What are two core values of the Palo Alto Network Security Operating Platform? (Choose two.}
A. prevention of cyber attacks
B. safe enablement of all applications
C. threat remediation
D. defense against threats with static security solution
A packet that is already associated with a current session arrives at the firewall. What is the flow of the packet after the firewall determines that it is matched with an existing session?
A. it is sent through the fast path because session establishment is not required. If subject to content inspection, it will pass through a single stream-based content inspection engine before egress.
B. It is sent through the slow path for further inspection. If subject to content inspection, it will pass through a single stream-based content inspection engines before egress
C. It is sent through the fast path because session establishment is not required. If subject to content inspection, it will pass through multiple content inspection engines before egress
D. It is sent through the slow path for further inspection. If subject to content inspection, it will pass through multiple content inspection engines before egress
What are three key benefits of the Palo Alto Networks platform approach to security? (Choose three)
A. operational efficiencies due to reduction in manual incident review and decrease in mean time to resolution (MTTR)
B. improved revenue due to more efficient network traffic throughput
C. Increased security due to scalable cloud delivered security Services (CDSS)
D. Cost savings due to reduction in IT management effort and device
The need for a file proxy solution, virus and spyware scanner, a vulnerability scanner, and HTTP decoder for URL filtering is handled by which component in the NGFW?
A. First Packet Processor
B. Stream-based Signature Engine
C. SIA (Scan It All) Processing Engine
D. Security Processing Engine
What is the recommended way to ensure that firewalls have the most current set of signatures for up-to-date protection?
A. Run a Perl script to regularly check for updates and alert when one is released
B. Monitor update announcements and manually push updates to Crewall
C. Store updates on an intermediary server and point all the firewalls to it
D. Use dynamic updates with the most aggressive schedule required by business needs
Which selection must be configured on PAN-OS External Dynamic Lists to support MineMeld indicators?
A. Prototype
B. Inputs
C. Class
D. Feed Base URL
A company has deployed the following
• VM-300 firewalls in AWS
• endpoint protection with the Traps Management Service
• a Panorama M-200 for managing its VM-Series firewalls
• PA-5220s for its internet perimeter,
• Prisma SaaS for SaaS security.
Which two products can send logs to the Cortex Data Lake? (Choose two).
A. Prisma SaaS
B. Traps Management Service
C. VM-300 firewalls
D. Panorama M-200 appliance
Which three of the following actions must be taken to enable Credential Phishing Prevention? (Choose three.)
A. Enable User Credential Detection
B. Enable User-ID
C. Define a Secure Sockets Layer (SSL) decryption rule base
D. Enable App-ID
E. Define a uniform resource locator (URL) Filtering profile
Which two methods are used to check for Corporate Credential Submissions? (Choose two.)
A. doman credentialiter
B. User-ID credential check
C. LDAP query
D. IP user mapping
A customer has business-critical applications that rely on the general web-browsing application. Which security profile can help prevent drive-by-downloads while still allowing web-browsing traffic?
A. File Blocking Profile
B. DoS Protection Profile
C. URL Filtering Profile
D. Vulnerability Protection Profile
WildFire machine learning (ML) for portable executable (PE) files is enabled in the antivirus profile and added to the appropriate firewall rules in the profile. In the Palo Alto Networks WildFire test av file, an attempt to download the test file is allowed through. Which command returns a valid result to verify the ML is working from the command line.
A. show wfml cloud-status
B. show mlav cloud-status
C. show ml cloud-status
D. show av cloud-status
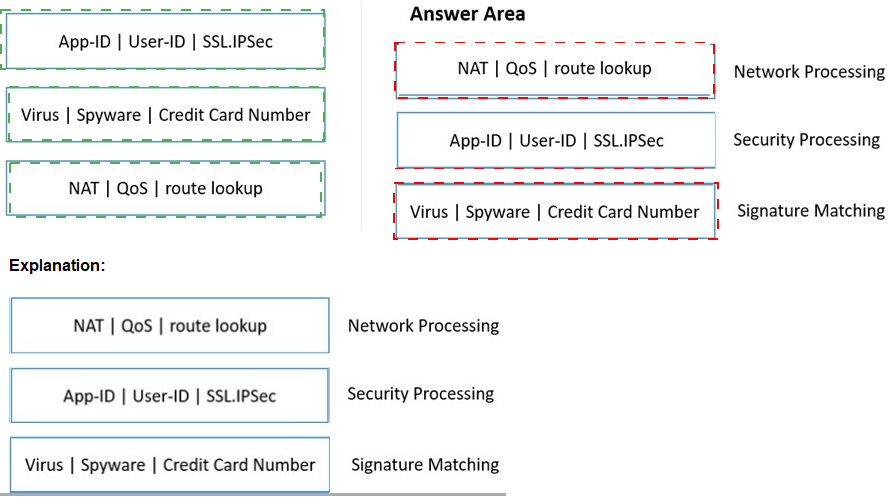
Match the functions to the appropriate processing engine within the dataplane.
| Page 3 out of 12 Pages |
| Previous |