Topic 3: Mix Questions
Your company is moving a big data solution to Azure.
The company plans to use the following storage workloads:
• Azure Storage blob containers
• Azure Data Lake Storage Gen2
• Azure Storage file shares
• Azure Disk Storage
Which two storage workloads support authentication by using Azure Active Directory
(Azure AD)?
Each correct answer presents a complete solution. NOTE: Each correct selection is worth
one point.
A. Azure Disk Storage
B. Azure Storage blob containers
C. Azure Storage file shares
D. Azure Data Lake Storage Gen2
Explanation:
https://docs.microsoft.com/en-us/azure/storage/blobs/authorize-accessazure-
active-directory
https://docs.microsoft.com/en-us/azure/databricks/data/data-sources/azure/adlsgen2/
azure-datalake-gen2-sp-access
Your company has an on-premise network in Seattle and an Azure subscription. The onpremises
network contains a Remote Desktop server.
The company contracts a third-party development firm from France to develop and deploy
resources to the virtual machines hosted in the Azure subscription.
Currently, the firm establishes an RDP connection to the Remote Desktop server. From the
Remote Desktop connection, the firm can access the virtual machines hosted in Azure by
using custom administrative tools installed on the Remote Desktop server. All the traffic to
the Remote Desktop server is captured by a firewall, and the firewall only allows specific
connections from France to the server.
You need to recommend a modern security solution based on the Zero Trust model. The
solution must minimize latency tor developers.
Which three actions should you recommend? Each correct answer presents part of the
solution.
NOTE: Each correct selection is worth one point.
A. Configure network security groups (NSGs) to allow access from only specific logical groupings of IP address ranges.
B. Implement Azure Firewall to restrict host pool outbound access.
C. Configure Azure Active Directory (Azure AD) Conditional Access with multi-factor authentication (MFA) and named locations.
D. Migrate from the Remote Desktop server to Azure Virtual Desktop.
E. Deploy a Remote Desktop server to an Azure region located in France.
Explanation:
https://docs.microsoft.com/en-us/azure/firewall/protect-azure-virtual-desktop
You have an Azure AD tenant that syncs with an Active Directory Domain Services {AD DS) domain. Client computers run Windows and are hybrid-joined to Azure AD.
You are designing a strategy to protect endpoints against ransomware. The strategy
follows Microsoft Security Best Practices.
You plan to remove all the domain accounts from the Administrators group on the Windows
computers.
You need to recommend a solution that will provide users with administrative access to the
Windows computers only when access is required. The solution must minimize the lateral
movement of ransomware attacks if an administrator account on a computer is
compromised.
What should you include in the recommendation?
A. Local Administrator Password Solution (LAPS)
B. Privileged Access Workstations (PAWs)
C. Azure AD Privileged Identity Management (PIM)
D. Azure AD identity Protection
You have an operational model based on the Microsoft Cloud Adoption framework for Azure. You need to recommend a solution that focuses on cloud-centric control areas to protect resources such as endpoints, database, files, and storage accounts. What should you include in the recommendation?
A. security baselines in the Microsoft Cloud Security Benchmark
B. modern access control
C. business resilience
D. network isolation
You have a customer that has a Microsoft 365 subscription and an Azure subscription.
The customer has devices that run either Windows, iOS, Android, or macOS. The Windows
devices are deployed on-premises and in Azure.
You need to design a security solution to assess whether all the devices meet the
customer's compliance rules.
What should you include in the solution?
A. Microsoft Information Protection
B. Microsoft Defender for Endpoint
C. Microsoft Sentinel
D. Microsoft Intune
Explanation:
https://docs.microsoft.com/en-us/mem/intune/protect/compliance-policymonitor#
open-the-compliance-dashboard
Your on-premises network contains an e-commerce web app that was developed in Angular and Node.js. The web app uses a MongoDB database You plan to migrate the web app to Azure. The solution architecture team proposes the following architecture as an Azure landing zone.

