Topic 2: Mix Questions
Note: This question is part of a series of questions that present the same scenario. Each
question in the series contains a unique solution that might meet the stated goals. Some
question sets might have more than one correct solution, while others might not have a
correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result,
these questions will not appear in the review screen.
You recently discovered that the developers at your company emailed Azure Storage
Account keys in plain text to third parties.
You need to ensure that when Azure Storage Account keys are emailed, the emails are
encrypted.
Solution: You configure a mail flow rule that matches the text patterns.
Does this meet the goal?
A. Yes
B. No
Explanation:
To ensure Azure Storage Account keys are encrypted when sent via email, you need a
Data Loss Prevention (DLP) policy that detects Azure Storage Account keys using a
sensitive information type and automatically encrypts emails containing these keys.
Text patterns in mail flow rules are not as reliable as sensitive information types in DLP.
Mail flow rules lack advanced content detection and machine learning-based classification,
making them less effective than DLP.
You have a Microsoft 365 E5 subscription that contains a retention policy named RP1 as shown in the following table.
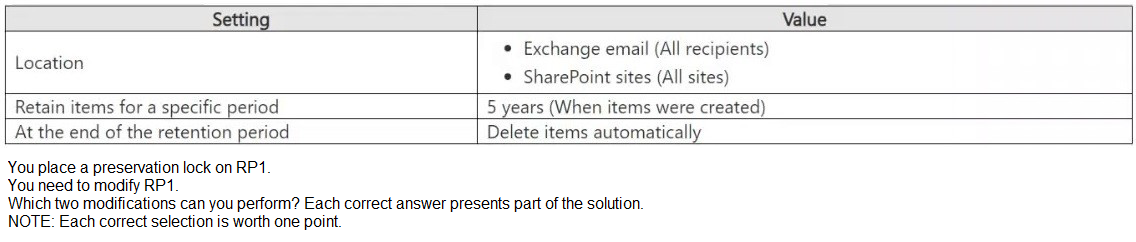
A. Add locations to the policy.
B. Delete the policy.
C. Remove locations from the policy.
D. Decrease the retention period of the policy.
E. Disable the policy.
F. Increase the retention period of the policy.
Explanation:
A Preservation Lock in Microsoft Purview Retention Policies enforces strict compliance and
prevents certain modifications to ensure data is retained according to compliance
requirements.
When a Preservation Lock is applied:
1. You cannot disable or delete the policy.
2. You cannot remove locations from the policy.
3. You cannot decrease the retention period.
4. You can add locations to the policy.
5. You can increase the retention period.
You can expand the retention policy to cover additional locations (e.g., more Exchange
mailboxes, SharePoint sites). You can extend the retention duration (e.g., increase from 5
years to 10 years) since this aligns with stricter compliance.
You have a Microsoft 565 E5 tenant that uses Microsoft Teams and contains two users named User1 and User2. You create a data Joss prevention (DIP) policy that is applied to the Teams chat and channel messages location for User1 and User? Which Teams entities will have DLP protection?
A. 1:1/n chats and general channels only
B. 1:1/n chats and private channels only
C. 1:1/n chats, general channels, and private channels
You have a Microsoft 365 E5 subscription that uses Microsoft Defender for Cloud Apps.
You plan to deploy a Defender for Cloud Apps file policy that will be triggered when the
following conditions are met:
A file is shared externally.
A file is labeled as internal only.
Which filter should you use for each condition? To answer, drag the appropriate filters to
the correct conditions. Each filter may be used once, more than once, or not at all. You
may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.

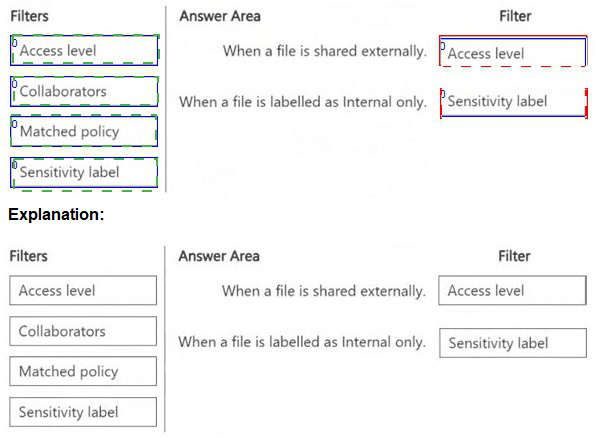
You have a Microsoft 365 IS subscription that contains the resources shown in the following table.
