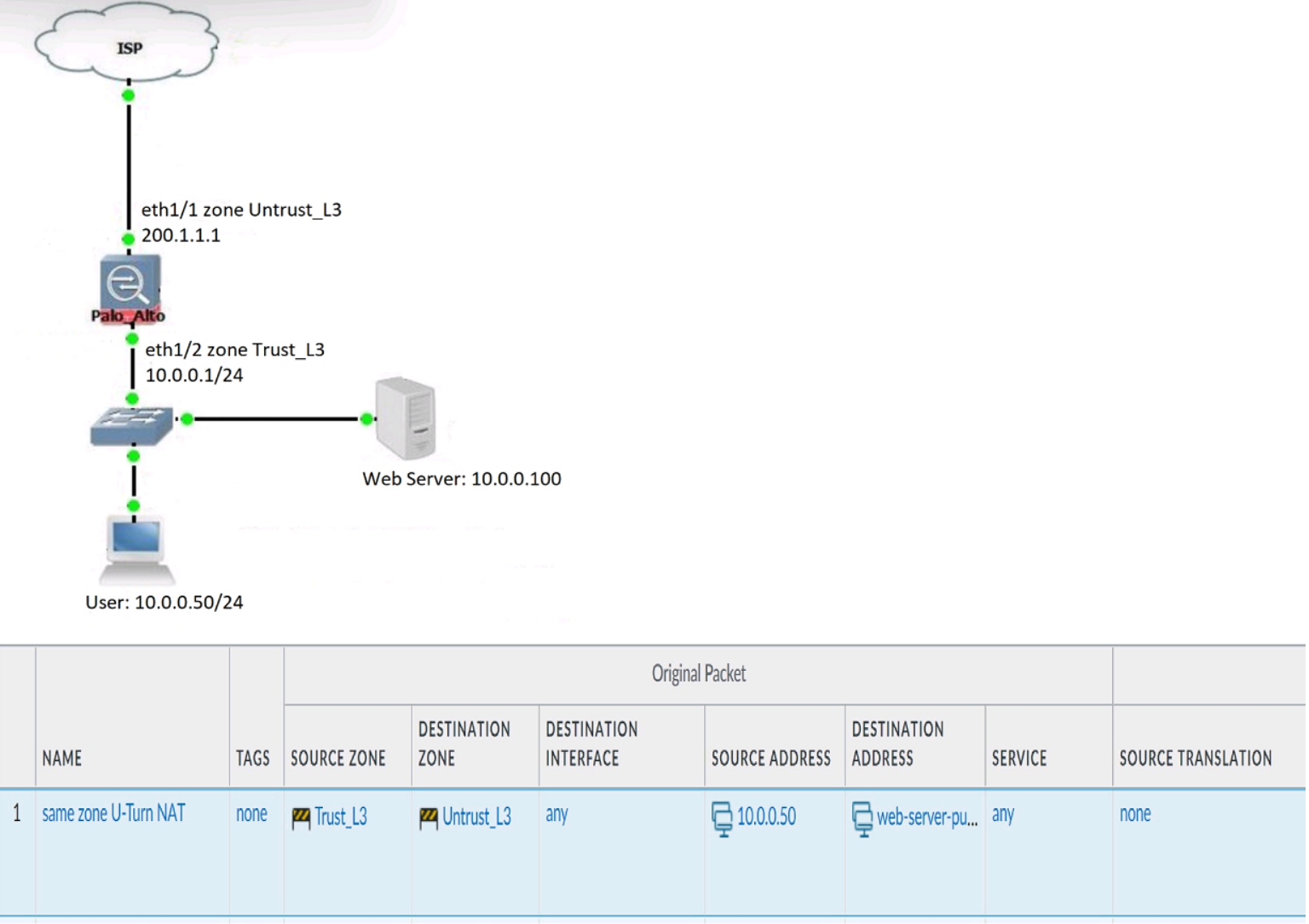
Review the information below. A firewall engineer creates a U-NAT rule to allow users in
the trust zone access to a server in the same zone by using an external,
public NAT IP for that server.
