A network administrator wants to deploy SSL Forward Proxy decryption. What two attributes should a forward trust certificate have? (Choose two.)
A. A subject alternative name
B. A private key
C. A server certificate
D. A certificate authority (CA) certificate
Explanation
🔹1: Recall what a Forward Trust Certificate is
In SSL Forward Proxy, the firewall intercepts TLS sessions, decrypts traffic, and re-signs the server’s certificate with its own Forward Trust Certificate.
For the client to accept this re-signed cert:
The firewall must act as a certificate authority (CA) (so it can generate and sign server certs on the fly).
That certificate must have a private key (so the firewall can actually sign new certs).
Clients must trust this CA (so you import it into browsers/endpoints).
🔹2: Evaluate Options
A. A subject alternative name (SAN)
❌ Not required on the forward trust cert. SANs matter for end-entity server certs, not for the CA signing cert.
B. A private key
✅ Required — without a private key, the firewall cannot dynamically sign certificates.
C. A server certificate
❌ Wrong — it’s not a single server cert; it must be a CA cert used for signing.
D. A certificate authority (CA) certificate
✅ Correct — the forward trust cert must be a CA cert so the firewall can generate child certificates.
🔹 Key Takeaway (PCNSE)
Forward Trust Cert = CA cert + private key → used to sign trusted server certs during SSL Forward Proxy.
Forward Untrust Cert = CA cert + private key → used to re-sign untrusted/invalid server certs.
📖 Reference:
Palo Alto Networks — Configure SSL Forward Proxy
An engineer needs to permit XML API access to a firewall for automation on a network segment that is routed through a Layer 3 sub-interface on a Palo Alto Networks firewall. However, this network segment cannot access the dedicated management interface due to the Security policy. Without changing the existing access to the management interface, how can the engineer fulfill this request?
A. Specify the subinterface as a management interface in Setup > Device > Interfaces.
B. Add the network segment's IP range to the Permitted IP Addresses list.
C. Enable HTTPS in an Interface Management profile on the subinterface
D. Configure a service route for HTTP to use the subinterface.
Explanation:
Why This Option?
1.Problem:
The network segment cannot access the dedicated management interface due to Security policy restrictions.
XML API access (which uses HTTPS) is needed for automation.
2.Solution:
Enable HTTPS management access on the Layer 3 sub-interface (where the network segment is connected).
This allows the segment to reach the firewall’s XML API via the sub-interface IP, bypassing the need for the management interface.
3.Steps:
Navigate to Network > Interfaces > [sub-interface] > Advanced > Management Profile.
Create/assign an Interface Management Profile with HTTPS enabled.
Ensure the Security policy allows access to the sub-interface IP.
Why Not Other Options?
A.Only dedicated management interfaces (MGT) can be set as management interfaces; data interfaces cannot.
B."Permitted IP Addresses" only applies to the dedicated management interface, not data interfaces.
DService routes control outbound firewall traffic (e.g., updates), not inbound API access.
Key Note:
XML API uses HTTPS (port 443), so enabling HTTPS on the sub-interface is sufficient.
Reference:
Palo Alto Management Interface Guide:
"Enable HTTPS in an Interface Management Profile to allow API access on data interfaces."
A company is deploying User-ID in their network. The firewall team needs to have the ability to see and choose from a list of usernames and user groups directly inside the Panorama policies when creating new security rules. How can this be achieved?
A. By configuring Data Redistribution Client in Panorama > Data Redistribution
B. By configuring User-ID group mapping in Panorama > User Identification
C. By configuring User-ID source device in Panorama > Managed Devices
D. By configuring Master Device in Panorama > Device Groups
Explanation:
Why This Option?
1.User-ID Group Mapping in Panorama:
To populate usernames and groups in Panorama policies, you must configure Group Mapping under:
Panorama > User Identification > Group Mapping.
This allows Panorama to query Active Directory (or other identity sources) and cache user/group data for use in policy rules.
2.How It Works:
Panorama connects to AD/LDAP servers (or User-ID agents) to retrieve user and group lists.
These lists become available in the Policy Editor when creating security rules (e.g., source/destination user fields).
Why Not Other Options?
A.Data Redistribution syncs data between firewalls, but doesn’t provide user/group lists to Panorama.
C.User-ID source device configures where User-ID data comes from, but doesn’t enable policy selection in Panorama.