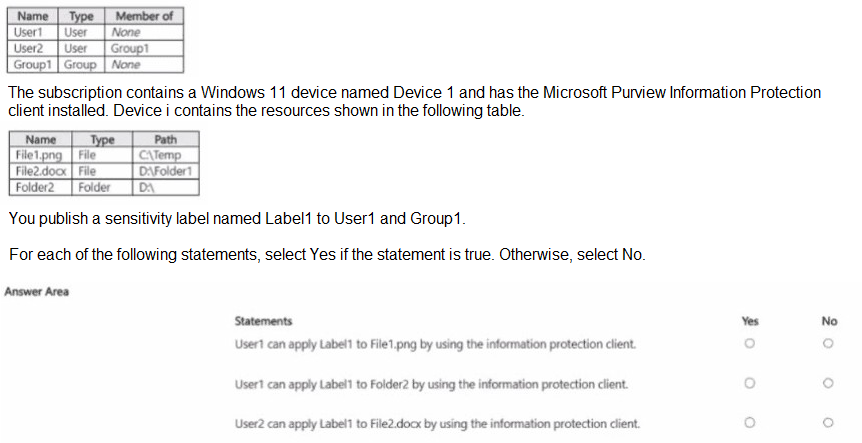
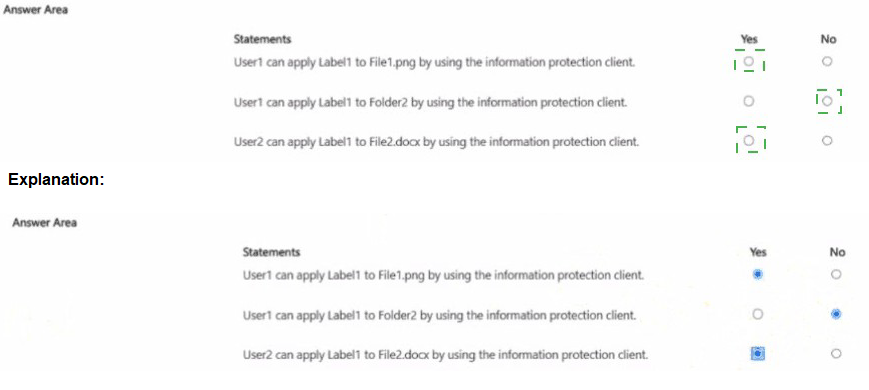
You need to provide a user with the ability to view data loss prevention (DIP) alerts in the Microsoft Purview portal. The solution must use the principle of least privilege. Which role should you assign to the user?
A. Compliance Administrator
B. Security Reader
C. Security Operator
D. Compliance Data Administrator
You have a Microsoft 365 E5 subscription.
You need to prevent users from uploading data loss prevention (DLP)-protected documents
to the following third-party websites:
web1.contoso.com
web2.contoso.com
The solution must minimize administrative effort.
To what should you set the Service domains setting for Endpoint DLP?
A. *.contoso.com
B. contoso.com
C. web1.contoso.com and web2.contoso.com
D. web*.contoso.com
Explanation:
The Service domains setting in Microsoft 365 Endpoint Data Loss Prevention (Endpoint
DLP) allows administrators to block or allow specific domains for file uploads. The goal is to
prevent users from uploading DLP-protected documents to web1.contoso.com and
web2.contoso.com.
Setting the Service domains to "web1.contoso.com and web2.contoso.com" precisely
targets the two specific third-party websites, minimizing administrative effort while ensuring
strict control.
You have a Microsoft 365 subscription.
You have a user named User1 Several users have full access to the mailbox of User1.
Some email messages sent to User 1 appeal to have been read and deleted before the
user viewed them
When you search the audit log in the Microsoft Purview portal to identify who signed in to
the mailbox of User l. the results are blank.
You need to ensure that you can view future sign-ins to the mailbox of User1.
Solution: You run the Set-AuditConfig -Workload Exchange command.
Does that meet the goal?
A. Yes
B. No
You have a Microsoft 36S ES subscription.
You plan to create an met data match (EDM) classifier named EDM1.
You need to grant permissions to hash and upload the sensitive ^formation source table for
EDMI. What should you create first?
A. a Microsoft Entra enterprise application named EDM.DataUploaders
B. a Microsoft Purview role group named EDM.DataUploaders
C. a security group named EDM.DataUploaders
D. a Microsoft Entra app registration named EDM.DataUploaders
E. a Microsoft 365 group named EDM.Datauploaders
You have a Microsoft 365 E5 subscription. The subscription contains 500 devices that are
onboarded to Microsoft Purview.
