Topic 1: Fabrikam, Inc Case Study 1
OverView
Fabrikam, Inc. is an insurance company that has a main office in New York and a branch
office in Paris.
On-premises Environment
The on-premises network contains a single Active Directory Domain Services (AD DS)
domain named corp.fabrikam.com.
Azure Environment
Fabrikam has the following Azure resources:
• An Azure Active Directory (Azure AD) tenant named fabrikam.onmicrosoft.com that syncs
with corp.fabnkam.com
• A single Azure subscription named Sub1
• A virtual network named Vnet1 in the East US Azure region
• A virtual network named Vnet2 in the West Europe Azure region
• An instance of Azure Front Door named FD1 that has Azure Web Application Firewall
(WAR enabled)
• A Microsoft Sentinel workspace
• An Azure SQL database named ClaimsDB that contains a table named ClaimDetails
• 20 virtual machines that are configured as application servers and are NOT onboarded to
Microsoft Defender for Cloud
• A resource group named TestRG that is used for testing purposes only
• An Azure Virtual Desktop host pool that contains personal assigned session hosts
All the resources in Sub1 are in either the East US or the West Europe region.
Partners
Fabrikam has contracted a company named Contoso, Ltd. to develop applications.
Contoso has the following infrastructure-.
• An Azure AD tenant named contoso.onmicrosoft.com
• An Amazon Web Services (AWS) implementation named ContosoAWS1 that contains
AWS EC2 instances used to host test workloads for the applications of Fabrikam
Developers at Contoso will connect to the resources of Fabrikam to test or update
applications. The developers will be added to a security Group named Contoso Developers
in fabrikam.onmicrosoft.com that will be assigned to roles in Sub1.
The ContosoDevelopers group is assigned the db.owner role for the ClaimsDB database.
Compliance Event
Fabrikam deploys the following compliance environment:
• Defender for Cloud is configured to assess all the resources in Sub1 for compliance to the
HIPAA HITRUST standard.
• Currently, resources that are noncompliant with the HIPAA HITRUST standard are
remediated manually.
• Qualys is used as the standard vulnerability assessment tool for servers.
Problem Statements
The secure score in Defender for Cloud shows that all the virtual machines generate the
following recommendation-. Machines should have a vulnerability assessment solution.
All the virtual machines must be compliant in Defender for Cloud.
ClaimApp Deployment
Fabrikam plans to implement an internet-accessible application named ClaimsApp that will
have the following specification
• ClaimsApp will be deployed to Azure App Service instances that connect to Vnetl and
Vnet2.
• Users will connect to ClaimsApp by using a URL of https://claims.fabrikam.com.
• ClaimsApp will access data in ClaimsDB.
• ClaimsDB must be accessible only from Azure virtual networks.
• The app services permission for ClaimsApp must be assigned to ClaimsDB.
Application Development Requirements
Fabrikam identifies the following requirements for application development:
• Azure DevTest labs will be used by developers for testing.
• All the application code must be stored in GitHub Enterprise.
• Azure Pipelines will be used to manage application deployments.
• All application code changes must be scanned for security vulnerabilities, including
application code or configuration files that contain secrets in clear text. Scanning must be
done at the time the code is pushed to a repository.
Security Requirement
Fabrikam identifies the following security requirements:
• Internet-accessible applications must prevent connections that originate in North Korea.
• Only members of a group named InfraSec must be allowed to configure network security
groups (NSGs} and instances of Azure Firewall, VJM. And Front Door in Sub1.
• Administrators must connect to a secure host to perform any remote administration of the
virtual machines. The secure host must be provisioned from a custom operating system
image.
AWS Requirements
Fabrikam identifies the following security requirements for the data hosted in
ContosoAWSV.
• Notify security administrators at Fabrikam if any AWS EC2 instances are noncompliant
with secure score recommendations.
• Ensure that the security administrators can query AWS service logs directly from the
Azure environment.
Contoso Developer Requirements
Fabrikam identifies the following requirements for the Contoso developers;
• Every month, the membership of the ContosoDevelopers group must be verified.
• The Contoso developers must use their existing contoso.onmicrosoft.com credentials to
access the resources in Sub1.
• The Comoro developers must be prevented from viewing the data in a column named
MedicalHistory in the ClaimDetails table.
Compliance Requirement
Fabrikam wants to automatically remediate the virtual machines in Sub1 to be compliant
with the HIPPA HITRUST standard. The virtual machines in TestRG must be excluded
from the compliance assessment.
You need to recommend a solution to meet the security requirements for the InfraSec group. What should you use to delegate the access?
A. subscription
B. a custom role-based access control (RBAC) role
C. a resource group
D. a management group
Explanation:
To meet specific security requirements for the InfraSec group, the most precise and flexible way to delegate access is by creating a custom RBAC role. This allows you to:
Define exact permissions tailored to InfraSec’s operational needs (e.g., read-only access to security insights, ability to manage Defender settings, etc.)
Assign the role at the appropriate scope (subscription, resource group, or management group)
Enforce least privilege and segregation of duties, aligning with Microsoft’s Zero Trust principles
This approach is recommended when built-in roles (like Security Reader or Contributor) don’t fully meet the group’s requirements.
❌ Why the other options are incorrect:
A. Subscription:
This is a scope, not a method of delegation. You still need a role (built-in or custom) to define what access is granted.
C. Resource group:
Also a scope, not a delegation mechanism. You can assign roles at this level, but it doesn’t define what access is granted.
D. Management group:
Another scope used for organizing multiple subscriptions. It’s useful for governance, but again, you need a role to delegate access.
📚 Reference:
Azure RBAC custom roles
Best practices for RBAC
You need to recommend a solution to scan the application code. The solution must meet the application development requirements. What should you include in the recommendation?
