Topic 1: Exam Pool A
The analyst then sends an internal user a link to the new website for testing purposes, and when the user clicks the link, the analyst is able to browse the website with the following
URL:
http://dev-site.comptia.org/home/show.php?sessionID=98988475&loc=us
Which of the following application attacks is being tested?
A.
Pass-the-hash
B.
Session replay
C.
Object deference
D.
Cross-site request forgery
Session replay
A company is setting up a web server on the Internet that will utilize both encrypted and
unencrypted web-browsing protocols. A security engineer runs a port scan against the server from the Internet and sees the following output:

Which of the following steps would be best for the security engineer to take NEXT?
A.
Allow DNS access from the internet.
B.
Block SMTP access from the Internet
C.
The SIP traffic logs
D.
The SNMP logs
Allow DNS access from the internet.
While checking logs, a security engineer notices a number of end users suddenly downloading files with the
.tar.gz extension. Closer examination of the files reveals they are PE32 files. The end users
state they did not initiate any of the downloads. Further investigation reveals the end users
all clicked on an external email containing an infected MHT file with an href link a week
prior. Which of the following is MOST likely occurring?
A.
A RAT was installed and is transferring additional exploit tools.
B.
The workstations are beaconing to a command-and-control server.
C.
A logic bomb was executed and is responsible for the data transfers.
D.
A fireless virus is spreading in the local network environment.
A RAT was installed and is transferring additional exploit tools.
An analyst visits an internet forum looking for information about a tool. The analyst finds a threat that appears to contain relevant information. One of the posts says the following: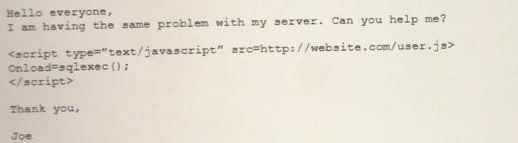
Which of the following BEST describes the attack that was attempted against the forum readers?
A.
SOU attack
B.
DLL attack
C.
XSS attack
D.
API attack
XSS attack
An organization routes all of its traffic through a VPN Most users are remote and connect
into a corporate datacenter that houses confidential information There is a firewall at the
Internet border followed by a DIP appliance, the VPN server and the datacenter itself.
Which of the following is the WEAKEST design element?
A.
The DLP appliance should be integrated into a NGFW.
B.
Split-tunnel connections can negatively impact the DLP appliance's performance
C.
Encrypted VPN traffic will not be inspected when entering or leaving the network
D.
Adding two hops in the VPN tunnel may slow down remote connections
Encrypted VPN traffic will not be inspected when entering or leaving the network
Which of the following disaster recovery tests is The LEAST time-consuming for the
disaster recovery team?
A.
Tabletop
B.
Parallel
C.
Full interruption
D.
Simulation
Simulation
Which of the following incident response steps involves actions to protect critical systems while maintaining business operations?
A.
AInvestigation
B.
Containment
C.
Recovery
D.
Lessons learned
Containment
An organization’s help desk is flooded with phone calls from users stating they can no longer access certain websites. The help desk escalates the issue to the security team, as
these websites were accessible the previous day. The security analysts run the following
command: ipconfig /flushdns, but the issue
persists. Finally, an analyst changes the DNS server for an impacted machine, and the
issue goes away. Which of the following attacks MOST likely occurred on the original DNS
server?
A.
DNS cache poisoning
B.
Domain hijacking
C.
Distributed denial-of-service
D.
DNS tunneling
Domain hijacking
An enterprise has hired an outside security firm to conduct penetration testing on its network and applications. The firm has only been given the documentation available to the customers of the applications. Which of the following BEST represents the type of testing that will occur?
A.
Bug bounty
B.
Black-box
C.
Gray-box
D.
White-box
E.
Red-leam
Bug bounty
Which of the following is the purpose of a risk register?
A.
To define the level or risk using probability and likelihood
B.
To register the risk with the required regulatory agencies
C.
To identify the risk, the risk owner, and the risk measures
D.
To formally log the type of risk mitigation strategy the organization is using
To identify the risk, the risk owner, and the risk measures
An attacker is exploiting a vulnerability that does not have a patch available. Which of the
following is the attacker exploiting?
A.
Zero-day
B.
Default permissions
C.
Weak encryption
D.
Unsecure root accounts
Zero-day
Several employees return to work the day after attending an industry trade show. That same day, the security manager notices several malware alerts coming from each of the employee’s workstations. The security manager investigates but finds no signs of an attack on the perimeter firewall or the NIDS. Which of the following is MOST likely causing the malware alerts?
A.
A worm that has propagated itself across the intranet, which was initiated by
presentation media
B.
A fileless virus that is contained on a vCard that is attempting to execute an attack
C.
A Trojan that has passed through and executed malicious code on the hosts
D.
A USB flash drive that is trying to run malicious code but is being blocked by the host firewall
A worm that has propagated itself across the intranet, which was initiated by
presentation media
| Page 19 out of 74 Pages |
| Previous |