Topic 3: Mix Questions
You have a Microsoft 365 E5 subscription and an Azure subscripts You need to evaluate
the existing environment to increase the overall security posture for the following
components:
• Windows 11 devices managed by Microsoft Intune
• Azure Storage accounts
• Azure virtual machines
What should you use to evaluate the components? To answer, select the appropriate
options in the answer area.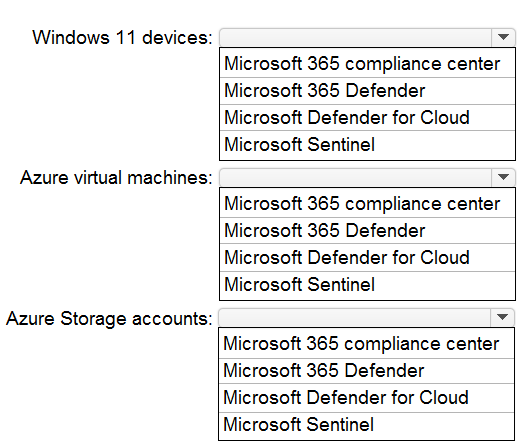
Explanation:
The question asks for the tool to evaluate the existing environment to increase the overall security posture. This is a request for a security posture assessment and management tool that provides secure configuration recommendations, not just alerting or compliance.
Correct Options:
Microsoft 365 Defender:
This is the correct choice for Windows 11 devices managed by Intune. It provides the Microsoft Secure Score for Devices, which is a dedicated security posture assessment for endpoints. It analyzes device configurations, antivirus status, firewall rules, and other security controls against Microsoft's benchmarks, providing a measurable score and specific recommendations to harden the devices.
Microsoft Defender for Cloud:
This is the unified platform for cloud security posture management (CSPM) and threat protection in Azure. It is the definitive tool for evaluating and improving the security posture of Azure resources, including Azure virtual machines and Azure Storage accounts. It provides a secure score, continuously assesses configurations against security benchmarks (like Azure CIS, NIST), and delivers prioritized remediation steps.
Incorrect Options:
Microsoft 365 compliance center:
This center focuses on data governance, compliance, and risk management (e.g., Data Loss Prevention, eDiscovery, Information Protection). It is not the primary tool for evaluating and providing configuration hardening recommendations to improve the security posture of endpoints or Azure infrastructure.
Microsoft Sentinel:
This is a Security Information and Event Management (SIEM) and Security Orchestration, Automation, and Response (SOAR) solution. Its primary function is aggregating, correlating, and investigating security alerts and logs for threat detection and response. While it can ingest data from posture tools, Sentinel itself is not a posture assessment tool that provides a "secure score" or configuration evaluation.
Reference:
Microsoft's documentation clearly delineates the roles of these services. Microsoft Secure Score (accessed via Microsoft 365 Defender) measures an organization's endpoint security posture. Microsoft Defender for Cloud's secure score is the central feature for measuring and improving the security posture of Azure, AWS, and Google Cloud resources, including compute and storage services.
Your company has a Microsoft 365 E5 subscription.
The Chief Compliance Officer plans to enhance privacy management in the working
environment. You need to recommend a solution to enhance the privacy management. The
solution must meet the following requirements:
• Identify unused personal data and empower users to make smart data handling
decisions.
• Provide users with notifications and guidance when a user sends personal data in
Microsoft Teams.
• Provide users with recommendations to mitigate privacy risks.
What should you include in the recommendation?
A. Microsoft Viva Insights
B. Advanced eDiscovery
C. Privacy Risk Management in Microsoft Priva
D. Communication compliance in insider risk management
Explanation:
This question focuses on enhancing privacy management by identifying, monitoring, and guiding the handling of personal data. The requirements specifically ask for a solution that identifies unused data, provides in-app guidance (like in Teams), and offers recommendations to mitigate privacy risks. This points directly to a dedicated privacy management tool within Microsoft's compliance suite.