A. Azure Key Vault
B. GitHub Advanced Security
C. Application Insights in Azure Monitor
D. Azure DevTest Labs
Explanation:
To scan application code for vulnerabilities, secrets, and other security issues during development, the recommended solution is GitHub Advanced Security (GHAS).
GHAS provides:
Code scanning
Uses tools like CodeQL to automatically analyze code for security vulnerabilities.
Integrates with GitHub Actions to scan code on every pull request or commit.
Secret scanning
Detects sensitive information such as API keys, credentials, and tokens embedded in the code.
Dependency review
Identifies vulnerable dependencies in project manifests (like package.json, pom.xml).
This solution meets application development requirements because it integrates directly into the development workflow, providing early detection of vulnerabilities before deployment.
Why the Other Options Are Incorrect:
A. Azure Key Vault
Used to store secrets, certificates, and keys securely, but it does not scan application code.
C. Application Insights in Azure Monitor
Used for application performance monitoring and telemetry, not code vulnerability scanning.
D. Azure DevTest Labs
Provides environments for testing and development, but does not perform security scanning of code.
Reference:
🔗 GitHub Docs: GitHub Advanced Security
You need to recommend a solution to meet the AWS requirements.
What should you include in the recommendation? To answer, select the appropriate
options in the answer area.
NOTE: Each correct selection is worth one point.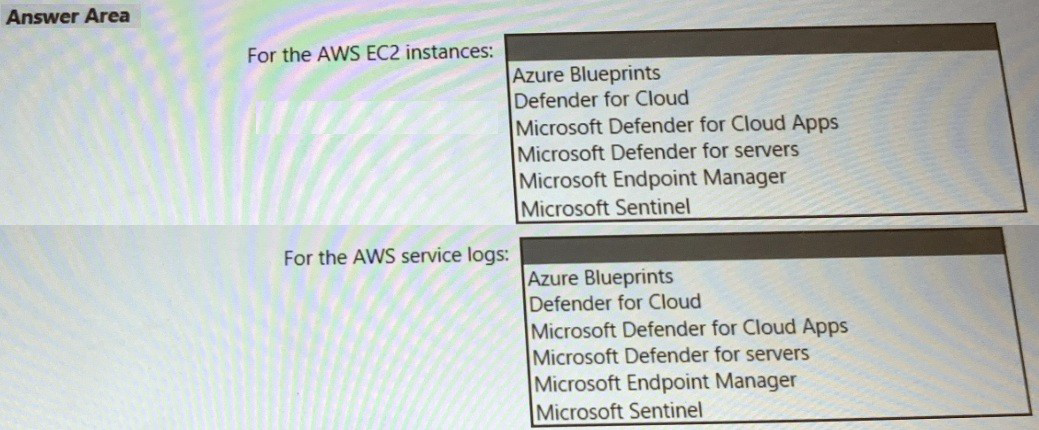
Explanation:
The requirement is to meet AWS security needs, which involves protecting compute resources and collecting logs for a centralized security view.
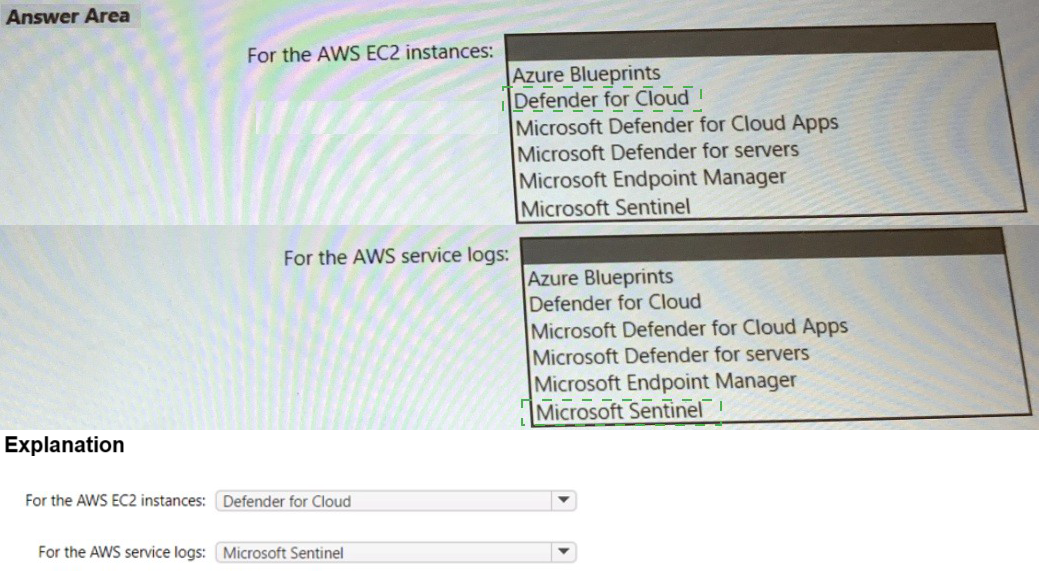
1. For the AWS EC2 instances: Microsoft Defender for servers
Reasoning:
Microsoft Defender for servers (specifically its Plan 2) is the component of Defender for Cloud that provides threat detection and advanced defenses for your Windows and Linux machines, regardless of where they are hosted. This includes:
Vulnerability Assessment:
Scans your EC2 instances for OS and software vulnerabilities.
Just-in-Time (JIT) VM Access:
Allows you to secure management ports on your EC2 instances.
Endpoint Detection and Response (EDR):
Provides advanced behavioral threat detection and investigation capabilities for the servers.
File Integrity Monitoring (FIM):
Monitors changes to critical files and registry keys.
Since EC2 instances are virtual machines, Defender for servers is the direct and correct service to protect them.
