Topic 4: Misc. Questions
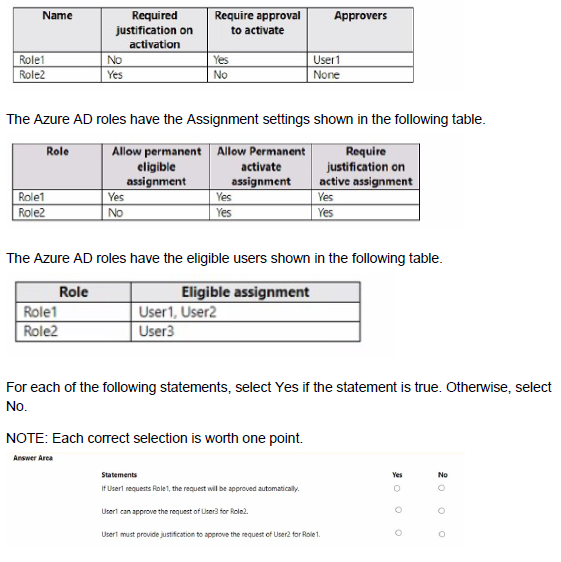
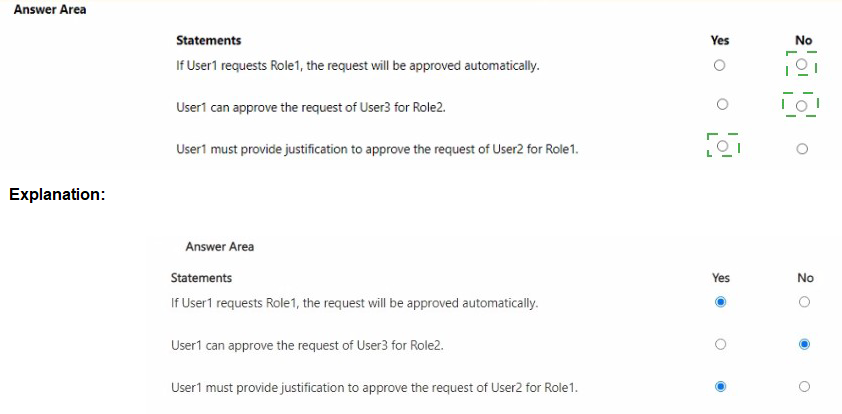
You have a Microsoft 365 E5 subscription that contains three users named User1, User2, and User3. You have two Azure AD roles that have the Activation settings shown in the following table.
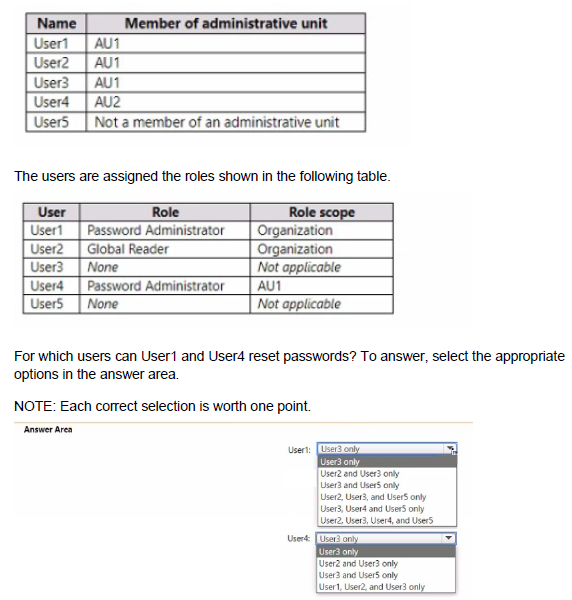
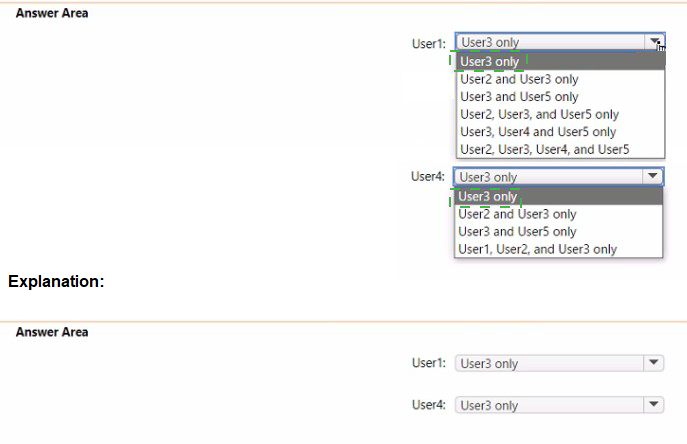
You have a Microsoft 365 E5 subscription that contains the users shown in the following table.
