Topic 5: Exam Pool E (NEW)
A Chief Information Officer receives an email stating a database will be encrypted within 24 hours unless a payment of $20,000 is credited to the account mentioned In the email. This BEST describes a scenario related to:
A.
whaling.
B.
smishing.
C.
spear phishing
D.
vishing
spear phishing
A nationwide company is experiencing unauthorized logins at all hours of the day. The
logins appear to originate from countries in which the company has no employees. Which
of the following controls.
should the company consider using as part of its IAM strategy? (Select TWO).
A.
A complex password policy
B.
Geolocation
C.
An impossible travel policy
D.
Self-service password reset
E.
Geofencing
F.
Time-based logins
A complex password policy
Geolocation
A systems administrator needs to install the same X.509 certificate on multiple servers. Which of the following should the administrator use?
A.
Key escrow
B.
A self-signed certificate
C.
Certificate chaining
D.
An extended validation certificate
Certificate chaining
During an investigation, a security manager receives notification from local authorities mat
company proprietary data was found on a former employees home computer, The former
employee’s corporate workstation has since been repurposed, and the data on the hard
drive has been overwritten Which of the following would BEST provide the security
manager with enough details to determine when the data was removed from the company
network?
A.
Properly congured hosts with security logging
B.
Properly congured endpoint security tool with darting
C.
Properly congured SIEM with retention policies
D.
Properly congured USB blocker with encryption
Properly congured hosts with security logging
The new Chief Executive Officer (CEO) of a large company has announced a partnership
with a vendor that will provide multiple collaboration applications t
make remote work easier. The company has a geographically dispersed staff located in
numerous remote offices in different countries. The company's IT
administrators are concerned about network traffic and load if all users simultaneously
download the application. Which of the following would work BEST to
allow each geographic region to download the software without negatively impacting the
corporate network?
A.
Update the host IDS rules.
B.
Enable application whitelisting
C.
Modify the corporate firewall rules
D.
Deploy all applications simultaneously.
Enable application whitelisting
A grocery store is expressing security and reliability concerns regarding the on-site backup
strategy currently being performed by locally attached disks. The main concerns are the
physical security of the backup media and the durability of the data stored on these devices
Which of the following is a cost-effective approach to address these concerns?
A.
Enhance resiliency by adding a hardware RAID.
B.
Move data to a tape library and store the tapes off site
C.
Install a local network-attached storage.
D.
Migrate to a cloud backup solution
Migrate to a cloud backup solution
A security analyst is reviewing the following output from a system:

Which of the following is MOST likely being observed?
A.
ARP poisoning
B.
Man in the middle
C.
Denial of service
D.
DNS poisoning
Denial of service
Which of the following is a reason why an organization would define an AUP?
A.
To define the lowest level of privileges needed for access and use of the organization's resources.
B.
To define the set of rules and behaviors for users of the organization's IT systems
C.
To define the intended partnership between two organizations
D.
To define the availability and reliability characteristics between an IT provider and
consumer
To define the lowest level of privileges needed for access and use of the organization's resources.
An organization's finance department is implementing a policy to protect against collusion.
Which of the following control types and corresponding procedures should the
organization implement to fulfill this policy's requirement? (Select TWO).
A.
Corrective
B.
Deterrent
C.
Preventive
D.
Mandatory vacations
E.
Job rotation
F.
Separation of duties
Mandatory vacations
Job rotation
An.. that has a large number of mobile devices is exploring enhanced security controls to
manage unauthorized access if a device is lost or stolen. Specifically, if mobile devices are
more
than 3mi (4 8km) from the building, the management team would like to have the security
team alerted and server resources restricted on those devices. Which of the following
controls should the organization implement?
A.
Geofencing
B.
Lockout
C.
Near-field communication
D.
GPS tagging
Geofencing
An analyst Is generating a security report for the management team. Security guidelines
recommend disabling all listening unencrypted services. Given this output from Nmap:
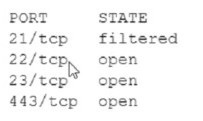
Which of the following should the analyst recommend to disable?
A.
21/tcp
B.
22/tcp
C.
23/tcp
D.
443/tcp
23/tcp
Which of the following would cause a Chief Information Security Officer (CISO) the MOST
concern regarding newly installed Internet-accessible 4K surveillance cameras?
A.
An inability to monitor 100%, of every facility could expose the company to unnecessary
risk.
B.
The cameras could be compromised if not patched in a timely manner.
C.
Physical security at the facility may not protect the cameras from theft.
D.
Exported videos may take up excessive space on the file servers.
An inability to monitor 100%, of every facility could expose the company to unnecessary
risk.
| Page 21 out of 74 Pages |
| Previous |