Given the following velocity chart:
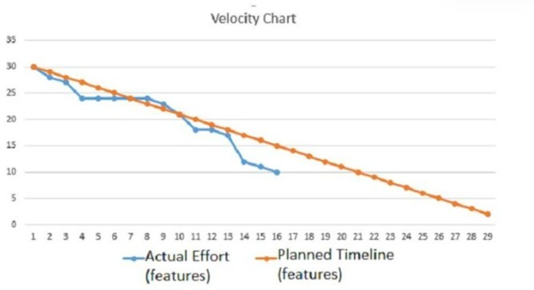
Which of the following updates on the project status should the Scrum master provide to the senior management team?
A. The project utilized all of its available reserve.
B. The project has scope creep.
C. The project deviated from the critical path.
D. The project is trending ahead of schedule.
Hackers are attempting to extract large amounts of data to sell on the dark web. Which of the following steps should a project manager take next to mitigate this risk?
A. Update the issue log.
B. Apply the contingency plan.
C. Transfer the risk.
D. Submit a change request.
A critical business initiative introduced new processes and technology to the organization. Which of the following approaches should be used to ensure the deliverables are increasingly adopted and leveraged by the organization over time?
A. Creation of a social news forum
B. Management directives to use the new system
C. New user kickoff meeting
D. Monthly feedback and training sessions
Explanation: Monthly feedback and training sessions are the best approach to ensure that the deliverables of a critical business initiative are increasingly adopted and leveraged by the organization over time. Feedback and training sessions are communication and learning activities that provide information and guidance on how to use and benefit from the new processes and technology introduced by the initiative. Feedback and training sessions can help to increase awareness, understanding, acceptance, and adoption of the deliverables among the organization’s employees and stakeholders. They can also help to identify and address any issues or challenges that may arise during the implementation and transition phases.
During a complex, multiyear project, a PM must discern which project tasks overlap so resources can be allocated appropriately. Which of the following is best for determining this information?
A. PERT chart
B. Milestone chart
C. Gantt chart
D. Budget burndown chart
Government projects require that personnel submit to background screenings for certain clearance requirements. Which of the following best describes this process?
A. Data security
B. Operational security
C. Physical security
D. Digital security
Explanation: Operational security is the process of identifying, protecting, and controlling sensitive information and activities from unauthorized access or disclosure. Operational security includes background screenings for personnel who need to access classified or restricted information or resources, as well as implementing policies and procedures to prevent leaks, breaches, or espionage. Operational security is essential for government projects that involve national security, defense, intelligence, or law enforcement. Operational security is different from data security, which is the process of safeguarding data from unauthorized access, use, modification, or destruction. Data security includes encryption, authentication, authorization, backup, and recovery of data. Operational security is also different from physical security, which is the process of securing physical assets, such as equipment, data, or personnel, from unauthorized access or damage. Physical security includes locks, alarms, cameras, guards, and fences. Operational security is also different from digital security, which is the process of protecting digital devices, networks, and systems from cyberattacks, malware, or hacking. Digital security includes firewalls, antivirus, VPN, and passwords.
A project manager has received different functional requests from three individual stakeholders. The project manager is able to have all parties concede somewhat in order to find a reasonable solution. Which of the following outcomes would most likely occur?
A. Too much time might be spent generating project delays.
B. The project manager might be seen as weak.
C. The number of change requests throughout the project might be reduced.
D. Some stakeholders might not be completely satisfied.
Explanation: When a project manager achieves a compromise, it often means that stakeholders may not be entirely satisfied with the outcome. However, compromise is sometimes necessary to balance differing needs, consistent with CompTIA Project+ principles on stakeholder management and negotiation.
During a stand-up meeting, a team member asks to include a change that an important stakeholder requested in the project board. This request is denied, and the team member has to go back to what was originally planned for the sprint. Which of the following individuals should the stakeholder have asked to request the change instead of the team member?
A. Architect
B. Project sponsor
C. Scrum master
D. Product owner
Explanation: The product owner is the person who is responsible for managing the product backlog, which includes adding, removing, or changing items based on stakeholder feedback and business value. The product owner is also the one who can collaborate with the development team and the scrum master to decide if a change can be accommodated in the current sprint or deferred to a future sprint. Therefore, the stakeholder should have asked the product owner to request the change instead of the team member, who is not authorized to make changes to the sprint backlog12.
A PM wants to add a chart to the monthly status report to show major accomplishments for key events. Which of the following is the best chart to use?
A. Milestone
B. Gantt
C. Burndown
D. PERT
A sponsor prefers to communicate with the team using email, phone calls, conversations in the hallway, and impromptu meetings. Which of the following types of communication is the sponsor using?
A. Informal communication
B. Formal communication
C. Synchronous communication
D. Asynchronous communication
Explanation: Informal communication is a type of communication that is casual, spontaneous, and unstructured. It does not follow any predefined rules, protocols, or formats. Examples of informal communication include email, phone calls, conversations in the hallway, and impromptu meetings12. The sponsor is using informal communication to communicate with the team, as these methods are convenient, flexible, and personal. However, informal communication may also have some drawbacks, such as lack of documentation, inconsistency, and potential for misunderstanding3. Therefore, the sponsor should also use formal communication when necessary, such as for official reports, contracts, and presentations4.
Which of the following software programs would be best to use to store information related to business transactions?
A. Record management system
B. Customer relationship management
C. Enterprise resource planning
D. Content management system
Explanation: Enterprise resource planning (ERP) software is a type of software that integrates various business functions and processes, such as accounting, finance, inventory, sales, purchasing, human resources, and more. ERP software helps businesses store, organize, and manage information related to business transactions, such as invoices, payments, orders, receipts, and reports. ERP software also provides real-time data analysis, reporting, and forecasting capabilities12.
Which of the following activities would a project manager perform during the closing phase? (Select THREE).
A. Lessons learned
B. Risk analysis
C. Removing resources
D. Acquiring resources
E. Statement of work sign-off
F. Stakeholder analysis
G. Removing access
Explanation: Lessons learned, removing resources, and removing access are activities that a project manager would perform during the closing phase of a project. Lessons learned is a process of collecting and documenting the knowledge and experience gained from a project for future reference and improvement. Removing resources is a process of releasing or reallocating any human or material resources that were used for the project. Removing access is a process of revoking any permissions or privileges that were granted to the project team members or stakeholders for accessing any systems or data related to the project. These activities can help to finalize and close a project successfully and ensure that all deliverables are transferred, all documentation is approved and archived, all contracts are closed, and all stakeholders are satisfied.
A project manager is eager to define access requirements during the initiation phase of a project. Which of the following steps should the project manager perform first?
A. Define the WBS.
B. Develop a RAM.
C. Manage the vendors.
D. Assess the resource pool.
| Page 9 out of 31 Pages |
| Previous |