Note: This question is part of a series of questions that present the same scenario. Each
question in the series contains a unique solution that might meet the stated goals. Some
question sets might have more than one correct solution, while others might not have a
correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result,
these questions will not appear in the review screen.
You have a Microsoft 365 tenant.
You have 100 IT administrators who are organized into 10 departments.
You create the access review shown in the exhibit. (Click the Exhibit tab.)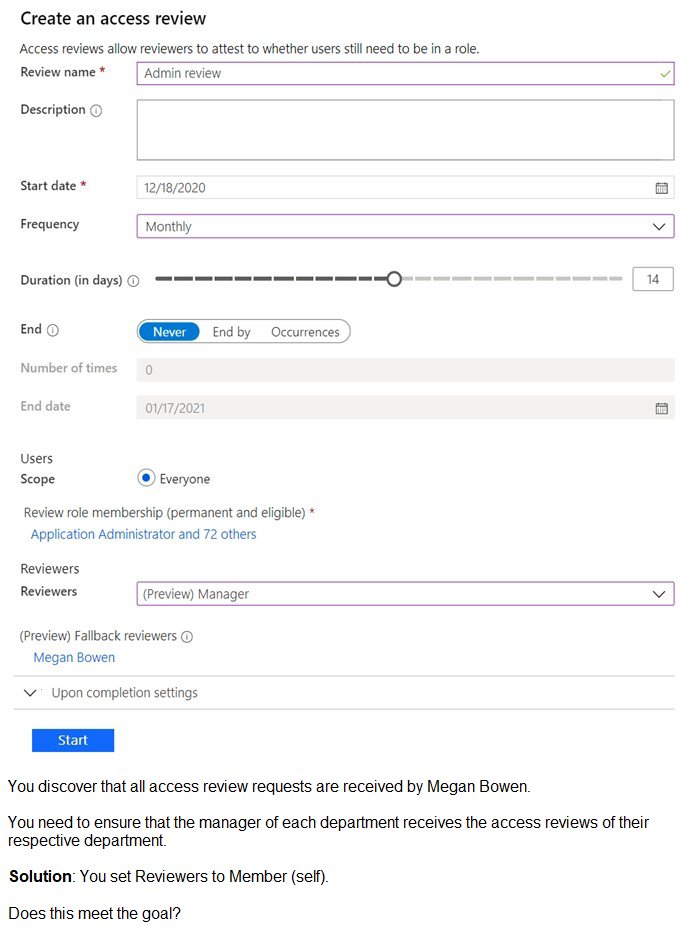
A. Yes
B. No
You have an Azure Active Directory (Azure AD) tenant named conto.so.com that has Azure AD Identity Protection enabled. You need to Implement a sign-in risk remediation policy without blocking access. What should you do first?
A. Configure access reviews in Azure AD.
B. Enforce Azure AD Password Protection
C. implement multi-factor authentication (MFA) for all users
D. Configure self-service password reset (SSPR) for all users.
Explanation: MFA and SSPR are both required. However, MFA is required first.
You have a Microsoft 365 E5 subscription. The subscription contains 500 devices that run
Windows.
You deploy the Global Secure Access client to the devices.
You need to prevent users from accessing httpsy/contoso.com from the devices.
Which three actions should you perform in sequence? To answer move the appropriate
actions from the list of actions to the answer area and arrange them in the correct order.

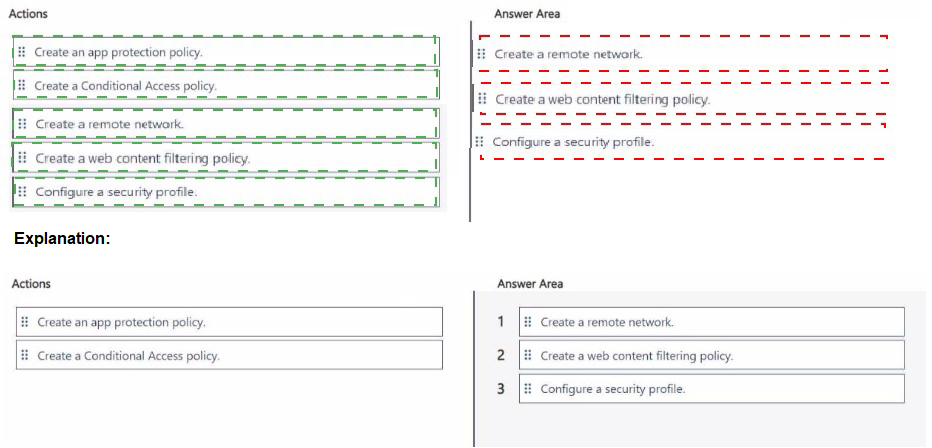
You have an Azure Active Directory (Azure AD) tenant.