Correct Option:
C. Privacy Risk Management in Microsoft Priva
Microsoft Priva is the dedicated privacy risk management solution within the Microsoft Purview compliance suite. Its Privacy Risk Management component is explicitly designed to meet all three requirements:
It uses machine learning to identify and map personal data across the tenant, including unused or overexposed data.
It can deliver real-time policy tips and guidance in applications like Microsoft Teams and Outlook when users are about to send personal data.
It provides insights and actionable recommendations to help organizations and users understand and mitigate privacy risks.
Incorrect Options:
A. Microsoft Viva Insights
Viva Insights is a productivity and wellbeing tool that provides personal and organizational insights based on Microsoft 365 collaboration data. While it handles data responsibly, its primary goal is not to manage privacy risks, send policy tips about sending personal data, or identify unused personal data stores.
B. Advanced eDiscovery
Advanced eDiscovery is a tool for legal and investigative purposes. It is used to identify, hold, and export data relevant to a legal case or internal investigation. It is reactive and case-focused, not designed for proactive privacy management, user guidance, or ongoing risk mitigation.
D. Communication compliance in insider risk management
This is a policy-based solution within the Insider Risk Management suite designed to detect and remediate inappropriate or risky communications (e.g., harassment, sensitive information sharing). While it can scan for keywords, its purpose is regulatory and internal policy compliance monitoring, not empowering users with guidance or managing general privacy risks related to personal data handling.
Reference:
Microsoft's documentation for Priva Privacy Risk Management states it helps organizations "identify and remediate privacy risks" and "empower employees to make smarter data handling decisions with built-in user notifications and guidance in Microsoft 365 apps," directly aligning with the scenario's requirements.
You need to recommend a security methodology for a DevOps development process
based on the Microsoft Cloud Adoption Framework for Azure.
During which stage of a continuous integration and continuous deployment (CI/CD)
DevOps process should each security-related task be performed? To answer, select the
appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
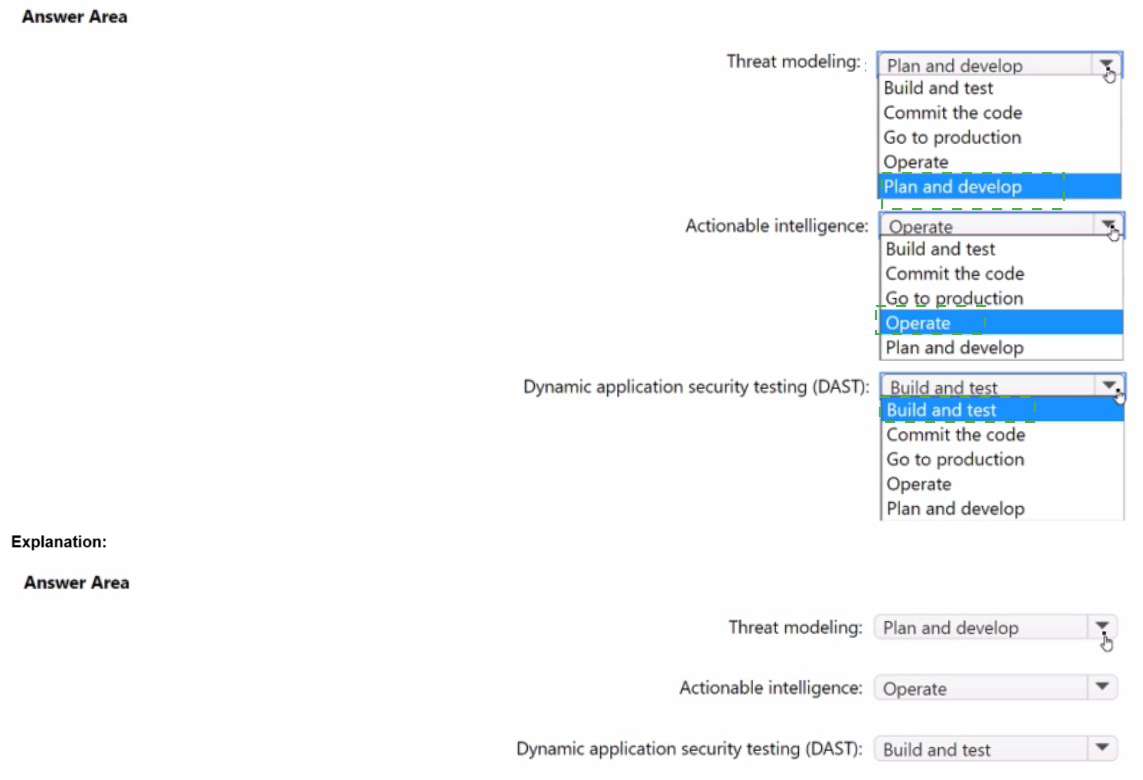
Explanation:
This question asks to align specific DevSecOps security tasks with the correct phase of a CI/CD pipeline. The goal is to integrate security "shifting left" (early in development) while also maintaining vigilance in operations.
Correct Options:
Threat modeling: Plan and develop
Threat modeling is a design-time activity. It involves analyzing the architecture and design of an application for potential security threats before any code is written. Therefore, it belongs in the Plan and Develop stage to identify and mitigate security flaws proactively at the earliest, most cost-effective phase.
Actionable intelligence: Operate
