Topic 3: Mix Questions
Your network contains an on-premises Active Directory Domain Services (AO DS) domain.
The domain contains a server that runs Windows Server and hosts shared folders The
domain syncs with Azure AD by using Azure AD Connect Azure AD Connect has group
writeback enabled.
You have a Microsoft 365 subscription that uses Microsoft SharePoint Online.
You have multiple project teams. Each team has an AD DS group that syncs with Azure AD
Each group has permissions to a unique SharePoint Online site and a Windows Server
shared folder for its project. Users routinely move between project teams.
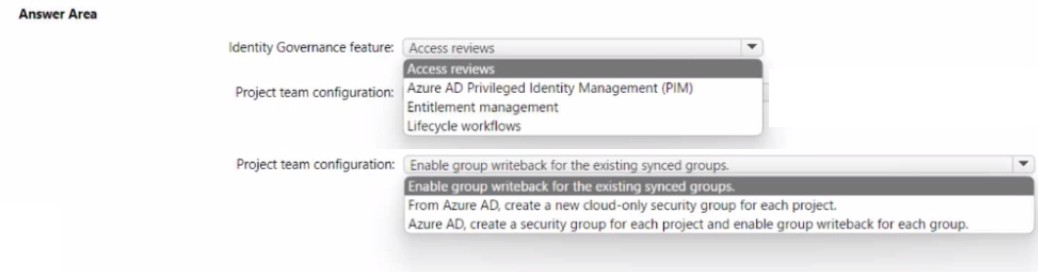
You need to recommend an Azure AD identity Governance solution that meets the
following requirements:
• Project managers must verify that their project group contains only the current members
of their project team
• The members of each project team must only have access to the resources of the project
to which they are assigned
• Users must be removed from a project group automatically if the project manager has
MOT verified the group s membership for 30 days.
• Administrative effort must be minimized.
What should you include in the recommendation? To answer select the appropriate options
in the answer area.
NOTE: Each correct selection is worth one point.
You have a Microsoft 365 E5 subscription.
You are designing a solution to protect confidential data in Microsoft SharePoint Online
sites that contain more than one million documents.
You need to recommend a solution to prevent Personally Identifiable Information (Pll) from
being shared.
Which two components should you include in the recommendation? Each correct answer
presents part of the solution.
NOTE: Each correct selection is worth one point.
A. data loss prevention (DLP) policies
B. sensitivity label policies
C. retention label policies
D. eDiscovery cases
Explanation:
Data loss prevention in Office 365. Data loss prevention (DLP) helps you
protect sensitive information and prevent its inadvertent disclosure. Examples of sensitive
information that you might want to prevent from leaking outside your organization include
financial data or personally identifiable information (PII) such as credit card numbers, social
security numbers, or health records. With a data loss prevention (DLP) policy, you can
identify, monitor, and automatically protect sensitive information across Office 365.
Sensitivity labels from Microsoft Purview Information Protection let you classify and protect
your organization's data without hindering the productivity of users and their ability to
collaborate.Plan for integration into a broader information protection scheme. On top of
coexistence with OME, sensitivity labels can be used along-side capabilities likeMicrosoft
Purview Data Loss Prevention (DLP) and Microsoft Defender for Cloud Apps.
https://motionwave.com.au/keeping-your-confidential-data-secure-with-microsoft-office-
365/
https://docs.microsoft.com/en-us/microsoft-365/solutions/information-protectiondeploy-
protect-information?view=o365-worldwide#sensitivity-labels
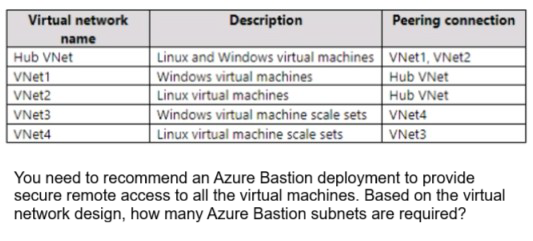
Your company plans to move all on-premises virtual machines to Azure. A network engineer proposes the Azure virtual network design shown in the following table.
