines someone is spoofing the MAC address of an authorized device. Given the table below:
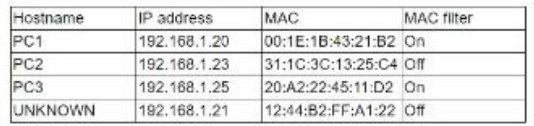
Which of the following should be the administrator's NEXT step to detect if there is a rogue system without impacting availability?
A.
Conduct a ping sweep
B.
Physically check each system
C.
Deny Internet access to the "UNKNOWN" hostname
D.
Apply MAC filtering
Apply MAC filtering
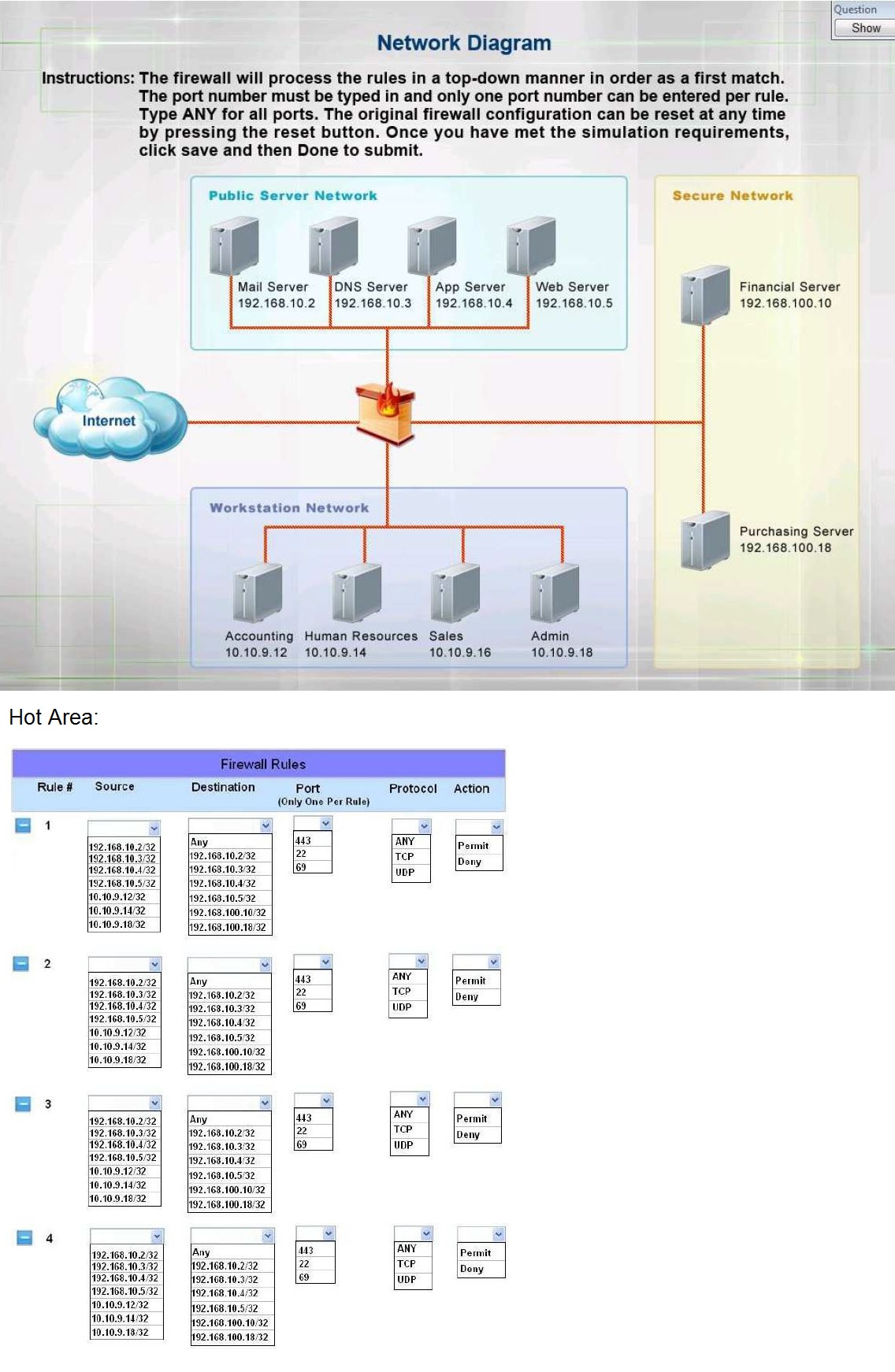
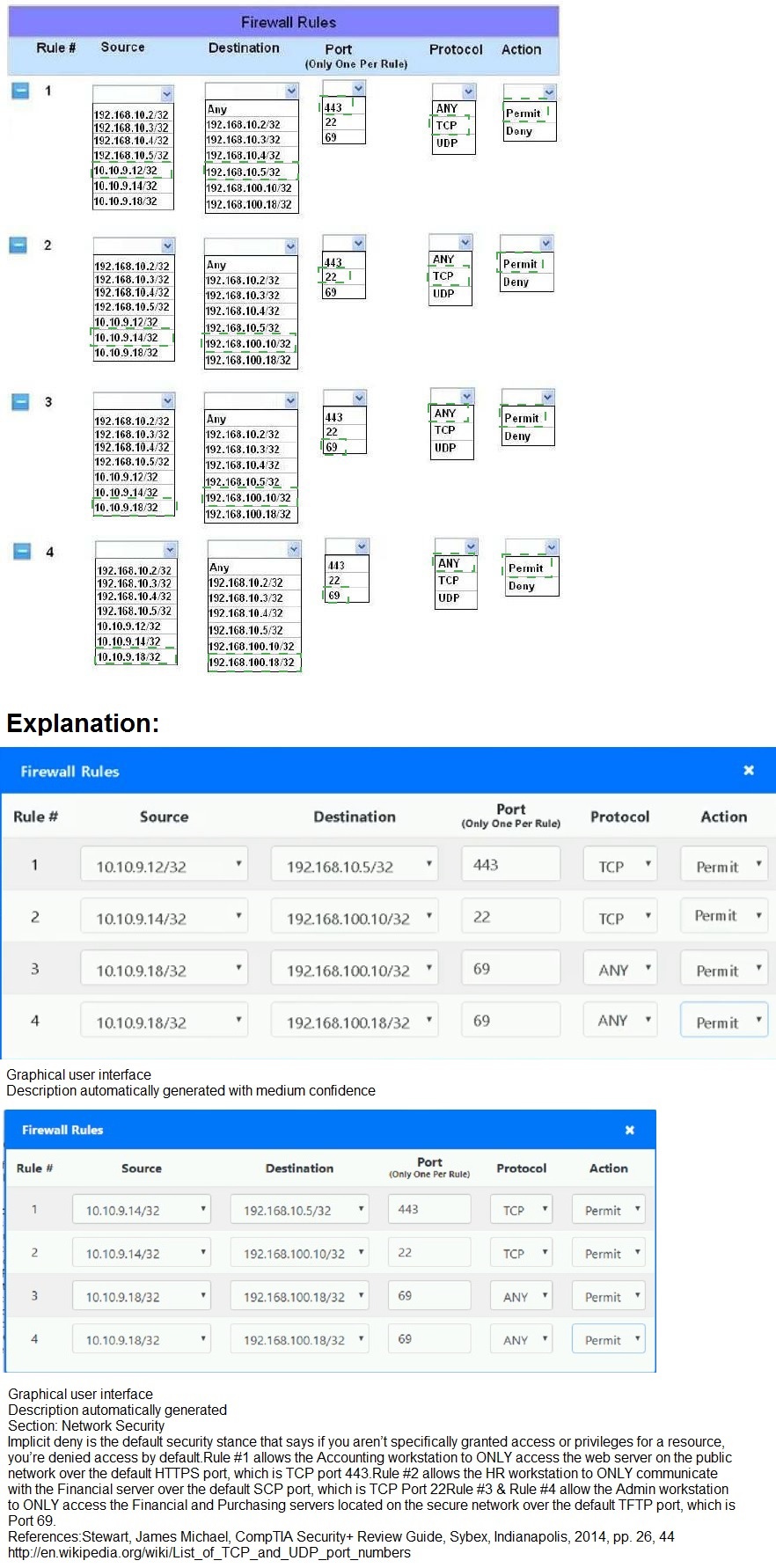
The security administrator has installed a new firewall which implements an implicit DENY
policy by default.
INSTRUCTIONS:
Click on the firewall and configure it to allow ONLY the following communication.
1. The Accounting workstation can ONLY access the web server on the public network
over the default HTTPS port. The accounting workstation should not access other
networks.
2. The HR workstation should be restricted to communicate with the Financial server
ONLY, over the default SCP port
3. The Admin workstation should ONLY be able to access the servers on the secure
network over the default TFTP port.
Instructions: The firewall will process the rules in a top-down manner in order as a first
match The port number must be typed in and only one port number can be entered per rule
Type ANY for all ports. The original firewall configuration can be reset at any time by
pressing the reset button. Once you have met the simulation requirements, click save and
then Done to submit.
The cost of '©movable media and the security risks of transporting data have become too
great for a laboratory. The laboratory has decided to interconnect with partner laboratones
to make data transfers easier and more secure. The Chief Security Officer <CSO) has
several concerns about proprietary data being exposed once the interconnections are
established. Which of the following security features should the network administrator
implement lo prevent unwanted data exposure to users in partner laboratories?
A.
VLAN zoning with a file-transfer server in an external-facing zone
