Topic 2: Mix Questions
You have a Microsoft 36S subscription.
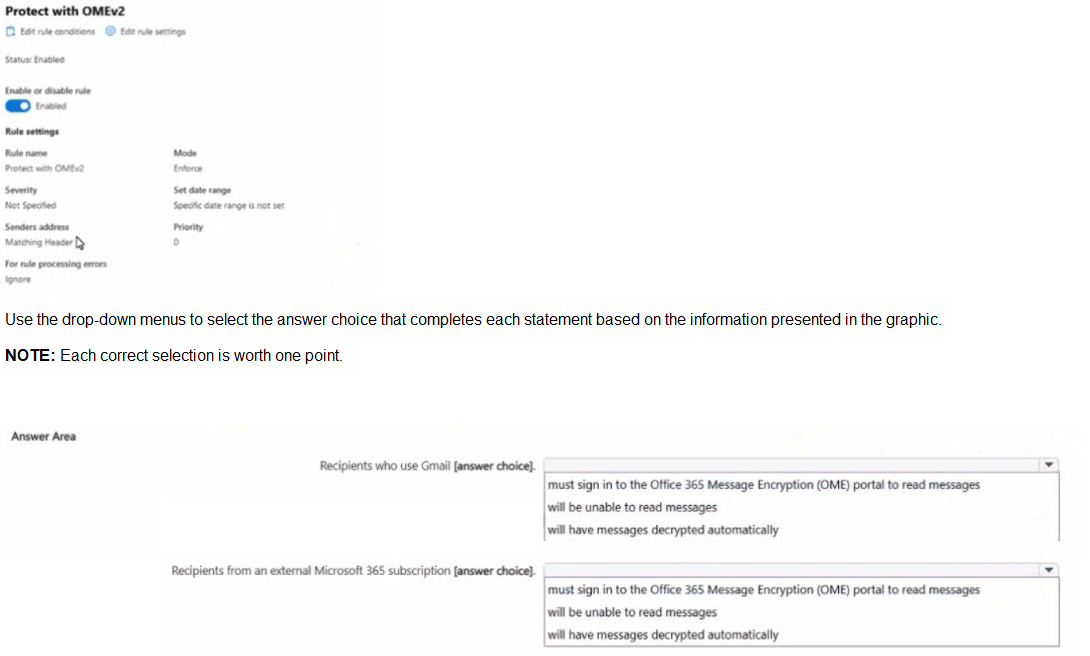
In Microsoft Exchange Online, you configure the mail flow rule shown in the following
exhibit.
Explanation:
The mail flow rule is configured to "Modify the message security... Apply Office 365 Message Encryption."
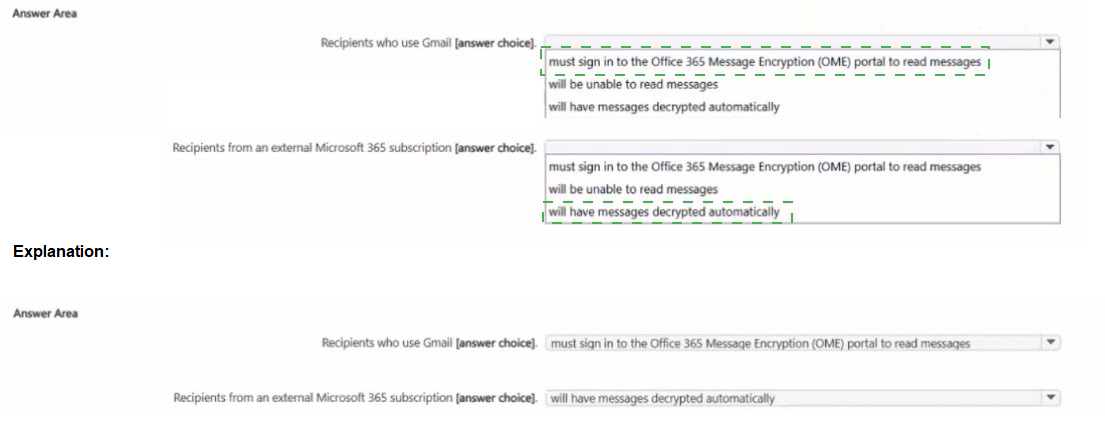
1. Recipients who use Gmail:
Gmail is a non-Microsoft email service. It has no built-in trust relationship with the Microsoft 365 encryption system.
Therefore, when a Gmail user receives an encrypted message, they cannot decrypt it directly in their inbox.