Actionable intelligence refers to using security insights from monitoring and incident response to inform improvements. This is an operational feedback activity. After an application is in production (Operate), data from attacks, vulnerabilities, and telemetry is analyzed to produce intelligence that feeds back into the planning phase for the next iteration.
Dynamic application security testing (DAST): Build and test
DAST is a testing methodology that analyzes a running application from the outside (like an attacker would) to find runtime vulnerabilities. Since it requires a functional, deployable application build to test, it is performed during the Build and Test stage of the CI/CD pipeline, typically in a staging environment before production deployment.
Incorrect Options for Context:
Commit the code: This is the stage where developers push code to the repository. Security tasks here are typically Static Application Security Testing (SAST) and code review, not DAST (which needs a built app) or threat modeling (which is earlier).
Go to production: This is the deployment/release stage. Security tasks here are final gates like security approval workflows or dependency scanning, not the primary execution phase for DAST or threat modeling.
Placing Threat modeling in any later phase defeats the "shift-left" purpose. Placing DAST in "Operate" is too late, as vulnerabilities should be caught before production. Placing Actionable intelligence in "Plan and develop" is incorrect, as the intelligence is generated from operational data.
Reference:
The Microsoft Cloud Adoption Framework for Azure's DevSecOps guidance emphasizes integrating security at every stage. It specifically recommends:
Threat modeling during design/planning.
DAST as part of the automated testing in the CI/CD pipeline.
Using operational insights (Actionable intelligence) from security monitoring to continuously improve the development process.
You are designing a security strategy for providing access to Azure App Service web apps
through an Azure Front Door instance.
You need to recommend a solution to ensure that the web apps only allow access through
the Front Door instance.
Solution: You recommend access restrictions to allow traffic from the backend IP address
of the Front Door instance.
Does this meet the goal?
A. Yes
B. No
Explanation:
The goal is to restrict access to the Azure App Service web apps only through Azure Front Door. The proposed solution uses access restrictions based on the backend IP address of Front Door. However, this method has a critical flaw because Front Door's backend IP address range is not static or exclusive; it is shared with other Azure services and can change.
Correct Answer: B. No
Correct Option Explanation:
The recommended solution does not fully meet the goal. While App Service Access Restrictions can limit traffic by source IP, Azure Front Door operates from a large, shared set of Azure infrastructure IP addresses that are not dedicated to your specific Front Door instance. These IPs are also used by other Azure services, meaning blocking all other IPs is not feasible, and using this range as an allowlist is not secure or exclusive. A truly effective solution requires a method to validate that incoming requests are specifically from your Front Door instance, not just from the Azure IP range.