Given the rule below, what change should be made to make sure the NAT works as
expected?
A. Change destination NAT zone to Trust_L3.
B. Change destination translation to Dynamic IP (with session distribution) using firewall ethI/2 address.
C. Change Source NAT zone to Untrust_L3.
D. Add source Translation to translate original source IP to the firewall eth1/2 interface translation.
Explanation:
This is a classic U-Turn NAT scenario, where internal users access an internal server using its public IP address. For this to work correctly, the NAT rule must reflect that both source and destination traffic are in the same zone — in this case, Trust_L3.
Why A is Correct:
The destination zone in the NAT rule must match the zone of the translated IP (i.e., the internal server).
Since the public IP is translated to 10.0.0.100, which resides in Trust_L3, the destination zone must be Trust_L3.
If you leave it as Untrust_L3, the firewall won’t match the NAT rule correctly, and the traffic will fail.
📚 Reference:
Palo Alto Networks – U-Turn NAT Configuration
❌ Why Other Options Are Wrong:
B. Dynamic IP translation:
Not relevant — this is a destination NAT scenario, not source NAT.
C. Source NAT zone to Untrust_L3:
Incorrect — the source zone is Trust_L3 and should remain so.
D. Add source translation:
Not required for U-Turn NAT unless there's a specific need to mask internal IPs.
A firewall engineer is configuring quality of service (OoS) policy for the IP address of a specific server in an effort to limit the bandwidth consumed by frequent downloads of large files from the internet. Which combination of pre-NAT and / or post-NAT information should be used in the QoS rule?
A. Post-NAT source IP address Pre-NAT source zone
B. Post-NAT source IP address Post-NAT source zone
C. Pre-NAT source IP address Post-NAT source zone
D. Pre-NAT source IP address Pre-NAT source zone
Explanation:
QoS rules are evaluated before NAT is applied (similar to security policies).
This means:
You must use the original (pre-NAT) IP address of the server.
You must also use the pre-NAT zone (the ingress zone where the traffic arrives).
Why pre-NAT?
NAT happens later in the processing sequence (after policy lookup).
QoS, like security rules, must decide based on the original values (source/destination IP + zones) before NAT rewrites them.
Why the other options are incorrect:
A. Post-NAT source IP + Pre-NAT zone ❌
Mixing pre- and post-NAT info doesn’t work.
B. Post-NAT source IP + Post-NAT source zone ❌
Incorrect because QoS doesn’t use post-NAT information for rule matching.
C. Pre-NAT source IP + Post-NAT source zone ❌
Again mixing pre- and post-NAT fields. Invalid.
D. Pre-NAT source IP + Pre-NAT source zone ✅
Correct, because QoS policy rules use pre-NAT source/destination addresses and zones.
Reference:
Palo Alto Networks TechDocs: QoS Policy Rules
PAN KB: Understanding Pre-NAT vs Post-NAT Policy Matching
A company configures its WildFire analysis profile to forward any file type to the WildFire public cloud. A company employee receives an email containing an unknown link that downloads a malicious Portable Executable (PE) file. What does Advanced WildFire do when the link is clicked?
A. Performs malicious content analysis on the linked page, but not the corresponding PE file.
B. Performs malicious content analysis on the linked page and the corresponding PE file.
C. Does not perform malicious content analysis on either the linked page or the corresponding PE file.
D. Does not perform malicious content analysis on the linked page, but performs it on the corresponding PE file.
Explanation:
Advanced WildFire provides multi-stage analysis for both web content and downloaded files. When a user clicks a suspicious link, WildFire can:
Analyze the linked page for:
Embedded scripts
Redirects
Exploit kits
Malicious behaviors
Analyze the downloaded file (in this case, a Portable Executable) for:
Behavioral indicators in a sandbox
Static and dynamic analysis
Malware signatures
Because the WildFire profile is configured to forward any file type, and the firewall detects both the URL and the downloaded PE file, both are submitted for analysis.
