Topic 3: Mix Questions
You have an Azure AD tenant that syncs with an Active Directory Domain Services (AD
DS) domain.
You have an on-premises datacenter that contains 100 servers. The servers run Windows
Server and are backed up by using Microsoft Azure Backup Server (MABS).
You are designing a recovery solution for ransomware attacks. The solution follows
Microsoft Security Best Practices.
You need to ensure that a compromised administrator account cannot be used to delete
the backups.
What should you do?
A. From a Recovery Services vault generate a security PIN for critical operations.
B. From Azure Backup, configure multi-user authorization by using Resource Guard.
C. From Microsoft Azure Backup Setup, register MABS with a Recovery Services vault
D. From Azure AD Privileged Identity Management (PIM), create a role assignment for the Backup Contributor role.
You have an Azure subscription. The subscription contains 100 virtual machines that run
Windows Server. The virtual machines are managed by using Azure Policy and Microsoft
Defender for Servers.
You need to enhance security on the virtual machines. The solution must meet the
following requirements:
• Ensure that only apps on an allowlist can be run.
• Require administrators to confirm each app added to the allowlist.
• Automatically add unauthorized apps to a blocklist when an attempt is made to launch the
app.
• Require administrators to approve an app before the app can be moved from the blocklist
to the allowlist.
What should you include in the solution?
A. a compute policy in Azure Policy
B. admin consent settings for enterprise applications in Azure AD
C. adaptive application controls in Defender for Servers