D.Master Device is for high availability, not user/group resolution.
Key Requirement:
Panorama must have direct access to AD/LDAP or a User-ID agent to fetch user/group information.
Reference:
Panorama User-ID Admin Guide:
"Group Mapping in Panorama allows administrators to select users/groups directly in security policies."
Which type of policy in Palo Alto Networks firewalls can use Device-ID as a match condition?
A. NAT
B. DOS protection
C. QoS
D. Tunnel inspection
Explanation:
The question asks which type of policy in Palo Alto Networks firewalls can use Device-ID as a match condition. Device-ID, part of the User-ID feature, identifies devices (e.g., laptops, phones) based on their attributes (e.g., MAC address, device type) and allows policies to be applied based on device identity. Let’s evaluate the options to determine where Device-ID can be used as a match condition.
Why C. QoS?
Purpose: Quality of Service (QoS) policies on Palo Alto Networks firewalls allow traffic prioritization and bandwidth management based on various match criteria, including User-ID and Device-ID. Device-ID can be used to classify traffic from specific devices (e.g., prioritizing VoIP phones or limiting bandwidth for guest devices), enabling granular QoS control.
Configuration:
Navigate to Policies > QoS.
Create or edit a QoS policy.
In the match criteria, select Device under the User/Device tab.
Choose a Device-ID group or specific device (e.g., "Corporate-Laptops") identified by the User-ID agent or Terminal Services agent.
Define the QoS class (e.g., priority, bandwidth limit).
Behavior: The firewall applies QoS rules based on the device identity, ensuring tailored traffic management.
Reference:
Palo Alto Networks documentation states, "QoS policies support Device-ID as a match condition to enforce bandwidth and prioritization based on device type."
Why Not the Other Options?
A. NAT:
Explanation: Network Address Translation (NAT) policies translate IP addresses and ports but do not support Device-ID as a match condition. NAT rules use source/destination zones, IPs, and ports, not device identity, as the focus is on address mapping, not behavioral or identity-based control.
Why Incorrect:
Device-ID is not a valid NAT criterion.
B. DoS Protection:
Explanation: Denial of Service (DoS) protection policies mitigate attacks by rate-limiting or blocking traffic based on source/destination, zones, or applications, but they do not support Device-ID as a match condition. DoS rules are designed for threat mitigation, not device-specific identification.
Why Incorrect:.
Device-ID is not applicable to DoS policies
D. Tunnel inspection:
Explanation: Tunnel inspection refers to policies or profiles (e.g., Decryption, VPN) that inspect traffic within tunnels (e.g., IPsec, SSL VPN). While User-ID can be used in Security policies to control tunnel traffic, Device-ID is not a supported match condition for tunnel inspection itself. Tunnel inspection focuses on protocol and content, not device identity.
Why Incorrect:
Device-ID is not a valid match for tunnel inspection policies.
Additional Context:
Device-ID Functionality: Device-ID extends User-ID by identifying devices using agents (e.g., Windows User-ID agent with Terminal Services) or profiling (e.g., via MAC OUI or DHCP fingerprints). It is supported in Security and QoS policies for granular control.
Supported Policies:
Security Policies: Use Device-ID to allow/deny traffic based on device.
QoS Policies: Use Device-ID for bandwidth allocation.
Other policy types (NAT, DoS, Tunnel) do not leverage Device-ID.
Configuration Steps:
Enable Device-ID under Device > User Identification > Device Identification.
Configure a Device-ID agent or profiling.
Apply to QoS policies as a match condition.
Best Practices:
Use Device-ID groups for scalability.
Test with Monitor > User-ID to verify device mappings.
Monitor QoS logs under Monitor > Logs > QoS.
PCNSE Exam Relevance: This question tests your understanding of policy types and Device-ID integration, a key topic in the PCNSE exam. It requires knowledge of where device-based conditions apply.
Conclusion:
The type of policy in Palo Alto Networks firewalls that can use Device-ID as a match condition is QoS, allowing the firewall to prioritize or limit traffic based on device identity.