A. Yes
B. No
Explanation:
When using Azure-provided PaaS services (e.g., Azure Storage, Azure
Cosmos DB, or Azure Web App, use the PrivateLink connectivity option to ensure all data
exchanges are over the private IP space and the traffic never leaves the Microsoft network
Your company is preparing for cloud adoption.
You are designing security for Azure landing zones.
Which two preventative controls can you implement to increase the secure score? Each
NOTE: Each correct selection is worth one point.
A. Azure Firewall
B. Azure Web Application Firewall (WAF)
C. Microsoft Defender for Cloud alerts
D. Azure Active Directory (Azure AD Privileged Identity Management (PIM)
E. Microsoft Sentinel
Explanation:
https://docs.microsoft.com/en-us/azure/defender-for-cloud/secure-scoresecurity-
controls
You have a Microsoft 365 subscription and an Azure subscription. Microsoft 365 Defender
and Microsoft Defender for Cloud are enabled.
The Azure subscription contains 50 virtual machines. Each virtual machine runs different
applications on Windows Server 2019.
You need to recommend a solution to ensure that only authorized applications can run on
the virtual machines. If an unauthorized application attempts to run or be installed, the
application must be blocked automatically until an administrator authorizes the application.
Which security control should you recommend?
A. Azure Active Directory (Azure AD) Conditional Access App Control policies
B. OAuth app policies in Microsoft Defender for Cloud Apps
C. app protection policies in Microsoft Endpoint Manager
D. application control policies in Microsoft Defender for Endpoint
Explanation:
https://docs.microsoft.com/en-us/windows/security/threatprotection/
windows-defender-application-control/select-types-of-rules-to-create#windowsdefender-
application-control-policy-rules
You have legacy operational technology (OT) devices and loT devices.
You need to recommend best practices for applying Zero Trust principles to the OT and loT
devices based on the Microsoft Cybersecurity Reference Architectures (MCRA). The
solution must minimize the risk of disrupting business operations.
Which two security methodologies should you include in the recommendation? Each
correct answer presents part of the solution.
NOTE: Each correct selection is worth one point
A. passive traffic monitoring
B. active scanning
C. threat monitoring
D. software patching
You are evaluating an Azure environment for compliance.
You need to design an Azure Policy implementation that can be used to evaluate
compliance without changing any resources.
Which effect should you use in Azure Policy?
A. Deny
B. Disabled
C. Modify
D. Append
Explanation:
Before looking to manage new or updated resources with your new policy
definition, it's best to see how it evaluates a limited subset of existing resources, such as a
test resource group. Use the enforcement mode Disabled (DoNotEnforce) on your policy assignment to prevent the effect from triggering or activity log entries from being created.
https://docs.microsoft.com/en-us/azure/governance/policy/concepts/evaluate-impact
You open Microsoft Defender for Cloud as shown in the following exhibit.