D. app governance in Microsoft Defender for Cloud Apps
You are designing the encryption standards for data at rest for an Azure resource.
You need to provide recommendations to ensure that the data at rest is encrypted by using
AES-256 keys. The solution must support rotating the encryption keys monthly.
Solution: For blob containers in Azure Storage, you recommend encryption that uses
Microsoft-managed keys within an encryption scope.
Does this meet the goal?
A. Yes
B. No
Explanation:
https://docs.microsoft.com/en-us/azure/key-vault/keys/how-to-configure-keyrotation
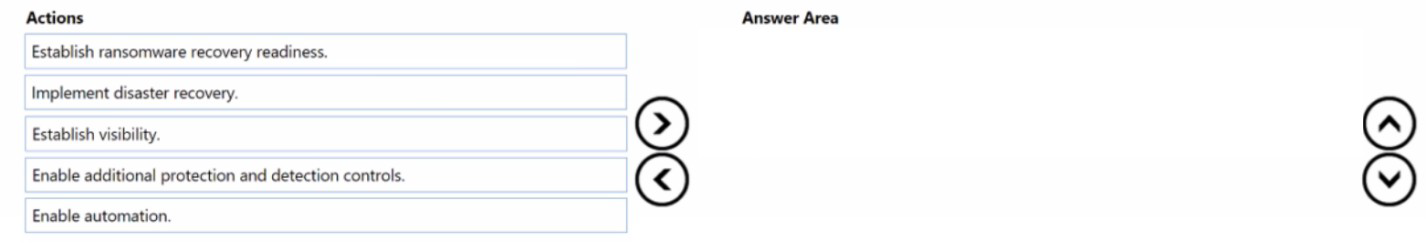
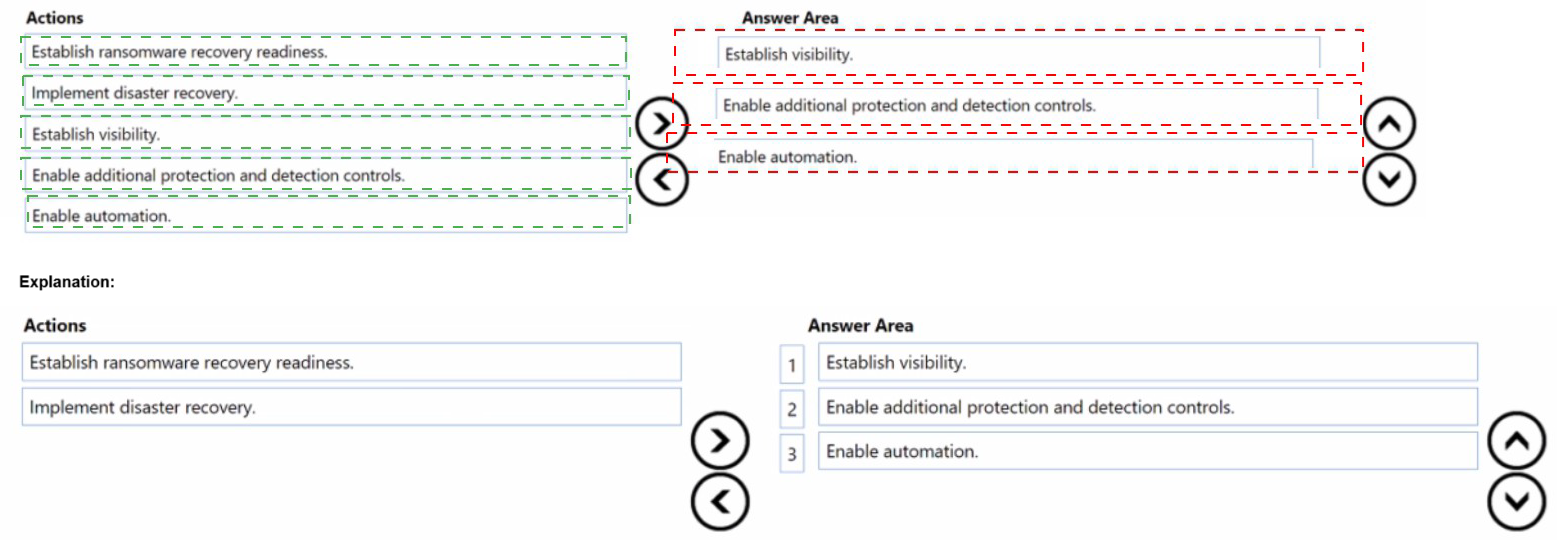
You are designing a security operations strategy based on the Zero Trust framework.
You need to increase the operational efficiency of the Microsoft Security Operations Center
(SOC).
Based on the Zero Trust framework, which three deployment objectives should you
prioritize in sequence? To answer, move the appropriate objectives from the list of
objectives to the answer area and arrange them in the correct order.
You are designing a new Azure environment based on the security best practices of the
Microsoft Cloud Adoption Framework for Azure. The environment will contain one
subscription for shared infrastructure components and three separate subscriptions for
applications.
You need to recommend a deployment solution that includes network security groups
(NSGs) Azure Key Vault, and Azure Bastion. The solution must minimize deployment effort
and follow security best practices of the Microsoft Cloud Adoption Framework for Azure.
What should you include in the recommendation?