References:
Palo Alto Networks Documentation: Device-ID Configuration
Palo Alto Networks Documentation: QoS Policy with Device-ID
ExamTopics PCNSE Discussion: Device-ID Usage
Exhibit.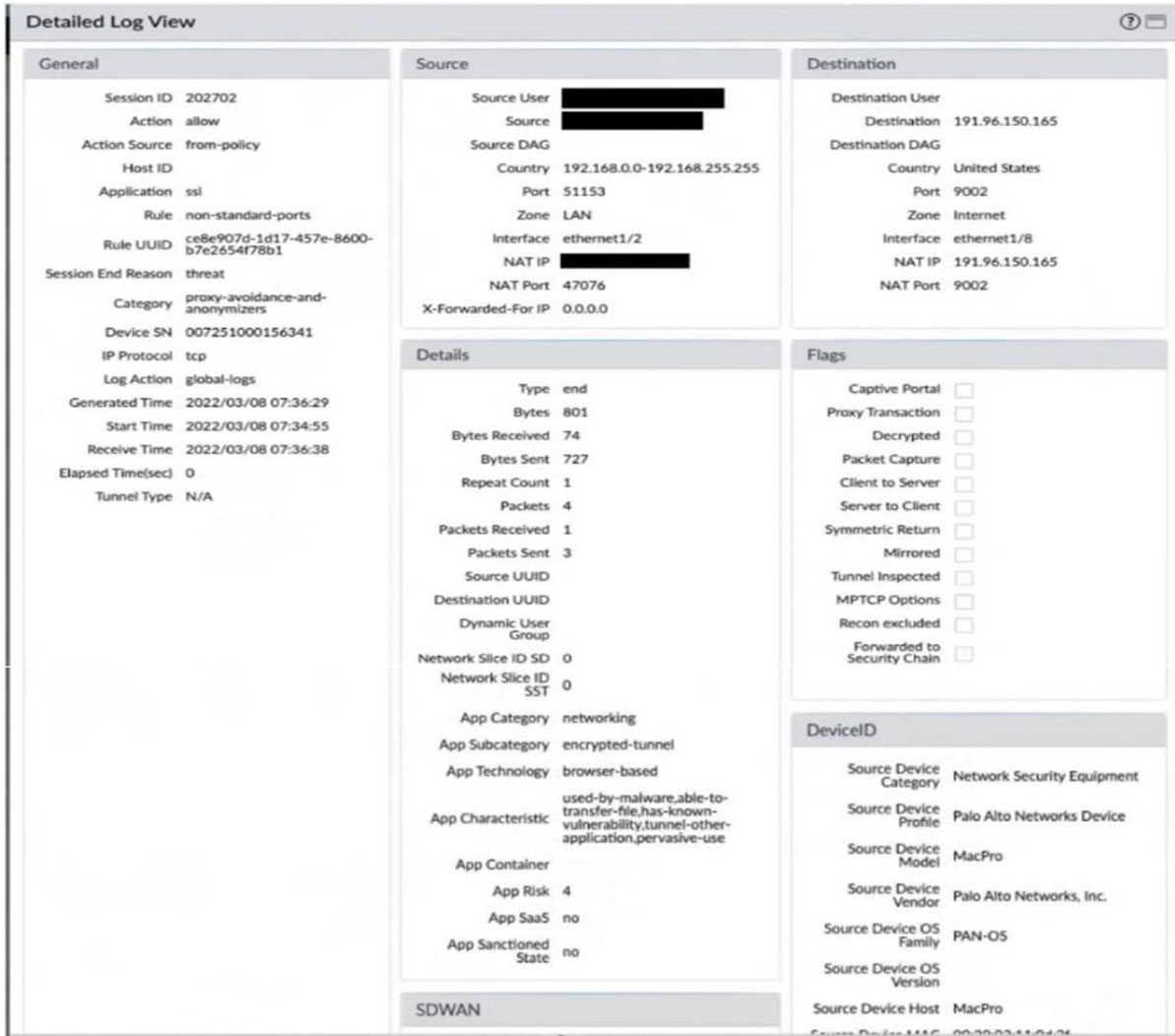
Given the screenshot, how did the firewall handle the traffic?
A. Traffic was allowed by profile but denied by policy as a threat.
B. Traffic was allowed by policy but denied by profile as a threat.
C. Traffic was allowed by policy but denied by profile as encrypted.
D. Traffic was allowed by policy but denied by profile as a nonstandard port.
Explanation:
Key Evidence from the Log:
1.Action: allow (from policy) and Session End Reason: threat
The traffic was allowed by the Security policy (rule non-standard-ports).