2. For the AWS service logs: Microsoft Sentinel
Reasoning:
Microsoft Sentinel is a cloud-native Security Information and Event Management (SIEM) solution. Its primary function is to collect, aggregate, and analyze log data from a wide variety of sources.
It has a built-in data connector for Amazon Web Services that can pull in logs from services like AWS CloudTrail, VPC Flow Logs, and GuardDuty.
Once the logs are in Sentinel, you can use its analytics rules, workbooks, and hunting capabilities to detect threats and investigate incidents across your hybrid cloud environment (Azure and AWS).
Therefore, for collecting and analyzing AWS service logs, Microsoft Sentinel is the correct recommendation.
Why the Other Options Are Incorrect:
Azure Blueprints:
This is an Azure service for deploying and governing environments using reusable artifacts called blueprints. It is not a security monitoring or threat protection tool and is not used for AWS resources.
Defender for Cloud:
While this is the overarching service, the question asks for the specific component. "Defender for servers" is the precise feature set within Defender for Cloud that protects compute instances. Selecting the broader "Defender for Cloud" is less specific than the exact product name provided in the list.
Microsoft Defender for Cloud Apps:
This is a Cloud Access Security Broker (CASB) used to discover and control access to SaaS applications (like Salesforce, Dropbox). It is not the primary tool for securing IaaS virtual machines (EC2) or ingesting raw service logs from AWS.
Microsoft Endpoint Manager (MEM):
This is a unified endpoint management (UEM) platform for managing devices (e.g., Windows 10/11, macOS, iOS, Android). It is not designed to manage server OSes in the cloud or collect cloud platform logs.
Reference:
Microsoft Learn - Microsoft Defender for servers:
Microsoft Learn - Connect AWS to Microsoft Sentinel:
What should you create in Azure AD to meet the Contoso developer requirements?
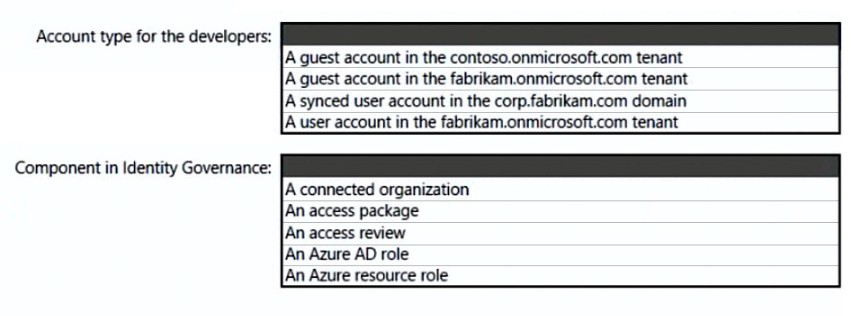
Explanation:
Scenario Analysis:
1.Account type for the developers:
The options include guest accounts in other tenants, synced user accounts, and user accounts in the tenant itself.
Typically, developers in your organization should have a user account in your own tenant so that they can access resources and participate in identity governance workflows.
Therefore, the correct account type is likely:
“A user account in the fabrikam.onmicrosoft.com tenant” (assuming Fabrikam is the Contoso tenant in this context).
2.Component in Identity Governance:
Identity Governance in Azure AD involves components like:
Access packages (for entitlement management, providing access to resources)
Access reviews (to review ongoing access)
Connected organizations (for guest accounts)
Azure AD roles (for role-based access control)
If the goal is to provision access for developers to multiple resources (e.g., apps, groups, or subscriptions) while managing lifecycle and approvals, you should create an access package.
Access packages are specifically designed for automating access requests for internal users and guests in Azure AD.
Recommended Solution:
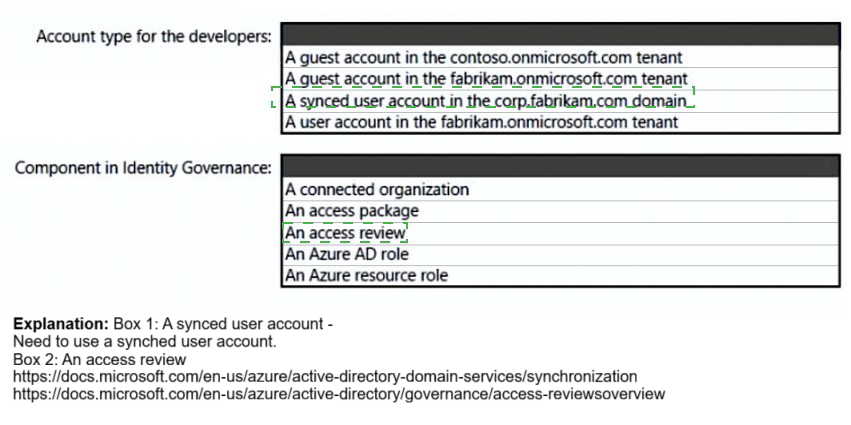
Account type for developers
A user account in the fabrikam.onmicrosoft.com tenant
Component in Identity Governance
An access package
Reference:
🔗 Microsoft Learn: Introduction to Azure AD entitlement management
You need to recommend a solution to meet the requirements for connections to ClaimsDB.
What should you recommend using for each requirement? To answer, select the
appropriate options in the answer area.