📚 Reference:
Palo Alto Networks – WildFire Analysis Workflow
❌ Why Other Options Are Wrong:
A. Incorrect — WildFire does analyze the PE file.
C. Incorrect — WildFire analyzes both components if properly configured.
D. Incorrect — WildFire does analyze the linked page if it’s suspicious.
Four configuration choices are listed, and each could be used to block access to a specific URL. If you configured each choice to block the same URL, then which choice would be evaluated last in the processing order to block access to the URL?
A. Custom URL category in URL Filtering profile
B. EDL in URL Filtering profile
C. PAN-DB URL category in URL Filtering profile
D. Custom URL category in Security policy rule
Explanation:
To determine the processing order, you must understand the hierarchy of policy enforcement on a Palo Alto Networks firewall. The system evaluates different components in a strict sequence, and a traffic flow must pass through all of them to be allowed.
The relevant order for this question is:
URL Filtering Profile (PAN-DB & EDL): The firewall first checks the URL against the URL Filtering profile attached to the matching Security policy. Within the profile, it evaluates the URL against its configured settings in a specific internal order.
Security Policy Rule (Custom URL Category): Only after the traffic has been evaluated and allowed by the URL Filtering profile does it proceed to be evaluated by the Security policy rule again for the final permit/deny decision. The custom URL category applied directly to the Security policy rule is part of this final check.
Let's break down why D is evaluated last:
A, B. and C are all components of a URL Filtering Profile. The firewall processes the URL Filtering profile as a single step. It checks the requested URL against the PAN-DB category (C), any External Dynamic Lists (EDLs) (B), and any custom URL categories (A) defined within that profile. The result of this entire profile evaluation (allow, block, alert, continue) is determined here. If the profile is set to block based on any of these three internal components (A, B, or C), the traffic is dropped immediately and never reaches the final Security Policy rule evaluation.
D .is part of the Security Policy Rule. A custom URL category can be added as a matching criterion directly in a Security policy rule. For the firewall to even consider this criterion, the traffic must have first been allowed by the URL Filtering profile. If the traffic was not blocked by the profile, it then moves to the final step: the Security policy rule check. Here, if the URL matches the custom category and the rule's action is set to deny, it will be blocked at this final stage.
Therefore, a block action triggered by a custom URL category in the Security policy rule (D) occurs after the traffic has successfully passed through (was allowed by) the URL Filtering profile.
Detailed Analysis of the Processing Order:
URL Filtering Profile Evaluation: The URL is checked.
Is it in a PAN-DB category set to block? (C) -> Blocked HERE.
Is it on an EDL set to block? (B) -> Blocked HERE.
Is it in a custom category within the profile set to block? (A) -> Blocked HERE.
If none of the above trigger a block, the profile allows the traffic to continue to the next step.
Security Policy Rule Evaluation: The traffic, now allowed by the URL Filtering profile, is evaluated against the Security policy rule.
Does the URL match the custom URL category defined in this rule? (D)
If yes, and the action is deny -> Blocked HERE (LAST).
PCNSE Exam Reference & Key Takeaway:
Core Concept: Policy Evaluation Order. A key mantra is "Profiles before Policy." Security profiles (URL Filtering, Vulnerability, Anti-Virus, etc.) are evaluated before the final allow/deny action of the Security policy rule is executed.
Troubleshooting: If a URL is being blocked and you can't figure out why, check the Traffic logs. The logs will clearly show the distinct phases:
A log-end reason of "url-block" indicates it was blocked by the URL Filtering profile (A, B, or C).
A log-end reason of "deny" indicates it was matched and blocked by the Security policy rule itself (D).
Use Case:
Placing a block in the Security policy (D) is useful for creating very explicit, high-priority deny rules that you want to be visible directly in the policy list. However, most URL blocking is efficiently handled within the URL Filtering profile.