A. 1
B. 2
C. 3
D. 4
E. 5
Explanation:
https://docs.microsoft.com/en-us/azure/bastion/vnet-peering
https://docs.microsoft.com/en-us/learn/modules/connect-vm-with-azure-bastion/2-what-isazure-
bastion
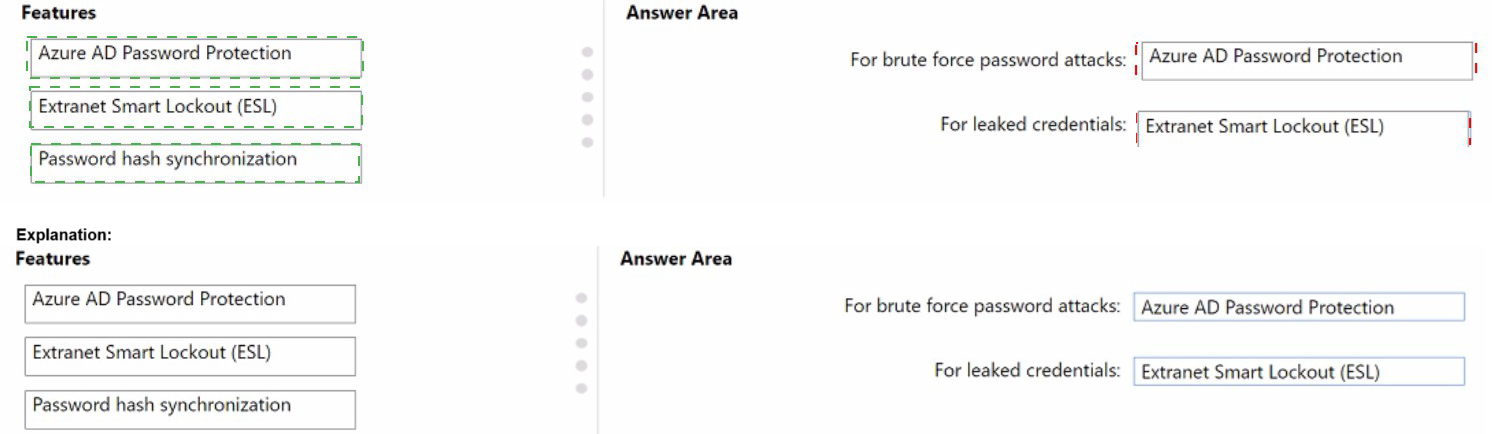
You have a hybrid Azure AD tenant that has pass-through authentication enabled.
You are designing an identity security strategy.
You need to minimize the impact of brute force password attacks and leaked credentials of
hybrid identities.
What should you include in the design? To answer, drag the appropriate features to the
correct requirements. Each feature may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.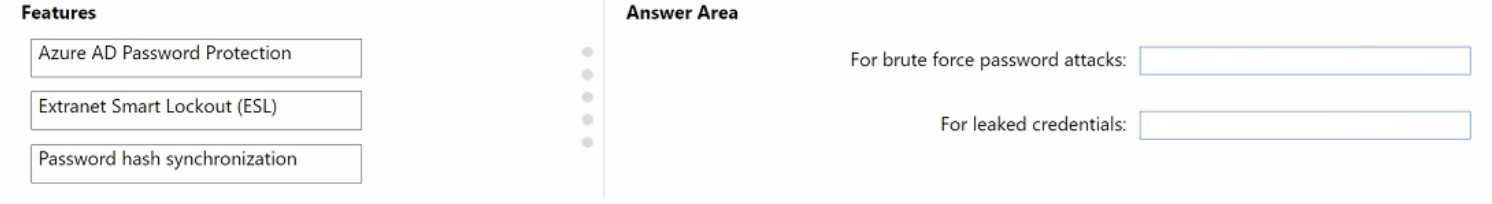
For a Microsoft cloud environment, you are designing a security architecture based on the
Microsoft Cloud Security Benchmark.
What are three best practices for identity management based on the Azure Security
Benchmark? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
A. Manage application identities securely and automatically.
B. Manage the lifecycle of identities and entitlements
C. Protect identity and authentication systems.
D. Enable threat detection for identity and access management.
E. Use a centralized identity and authentication system.
You have a Microsoft 365 E5 subscription.