The email will contain a link or an attachment that directs them to the OME portal. They must authenticate (often with a one-time passcode sent to their email or by using a Google/Microsoft account) to read the message in a secure web browser.
Conclusion: They must sign in to the OME portal.
2. Recipients from an external Microsoft 365 subscription:
This scenario leverages a trusted service-to-service connection between two Microsoft 365 tenants.
When an encrypted email is sent from one Microsoft 365 organization to another, the encryption rights are honored seamlessly.
The recipient in the external tenant can open the encrypted message directly in their Outlook client (desktop, web, or mobile) without any additional steps. The decryption happens automatically in the background because both systems use the same underlying Microsoft Purview technology.
Conclusion: Messages are decrypted automatically.
Reference
Microsoft Learn: Office 365 Message Encryption
This documentation explains the different recipient experiences, including the seamless experience for users in other Microsoft 365 organizations and the portal experience for non-Microsoft users.
You have a Microsoft 365 E5 tenant.
You need to add a new keyword dictionary.
What should you create?
A. a trainable classifier
B. a retention policy
C. a sensitivity label
D. a sensitive info type
Explanation:
To add a new keyword dictionary in Microsoft Purview, you must create a custom sensitive information type. Keyword dictionaries are specifically designed as components within sensitive information types, allowing you to define custom lists of terms (such as project names, internal codes, or specialized terminology) that Microsoft's built-in classifiers don't cover. The sensitive information type framework provides the structure to incorporate keyword dictionaries along with configurable elements like character proximity, confidence levels, and supporting patterns to create precise detection rules.
The process involves accessing the Microsoft Purview compliance portal, navigating to the sensitive information types section, and creating a new custom classifier where you can import or define your keyword list. This dictionary then becomes available for use across various Purview capabilities including Data Loss Prevention (DLP) policies, communication compliance, and information protection labeling rules.
Why Other Options Are Incorrect:
A. a trainable classifier:
While trainable classifiers also identify content, they use machine learning based on submitted sample documents rather than predefined keyword lists. They're designed for pattern recognition in complex content types that are difficult to define with explicit keywords, making them unsuitable for creating structured keyword dictionaries.
B. a retention policy:
Retention policies manage content lifecycle through retention and deletion schedules across Microsoft 365 workloads. They operate at the container or location level and lack any capability for keyword detection or dictionary management, focusing entirely on time-based data governance rather than content inspection.
C. a sensitivity label:
Sensitivity labels provide classification, protection controls (encryption, watermarks), and access governance for documents and emails. While they can be automatically applied using sensitive information types that reference keyword dictionaries, the labels themselves cannot contain or create keyword dictionaries—they consume the output of detection mechanisms rather than defining them.
Reference
Microsoft Learn: Create a keyword dictionary
This documentation explicitly states:
"You can create a keyword dictionary for use as a sensitive information type in the Microsoft Purview compliance portal." It provides the procedural guidance for creating keyword dictionaries specifically within the sensitive information types framework.
Microsoft Learn:
Learn about sensitive information types
This reference explains the architecture of sensitive information types and how keyword dictionaries integrate as detectable patterns within this classification system.
You have a Microsoft 365 E5 subscription.
You plan to implement Microsoft Purview insider risk management.
You implement the HR data connector.
You need to prepare the data that will be imported by the data connector.
In which format should you prepare the data?
A. JSON
B. CSV
C. TSV
D. XML
E. PRN
Explanation:
The Microsoft Purview HR connector for insider risk management requires data to be prepared in CSV (Comma-Separated Values) format. This requirement is explicitly specified in Microsoft's documentation and is integral to the connector's design for importing human resources data such as employee termination dates, resignation dates, and employment status changes. The CSV format provides a standardized, structured approach that ensures reliable parsing and processing of HR data by the Purview compliance platform.
The implementation process involves exporting HR data from source systems (like Workday or SAP SuccessFactors) into a CSV file containing specific mandatory columns including DateOfTermination, LastWorkingDate, ResignationDate, and ManagerEmail. This file must then be uploaded to an Azure Storage container, from which the HR connector automatically imports the data to trigger and support insider risk management policies based on user employment status changes.
Why Other Options Are Incorrect:
A. JSON & D. XML:
These structured data formats are primarily used for API integrations and web services communication. While they excel in programmatic data exchange, the HR connector is specifically engineered to process flat file exports from HR systems through scheduled batch processes rather than real-time API consumption.
C. TSV (Tab-Separated Values):
Although functionally similar to CSV as a delimited text format, TSV uses tabs as delimiters rather than commas. The HR connector's parsing engine is specifically calibrated for comma-separated values, and using TSV format would likely result in import failures or data misinterpretation due to the different delimiter specification.
