Topic 1: Mix Questions
A company needs to deploy a new workload on AWS. The company must encrypt all data at rest and must rotate the encryption keys once each year. The workload uses an Amazon RDS for MySQL Multi-AZ database for data storage. Which configuration approach will meet these requirements?
A. Enable Transparent Data Encryption (TDE) in the MySQL configuration file. Manually rotate the key every 12 months.
B. Enable RDS encryption on the database at creation time by using the AWS managed key for Amazon RDS.
C. Create a new AWS Key Management Service (AWS KMS) customer managed key. Enable automatic key rotation. Enable RDS encryption on the database at creation time by using the KMS key.
D. Create a new AWS Key Management Service (AWS KMS) customer managed key. Enable automatic key rotation. Enable encryption on the Amazon Elastic Block Store (Amazon EBS) volumes that are attached to the RDS DB instance.
Explanation: This configuration approach will meet the requirement of encrypting all data at rest and rotating the encryption keys once each year. By creating a new AWS KMS customer managed key and enabling automatic key rotation, the encryption keys will be rotated automatically every year. By enabling RDS encryption on the database at creation time using the KMS key, all data stored in the RDS for MySQL Multi-AZ database will be encrypted at rest. This approach provide more control over key management and rotation and provide additional security benefits.
A company with multiple AWS accounts needs to obtain recommendations for AWS Lambda functions and identify optimal resource configurations for each Lambda function. How should a SysOps administrator provide these recommendations?
A. Create an AWS Serverless Application Repository and export the Lambda function recommendations.
B. Enable AWS Compute Optimizer and export the Lambda function recommendations
C. Enable all features of AWS Organization and export the recommendations from AWS CloudTrail Insights.
D. Run AWS Trusted Advisor and export the Lambda function recommendations
Explanation: AWS Compute Optimizer provides recommendations for optimizing the performance and cost of your AWS resources, including Lambda functions.
A company is using Amazon CloudFront to serve static content for its web application to its users. The CloudFront distribution uses an existing on-premises website as a custom origin. The company requires the use of TLS between CloudFront and the origin server. This configuration has worked as expected for several months. However, users are now experiencing HTTP 502 (Bad Gateway) errors when they view webpages that include content from the CloudFront distribution. What should a SysOps administrator do to resolve this problem?
A. Examine the expiration date on the certificate on the origin site. Validate that the certificate has not expired. Replace the certificate if necessary.
B. Examine the hostname on the certificate on the origin site. Validate that the hostname matches one of the hostnames on the CloudFront distribution. Replace the certificate if necessary.
C. Examine the firewall rules that are associated with the origin server. Validate that port 443 is open for inbound traffic from the internet. Create an inbound rule if necessary.
D. Examine the network ACL rules that are associated with the CloudFront distribution. Validate that port 443 is open for outbound traffic to the origin server. Create an outbound rule if necessary.
There's an SSL negotiation failure because the origin is using SSL/TLS protocols and ciphers that aren't supported by CloudFront. There's an SSL negotiation failure because the SSL certificate on the origin is expired or invalid, or because the certificate chain is invalid. There's a host header mismatch in the SSL negotiation between your CloudFront distribution and the custom origin. The custom origin isn't responding on the ports specified in the origin settings of the CloudFront distribution. The custom origin is ending the connection to CloudFront too quickly.
A database is running on an Amazon RDS Mufti-AZ DB instance. A recent security audit found the database to be out of compliance because it was not encrypted. Which approach will resolve the encryption requirement?
A. Log in to the RDS console and select the encryption box to encrypt the database
B. Create a new encrypted Amazon EBS volume and attach it to the instance
C. Encrypt the standby replica in the secondary Availability Zone and promote it to the primary instance
D. Take a snapshot of the RDS instance, copy and encrypt the snapshot and then restore to the new RDS instance
Explanation: Amazon RDS does not support enabling encryption for an existing
unencrypted DB instance directly. However, you can achieve encryption by following these
steps:
A company is using AWS Certificate Manager (ACM) to manage public SSL/TLS certificates. A SysOps administrator needs to send an email notification when a certificate has less than 14 days until expiration. Which solution will meet this requirement with the LEAST operational overhead?