The correct, more secure solution would involve:
Service Tags (More practical than IPs):
Configure App Service Access Restrictions to allow the AzureFrontDoor.Backend Service Tag. This tag represents the official IP range for Front Door backends and is managed by Microsoft, but it's still a shared range.
Front Door ID Header Validation (Most Secure):
The definitive method is to configure Front Door to send a unique, secret header (e.g., X-Azure-FDID) with a verified value to the origin (App Service). Then, configure the App Service to only accept requests that contain this specific header and value. This guarantees that traffic is explicitly from your Front Door instance, regardless of source IP.
Reference:
Microsoft documentation for securing an App Service behind Front Door explicitly states that IP-based filtering using Front Door's backend IPs is not recommended for production due to the shared, dynamic nature of the IP range. It recommends using the X-Azure-FDID header validation approach as the primary mechanism to "lock your App Service to Azure Front Door."
You use Azure Pipelines with Azure Repos to implement continuous integration and
continuous deployment (CI/CO) workflows.
You need to recommend best practices to secure the stages of the CI/CD workflows based
on the Microsoft Cloud Adoption Framework for Azure.
What should you include in the recommendation for each stage? To answer, select the
appropriate options in the answer area.
NOTE: Each correct selection is worth one point.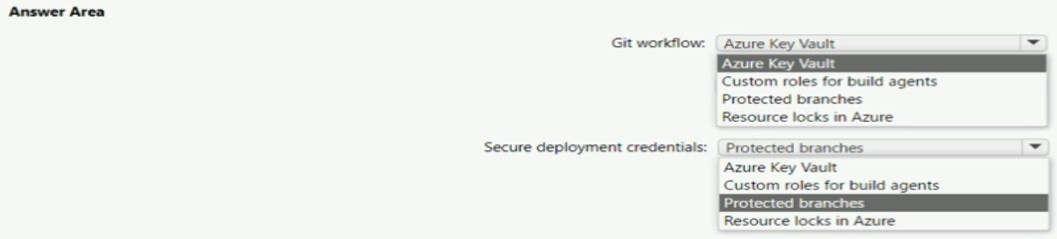
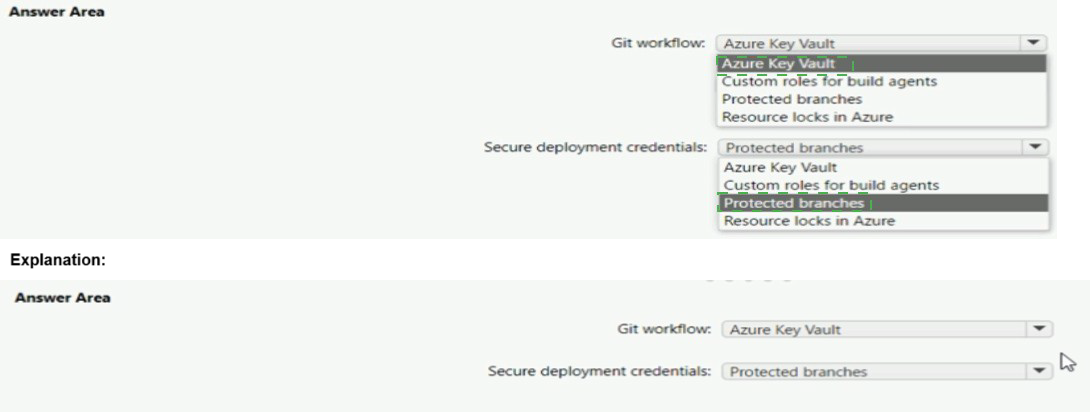
Explanation:
The question asks for best practices to secure two specific stages of a CI/CD workflow. The Git workflow stage concerns securing the source code and its change process, while Secure deployment credentials concerns managing the secrets used by the pipeline to deploy resources.