E. PRN (Printer File):
This is a legacy fixed-width format designed for printer output that lacks the structured delimiter approach required by modern data connectors. PRN files do not provide the consistent column separation necessary for reliable automated processing by the HR connector's import mechanism.
Reference:
Microsoft Learn: Import data with the HR connector
This documentation explicitly states: "You'll need to create a CSV file with the following columns..." and provides the complete schema specification, file preparation requirements, and implementation steps for the HR connector, confirming CSV as the mandatory format.
You have a Microsoft 365 subscription.
You need to customize encrypted email for the subscription. The solution must meet the
following requirements.
Ensure that when an encrypted email is sent, the email includes the company logo.
Minimize administrative effort.
Which PowerShell cmdlet should you run?
A. Set-IRMConfiguration
B. Set-OMEConfiguration
C. Set-RMSTemplate
D. New-OMEConfiguration
Explanation:
The Set-OMEConfiguration PowerShell cmdlet is specifically designed to customize the branding and appearance of encrypted emails sent via Microsoft Purview Message Encryption (formerly known as Office 365 Message Encryption). This cmdlet allows you to modify the default encryption portal experience to include your company's branding elements.
Key Reasons:
The primary requirement is to add a company logo to encrypted emails. The Set-OMEConfiguration cmdlet includes parameters such as -LogoURL that allow you to specify the web-accessible location of your company logo image file.
The requirement to minimize administrative effort is met because this cmdlet provides a centralized way to configure branding that automatically applies to all future encrypted emails sent from your organization, eliminating the need for per-user or per-message configuration.
This cmdlet also supports other branding customizations like custom introductory text, disclaimer text, and color schemes, providing a comprehensive solution for email encryption branding.
Why Other Options Are Incorrect:
A. Set-IRMConfiguration:
This cmdlet manages Azure Rights Management (now part of Microsoft Purview Information Protection) settings at the organizational level, such as enabling/disabling the service or journal report decryption. It does not handle the visual branding customization of encrypted email messages.
C. Set-RMSTemplate:
This cmdlet is used to modify Rights Management Service (RMS) templates that control permissions and encryption settings for documents. While related to information protection, it does not control the visual branding elements (like logos) displayed in encrypted emails.
D. New-OMEConfiguration:
This cmdlet does not exist in Exchange Online PowerShell. The correct cmdlets for OME configuration management are Get-OMEConfiguration, Set-OMEConfiguration, and Remove-OMEConfiguration.
Reference:
Microsoft Learn: Set-OMEConfiguration
This documentation specifically describes how to use the Set-OMEConfiguration cmdlet to customize the appearance of encrypted messages, including the -LogoURL parameter for adding company branding.
You have a Microsoft 365 E5 subscription that contains a trainable classifier named Trainable1. You plan to create the items shown in the following table.
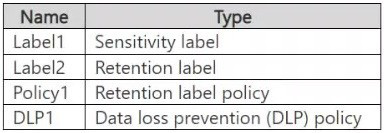
A. Label2 only
B. Label1 and Label2 only
C. Label1 and Policy1 only
D. Label2, Policy1, and DLP1 only
E. Label1, Label2, Policy1, and DLP1
Explanation:
A trainable classifier in Microsoft Purview (formerly Microsoft 365 Compliance Center) is a machine learning–based classification method that helps automatically identify and categorize content according to its meaning rather than fixed patterns or keywords. Unlike sensitive information types, which depend on patterns (like credit card or ID numbers), trainable classifiers analyze text context and behavior to detect items such as “contracts,” “invoices,” or “resumes.” They are primarily used to auto-apply retention labels, configure data loss prevention (DLP) policies, or drive compliance actions based on the content type.
Trainable classifiers are created and trained within Microsoft Purview using sample content. Once trained, they can be published and used in certain types of policies or labels that support automatic classification.
Why Option D Is Correct
Label2 (Retention Label):
A retention label is used to manage the lifecycle of data by defining how long items should be retained and what happens when the retention period expires. Microsoft Purview allows you to use a trainable classifier to automatically apply a retention label when content matches the classifier’s pattern. For example, if you have a classifier named “Contracts,” it can automatically apply a retention label to any document in SharePoint or OneDrive that Purview identifies as a contract. This helps organizations enforce retention and deletion policies automatically, ensuring compliance with data governance regulations.