A. Create an Amazon CloudWatch custom metric to monitor certificate expiration for all ACM certificates. Create an Amazon EventBridge rule that has an event source of a ws. cloud watch Configure the rule to send an event to a target Amazon Simple Notification Service (Amazon SNS) topic if the DaysToExpiry metric is less than 14. Subscribe the appropriate email addresses to the SNS topic.
B. Create an Amazon EventBridge rule that has an event source of aws.acm. Configure the rule to evaluate the DaysToExpiry melric for all ACM certificates. Configure the rule to send an event to a target Amazon Simple Notification Service (Amazon SNS) topic if DaysToExpiry is less than 14. Subscribe the appropriate email addresses to the SNS topic.
C. Create an Amazon CloudWatch dashboard that displays the DaysToExpiry metric for all ACM certificates. If DaysToExpiry is less than 14, send an email message to the appropriate email addresses. Send the email message by running a predefined CLI command to publish to an Amazon Simple Notification Service (Amazon SNS) topic.
D. Create an Amazon EventBridge rule that has an event source of aws.acm. Configure the rule to evaluate the DaysToExpiry metric for all ACM certificates. Configure a target SMS identity that uses a predefined email template. Configure the rule to send an event to the target SMS identity if DaysToExpiry is less than 14.
Explanation: To send an email notification when an ACM certificate has less than 14 days until expiration, the most operationally efficient solution is to create an Amazon EventBridge rule that directly monitors AWS ACM for certificate expiry details. EventBridge can capture aws.acm events related to certificate expiration and evaluate the DaysToExpiry metric directly. Configure the rule to send notifications to an Amazon SNS topic when DaysToExpiry is less than 14, and subscribe the necessary email addresses to this SNS topic. This approach avoids the need for custom metrics or manual monitoring, providing a streamlined and automatic notification system. Option B is the correct answer as it leverages native integration between ACM, EventBridge, and SNS for minimal operational overhead. More details on EventBridge rules can be found in AWS documentation EventBridge Rules.
A company must migrate its applications to AWS The company is using Chef recipes for configuration management The company wants to continue to use the existing Chef recipes after the applications are migrated to AWS. What is the MOST operationally efficient solution that meets these requirements?
A. Use AWS Cloud Format ion to create an Amazon EC2 instance, install a Chef server, and add Chef recipes.
B. Use AWS CloudFormation to create a stack and add layers for Chef recipes.
C. Use AWS Elastic Beanstalk with the Docker platform to upload Chef recipes.
D. Use AWS OpsWorks to create a stack and add layers with Chef recipes.
Explanation: AWS OpsWorks is a configuration management service that provides managed instances of Chef and Puppet. This service is designed to work seamlessly with Chef recipes, making it the most operationally efficient solution for continuing to use existing Chef recipes after migrating applications to AWS.
A SysOps administrator is investigating a company's web application for performance problems The application runs on Amazon EC2 instances that are in an Auto Scaling group. The application receives large traffic increases at random times throughout the day. During periods of rapid traffic increases, the Auto Scaling group is not adding capacity fast enough. As a result, users are experiencing poor performance. The company wants to minimize costs without adversely affecting the user experience when web traffic surges quickly. The company needs a solution that adds more capacity to me Auto Scaling group for larger traffic increases than for smaller traffic increases. How should the SysOps administrator configure the Auto Scaling group to meet these requirements?
A. Create a simple scaling policy with settings to make larger adjustments in capacity when the system is under heavy load
B. Create a step scaling policy with settings to make larger adjustments in capacity when the system is under heavy load.
C. Create a target tracking scaling policy with settings to make larger adjustments in capacity when the system is under heavy load
D. Use Amazon EC2 Auto Scaling lifecycle hooks Adjust the Auto Scaling group's maximum number of instances after every scaling event
An ecommerce company uses an Amazon ElastiCache for Memcached cluster for inmemory caching of popular product queries on the shopping site. When viewing recent Amazon CloudWatch metrics data for the ElastiCache cluster, the SysOps administrator notices a large number of evictions. Which of the following actions will reduce these evictions? (Choose two.)