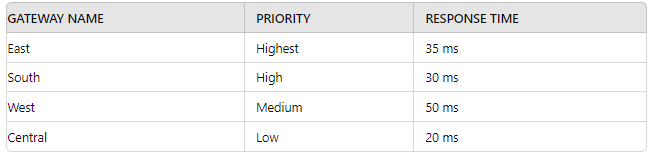
A security engineer has configured a GlobalProtect portal agent with four gateways Which
GlobalProtect Gateway will users connect to based on the chart provided?
A. South
B. West
C. East
D. Central
Explanation:
In a Palo Alto Networks GlobalProtect deployment, the portal agent determines which gateway users connect to based on a combination of priority and response time, following a specific selection process. The chart provides details for four gateways: East (Highest priority, 35 ms response time), South (High priority, 30 ms response time), West (Medium priority, 50 ms response time), and Central (Low priority, 20 ms response time). GlobalProtect uses a two-step selection process: it first considers the priority assigned to each gateway, and if multiple gateways share the same priority, it then evaluates the response time (lowest is preferred). The Palo Alto Networks PAN-OS 11.1 Administrator’s Guide outlines that the gateway with the highest priority is selected, and in case of a tie, the one with the lowest response time wins.
Priority Evaluation:
The East gateway has the Highest priority, which takes precedence over South (High), West (Medium), and Central (Low). Since no other gateway matches the Highest priority, East is the initial candidate.
Response Time Consideration: Although response time is a tiebreaker when priorities are equal, it is irrelevant here because East’s priority is uniquely the highest. However, for completeness, East’s 35 ms is reasonable compared to others, but priority alone suffices.
Why Other Options Are Incorrect:
A. South: With a High priority and 30 ms response time, South is outranked by East’s Highest priority. Response time (30 ms) is better than East’s 35 ms, but priority trumps it.
B. West: Medium priority and 50 ms response time place West lower than East in both priority and response time, making it an unlikely choice.
D. Central: Low priority and 20 ms response time (the best response time) are insufficient due to the lowest priority ranking, which overrides the response time advantage.
GlobalProtect Gateway Selection Process:
The portal agent queries all configured gateways.
It ranks them by priority (Highest > High > Medium > Low).
If priorities tie, it selects the gateway with the lowest response time.
The agent connects to the top-ranked gateway unless it’s unreachable, then falls back to the next.
Given East’s Highest priority, users will connect to it regardless of response times. The PCNSE Study Guide reinforces that priority is the primary factor, with response time as a secondary metric.
Practical Steps:
Verify gateway settings under Network > GlobalProtect > Gateways.
Confirm East is set to Highest priority in the portal configuration (Network > GlobalProtect > Portals).
Monitor connections via Monitor > Logs > GlobalProtect.
References:
Palo Alto Networks PAN-OS 11.1 Administrator’s Guide: Details GlobalProtect gateway selection based on priority and response time.
Palo Alto Networks PCNSE Study Guide: Explains gateway prioritization in GlobalProtect.
A network administrator notices a false-positive state after enabling Security profiles. When
the administrator checks the threat prevention logs, the related signature displays the
following:
threat type: spyware category: dns-c2 threat ID: 1000011111
Which set of steps should the administrator take to configure an exception for this
signature?
A. Navigate to Objects > Security Profiles > Anti-Spyware Select related profile Select DNS exceptions tabs Search related threat ID and click enable Commit
B. Navigate to Objects > Security Profiles > Vulnerability Protection Select related profile Select the signature exceptions tab and then click show all signatures Search related threat ID and click enable Change the default action Commit
C. Navigate to Objects > Security Profiles > Vulnerability Protection
Select related profile
Select the Exceptions lab and then click show all signatures
Search related threat ID and click enable
Commit
D. Navigate to Objects > Security Profiles > Anti-Spyware
Select related profile
Select the Exceptions lab and then click show all signatures
Search related threat ID and click enable Commit
Explanation:
The threat log indicates:
Threat Type: Spyware
Category: dns-c2 (DNS command-and-control)
Threat ID: 1000011111
This means the detection was triggered by the Anti-Spyware profile, specifically targeting DNS-based C2 activity. To create an exception for this signature, the administrator must modify the Anti-Spyware profile.