However, it was blocked by a Security profile (e.g., Antivirus, Anti-Spyware) because it was classified as a threat.
2.Threat Indicators:
Category: proxy-avoidance-and-anonymizers (suspicious).
Application: ssl on non-standard port 9002 (often used for tunneling).
App Subcategory: encrypted-tunnel (potential bypass attempt).
3.Profile Override:
Security profiles can override policy allows if threats are detected (e.g., block malicious content).
Why Not Other Options?
A.Policies don’t deny traffic after allowing it; profiles do.
C.Encryption alone doesn’t cause denies—threats do.
D.Non-standard ports are allowed by the policy (rule name confirms).
Reference:
Palo Alto Security Profiles Documentation:
"Security profiles can block sessions allowed by policies if threats are detected."
An administrator needs to validate that policies that will be deployed will match the appropriate rules in the device-group hierarchy. Which tool can the administrator use to review the policy creation logic and verify that unwanted traffic is not allowed?
A. Preview Changes
B. Managed Devices Health
C. Test Policy Match
D. Policy Optimizer
Explanation:
Why "Test Policy Match"?
1.Purpose:
The Test Policy Match tool (in Panorama or firewall) allows administrators to simulate traffic against the policy rulebase before deployment.
It checks which rule matches specific traffic (source, destination, application, etc.) and validates if the intended behavior (allow/deny) occurs.
2.Key Benefits:
Identifies rule misconfigurations (e.g., overly permissive rules).
Ensures policies align with security requirements without live traffic.
Why Not Other Options?
A. Preview Changes
Shows configuration diffs (e.g., new rules), but doesn’t test traffic matching.
B. Managed Devices Health
Monitors device status, not policy logic.
D. Policy Optimizer
Recommends rule adjustments based on logs, but doesn’t simulate traffic.
How to Use:
In Panorama, go to: Policies > Security > Test Policy Match.
Enter traffic parameters (e.g., source IP, destination IP, application).
Review which rule matches and the action (allow/deny).
Reference:
Palo Alto Admin Guide:
"Test Policy Match validates rule precedence and traffic handling before commit."
An administrator notices interface ethernet1/2 failed on the active firewall in an active / passive firewall high availability (HA) pair Based on the image below what - if any - action was taken by the active firewall when the link failed?
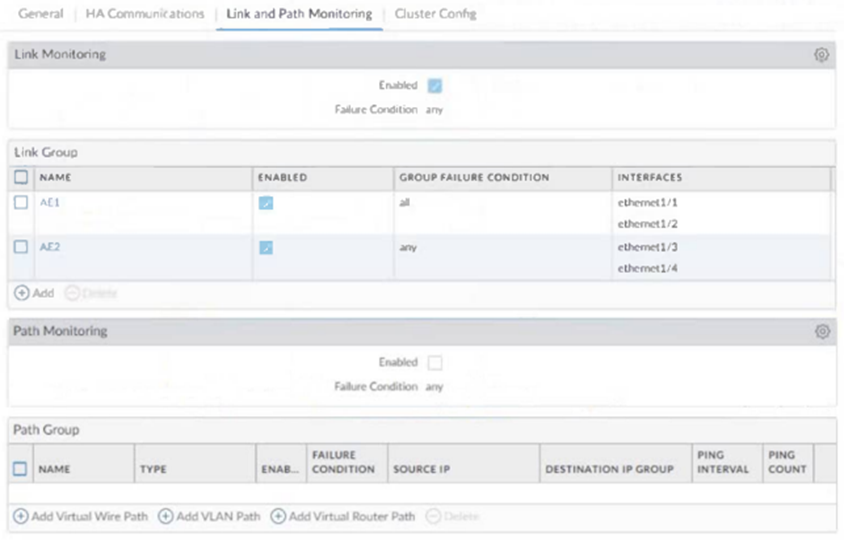
A. The active firewall failed over to the passive HA member because "any" is selected for the Link Monitoring
B. No action was taken because Path Monitoring is disabled
C. No action was taken because interface ethernet1/1 did not fail
D. The active firewall failed over to the passive HA member due to an AE1 Link Group failure
Explanation:
Key Configuration from the Screenshot:
1.Link Group A1:
Interfaces: ethernet1/1 and ethernet1/2
Group Failure Condition: all (meaning both interfaces must fail to trigger an HA failover).