Policy1 (Retention Label Policy):
A retention label policy is a publishing mechanism that distributes retention labels (including those using trainable classifiers) across Microsoft 365 locations such as SharePoint, OneDrive, Exchange, and Teams. When an admin configures an auto-labeling policy, they can choose a trainable classifier as the condition to determine where the label should be applied. For instance, you can create a policy that automatically applies a label to all files identified as “Confidential Financial Data” using the classifier. Thus, Policy1 can utilize Trainable1 indirectly by including the classifier-based retention label.
DLP1 (Data Loss Prevention Policy):
A data loss prevention (DLP) policy helps detect and prevent the accidental sharing of sensitive or confidential information. DLP policies support trainable classifiers as a condition within their rules. This allows the DLP engine to detect files or messages containing content that matches a classifier’s definition — for example, any document classified as “Legal Contract” or “Financial Statement.” When matched, DLP actions such as blocking sharing, applying encryption, or sending alerts can be triggered. Therefore, Trainable1 can be used within DLP1 to protect classified content.
Why the Other Options Are Incorrect
A. Label2 only:
This option is partially correct but incomplete. While a retention label (Label2) can indeed use a trainable classifier to automatically classify and label content, trainable classifiers can also be used in retention label policies and DLP policies. Therefore, limiting it only to Label2 ignores other valid uses.
B. Label1 and Label2 only:
A sensitivity label (Label1) cannot use trainable classifiers. Sensitivity labels are used to protect data (through encryption, content marking, and access restrictions), not to classify it based on machine learning models. They depend on sensitive information types or manual user application, not classifiers. While Label2 can use classifiers, Label1 cannot. Hence, this option is incorrect.
C. Label1 and Policy1 only:
As explained above, Label1 cannot use classifiers. While Policy1 can use classifiers via auto-labeling, combining it with Label1 makes this option incorrect.
E. Label1, Label2, Policy1, and DLP1:
Although Label2, Policy1, and DLP1 can use classifiers, Label1 cannot. Sensitivity labels operate under Microsoft Purview Information Protection, not Data Lifecycle Management, and do not support trainable classifiers. Thus, including Label1 makes this option invalid.
References:
Microsoft Learn – Trainable classifiers in Microsoft Purview:
Microsoft Learn – Automatically apply a retention label:
Microsoft Learn – Create and use custom trainable classifiers:
You implement Microsoft 36S Endpoint data loss pi event ion (Endpoint DIP).
You have computer that run Windows 11 and have Microsoft 365 Apps instated The
computers are joined to a Microsoft Entra
tenant.
You need to ensure that endpoint DIP policies can protect content on the computers.
Solution: You deploy the Microsoft Purview Information Protection client to the computers.
Does this meet the goal?
A. Yes
B. No
Explanation:
This solution does not meet the goal. The Microsoft Purview Information Protection (MPIP) client is not required for Endpoint Data Loss Prevention (Endpoint DLP) to function on Windows 11 devices.
Here's the correct understanding:
Endpoint DLP Architecture: Endpoint DLP uses a built-in component integrated directly into the Windows 11/10 operating system (specifically, part of the Microsoft Defender stack). This integration is what allows it to monitor and control file activities (copy, paste, print, share) and application access at the operating system level.
Correct Prerequisites: To enable Endpoint DLP protection on Windows devices, you must:
Onboard the devices to Microsoft Purview via the Device Onboarding configuration package.
Ensure the devices are running a supported Windows 10/11 edition (like Enterprise or Pro) with the necessary components enabled.
The Microsoft 365 Apps requirement in the question is correct, as Endpoint DLP policies often interact with Office applications to enforce rules.
Role of the MPIP Client: The Microsoft Purview Information Protection client (also known as the Azure Information Protection Unified Labeling Client - AIP UL Client) is a legacy, standalone client used primarily for:
Applying sensitivity labels in classic File Explorer (right-click labeling).
Providing additional features for existing AIP deployments.
It is not the core engine that powers Endpoint DLP monitoring and enforcement. In fact, Microsoft recommends moving to the built-in labeling that is integrated into Windows and Office 365 Apps, which works seamlessly with Endpoint DLP without requiring the separate MPIP client.
Conclusion: Deploying the MPIP client is an incorrect and unnecessary step for enabling Endpoint DLP. The required action is to onboard the devices to Microsoft Purview, which activates the built-in Endpoint DLP capabilities already present in Windows 11.
Reference
Microsoft Learn: Get started with Endpoint data loss prevention
This documentation details the prerequisites, which focus on device onboarding and supported Windows versions, with no mention of requiring the MPIP client for Endpoint DLP functionality.
You have a Microsoft 365 E5 tenant that has devices onboarded to Microsoft Defender for Endpoint as shown in the following table.