A. the Azure landing zone accelerator
B. the Azure Will-Architected Framework
C. Azure Security Benchmark v3
D. Azure Advisor
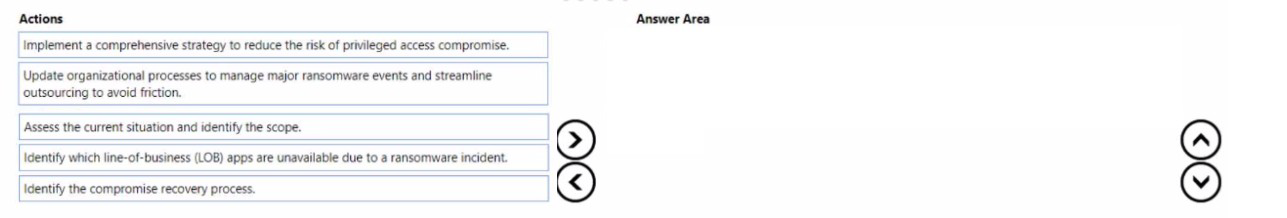
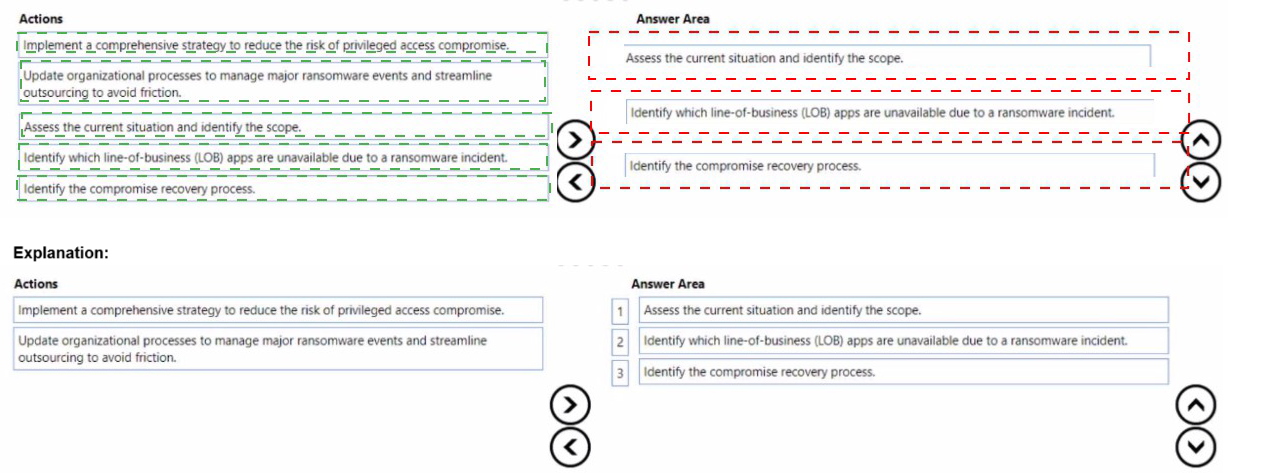
Your company wants to optimize ransomware incident investigations.
You need to recommend a plan to investigate ransomware incidents based on the
Microsoft Detection and Response Team (DART) approach.
Which three actions should you recommend performing in sequence in the plan? To
answer, move the appropriate actions from the list of actions to the answer area and
arrange them in the correct order.
You have an Azure subscription that has Microsoft Defender for Cloud enabled.
You are evaluating the Azure Security Benchmark V3 report.
In the Secure management ports controls, you discover that you have 0 out of a potential 8
points.
You need to recommend configurations to increase the score of the Secure management
ports controls.
Solution: You recommend enabling just-in-time (JIT) VM access on all virtual machines.
Does this meet the goal?
A. Yes
B. No
Explanation:
https://docs.microsoft.com/en-us/security/benchmark/azure/security-controlsv3-
privileged-access#pa-2-avoid-standing-access-for-user-accounts-and-permissions
Your company has a Microsoft 365 E5 subscription.
The company wants to identify and classify data in Microsoft Teams, SharePoint Online,
and Exchange Online.
You need to recommend a solution to identify documents that contain sensitive information.
What should you include in the recommendation?
A. data classification content explorer
B. data loss prevention (DLP)
C. eDiscovery
D. Information Governance
Your company plans to deploy several Azure App Service web apps. The web apps will be
deployed to the West Europe Azure region. The web apps will be accessed only by
customers in Europe and the United States.
You need to recommend a solution to prevent malicious bots from scanning the web apps
for vulnerabilities. The solution must minimize the attach surface.
What should you include in the recommendation?
A. Azure Firewall Premium
B. Azure Application Gateway Web Application Firewall (WAF)
C. Network security groups (NSGs)
D. Azure Traffic Manager and application security groups
Explanation:
https://docs.microsoft.com/en-us/azure/web-application-firewall/ag/botprotection
Note: This question is part of a series of questions that present the same scenario. Each
question in the series contains a unique solution that might meet the stated goals. Some
question sets might have more than one correct solution, while others might not have a
correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result,
these questions will not appear in the review screen.