Link Monitoring Failure Condition: Set to any (meaning any Link Group failing triggers failover).
2.Scenario Analysis:
Only ethernet1/2 failed, but ethernet1/1 is still operational.
Since Link Group A1 requires both interfaces to fail (due to all condition), the group does not report a failure.
Thus, no HA failover occurs.
Why Not Other Options?
A.Failover requires entire Link Group failure (not just one interface).
B.Path Monitoring is irrelevant—Link Monitoring is enabled and configured.
D.AE1 Link Group didn’t fail (only one interface down).
Reference:
Palo Alto HA Link Monitoring Guide:
"Link Groups with 'all' condition require all interfaces to fail to trigger failover."
What must be configured to apply tags automatically based on User-ID logs?
A. Device ID
B. Log Forwarding profile
C. Group mapping
D. Log settings
Explanation:
To apply tags automatically based on User-ID logs, the engineer must
configure a Log Forwarding profile that specifies the criteria for matching the logs and the
tags to apply. The Log Forwarding profile can be attached to a security policy rule or a
decryption policy rule to enable auto-tagging for the traffic that matches the rule. The tags
can then be used for dynamic address groups, policy enforcement, or
reporting1.
References:
Use Auto-Tagging to Automate Security Actions, PCNSE Study Guide (page 49)
An administrator is using Panorama to manage multiple firewalls. After upgrading all
devices to the latest PAN-OS software, the administrator enables log forwarding from the
firewalls to Panorama.
However, pre-existing logs from the firewalls are not appearing in Panorama.
Which action should be taken to enable the firewalls to send their pre-existing logs to
Panorama?
A. Export the log database.
B. Use the import option to pull logs.
C. Use the scp logdb export command.
D. Use the ACC to consolidate the logs.
Explanation:
When you configure log forwarding from firewalls to Panorama, only new logs generated after enabling the feature are forwarded.
Pre-existing logs already stored on the local firewall’s log database will not be automatically sent to Panorama.
To move old logs, you need to manually export them from the firewall log database and import them into Panorama
.
The correct method is to run the scp logdb export command on the firewall, which securely copies the firewall’s log database to Panorama (or another SCP server for import).
Why not the others?
A. Export the log database
→ too vague; doesn’t specify the actual mechanism (SCP is required).
B. Use the import option to pull logs
→ Panorama cannot pull logs from firewalls; logs must be pushed/exported.
D. Use the ACC to consolidate the logs
→ ACC (Application Command Center) only summarizes existing logs; it cannot retrieve old logs from firewalls.
A firewall engineer is tasked with defining signatures for a custom application. Which two sources can the engineer use to gather information about the application patterns'? (Choose two.)
A. Traffic logs
B. Data filtering logs
C. Policy Optimizer
D. Wireshark
Explanation:
The scenario involves a firewall engineer tasked with defining signatures for a custom application on a Palo Alto Networks firewall. Custom application signatures are created using the Application Override or Custom Application features in PAN-OS to identify unique traffic patterns. The engineer needs sources to gather information about the application’s patterns (e.g., ports, protocols, packet contents). Let’s evaluate the options to determine the two appropriate sources.
Why A. Traffic logs?
Purpose: Traffic logs (available under Monitor > Logs > Traffic) record details of network traffic processed by the firewall, including source/destination IPs, ports, protocols, and application identification attempts. For a custom application not yet recognized by App-ID, the logs can show the traffic’s behavior (e.g., consistent use of a non-standard port like TCP 12345) and help identify patterns that can be used to define a signature.
Use Case: The engineer can filter logs for traffic from known clients or servers of the custom application, noting the port, protocol, and any identifiable payload characteristics to inform the signature.
Reference:
Palo Alto Networks documentation suggests, "Traffic logs can be analyzed to identify patterns for custom application signatures."
Why D. Wireshark?
Purpose:
Wireshark is a packet analysis tool that captures and inspects network traffic in real-time, providing detailed packet-level information (e.g., headers, payloads, protocol sequences). The engineer can use Wireshark to capture traffic from the custom application, analyzing its unique patterns (e.g., specific byte sequences, handshake behavior) to create an accurate custom signature.
Use Case: By setting up a capture on the network segment where the application operates, the engineer can extract protocol details and payload data to define match conditions in the firewall’s custom application settings.