B.
DLP running on hosts to prevent file transfers between networks
C.
NAC that permits only data-transfer agents to move data between networks
D.
VPN with full tunneling and NAS authenticating through the Active Directory
DLP running on hosts to prevent file transfers between networks
Remote workers in an organization use company-provided laptops with locally installed
applications and locally stored data Users can store data on a remote server using an
encrypted connection. The organization discovered data stored on a laptop had been made
available to the public Which of the following security solutions would mitigate the risk of
future data disclosures?
A.
FDE
B.
TPM
C.
HIDS
D.
VPN
FDE
Which of the following environments utilizes dummy data and is MOST likely to be installed
locally on a system that allows code to be assessed directly and modified easily with each
build?
A.
Production
B.
Test
C.
Staging
D.
Development
Test
An organization relies on third-party video conferencing to conduct daily business. Recent
security changes now require all remote workers to utilize a VPN to corporate resources.
Which of the following would BEST maintain
high-quality video conferencing while minimizing latency when connected to the VPN?
A.
Using geographic diversity to have VPN terminators closer to end users
B.
Utilizing split tunneling so only traffic for corporate resources is encrypted
C.
Purchasing higher-bandwidth connections to meet the increased demand
D.
Configuring QoS properly on the VPN accelerators
Configuring QoS properly on the VPN accelerators
Which of the following is a difference between a DRP and a BCP?
A.
A BCP keeps operations running during a disaster while a DRP does not.
B.
A BCP prepares for any operational interruption while a DRP prepares for natural
disasters
C.
A BCP is a technical response to disasters while a DRP is operational.
D.
A BCP Is formally written and approved while a DRP is not.
A BCP is a technical response to disasters while a DRP is operational.
| Page 23 out of 74 Pages |
| Previous |