Steps to configure the exception:
Go to Objects > Security Profiles > Anti-Spyware
Select the relevant Anti-Spyware profile
Navigate to the Exceptions tab
Click Show All Signatures
Search for Threat ID 1000011111
Click Enable to allow editing
Modify the action (e.g., alert instead of block)
Commit the changes
📚 Reference:
Palo Alto Networks – Configure Anti-Spyware Exceptions
❌ Why Other Options Are Wrong:
A. Incorrect — DNS exceptions tab is for domain-based exceptions, not threat ID-based signature exceptions.
B & C. Incorrect — Vulnerability Protection profiles do not handle spyware or DNS-C2 signatures.
An administrator configures HA on a customer's Palo Alto Networks firewalls with path monitoring by using the default configuration values. What are the default values for ping interval and ping count before a failover is triggered?
A. Ping interval of 200 ms and ping count of three failed pings
B. Ping interval of 5000 ms and ping count of 10 failed pings
C. Ping interval of 200 ms and ping count of 10 failed pings
D. Ping interval of 5000 ms and ping count of three failed pings
Explanation:
In Palo Alto Networks High Availability (HA) configuration, path monitoring is used to detect link or path failures by sending periodic pings to a monitored IP address. If the pings fail consistently, a failover is triggered.
The default values for path monitoring are:
Ping Interval: 200 milliseconds
Ping Count: 10 consecutive failed pings
This means the firewall will wait for 10 failed pings, each spaced 200 ms apart, before initiating a failover.
📚 Reference:
Palo Alto Networks – Configure HA Path Monitoring
❌ Why Other Options Are Wrong:
A. Incorrect ping count (only 3)
B. & D. Incorrect ping interval (5000 ms is not default)
A company wants to deploy IPv6 on its network which requires that all company Palo Alto Networks firewalls process IPv6 traffic and to be configured with IPv6 addresses. Which consideration should the engineers take into account when planning to enable IPv6?
A. Device > Setup Settings Do not enable on each interface
B. Network > Zone Settings Do not enable on each interface
C. Network > Zone Settings Enable on each interface
D. Device > Setup Settings Enable on each interface
Explanation:
When you want to enable IPv6 support on Palo Alto firewalls:
1.Enable IPv6 per zone
Go to Network → Zones
Edit the zone → Enable IPv6 checkbox must be checked.
Without this, the zone won’t process IPv6 traffic, even if the interface has an IPv6 address.
2.Assign IPv6 addresses on interfaces
Go to Network → Interfaces
Add IPv6 addresses in the interface config.
This step provides the IPv6 identity for the firewall on that subnet.
The key planning consideration is that IPv6 must be enabled at the zone level per interface, not just globally in Device > Setup.
Why the other options are incorrect:
A. Device > Setup Settings Do not enable on each interface ❌
There’s no global IPv6 toggle at Device > Setup. IPv6 is handled at zone + interface levels.
B. Network > Zone Settings Do not enable on each interface ❌
Wrong — you must enable IPv6 at the zone level for each zone that will process IPv6 traffic.
C. Network > Zone Settings Enable on each interface ✅
Correct — IPv6 traffic processing requires enabling IPv6 per zone and per interface.
D. Device > Setup Settings Enable on each interface ❌
Wrong location. Interfaces and zones are configured under Network, not Device > Setup.
Reference:
Palo Alto Networks TechDocs: Configure IPv6
PAN KB: How to Enable IPv6 in Zones and Interfaces
An engineer is pushing configuration from Panorama to a managed firewall What happens when the pushed Panorama configuration has Address Object names that duplicate the Address Objects already configured on the firewall?