You create an enterprise application collection named HR Apps that has the following settings:
A. From Users and groups, add HRUsers.
B. Prom Properties, change User assignment required to No
C. From Permissions, review the User consent permissions
D. From Single sign on, configure a sign-on method
You have an Azure Active Directory (Azure AD) tenant. You need to review the Azure AD sign-in logs to investigate sign-ins that occurred in the past. For how long does Azure AD store events in the sign-in logs?
A. 14 days
B. 30 days
C. 90 days
D. 365 days
Note: This question is part of a series of questions that present the same scenario. Each
question in the series contains a unique solution that might meet the stated goals. Some
question sets might have more than one correct solution, while others might not have a
correct solution.
After you answer a question in this section, you will NOT be able to return to it as a result
these questions will not appear in the review screen.
You have a Microsoft 365 ES subscription.
You create a user named User1.
You need to ensure that User1 can update the status of identity Secure Score improvement
actions.
Solution: You assign the Exchange Administrator role to User1.
A. Yes
B. No
Your company has an Azure AD tenant that contains the users shown in the following table.
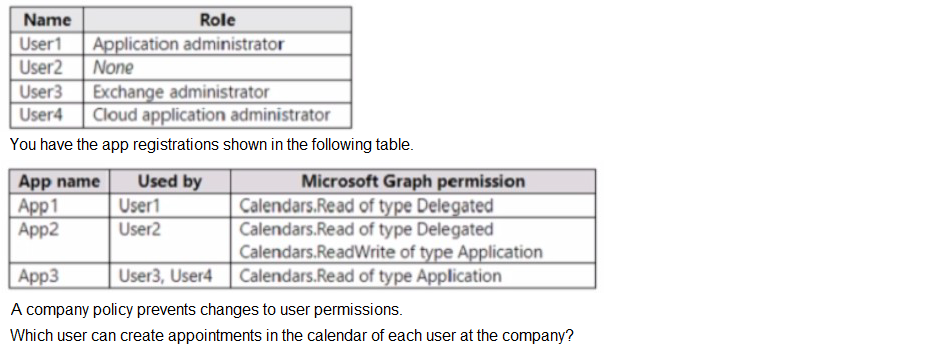
A. User1
B. User2
C. User3
D. User4
You have an Azure subscription named Sub1.
You purchase a Microsoft Entra Permissions Management license.
You need to onboard Permissions Management.
Which two actions should you perform? Each correct answer presents part of the solution.
NOTE; Each correct selection is worth one point.
A. Implement a Microsoft Entra application proxy.
B. From Microsoft Entra Permissions Management, configure data collection
C. Create a role assignment for Sub1.
D. From the Microsoft Entra admin center, configure the Diagnostic settings
E. From the Microsoft Entra admin center, create an app registration.
F. From the Azure portal, create a data collection rule (DCR).
You have an Azure AD tenant that contains a user named User1 and the conditional access policies shown in the following table.
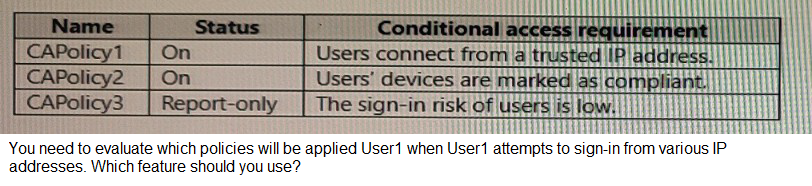
A. Access reviews
B. Identity Secure Score
C. The What If tool
D. the Microsoft 365 network connectivity test tool
You have a Microsoft 365 tenant.
The Azure Active Directory (Azure AD) tenant syncs to an on-premises Active Directory
domain.
Users connect to the internet by using a hardware firewall at your company. The users
authenticate to the
firewall by using their Active Directory credentials.
You plan to manage access to external applications by using Azure AD.
You need to use the firewall logs to create a list of unmanaged external applications and
the users who access
them.
What should you use to gather the information?
A. Application Insights in Azure Monitor
B. Access reviews in Azure AD
C. Cloud App Discovery in Microsoft Cloud App Security
D. Enterprise applications in Azure AD
| Page 11 out of 30 Pages |
| Previous |