NOTE: Each correct selection is worth one point.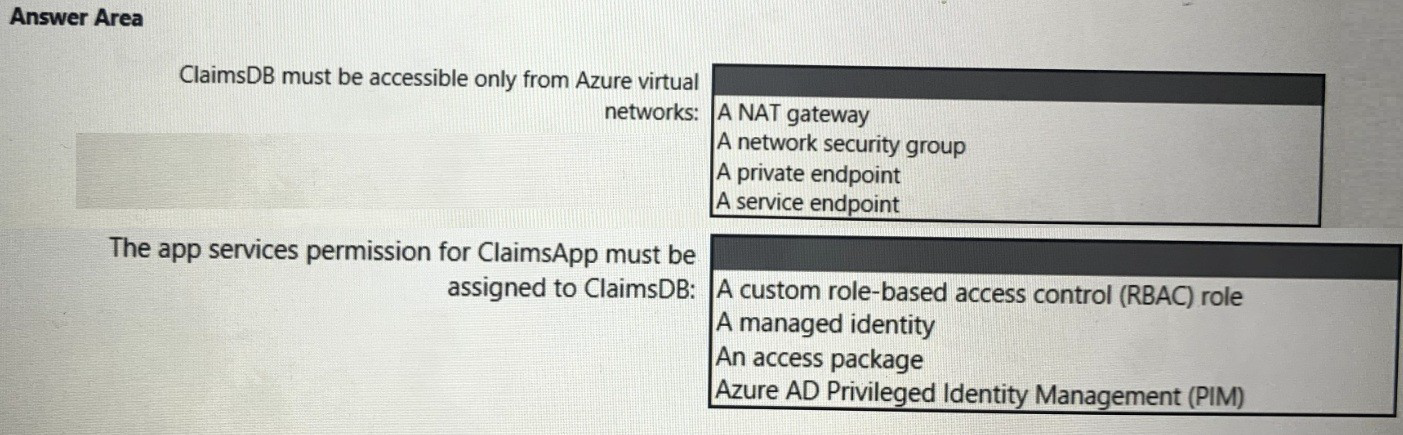
Explanation:
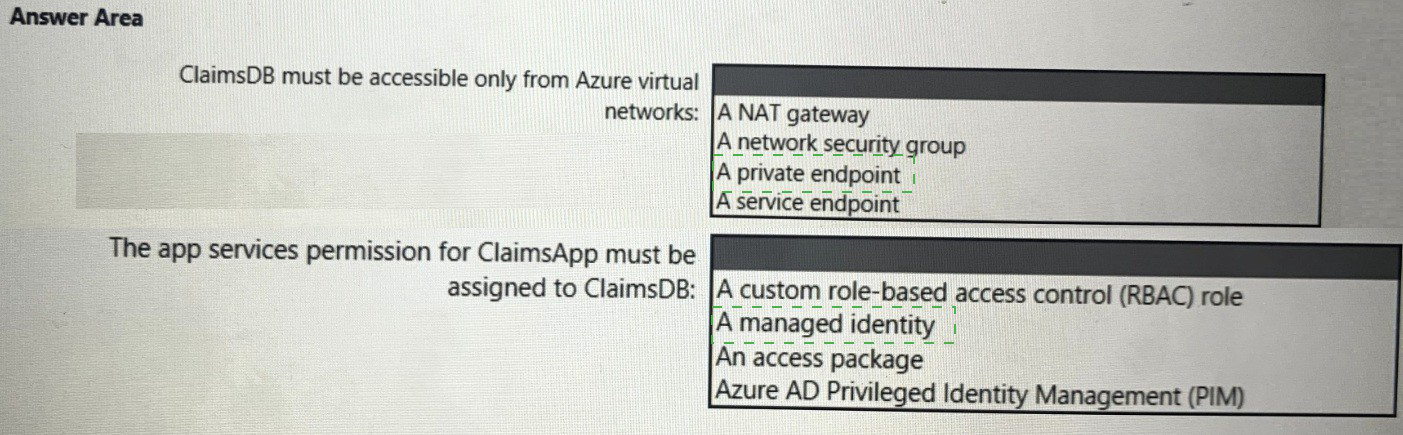
✅ ClaimsDB must be accessible only from Azure virtual networks
Correct answer: Private endpoint
A private endpoint maps a resource (like Azure SQL or storage) to a private IP address within your virtual network.
This ensures exclusive access from Azure VNets, blocking public internet exposure.
It’s the most secure and recommended approach for restricting access to PaaS services like ClaimsDB.
✅ The app services permission for ClaimsApp must be assigned to ClaimsDB
Correct answer: Managed identity
A managed identity allows Azure resources (like App Services) to authenticate securely to other services (like ClaimsDB) without storing credentials.
It supports role-based access control (RBAC) and integrates natively with Azure AD.
This is the best practice for secure, automated identity delegation between services.
📚 References:
Private endpoint overview
Managed identities for Azure resources
You need to recommend a solution to secure the MedicalHistory data in the ClaimsDetail table. The solution must meet the Contoso developer requirements. What should you include in the recommendation?
A. Transparent Data Encryption (TDE)
B. Always Encrypted
C. row-level security (RLS)
D. dynamic data masking
E. data classification
Explanation:
To secure sensitive data like MedicalHistory in the ClaimsDetail table, and meet developer requirements for data confidentiality during query processing, the best solution is Always Encrypted.
Always Encrypted ensures:
Data is encrypted at rest, in transit, and in use.
The SQL Server or Azure SQL Database never sees unencrypted values, protecting against insider threats.
Encryption and decryption happen client-side, using a trusted application with access to encryption keys.
Developers can still query encrypted columns using parameterized queries, preserving functionality.
This is ideal for highly sensitive fields like medical history, financial data, or national IDs.
❌ Why the other options are incorrect:
A. Transparent Data Encryption (TDE):
Encrypts the entire database at rest, but does not protect data in use or in transit, nor does it prevent DBAs from viewing sensitive data.
C. Row-Level Security (RLS):
Controls who can access which rows, but does not encrypt data. It’s an access control mechanism, not a data protection solution.
D. Dynamic Data Masking:
Masks data at query time, but does not encrypt it. It’s useful for obfuscation, not for true security against unauthorized access.