A. The firewall ignores only the pushed objects that have the same name as the locally configured objects, and it will commit the rest of the pushed configuration.
B. The firewall fully commits all of the pushed configuration and overwrites its locally configured objects
C. The firewall rejects the pushed configuration, and the commit fails.
D. The firewall renames the duplicate local objects with "-1" at the end signifying they are clones; it will update the references to the objects accordingly and fully commit the pushed configuration.
Explanation:
When an engineer pushes a configuration from Panorama to a managed Palo Alto Networks firewall, conflicts can arise if the pushed configuration contains Address Object names that duplicate those already configured locally on the firewall. In Palo Alto Networks’ management architecture, Panorama manages device groups and templates, but the firewall maintains its own local configuration database. When a push occurs, Panorama attempts to merge its configuration with the firewall’s local settings. If duplicate Address Object names are detected (e.g., the same name with different IP addresses or attributes), the firewall considers this a configuration conflict. By default, the firewall rejects the entire pushed configuration, and the commit fails, requiring the administrator to resolve the conflict manually. The Palo Alto Networks PAN-OS 11.1 Administrator’s Guide states that duplicate object names cause a commit failure unless explicitly resolved, making option C correct.
Why Other Options Are Incorrect:
A. The firewall ignores only the pushed objects that have the same name as the locally configured objects, and it will commit the rest of the pushed configuration:
This is incorrect because the firewall does not selectively ignore duplicates and commit the rest. A conflict triggers a full rejection to maintain configuration integrity. The PCNSE Study Guide notes that partial commits are not supported in such cases.
B. The firewall fully commits all of the pushed configuration and overwrites its locally configured objects:
This is incorrect because Panorama does not automatically overwrite local objects without explicit override settings (e.g., force sync or template stack override), which are not default. The PAN-OS 11.1 Administrator’s Guide indicates that overwrites require manual intervention or specific configuration options.
D. The firewall renames the duplicate local objects with "-1" at the end signifying they are clones;
it will update the references to the objects accordingly and fully commit the pushed configuration: This is incorrect because the firewall does not automatically rename objects or resolve duplicates by appending "-1". Such behavior would risk policy inconsistencies, and the PCNSE Study Guide confirms that manual resolution is required.
Practical Steps:
1.After the commit fails, check the commit error in Panorama under Commit > Push to Devices > Task Details.
2.Review the conflicting Address Objects in Objects > Addresses on both Panorama and the firewall.
3.Resolve duplicates by either:
Renaming the pushed objects in Panorama to avoid conflicts.
Deleting or modifying the local objects on the firewall to align with Panorama.
Retry the push and commit.
References:
Palo Alto Networks PAN-OS 11.1 Administrator’s Guide: Details configuration push conflicts and commit failure due to duplicate objects.
Palo Alto Networks PCNSE Study Guide: Explains resolution of object name conflicts during Panorama pushes.
Which statement about High Availability timer settings is true?
A. Use the Critical timer for faster failover timer settings.
B. Use the Aggressive timer for faster failover timer settings
C. Use the Moderate timer for typical failover timer settings
D. Use the Recommended timer for faster failover timer settings.
Explanation:
Palo Alto Networks firewalls use timers to monitor the health of the HA peers and trigger a failover if a peer is detected as failed. These timers are categorized into three predefined sets:
Recommended:
This is the default timer setting. It provides a balance between detecting failures and avoiding false positives caused by temporary network issues. This is the setting you would use for a typical, stable network environment.
Aggressive:
This setting uses the shortest possible timer values. It is designed to provide the fastest possible failover detection. You would use this in environments where downtime is extremely critical and you need to fail over as quickly as possible, even at the risk of a false failover from a minor network fluctuation.
Critical:
This setting uses a failover threshold that is even more stringent than the Aggressive setting. The timer values are so small that they are only applicable in very specific, high-performance environments and can be prone to false positives if not used carefully.