You select Activate Microsoft Purview Audit.
You need to ensure that you can track interactions between users and generative AI
websites.
What should you deploy to the devices?
A. the Microsoft Purview extension
B. the Microsoft Purview Information Protection client
C. the Microsoft Defender Browser Protection extension
D. Endpoint analytics
Explanation:
To track interactions between users and generative AI websites in Microsoft Purview Audit,
you need to deploy the Microsoft Purview browser extension to the devices. This extension
enables tracking of user activities on web-based applications, including AI-related tools like
ChatGPT, Microsoft Copilot, and other generative AI platforms.
Microsoft Purview extension provides visibility into browser-based activities, including AI
tool usage, ensuring compliance and risk management within Microsoft Purview. This
extension works with Microsoft Edge and Google Chrome to track and log user
interactions.
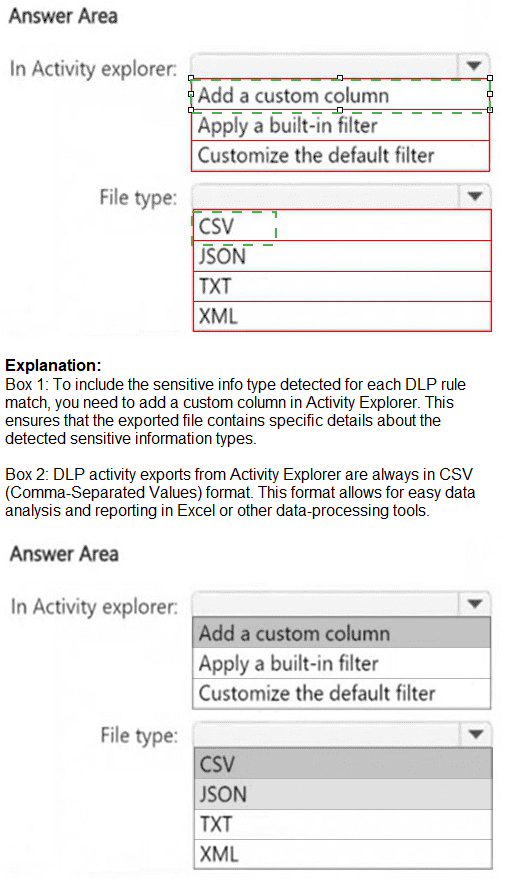
HOTSPOT
You have a Microsoft 365 E5 subscription that has data loss prevention (DLP)
implemented.
You plan to export DLP activity by using Activity explorer.
The exported file needs to display the sensitive info type detected for each DLP rule match.
What should you do in Activity explorer before exporting the data, and in which file format is
the file exported? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.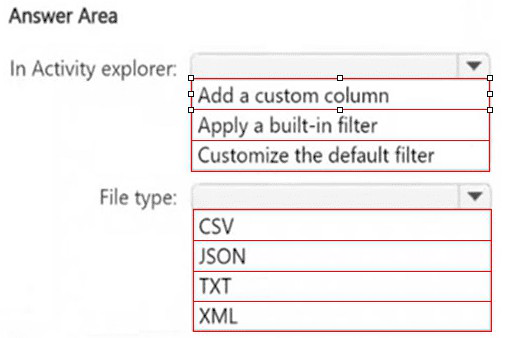
You have a Microsoft 365 subscription.
Users have devices that run Windows 11.
You plan to create a Microsoft Purview insider risk management policy that will detect when
a user performs the following actions:
Deletes files that contain a sensitive information type (SIT) from their device
Copies files that contain a SIT to a USB drive
Prints files that contain a SIT
You need to prepare the environment to support the policy.
What should you do?
A. Configure the physical badging connector.
B. Configure the HR data connector.
C. Create a Microsoft Purview communication compliance policy.
D. Onboard the devices to Microsoft Purview.
Explanation:
To ensure that Microsoft Purview Insider Risk Management can detect file deletions, USB
copies, and print actions on sensitive information, you must onboard the Windows 11
devices to Microsoft Purview.
Device onboarding enables endpoint activity monitoring, allowing Purview to track and log
user activities such as file deletions, USB transfers, and printing of sensitive files. Once
onboarded, the Insider Risk Management policy can analyze these activities and generate
risk alerts when sensitive information types (SITs) are involved.
| Page 4 out of 11 Pages |
| Previous |