Correct Options:
Git workflow: Protected branches
Securing the Git workflow fundamentally involves controlling how code changes are merged into critical branches (like main). Protected branch policies in Azure Repos are the primary tool for this. They enforce security and quality gates by requiring pull requests, a minimum number of reviewers, and successful build validation before any merge can occur. This prevents direct, unreviewed pushes and ensures all changes are vetted.
Secure deployment credentials: Azure Key Vault
The best practice for managing secrets (like passwords, certificates, API keys) used by pipelines for deployment is to never store them in plaintext in code, variables, or build agents. Azure Key Vault is the dedicated Azure service for securely storing and managing secrets. Pipelines can securely retrieve secrets from Key Vault at runtime using managed identities or service principals, ensuring credentials are not exposed in logs or source code.
Incorrect Options:
Azure Key Vault for Git workflow:
Key Vault secures secrets, not the code change process itself. It does not enforce how code is reviewed or merged.
Custom roles for build agents:
This is a security practice for least-privilege access control for the pipeline's identity (service principal or managed identity) that deploys resources to Azure. While important for securing the deployment stage, it is not the direct tool for securing deployment credentials themselves; Key Vault is.
Resource locks in Azure:
This is a post-deployment governance control used in Azure to prevent accidental deletion or modification of critical resources (e.g., setting a CanNotDelete lock). It is not a CI/CD workflow security practice for the Git or credential management stages.
Reference:
The Microsoft Cloud Adoption Framework for Azure's DevSecOps guidance clearly recommends:
Using branch policies and protected branches to secure the development workflow and enforce code quality.
Integrating Azure Key Vault with Azure Pipelines to manage deployment secrets, as outlined in the "Secure your pipeline" and "Secret management" best practices.
You need to recommend a strategy for routing internet-bound traffic from the landing zones. The solution must meet the landing zone requirements. What should you recommend as part of the landing zone deployment?
A. service chaining
B. local network gateways
C. forced tunneling
D. a VNet-to-VNet connection
Explanation:
In Azure landing zone architectures, a common security requirement is to inspect all internet-bound traffic from workloads. This is typically achieved using a hub-and-spoke model where the hub VNet contains a firewall/NVA. The solution needs to ensure traffic from spoke VNets (landing zones) destined for the internet is routed through this central inspection point.
Correct Answer:
A. service chaining
Correct Option Explanation:
Service chaining is the Azure capability that enables you to direct traffic from one virtual network to a virtual appliance (like a firewall or NVA) in a different virtual network via user-defined routes (UDRs). This is the specific mechanism used to implement the "forced tunneling" requirement through a central hub. You create a UDR in the landing zone subnet with a route (e.g., 0.0.0.0/0) pointing to the IP address of the Azure Firewall or NVA in the hub VNet as the next hop, "chaining" the traffic to that service.
Incorrect Options:
B. local network gateways:
A local network gateway represents an on-premises VPN device's IP address in Azure for setting up a Site-to-Site (S2S) VPN connection. It is used for hybrid connectivity, not for routing internet traffic between Azure VNets.
C. forced tunneling:
This is the requirement or design goal (to "force" internet traffic through an inspection point), not the implementation component you deploy. Forced tunneling is achieved by deploying service chaining with UDRs. The question asks for what to deploy as part of the landing zone.
D. a VNet-to-VNet connection:
This typically refers to VNet Peering, which directly connects two VNets. While peering is needed for the hub-spoke connectivity, it alone does not force traffic through an appliance. Without UDRs (service chaining), peered traffic flows directly between VNets.
To give a definitive answer, the landing zone requirements would need to specify the intent to route internet traffic through a centralized security service. Given the options, "service chaining" is the technical implementation for that pattern.