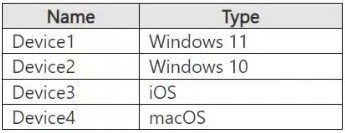
A. Device1 only
B. Device1 and Device2 only
C. Device1 and Device4 only
D. Device1, Device2, and Device4 only
E. Device1, Device2, Device3, and Device4
Explanation:
Microsoft 365 Endpoint Data Loss Prevention (DLP) operates through deep integration with device operating systems to monitor file activities, control data transfers, and enforce protection policies. The solution's availability is strictly limited to platforms where Microsoft can deploy specialized agents that interface with core system components for comprehensive monitoring and enforcement capabilities.
Supported Platforms:
Windows 11 (Device1) and Windows 10 (Device2) receive full support through native integration within the Microsoft Defender for Endpoint platform. This integration enables real-time monitoring of file operations, application usage, network transfers, and clipboard activities while providing granular control over data movement through both user interface and background processes.
macOS (Device4) versions 12 (Monterey) and later are supported through a dedicated DLP agent that monitors file system activities, tracks sensitive data access, and enforces organizational DLP policies on Apple's desktop environment, though with some functional limitations compared to the Windows implementation.
Unsupported Platform:
iOS (Device3) is explicitly excluded from Endpoint DLP support due to fundamental architectural constraints in Apple's mobile operating system. iOS employs stringent application sandboxing that prevents the system-level monitoring required for comprehensive endpoint DLP functionality. Data protection for iOS devices is instead managed through alternative Microsoft technologies including Microsoft Defender Application Guard, App Protection Policies (MAM), and conditional access controls that operate within Apple's application framework limitations.
Reference:
Microsoft Learn: Get started with Endpoint data loss prevention - Supported operating systems
This official documentation explicitly confirms platform support: "Endpoint DLP supports Windows 10, Windows 11, and macOS (Monterey 12, Ventura 13, and Sonoma 14) devices," while notably excluding iOS and other mobile operating systems from the supported platform list.
HOTSPOT
You have a Microsoft 365 E5 subscription that contains two users named User1 and User2.
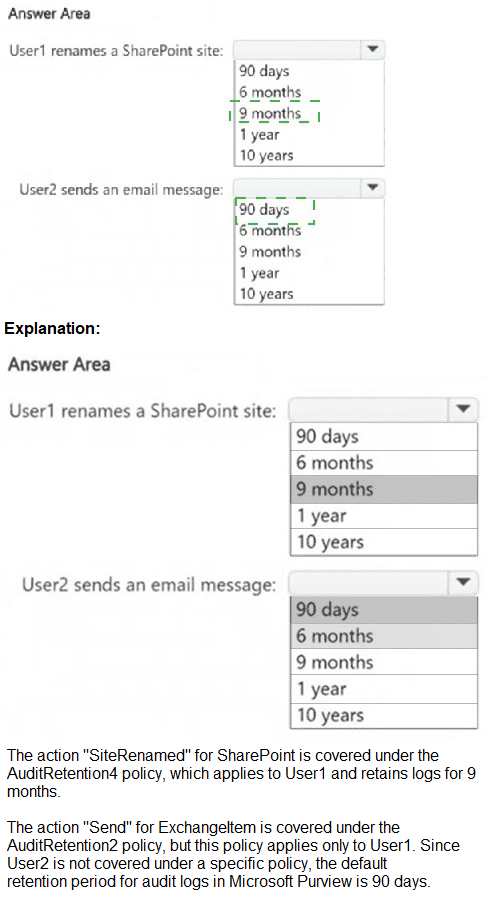
You create the audit retention policies shown in the following table.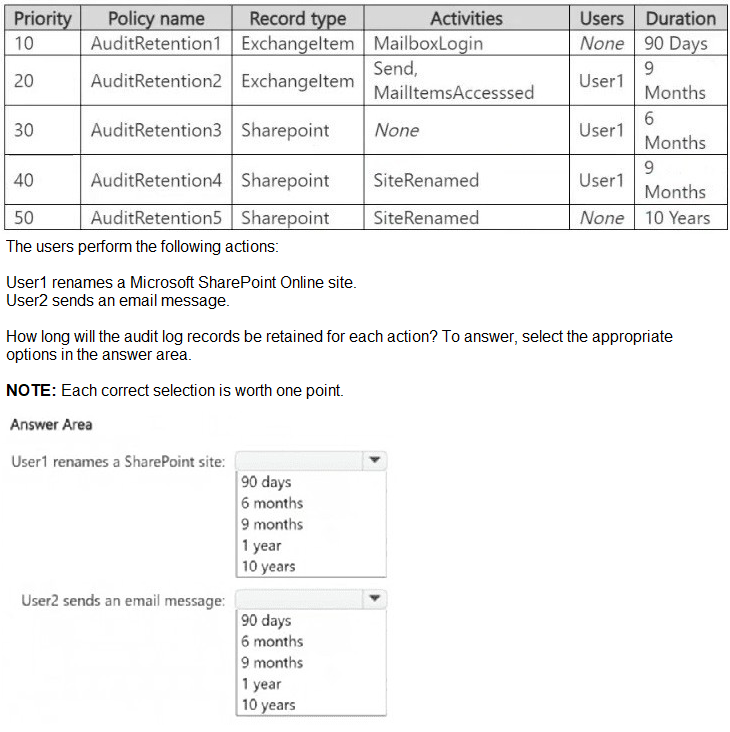
You have a Microsoft 36S subscription that contains the users shown in the following table.