Moderate:
There is no pre-defined "Moderate" timer setting in the Palo Alto Networks HA configuration. The available options are Recommended, Aggressive, and Critical.
Analysis of the Options
A. Use the Critical timer for faster failover timer settings:
While the Critical timer is fast, the Aggressive timer is the most commonly recommended choice for "faster failover" in a typical setup. The Critical timer is a more specialized, extreme setting.
B. Use the Aggressive timer for faster failover timer settings:
This is the correct statement. The Aggressive timer is specifically designed for environments that require faster failover detection than the default "Recommended" setting.
C. Use the Moderate timer for typical failover timer settings:
This is incorrect. There is no "Moderate" timer. The "Recommended" timer is the one used for typical settings.
D. Use the Recommended timer for faster failover timer settings:
This is incorrect. The Recommended timer is the default and is designed for normal operations, not for fast failover. The Aggressive and Critical timers are the options for faster failover
A firewall engineer is investigating high dataplane CPU utilization. To decrease the load on this CPU, what should be reduced?
A. The amount of decrypted traffic
B. The timeout value for admin sessions
C. The number of mapped User-ID groups
D. The number of permitted IP addresses on the management interface
Explanation:
The dataplane CPU is responsible for handling traffic processing, which includes:
Session setup and teardown
Security policy enforcement
Content inspection (threat prevention, URL filtering, WildFire analysis, etc.)
SSL/TLS decryption and re-encryption (a very CPU-intensive operation)
🔹 When dataplane CPU is high, one of the first tuning levers is to check how much traffic is being decrypted. SSL/TLS decryption (especially with strong ciphers) can significantly increase load. Reducing the amount of decrypted traffic (by excluding certain trusted traffic or unnecessary categories like streaming or updates) will directly reduce dataplane CPU utilization.
Why the other options are incorrect:
B. The timeout value for admin sessions ❌
Admin sessions (WebUI/CLI) consume management plane CPU, not dataplane CPU.
Adjusting timeout values won’t affect dataplane utilization.
C. The number of mapped User-ID groups ❌
User-ID group mapping impacts management plane memory/processing (handling group lookups from AD/LDAP), not dataplane CPU.
D. The number of permitted IP addresses on the management interface ❌
This affects management plane access (which IPs can reach the management interface).
It has no effect on dataplane CPU load.
Reference:
Palo Alto Networks TechDocs: Monitor Firewall Resources
Best Practices: Reduce SSL Decryption Overhead
Phase two of a VPN will not establish a connection. The peer is using a policy-based VPN configuration. What part of the configuration should the engineer verify?
A. IKE Crypto Profile
B. Security policy
C. Proxy-IDs
D. PAN-OS versions
Explanation:
When a Palo Alto Networks firewall is establishing Phase 2 (IPSec) of a VPN with a policy-based VPN peer, the most critical configuration to verify is the Proxy-ID.
Why Proxy-IDs Matter:
Policy-based VPNs (e.g., Cisco ASA, Fortinet) define VPN traffic using access control lists (ACLs) or policies, not tunnel interfaces.
Palo Alto Networks firewalls use route-based VPNs, which rely on Proxy-IDs to define the traffic selectors for Phase 2.
If the Proxy-ID values (local and remote subnets) do not match what the peer expects, Phase 2 will fail even if Phase 1 (IKE) succeeds.
📚 Reference:
Palo Alto Networks – Configure IPSec VPN with Proxy IDs
❌ Why Other Options Are Wrong:
A. IKE Crypto Profile: Relevant for Phase 1 (IKE), not Phase 2.
B. Security Policy: Needed for allowing traffic through the tunnel, but not for Phase 2 establishment.
D. PAN-OS Versions: Mismatched versions may cause compatibility issues, but they don’t directly affect Proxy-ID negotiation.
| Page 8 out of 27 Pages |
| Previous |