E. Data Classification:
Helps label and track sensitive data, but does not enforce protection. It’s a governance tool, not a security control.
📚 Reference:
Always Encrypted overview
Choose the right data protection method
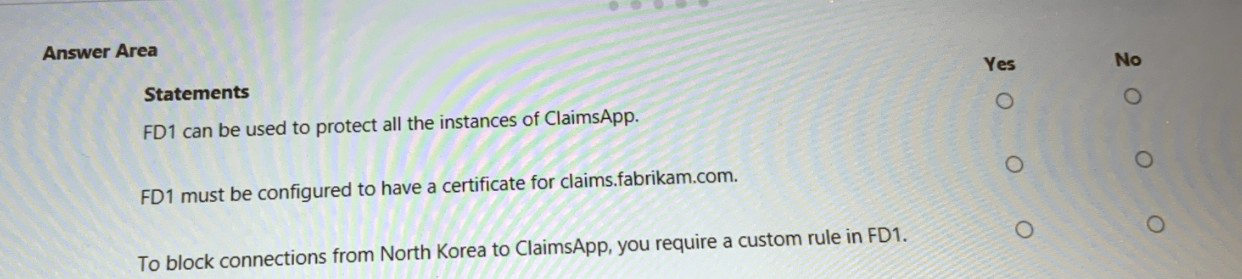
You are evaluating the security of ClaimsApp.
For each of the following statements, select Yes if the statement is true. Otherwise, select
No.
NOTE; Each correct selection is worth one point.
Explanaion:
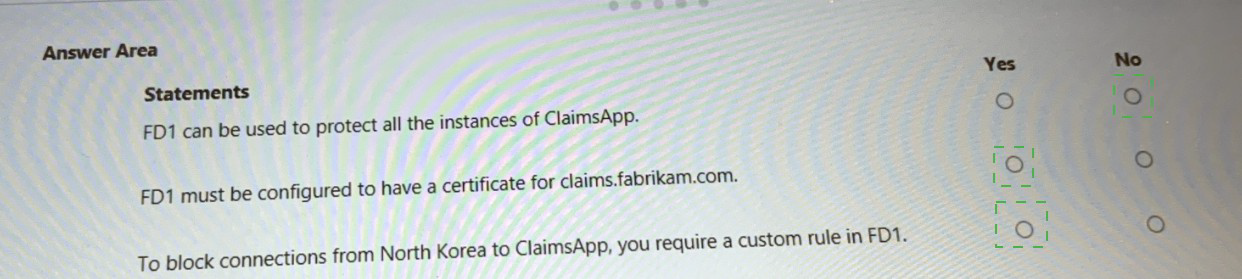
1️⃣ FD1 can be used to protect all the instances of ClaimsApp
✅ Answer: Yes
Azure Front Door (FD1) is a global, scalable entry point that can route and protect traffic to multiple backend instances of ClaimsApp across regions.
It supports Web Application Firewall (WAF), SSL offloading, and DDoS protection, making it suitable for securing all instances.
2️⃣ FD1 must be configured to have a certificate for claims.fabrikam.com
✅ Answer: Yes
To enable HTTPS for custom domains like claims.fabrikam.com, FD1 must be configured with a TLS/SSL certificate for that domain.
This ensures secure communication and meets best practices for public-facing apps.
3️⃣ To block connections from North Korea to ClaimsApp, you require a custom rule in FD1
✅ Answer: Yes
Azure Front Door’s WAF custom rules can be configured to block traffic by country/region using Geo-filtering.
Blocking traffic from North Korea requires a custom WAF rule, as it's not blocked by default.
📚 References:
Azure Front Door overview
Geo-filtering with WAF custom rules
You need to recommend a solution to meet the compliance requirements.
What should you recommend? To answer, select the appropriate options in the answer
area.
NOTE: Each correct selection is worth one point.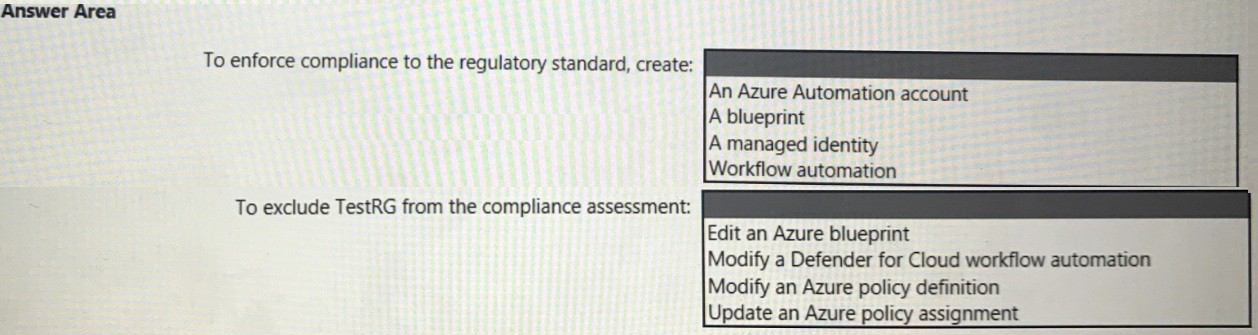
Explanation:
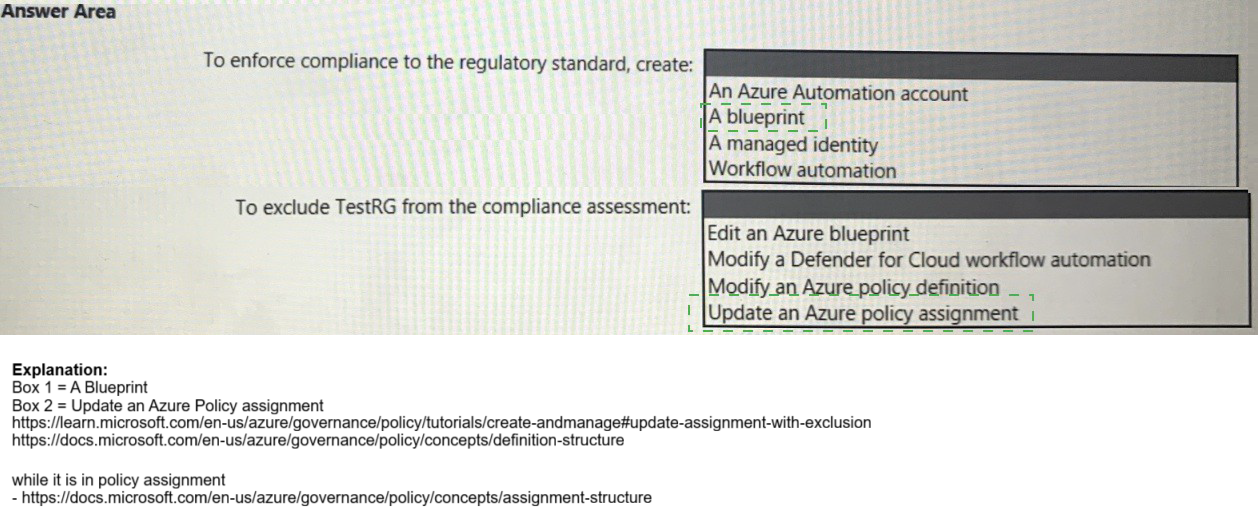
1. To enforce compliance to the regulatory standard, create: A blueprint
Reasoning:
Azure Blueprints is a service specifically designed for large-scale, repeatable deployment of Azure environments that adhere to organizational standards, policies, and compliance requirements (like regulatory standards such as NIST, ISO, CIS).
A blueprint package includes Azure Policy assignments, resource groups, ARM templates, and role assignments.
When you assign a blueprint, it consistently deploys and enforces the entire package, including the policies that check for and enforce compliance. This is the correct tool for "enforcing compliance to a regulatory standard" across your environment in a governed, version-controlled manner.
2. To exclude TestRG from the compliance assessment: Update an Azure policy assignment
Reasoning:
Compliance assessments in Defender for Cloud are driven by Azure Policy. When a policy is assigned, it evaluates resources within its scope.
To exclude a specific resource group (TestRG), you do not modify the policy definition itself, as that would change the rule for everyone.
Instead, you update the policy assignment. When creating or editing an assignment, you can specify exclusions, effectively scoping the assignment to * but NOT TestRG. This is the precise and correct method for excluding a specific resource group from a compliance assessment.
Why the Other Options Are Incorrect:
For "enforce compliance":
An Azure Automation account:
This is used for process automation (runbooks) and managing updates. It is not the primary service for defining and deploying compliance standards.
A managed identity:
This is an identity for an Azure resource to authenticate to other services. It is a supporting component, not the main tool for enforcing compliance.
Workflow automation:
This is a feature in Microsoft Defender for Cloud that automatically triggers Logic Apps in response to specific security alerts or recommendations. It is for reactive automation, not for proactively defining and deploying a compliance standard.
For "exclude TestRG":
Edit an Azure blueprint:
While a blueprint contains policy assignments, you don't "edit a blueprint" to make a quick, targeted exclusion. You would version and republish the entire blueprint, which is an overly heavy process for this simple task. The direct action is to update the policy assignment, which may have been deployed via a blueprint or directly.
Modify a Defender for Cloud workflow automation:
This is for alerting and notification workflows and has nothing to do with scoping policy evaluations for compliance.
Modify an Azure policy definition:
This changes the rule for everyone who uses this definition. If you modified the definition to exclude a certain resource type, it would affect all subscriptions and management groups where it's assigned. This is the wrong approach for excluding a single resource group.
Reference:
Microsoft Learn - What are Azure Blueprints?:
Microsoft Learn - Azure Policy assignment structure: (See the notScopes property for exclusions):
You need to recommend a solution to resolve the virtual machine issue. What should you include in the recommendation? (Choose Two)
A. Onboard the virtual machines to Microsoft Defender for Endpoint.
B. Onboard the virtual machines to Azure Arc.
C. Create a device compliance policy in Microsoft Endpoint Manager.
D. Enable the Qualys scanner in Defender for Cloud.
Explanation:
To resolve security or compliance issues related to virtual machines, especially in hybrid or multi-cloud environments, Microsoft recommends the following two actions:
✅ A. Onboard the virtual machines to Microsoft Defender for Endpoint
This enables endpoint detection and response (EDR), threat protection, and attack surface reduction.
Defender for Endpoint integrates with Defender for Cloud to provide advanced threat detection on VMs.
It's essential for real-time monitoring, behavioral analytics, and automated investigation/remediation.
✅ D. Enable the Qualys scanner in Defender for Cloud
Defender for Cloud uses Qualys for vulnerability scanning of virtual machines.
This helps identify missing patches, misconfigurations, and known CVEs.
It’s a foundational step for secure score improvement and compliance posture.
❌ Why the other options are incorrect:
B. Azure Arc:
Useful for managing non-Azure VMs, but not a direct solution to resolve VM security issues. It’s an enabler, not a security control.
C. Microsoft Endpoint Manager compliance policy:
Applies to user devices (e.g., laptops, mobiles), not virtual machines. It’s part of Intune, not Defender for Cloud or VM security.
📚 References:
Microsoft Defender for Endpoint onboarding
Enable Qualys vulnerability assessment in Defender for Cloud
You need to recommend a solution to meet the security requirements for the virtual machines. What should you include in the recommendation?