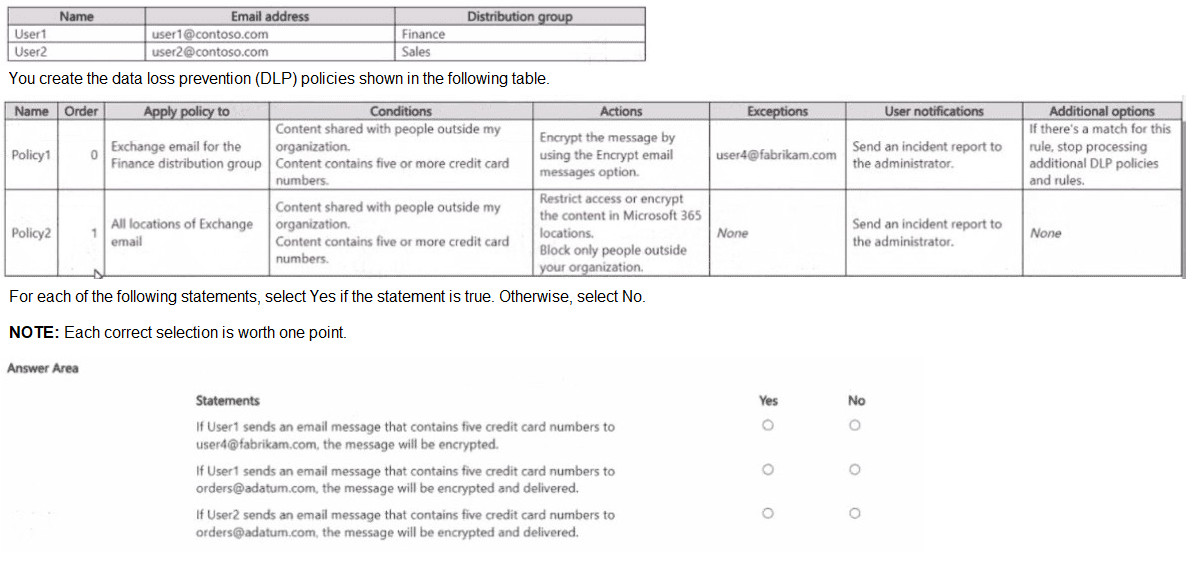
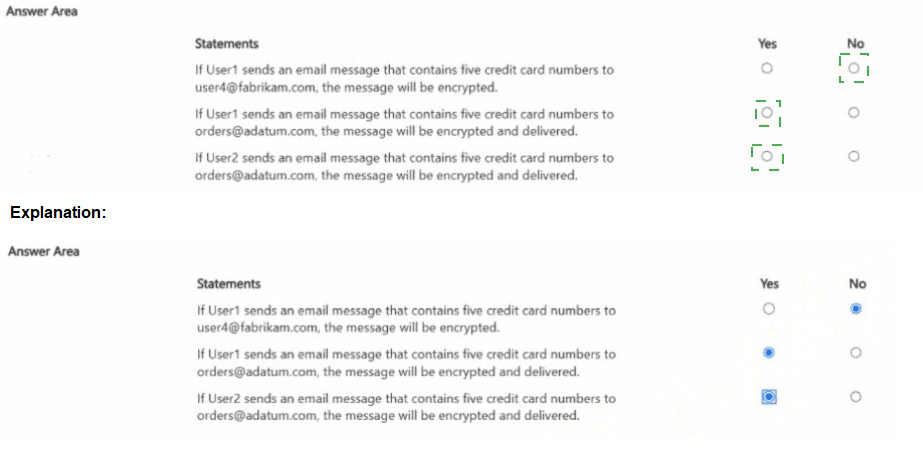
Statement 1: If User1 sends an email message that contains five credit card numbers to user4@fabrikam.com, the message will be encrypted.