You need to recommend a solution to add a watermark to email attachments that contain
sensitive data. What should you include in the recommendation?
A. Microsoft Defender for Cloud Apps
B. insider risk management
C. Microsoft Information Protection
D. Azure Purview
Explanation:
https://docs.microsoft.com/en-us/microsoft-365/compliance/sensitivitylabels?
view=o365-worldwide
You can use sensitivity labels to: Provide protection settings that include encryption and
content markings. For example, apply a "Confidential" label to a document or email, and
that label encrypts the content and applies a "Confidential" watermark. Content markings
include headers and footers as well as watermarks, and encryption can also restrict what
actions authorized people can take on the content. Protect content in Office apps across
different platforms and devices.
Supported by Word, Excel, PowerPoint, and Outlook on
the Office desktop apps and Office on the web. Supported on Windows, macOS, iOS, and
Android. Protect content in third-party apps and services by using Microsoft Defender for
Cloud Apps. With Defender for Cloud Apps, you can detect, classify, label, and protect
content in third-party apps and services, such as SalesForce, Box, or DropBox, even if the
third-party app or service does not read or support sensitivity labels.
A customer is deploying Docker images to 10 Azure Kubernetes Service (AKS) resources
across four Azure subscriptions. You are evaluating the security posture of the customer.
You discover that the AKS resources are excluded from the secure score
recommendations. You need to produce accurate recommendations and update the secure
score.
Which two actions should you recommend in Microsoft Defender for Cloud? Each correct
answer presents part of the solution.
NOTE: Each correct selection is worth one point.
A. Configure auto provisioning.
B. Assign regulatory compliance policies.
C. Review the inventory.
D. Add a workflow automation.
E. Enable Defender plans.
Explanation:
https://docs.microsoft.com/en-us/azure/defender-for-cloud/update-regulatorycompliance-packages
https://docs.microsoft.com/en-us/azure/defender-for-cloud/workflowautomation
Your on-premises network contains an e-commerce web app that was developed in Angular and Node.js. The web app uses a MongoDB database. You plan to migrate the web app to Azure. The solution architecture team proposes the following architecture as an Azure landing zone.

A. Yes
B. No
You have the following on-premises servers that run Windows Server:
• Two domain controllers in an Active Directory Domain Services (AD DS) domain
• Two application servers named Server1 and Server2 that run ASP.NET web apps
• A VPN server named Server3 that authenticates by using RADIUS and AD DS
End users use a VPN to access the web apps over the internet.
You need to redesign a user access solution to increase the security of the connections to
the web apps. The solution must minimize the attack surface and follow the Zero Trust
principles of the Microsoft Cybersecurity Reference Architectures (MCRA).
What should you include in the recommendation?
A. Configure connectors and rules in Microsoft Defender for Cloud Apps.
B. Configure web protection in Microsoft Defender for Endpoint.
C. Publish the web apps by using Azure AD Application Proxy.
D. Configure the VPN to use Azure AD authentication.
Your company has on-premises Microsoft SQL Server databases.
The company plans to move the databases to Azure.
You need to recommend a secure architecture for the databases that will minimize
operational requirements for patching and protect sensitive data by using dynamic data
masking. The solution must minimize costs.
What should you include in the recommendation?
A. Azure SQL Managed Instance
B. Azure Synapse Analytics dedicated SQL pools
C. Azure SQL Database
D. SQL Server on Azure Virtual Machines
You are designing a ransomware response plan that follows Microsoft Security Best
Practices-
You need to recommend a solution to limit the scope of damage of ransomware attacks
without being locked out.
What should you include in the recommendations?
A. Privileged Access Workstations (PAWs)
B. emergency access accounts
C. device compliance policies
D. Customer Lockbox for Microsoft Azure
You are designing the encryption standards for data at rest for an Azure resource.
You need to provide recommendations to ensure that the data at rest is encrypted by using
AES-256 keys. The solution must support rotating the encryption keys monthly.
Solution: For blob containers in Azure Storage, you recommend encryption that uses
customer-managed keys (CMKs).
Does this meet the goal?
A. Yes
B. No
| Page 6 out of 15 Pages |
| Previous |