A customer has a Microsoft 365 E5 subscription and an Azure subscription.
The customer wants to centrally manage security incidents, analyze log, audit activity, and
search for potential threats across all deployed services.
You need to recommend a solution for the customer. The solution must minimize costs.
What should you include in the recommendation?
A. Microsoft 365 Defender
B. Microsoft Defender for Cloud
C. Microsoft Defender for Cloud Apps
D. Microsoft Sentinel
Your on-premises network contains an e-commerce web app that was developed in Angular and Nodejs. The web app uses a MongoDB database. You plan to migrate the web app to Azure. The solution architecture team proposes the following architecture as an Azure landing zone.
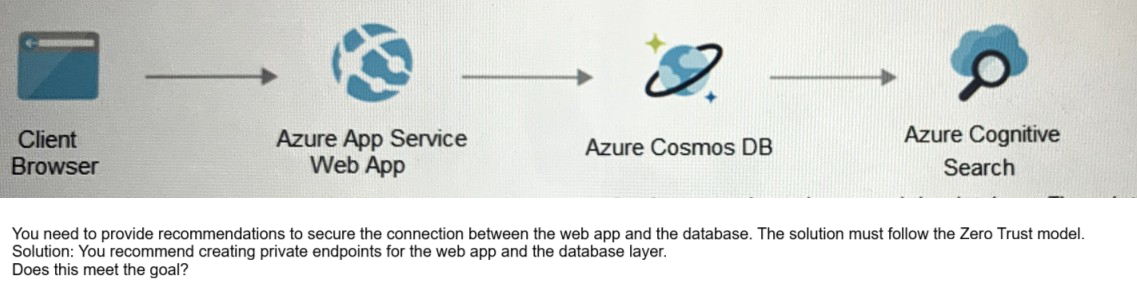
A. Yes
B. No
Explanation:
When using Azure-provided PaaS services (e.g., Azure Storage, Azure
Cosmos DB, or Azure Web App, use the PrivateLink connectivity option to ensure all data
exchanges are over the private IP space and the traffic never leaves the Microsoft network.
https://docs.microsoft.com/en-us/azure/cosmos-db/how-to-configure-private-endpoints
Your company plans to apply the Zero Trust Rapid Modernization Plan (RaMP) to its IT
environment.
You need to recommend the top three modernization areas to prioritize as part of the plan.
Which three areas should you recommend based on RaMP? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
A. data, compliance, and governance
B. user access and productivity
C. infrastructure and development
D. modern security operations
E. operational technology (OT) and loT
You have an Azure subscription that has Microsoft Defender for Cloud enabled. You need to enforce ISO 2700V2013 standards for the subscription. The solution must ensure that noncompliant resources are remediated automatically. What should you use?
A. the regulatory compliance dashboard in Defender for Cloud
B. Azure Policy
C. Azure Blueprints
D. Azure role-based access control (Azure RBAC)
Explanation:
https://azure.microsoft.com/en-us/blog/simplifying-your-environment-setupwhile-
meeting-compliance-needs-with-built-in-azure-blueprints/
You have a customer that has a Microsoft 365 subscription and uses the Free edition of
Azure Active Directory (Azure AD)
The customer plans to obtain an Azure subscription and provision several Azure resources.
You need to evaluate the customer's security environment.
What will necessitate an upgrade from the Azure AD Free edition to the Premium edition?
A. role-based authorization
B. Azure AD Privileged Identity Management (PIM)
C. resource-based authorization
D. Azure AD Multi-Factor Authentication
Explanation:
(https://docs.microsoft.com/en-us/azure/active-directory/privileged-identitymanagement/pim-configure)
https://www.microsoft.com/en-us/security/business/identity-access/azure-active-directorypricing?
rtc=1
Your company has a Microsoft 365 E5 subscription, an Azure subscription, on-premises
applications, and Active Directory Domain Services (AD DS).