Explanation:
This tests policy processing order and exception handling. Policy1 (order 0) applies to User1 (in Finance) sharing content externally. The condition is met (external email with sensitive data), but the recipient user4@fabrikam.com is listed as an exception in Policy1. Exceptions prevent the rule's actions from being applied.
Correct Option:
No. The message will not be encrypted. While the email from User1 to an external address triggers Policy1's condition, the specific recipient user4@fabrikam.com is explicitly configured as an exception to the rule. Therefore, the encrypt action is bypassed for this recipient.
Incorrect Option:
Yes is incorrect because exceptions take precedence. An exception in a DLP rule means that if the message matches the exception criteria, the rule's protective actions (like encryption) are not applied, even if all other conditions are satisfied.
Statement 2: If User1 sends an email message that contains five credit card numbers to orders@adatum.com, the message will be encrypted and delivered.
Explanation:
This tests policy priority and the "stop processing" action. User1 (Finance) sends an external email (orders@adatum.com) with sensitive data. This matches Policy1's conditions, and the recipient is not an exception. Policy1's action is to encrypt, and its "Additional option" is to stop processing additional DLP policies and rules.
Correct Option:
Yes. The message will be encrypted and delivered. Policy1 (order 0) is triggered, encrypts the message, and then stops all further DLP policy processing. Policy2 is never evaluated for this message, ensuring the encrypted message is delivered.
Incorrect Option:
No is incorrect because Policy1 is designed to handle this exact scenario. The "stop processing" clause prevents any subsequent policy (like Policy2, which might have different actions like block) from interfering, ensuring the encrypted message is delivered.
Statement 3: If User2 sends an email message that contains five credit card numbers to orders@adatum.com, the message will be encrypted and delivered.
Explanation:
This tests policy scoping. Policy1 applies only to the Finance distribution group. User2 is in the Sales group, so Policy1 does not apply to them. Therefore, the email is evaluated only by Policy2, which applies to all Exchange email locations.
Correct Option:
No. The message will likely be blocked, not encrypted and delivered. Policy2's action is "Restrict access or encrypt," but for Exchange email, a typical configuration for this action when sharing sensitive data externally is to block the message. Without an explicit "stop processing" clause, the policy would apply its restrictive action, preventing delivery.
Incorrect Option:
Yes is incorrect because it assumes User2's message is encrypted by Policy1 or Policy2. Policy1 doesn't scope to User2. Policy2, which does apply, is configured with a more restrictive default action for external sharing of sensitive content, which typically blocks delivery rather than just encrypting.
Reference:
Microsoft Learn: "Define the priority of DLP policies" and "Configure DLP policy tips and email notifications." The key concepts tested are policy order, exceptions, the Stop processing more rules option, and policy scoping (Apply to).
HOTSPOT
You have a Microsoft 365 subscription.
You plan to deploy an audit log retention policy.
You need to perform a search to validate whether the policy will be applied to the intended
entries.
Which two fields should you configure for the search? To answer, select the appropriate
fields in the answer area.
NOTE: Each correct selection is worth one point.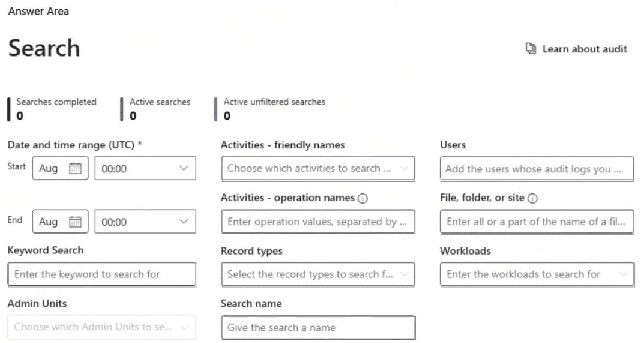
Explanation:
To validate if an audit retention policy will apply correctly, you must search for specific audit log entries that match the policy's criteria. Retention policies are scoped based on users (or groups) and record types (specific audit log activities, like ExchangeItem or SharePointFileOperation). Searching by these two fields allows you to preview the exact set of audit entries the policy will target and retain.
Why these are the correct fields:
Record types:
Audit retention policies are configured to retain specific types of audit records (e.g., AzureActiveDirectory, ExchangeItem, SharePoint). By selecting the relevant record types in the search, you filter the audit log to show only the entries that correspond to the activities your policy is designed to cover.