A. an Azure Bastion host
B. a network security group (NSG)
C. just-in-time (JIT) VM access
D. Azure Virtual Desktop
Explanation:
To secure virtual machines (VMs) in an Azure subscription, just-in-time (JIT) VM access, a feature of Microsoft Defender for Cloud, is the most effective solution to meet security requirements, particularly those aligned with the Azure Security Benchmark (ASB) V3 (NS-2: Secure management ports). JIT reduces the attack surface by keeping management ports (e.g., RDP 3389, SSH 22) closed by default and opening them only for authorized users, from trusted IPs, for a limited time. This aligns with Zero Trust principles, ensuring least-privilege access and minimizing exposure to brute-force or unauthorized access attempts, which are common threats to VMs. JIT integrates with network security groups (NSGs) or Azure Firewall to dynamically modify access rules, logs all requests for auditing, and supports compliance with standards like HIPAA or PCI DSS, making it a core focus of the SC-100 exam’s infrastructure security domain.
How JIT Works:
In Microsoft Defender for Cloud, administrators enable JIT for VMs, specifying allowed ports, protocols, source IPs, and access duration (e.g., 3 hours). When a user requests access via the Azure portal or API, JIT verifies identity (optionally with Azure AD MFA), modifies NSG/Firewall rules to allow temporary access, and reverts rules post-session. This ensures management ports are not persistently exposed, directly addressing ASB V3’s requirement to secure management ports. For example, a VM’s RDP port remains blocked until a developer requests access, reducing the risk of external attacks.
Implementation Steps:
Enable Defender for Cloud (Standard tier required for JIT).
Navigate to Workload protections > Just-in-time VM access in the Defender portal.
Select VMs, configure JIT policies (e.g., allow port 3389 from specific IPs for 4 hours).
Monitor access logs in Defender for Cloud for compliance and auditing.
This approach is proactive, auditable, and minimizes manual configuration, making it ideal for securing VMs hosting sensitive workloads.
Why Other Options Are Not Correct:
A. Azure Bastion:
Bastion provides secure RDP/SSH access via a browser or native client without public IPs, reducing exposure. However, it’s a connectivity solution, not an access control mechanism like JIT. It doesn’t dynamically manage port access or enforce time-bound restrictions, failing to fully address ASB V3’s NS-2 control. Bastion complements JIT but isn’t the primary solution.
B. Network Security Group (NSG):
NSGs filter traffic using rules (e.g., deny RDP from 0.0.0.0/0). While useful, NSGs require manual or scripted updates to manage access dynamically, lacking JIT’s automated, auditable workflow and identity integration. NSGs are often used with JIT but alone are insufficient.
D. Azure Virtual Desktop (AVD):
AVD delivers virtualized desktops and apps for end-users, not infrastructure-level VM security. It’s irrelevant to securing management ports or controlling admin access to VMs, making it unsuitable.
Why JIT Is Best:
JIT directly addresses the ASB V3 NS-2 control by ensuring management ports are closed by default, only opened on verified request, and monitored for compliance. It reduces administrative overhead compared to manual NSG updates, integrates with Azure AD for identity security, and supports auditing, which is critical for regulated environments. Combining JIT with NSGs or Bastion can enhance security, but JIT is the primary control for dynamic, secure VM access.
References
Microsoft Docs: Just-in-time VM access – Explains JIT configuration and benefits for VM security.
Microsoft Docs: ASB V3 – NS-2: Secure management ports – Outlines JIT as a key control.
Microsoft Learn: SC-100 Study Guide – Infrastructure security – Covers JIT for VM protection.
Microsoft Docs: Azure Bastion overview – Clarifies Bastion’s role vs. JIT.
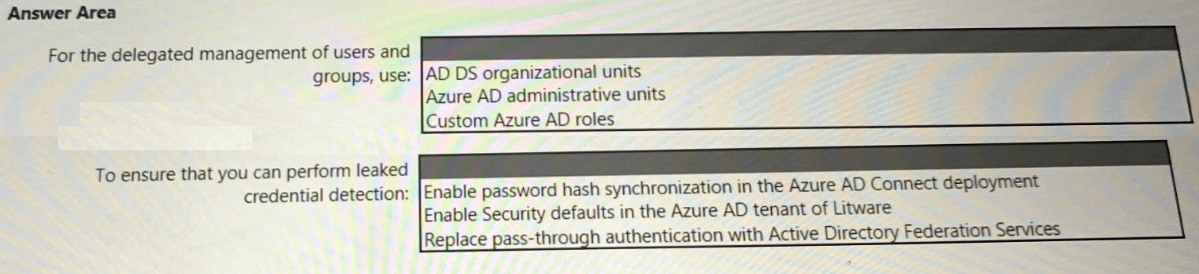
You need to recommend an identity security solution for the Azure AD tenant of Litware.
The solution must meet the identity requirements and the regulatory compliance
requirements.
What should you recommend? To answer, select the appropriate options in the answer
area.
NOTE: Each correct selection is worth one point.