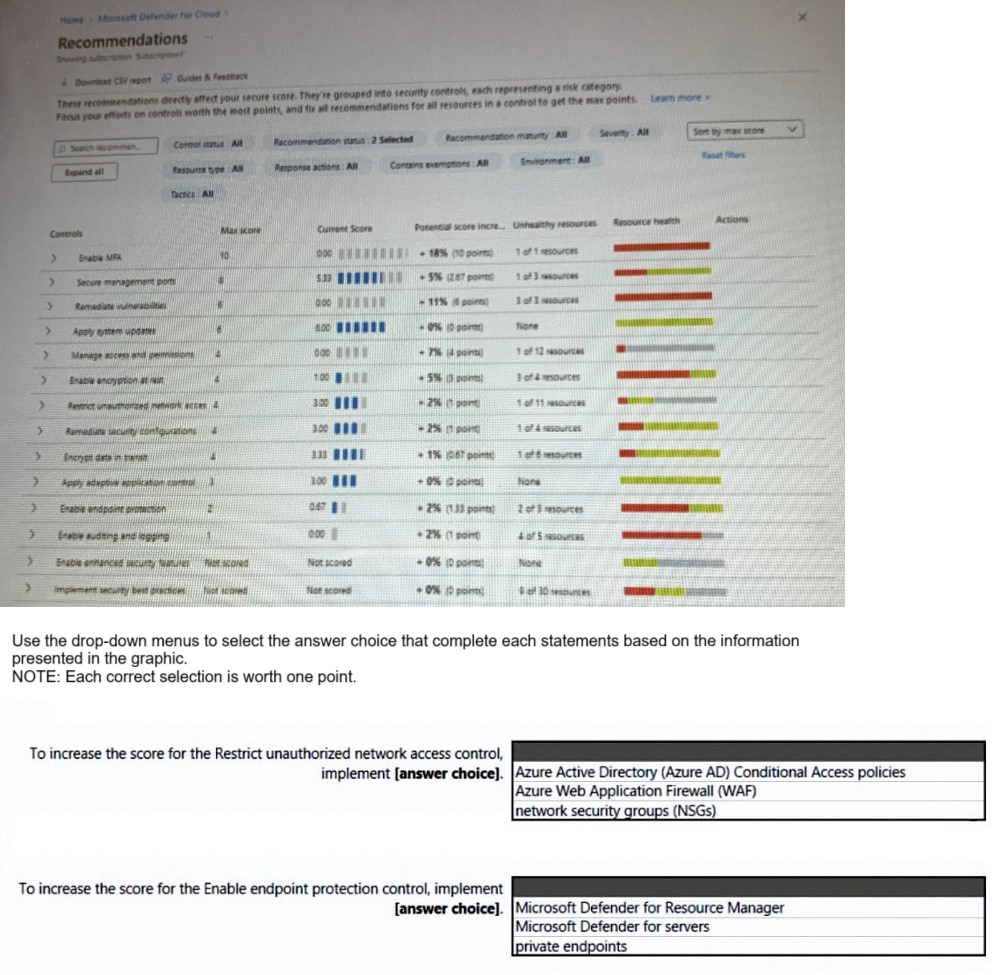
You have an Azure subscription and an on-premises datacenter. The datacenter contains
100 servers that run Windows Server. AJI the servers are backed up to a Recovery
Services vault by using Azure Backup and the Microsoft Azure Recovery Services (MARS)
agent.
You need to design a recovery solution for ransomware attacks that encrypt the onpremises
servers. The solution must follow Microsoft Security Best Practices and protect
against the following risks:
• A compromised administrator account used to delete the backups from Azure Backup
before encrypting the servers
• A compromised administrator account used to disable the backups on the MARS agent
before encrypting the servers
What should you use for each risk? To answer, select the appropriate options in the
answer area.
NOTE: Each correct selection is worth one point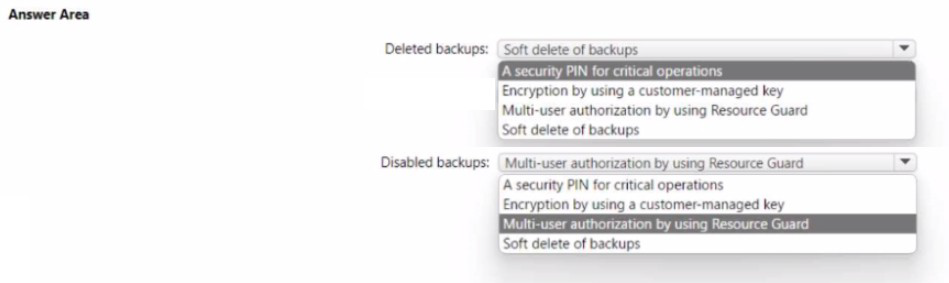
| Page 4 out of 15 Pages |
| Previous |