Users:
Policies are often scoped to specific users, groups, or the entire organization. Adding the intended users to the search validates that the audit entries generated by those individuals are present and will be captured by the policy's scope.
Why other key fields are not the primary selections:
Activities / Operation Names:
While related, "Record types" is the broader, policy-relevant category. Activities are subtypes within a record type.
Date and Time Range:
This is for filtering the search window, not for defining the policy's target criteria. The policy itself applies to events based on when they occurred, not based on a search date.
Workloads:
This is a high-level filter (like "Exchange" or "SharePoint"), but "Record types" provides the more granular, direct mapping to policy configuration.
Reference:
Microsoft Learn, "Manage audit log retention policies." The documentation specifies that policies are defined based on record types (like ExchangeItem) and scoped to users or groups. The audit log search interface is the tool used to verify the scope of these policies.
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some
question sets might have more than one correct solution, while others might not have a
correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result,
these questions will not appear in the review screen.
You have a Microsoft 365 tenant and 500 computers that run Windows 11. The computers
are onboarded to Microsoft Purview.
You discover that a third-party application named Tailspin_scanner.exe accessed protected
sensitive information on multiple computers. Tailspin_scanner.exe is installed locally on the
computers.
You need to block Tailspin_scanner.exe from accessing sensitive documents without
preventing the application from accessing other documents.
Solution: From the Microsoft Defender for Cloud Apps, you mark the application as
Unsanctioned.
Does this meet the goal?
A. Yes
B. No
Explanation:
The goal is to block a specific locally installed executable from accessing sensitive documents on endpoint devices. Microsoft Defender for Cloud Apps (now part of Microsoft Defender XDR) is a cloud access security broker (CASB). Its application sanctioning controls are designed to monitor and govern access to cloud applications and services (like SaaS apps), not to control file access permissions for locally installed executables on Windows endpoints.
Why the solution does NOT meet the goal:
Scope Mismatch:
Marking an application as "Unsanctioned" in Defender for Cloud Apps primarily affects user connections to cloud services from that app. It can trigger alerts or block sessions to cloud apps, but it does not install an endpoint-level block to prevent the local .exe from opening specific files on the local machine or network shares.
Correct Tool:
The required action needs a device-centric solution. The appropriate tool within Microsoft Purview for this scenario is Endpoint data loss prevention (Endpoint DLP), where you can create a policy that uses file path or service definitions to block specific applications from accessing files labeled as sensitive.
Reference:
Microsoft Learn, "Get started with Endpoint data loss prevention." Endpoint DLP allows you to define restrictions that "Block" activities like Copy to clipboard or Copy to a network share by untrusted apps, which is the correct method for controlling local application behavior based on file sensitivity.
Note: This question is part of a series of questions that present the same scenario. Each
question in the series contains a unique solution that might meet the stated goals. Some
question sets might have more than one correct solution, while others might not have a
correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result,
these questions will not appear in the review screen.
You have a Microsoft 365 subscription.
You have a user named User1. Several users have full access to the mailbox of User1.
Some email messages sent to User1 appear to have been read and deleted before the
user viewed them.
When you search the audit log in the Microsoft Purview portal to identify who signed in to
the mailbox of User1, the results are blank.
You need to ensure that you can view future sign-ins to the mailbox of User1.
Solution: You run the Set-MailboxFolderPermission -Identity "User1" -User
User1@contoso.com -AccessRights Owner command.
Does that meet the goal?
A. Yes
B. No
Explanation:
The goal is to audit and view future sign-ins to a shared mailbox. The issue is that mailbox audit logging for non-owner actions (like those by users with Full Access permissions) is not enabled by default, which is why the audit log search returned blank results. The solution modifies folder permissions but does not address the core requirement of enabling audit logging for the mailbox.
Why the solution does NOT meet the goal:
Action Mismatch:
The Set-MailboxFolderPermission command grants folder-level access rights (in this case, making User1 the owner of their own mailbox folders, which they likely already are). It does not enable or configure mailbox audit logging.
Correct Action:
To log sign-ins and actions by delegates, you must enable mailbox auditing specifically. The correct command would be Set-Mailbox User1 -AuditEnabled $true -AuditDelegate Admin,Update. This enables the generation of the audit records that the Purview portal searches.
Reference:
Microsoft Learn, "Enable mailbox auditing in Microsoft Purview." The documentation states that to audit delegate actions, you must run the Set-Mailbox -AuditEnabled $true cmdlet. Changing permissions does not activate the logging mechanism.
| Page 2 out of 11 Pages |
| Previous |