You are designing the encryption standards for data at rest for an Azure resource.
You need to provide recommendations to ensure that the data at rest is encrypted by using
AES-256 keys. The solution must support rotating the encryption keys monthly.
Solution: For Azure SQL databases, you recommend Transparent Data Encryption (TDE)
that uses Microsoft-managed keys.
Does this meet the goal?
A. Yes
B. No
You have an Azure subscription that has Microsoft Defender for Cloud enabled.
You need to enforce ISO 27001:2013 standards for new resources deployed to the
subscription. The solution must ensure that noncompliant resources are automatically
detected.
What should you use?
A. Azure Blueprints
B. The regulatory compliance dashboard in Defender for Cloud
C. Azure role-based access control (Azure RBAC)
D. Azure Policy
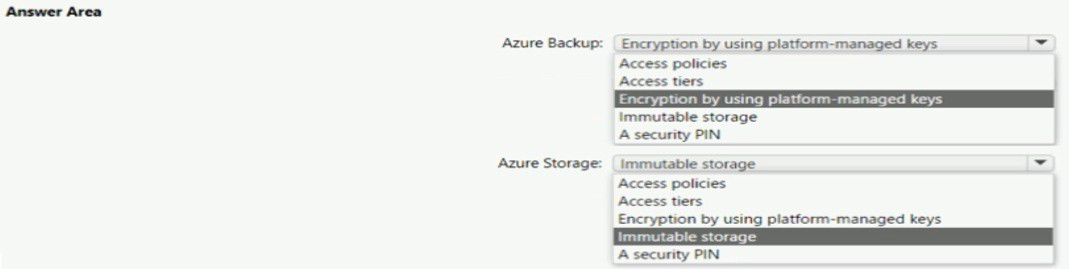
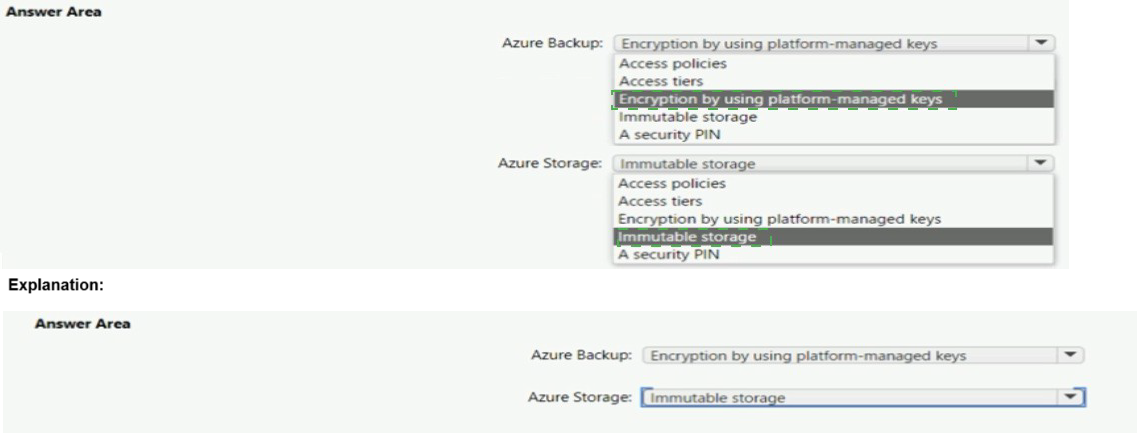
Your company wants to optimize using Azure to protect its resources from ransomware.
You need to recommend which capabilities of Azure Backup and Azure Storage provide
the strongest protection against ransomware attacks. The solution must follow Microsoft
Security Best Practices.
What should you recommend? To answer, select the appropriate options in the answer
area.
NOTE: Each correct selection is worth one point.
| Page 5 out of 15 Pages |
| Previous |