Reference:
Palo Alto Networks documentation recommends, "Packet captures from tools like Wireshark can be used to gather detailed traffic patterns for custom application signatures."
Why Not the Other Options?
B. Data filtering logs:
Explanation: Data filtering logs (under Monitor > Logs > Data Filtering) record events related to data loss prevention (DLP) or file transfer policies, focusing on file types and content rather than application identification patterns. These logs are not designed to provide the protocol or traffic behavior data needed to define a custom application signature.
Why Incorrect: These logs are irrelevant to application pattern analysis.
C. Policy Optimizer:
Explanation: The Policy Optimizer (under Policies > Policy Optimizer) analyzes traffic logs to identify unused or shadowed Security rules and suggests optimizations. While it uses traffic data, it is a post-analysis tool for policy refinement, not a source for gathering raw application pattern information to create signatures.
Why Incorrect: This is for policy optimization, not signature development.
Additional Context:
Custom Application Signatures: Defined under Objects > Custom Objects > Applications, these signatures use pattern matching (e.g., port, protocol, regular expressions) to identify custom apps. Sources like traffic logs and packet captures provide the necessary data.
Configuration Steps:
Analyze Traffic logs for port/protocol usage.
Use Wireshark to capture and decode packets.
Create a custom application with the identified patterns (e.g., port 12345, TCP, specific string).
Test the signature with Monitor > Packet Capture.
Best Practices:
Capture traffic during peak usage for accuracy.
Validate signatures with test traffic.
Update signatures if the application behavior changes.
PCNSE Exam Relevance:
This question tests your understanding of custom application signature creation, a key topic in the PCNSE exam. It requires knowledge of data sources for pattern analysis.
Conclusion:
The two sources the engineer can use to gather information about the custom application’s patterns are Traffic logs for high-level traffic behavior and Wireshark for detailed packet-level analysis, enabling the creation of effective signatures.
References:
Palo Alto Networks Documentation: Custom Application Signatures
Palo Alto Networks Documentation: Traffic Log Analysis
ExamTopics PCNSE Discussion: Custom App Signature Sources
Which two scripting file types require direct upload to the Advanced WildFire portal/API for analysis? (Choose two.)
A. Ps1
B. Perl
C. Python
D. VBS
Explanation:
Why These File Types?
PowerShell (.ps1) and VBScript (.vbs) are scripting languages commonly used in malware.
The Advanced WildFire portal/API requires direct upload for these because:
They are not executable binaries (e.g., .exe, .dll) that can be analyzed via standard WildFire submission (e.g., email, URL).
They require specialized sandboxing to simulate execution and detect malicious behavior.
Why Not Others?
Perl (.pl) and Python (.py) can also be analyzed, but they are less commonly targeted for direct upload requirements in this context. However, the question specifies "require direct upload," and PowerShell and VBScript are the most critical due to their prevalence in attacks.
Reference:
Palo Alto WildFire Admin Guide:
"Script files (e.g., .ps1, .vbs) must be uploaded directly to the Advanced WildFire portal for analysis."
<
An engineer has been asked to limit which routes are shared by running two different areas within an OSPF implementation. However, the devices share a common link for communication. Which virtual router configuration supports running multiple instances of the OSPF protocol over a single link?
A. OSPFV3
B. ECMP
C. ASBR
D. OSBF
Explanation:
Why OSPFv3?
1.Multiple OSPF Instances over a Single Link:
OSPFv3 (Open Shortest Path First version 3) supports multiple instances on a single interface.
Each instance operates independently, allowing different routing domains (areas) to share the same physical link.
2.Key Feature:
OSPFv3 uses Instance ID (ranging from 0 to 255) to differentiate between instances on the same link.
This enables segregation of routing information (e.g., limiting route sharing between areas).
Why Not Other Options?
B. ECMP
Equal-Cost Multi-Pathing balances traffic across multiple routes, but doesn’t support multiple OSPF instances.
C. ASBR
Autonomous System Boundary Router connects OSPF to other protocols, but doesn’t enable multiple instances on a link.
D. OSBF
Not a valid protocol (likely typo for OSPF).
Configuration Example:
In the virtual router, configure OSPFv3 with distinct instance IDs for each area.
Reference:
Palo Alto OSPFv3 Documentation:
"OSPFv3 instance IDs allow multiple routing domains over a single link."
| Page 5 out of 27 Pages |
| Previous |