A. Add an additional node to the ElastiCache cluster.
B. Increase the ElastiCache time to live (TTL).
C. Increase the individual node size inside the ElastiCache cluster.
D. Put an Elastic Load Balancer in front of the ElastiCache cluster.
E. Use Amazon Simple Queue Service (Amazon SQS) to decouple the ElastiCache cluster.
Explanation: https://d1.awsstatic.com/training-and-certification/docs-sysopsassociate/ AWS-Certified-SysOps-Administrator-Associate_Sample-Questions_C02.pdf Evictions in Amazon ElastiCache for Memcached occur when the cache runs out of available memory and needs to remove existing data to store new data. To reduce evictions, you can either add more nodes to the cluster or increase the size of the individual nodes.
A company has migrated its application to AWS. The company will host the application on Amazon EC2 instances of multiple instance families. During initial testing, a SysOps administrator identifies performance issues on selected EC2 instances. The company has a strict budget allocation policy, so the SysOps administrator must use the right resource types with the performance characteristics to match the workload. What should the SysOps administrator do to meet this requirement?
A. Purchase regional Reserved Instances (RIs) for immediate cost savings. Review and take action on the EC2 rightsizing recommendations in Cost Explorer. Exchange the RIs for the optimal instance family after rightsizing.
B. Purchase zonal Reserved Instances (RIs) for the existing instances. Monitor the RI utilization in the AWS Billing and Cost Management console. Make adjustments to instance sizes to optimize utilization.
C. Review and take action on AWS Compute Optimizer recommendations. Purchase Compute Savings Plans to reduce the cost that is required to run the compute resources.
D. Review resource utilization metrics in the AWS Cost and Usage Report. Rightsize the EC2 instances. Create On-Demand Capacity Reservations for the rightsized resources.
Explanation: When managing performance and cost for EC2 instances across different
families, the following steps are recommended:
A company runs an application on Amazon EC2 instances behind an Application Load Balancer. The EC2 instances are in an Auto Scaling group. The application sometimes becomes slow and unresponsive. Amazon CloudWatch metrics show that some EC2 instances are experiencing high CPU load. A SysOps administrator needs to create a CloudWatch dashboard that can automatically display CPU metrics of all the EC2 instances. The metrics must include new instances that are launched as part of the Auto Scaling group. What should the SysOps administrator do to meet these requirements in the MOST operationally efficient way?
A. Create a CloudWatch dashboard. Use activity notifications from the Auto Scaling group to invoke a custom AWS Lambda function. Use the Lambda function to update the CloudWatch dashboard to monitor the CPUUtilization metric for the new instance IDs.
B. Create a CloudWatch dashboard. Run a custom script on each EC2 instance to stream the CPU utilization to the dashboard.
C. Use CloudWatch metrics explorer to filter by the aws:autoscaling:groupName tag and to create a visualization for the CPUUtilization metric. Add the visualization to a CloudWatch dashboard.
D. Use CloudWatch metrics explorer to filter by instance state and to create a visualization for the CPUUtilization metric. Add the visualization to a CloudWatch dashboard.
Explanation:
CloudWatch Metrics Explorer is a powerful tool for creating dynamic dashboards based on
tags. This method is efficient for monitoring Auto Scaling groups:
ASysOps administrator is using 1AM credentials to try to upload a file to a customer's
Amazon S3 bucket that is named DOC-EXAMPLE-BUCKET. The SysOps administrator is
receiving an AccessDenied message.
Which combination of configuration changes will correct this problem? (Select TWO.)