Explanation:
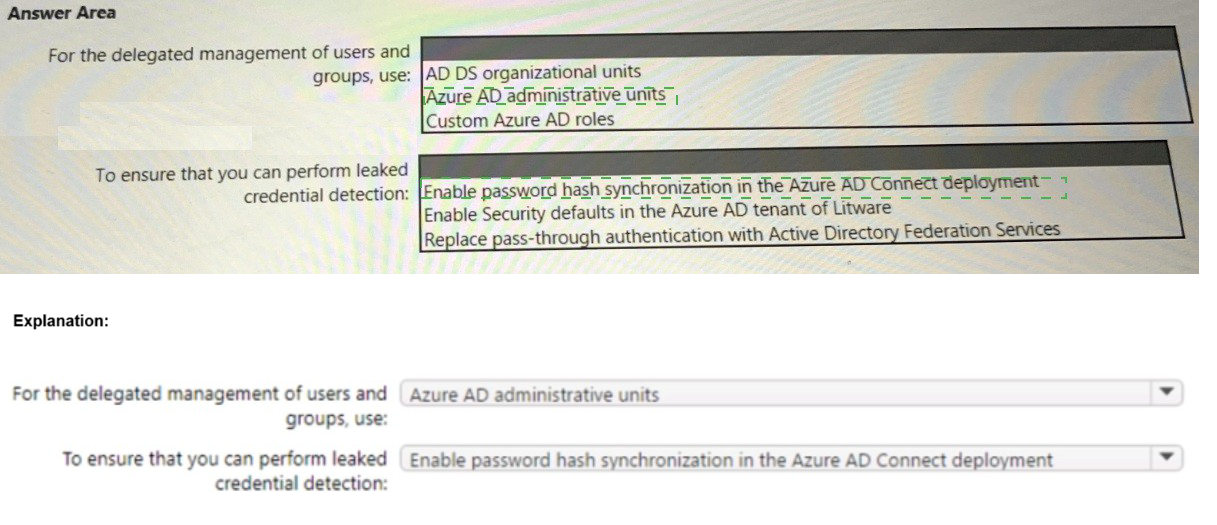
1. For the delegated management of users and groups, use: Azure AD administrative units
Reasoning:
This requirement is about delegating administrative permissions for a subset of users, which is a common need for large organizations or those with regulatory requirements for data locality/segregation.
Azure AD Administrative Units (AUs) are containers that allow you to segment your Azure AD users and groups. You can then assign a role (like User Administrator or Helpdesk Administrator) that is scoped only to a specific Administrative Unit. This allows, for example, a regional IT admin to manage users only in their region, without having global permissions.
The other options are incorrect:
AD DS organizational units:
This is for on-premises Active Directory and does not apply to delegating management within an Azure AD tenant.
Custom Azure AD roles:
While you can create custom roles, they are for defining custom permissions, not for scoping administration to a specific group of users. You would use a custom role in combination with an Administrative Unit to achieve granular delegation.
2. To ensure that you can perform leaked credential detection:
Enable password hash synchronization in the Azure AD Connect deployment
Reasoning:
Leaked credential detection is a critical feature of Azure AD Identity Protection. This service works by comparing user sign-in credentials (hashes of passwords) against a continuously updated database of known leaked credentials.
For this comparison to happen, Azure AD needs access to the password hash. Password Hash Synchronization in Azure AD Connect synchronizes a hash of the user's on-premises AD password hash to Azure AD. This is a prerequisite for leaked credential detection to function.
The other options are incorrect:
Enable Security defaults:
This enables basic security settings like requiring MFA for admins and blocking legacy authentication. It does not, by itself, enable the advanced machine learning-based leaked credential detection service.
Replace pass-through authentication with Active Directory Federation Services (AD FS): With AD FS, passwords remain on-premises and are not hashed in Azure AD. Therefore, Azure AD Identity Protection cannot perform leaked credential detection in this configuration. Enabling Password Hash Sync is actually recommended even with AD FS precisely to enable these features.
Reference:
Microsoft Learn - Administrative units in Azure Active Directory:
Microsoft Learn - What is password hash synchronization?: This document explains that PHS is required for leaked credential detection.
You need to recommend a solution for securing the landing zones. The solution must meet the landing zone requirements and the business requirements. What should you configure for each landing zone?
A. Azure DDoS Protection Standard
B. an Azure Private DNS zone
C. Microsoft Defender for Cloud
D. an ExpressRoute gateway
Explanation:
The primary purpose of a landing zone is to establish a secure, scalable, and well-governed foundation for hosting workloads in Azure. Microsoft Defender for Cloud is the central, Azure-native service for Cloud Security Posture Management (CSPM) and Cloud Workload Protection Platform (CWPP). It is a non-negotiable component for any production-grade landing zone because it provides continuous security assessment, compliance monitoring, and threat protection across all deployed resources from the moment they are created.
How it Meets the Requirements:
It directly fulfills the implied "landing zone requirements" for a secure baseline by providing a secure score, regulatory compliance dashboards (e.g., for NIST, ISO), and actionable recommendations to harden configurations (e.g., enabling encryption, enforcing network security rules). It meets "business requirements" by unifying security management, reducing business risk, and helping to demonstrate due diligence for compliance.
Why the Other Options Are Incorrect:
A. Azure DDoS Protection Standard:
This is a specific, high-value service for protecting public endpoints from volumetric attacks. However, it is not a foundational requirement for every landing zone. A landing zone hosting only internal, private APIs or backend services with no public IPs would not require it. It is a targeted control, not the ubiquitous security posture tool that Defender for Cloud is.
B. an Azure Private DNS Zone:
This is a core networking component for managing custom domain name resolution within a virtual network. While critical for many architectures for service discovery, it is a design choice for network architecture, not a primary security control that defines the security posture of the landing zone itself.
D. an ExpressRoute Gateway:
This component is used to connect an Azure virtual network to an on-premises network via a private ExpressRoute circuit. Its necessity is purely dependent on a specific hybrid connectivity requirement. A fully cloud-native landing zone with no on-premises dependencies would not need this gateway. It is a connectivity solution, not a security foundational service.
Reference:
Microsoft Learn - Introduction to Microsoft Defender for Cloud:
This document establishes Defender for Cloud as the central platform for security posture management and threat protection.
Microsoft Cloud Adoption Framework - Azure landing zone security governance:
This guidance explicitly positions security services like Defender for Cloud as a foundational element of a secure landing zone.
| Page 1 out of 15 Pages |