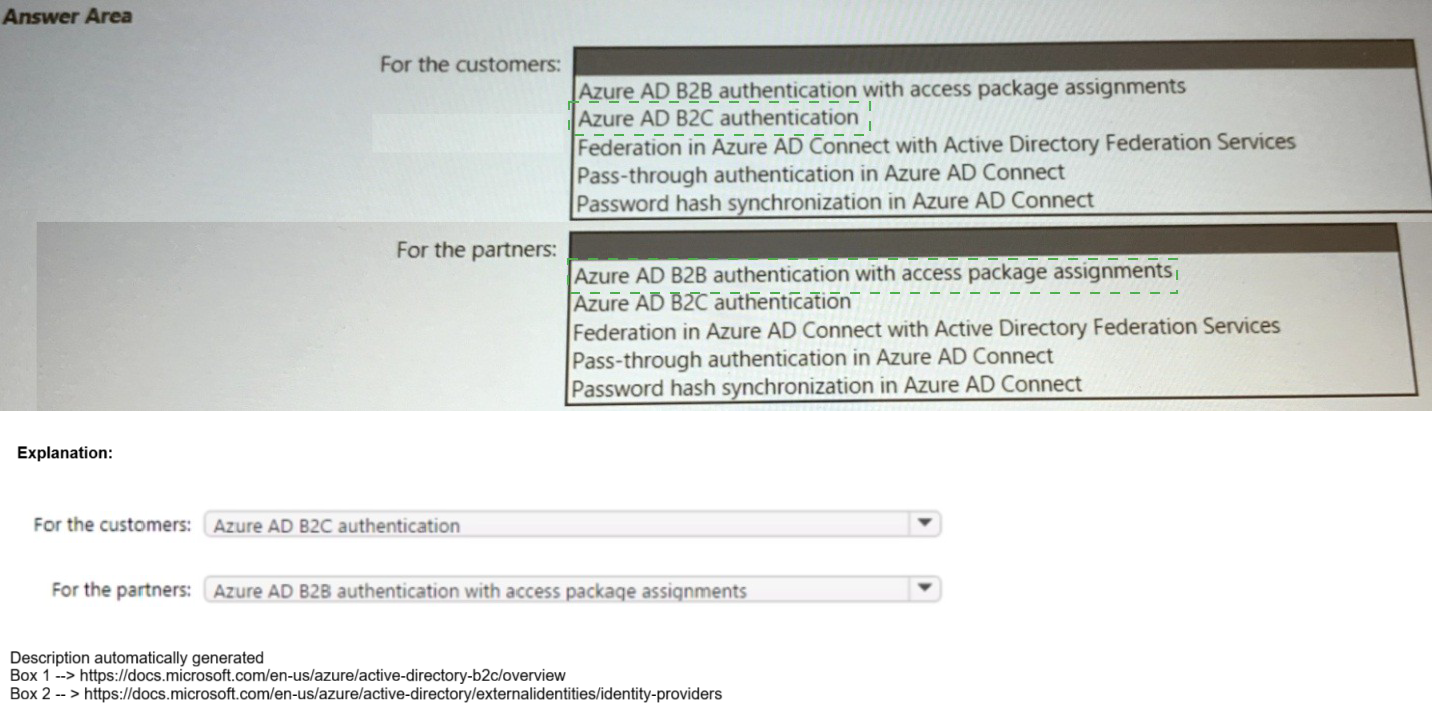
You need to recommend an identity security strategy that meets the following
requirements:
• Ensures that customers can use their Facebook credentials to authenticate to an Azure
App Service website
• Ensures that partner companies can access Microsoft SharePoint Online sites for the
project to which they are assigned
The solution must minimize the need to deploy additional infrastructure components. What
should you include in the recommendation? To answer, select the appropriate options in
the answer area.
NOTE: Each correct selection is worth one point.
| Page 3 out of 15 Pages |
| Previous |