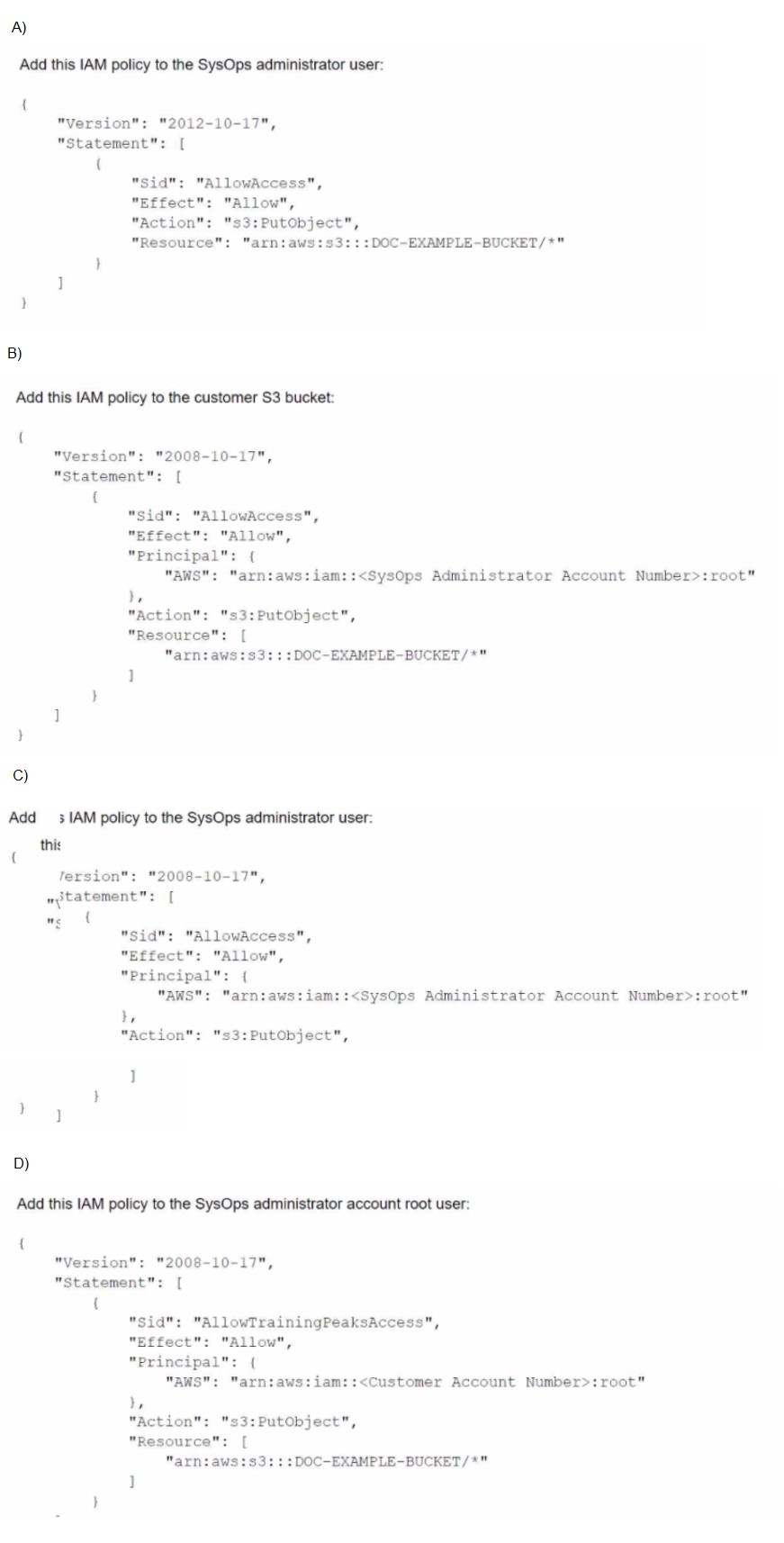
A. Option A
B. Option B
C. Option C
D. Option D
A company is planning to host its stateful web-based applications on AWS A SysOps administrator is using an Auto Scaling group of Amazon EC2 instances The web applications will run 24 hours a day 7 days a week throughout the year The company must be able to change the instance type within the same instance family later in the year based on the traffic and usage patterns Which EC2 instance purchasing option will meet these requirements MOST cost-effectively?
A. Convertible Reserved Instances
B. On-Demand instances
C. Spot instances
D. Standard Reserved instances
| Page 17 out of 41 Pages |
| Previous |