An administrator is required to create an application-based Security policy rule to allow Evernote. The Evernote application implicitly uses SSL and web browsing. What is the minimum the administrator needs to configure in the Security rule to allow only Evernote?
A. Add the Evernote application to the Security policy rule, then add a second Security policy rule containing both HTTP and SSL.
B. Create an Application Override using TCP ports 443 and 80.
C. Add the HTTP. SSL. and Evernote applications to the same Security policy
D. Add only the Evernote application to the Security policy rule.
Explanation:
Palo Alto Networks firewalls use App-ID, a patented technology that identifies applications regardless of the port, protocol, or encryption used. App-ID works by using multiple classification techniques, including application signatures, protocol decoding, and heuristics, to accurately identify the application running on the network.
When you add the Evernote application to a security policy, the firewall's App-ID engine takes care of identifying and allowing all the necessary components for that application to function correctly, including its implicit use of SSL and web browsing.
App-ID Dependency:
The firewall understands the dependencies of applications. For example, it knows that Evernote traffic includes both the core Evernote application traffic and the underlying SSL and web-browsing protocols that it uses to communicate.
Default Behavior:
By default, when you select a higher-level application like evernote, the firewall implicitly allows the dependent applications like ssl and web-browsing. You don't need to manually add them to the rule. Doing so would be redundant and could potentially open up your network to unwanted traffic from other applications that also use SSL and web-browsing.
Therefore, the minimum and most secure configuration is to add only the Evernote application to the security policy rule. The firewall's App-ID will handle the rest.
The other options are incorrect:
A & C: Adding separate rules or including http and ssl in the same rule would be redundant and less secure. It would allow any traffic using HTTP/SSL to pass through, not just Evernote.
B: Application Override is used to bypass App-ID's default behavior, typically for custom or non-standard applications. It's not the correct approach here, as the firewall already has a signature for Evernote.
References:
App-ID Overview, Create a Security Policy Rule
Refer to the diagram. Users at an internal system want to ssh to the SSH server. The server is configured to respond only to the ssh requests coming from IP 172.16.16.1. In order to reach the SSH server only from the Trust zone, which Security rule and NAT rule must be configured on the firewall?
A. NAT Rule:
Source Zone: Trust -
Source IP: Any -
Destination Zone: Server -
Destination IP: 172.16.15.10 -
Source Translation: Static IP / 172.16.15.1
Security Rule:
Source Zone: Trust -
Source IP: Any -
Destination Zone: Trust -
Destination IP: 172.16.15.10 -
Application: ssh
B. NAT Rule:
Source Zone: Trust -
Source IP: 192.168.15.0/24 -
Destination Zone: Trust -
Destination IP: 192.168.15.1 -
Destination Translation: Static IP / 172.16.15.10
Security Rule:
Source Zone: Trust -
Source IP: 192.168.15.0/24 -
Destination Zone: Server -
Destination IP: 172.16.15.10 -
Application: ssh
C. NAT Rule:
Source Zone: Trust -
Source IP: Any -
Destination Zone: Trust -
Destination IP: 192.168.15.1 -
Destination Translation: Static IP /172.16.15.10
Security Rule:
Source Zone: Trust -
Source IP: Any -
Destination Zone: Server -
Destination IP: 172.16.15.10 -
Application: ssh
D. NAT Rule:
Source Zone: Trust -
Source IP: Any -
Destination Zone: Server -
Destination IP: 172.16.15.10 -
Source Translation: dynamic-ip-and-port / ethernet1/4
Security Rule:
Source Zone: Trust -
Source IP: Any -
Destination Zone: Server -
Destination IP: 172.16.15.10 -
Application: ssh
Explanation:
The SSH server is configured to only respond to requests from IP 172.16.16.1. To meet this requirement, the firewall must perform Source NAT so that outbound SSH traffic from the Trust zone appears to originate from that specific IP.
The correct configuration is:
1.NAT Rule:
Source Zone: Trust
Source IP: Any
Destination Zone: Server
Destination IP: 172.16.15.10
Source Translation: dynamic-ip-and-port / ethernet1/4
2.Security Rule:
Source Zone: Trust
Source IP: Any
Destination Zone: Server
Destination IP: 172.16.15.10
Application: ssh
3.This setup ensures:
Traffic from internal users is NATed to the expected source IP.
The SSH server receives traffic that matches its configured source filter.
The firewall allows the traffic through the correct zones and application.
📘 Reference:
Verified via Exam4Training PCNSE Question #71 and Ace4Sure PCNSE Scenario
Which GlobalProtect gateway selling is required to enable split-tunneling by access route, destination domain, and application?
A. No Direct Access to local networks
B. Tunnel mode
C. iPSec mode
D. Satellite mode
Explanation:
Why Tunnel Mode?
1.Split-Tunneling Granularity:
Tunnel mode is the only GlobalProtect gateway setting that supports split-tunneling by access route, destination domain, and application simultaneously.
It allows administrators to define:
Access Routes: Specific IP subnets to tunnel (e.g., corporate networks).
Domains: Destination domains (e.g., *.company.com) to tunnel.
Applications: Specific executables (e.g., outlook.exe) to tunnel.
2.How It Works:
Traffic matching any of these criteria is routed through the VPN tunnel.
Non-matching traffic (e.g., general web browsing) accesses the internet directly.
Why Not Other Options?
ADisables split-tunneling entirely (forces all traffic through VPN).
CIPSec mode is legacy and does not support domain/application-based split-tunneling.
DSatellite mode is for cloud gateways and lacks granular split-tunneling controls.
Configuration Steps:
Navigate to: Network > GlobalProtect > Gateways > [Gateway] > Agent > Split Tunnel.
Set Tunnel Mode = Enabled.
Configure:
Access Routes (e.g., 10.0.0.0/8).
Domains (e.g., *.internal.com).
Applications (e.g., ms-outlook.exe).
Reference:
Palo Alto GlobalProtect Admin Guide
"Tunnel mode enables advanced split-tunneling by access route, domain, and application."
An engineer is deploying multiple firewalls with common configuration in Panorama. What are two benefits of using nested device groups? (Choose two.)
A. Inherit settings from the Shared group
B. Inherit IPSec crypto profiles
C. Inherit all Security policy rules and objects
D. Inherit parent Security policy rules and objects
Explanation:
The scenario involves an engineer deploying multiple firewalls with a common configuration using Panorama, and the question asks for two benefits of using nested device groups. Nested device groups in Panorama allow for a hierarchical structure where settings and policies can be inherited from parent groups, providing flexibility and centralized management. Let’s evaluate the options to determine the correct benefits.
Why A. Inherit settings from the Shared group?
Purpose: In Panorama, the Shared group is a top-level container that holds configurations (e.g., network settings, templates, and objects) applicable to all device groups unless overridden. Nested device groups can inherit these settings, allowing the engineer to define common configurations (e.g., DNS, NTP, or interface settings) at the Shared level and apply them to all firewalls, reducing redundancy.
Benefit: This enables consistent baseline configurations across all firewalls while allowing nested groups to customize specific settings as needed. It simplifies management by centralizing common settings.
Reference:
Palo Alto Networks documentation states, "Nested device groups can inherit settings from the Shared group, providing a foundation for common configurations."
Why D. Inherit parent Security policy rules and objects?
Purpose: Nested device groups inherit Security policy rules and objects (e.g., addresses, services, applications) from their parent device groups. This hierarchical inheritance allows the engineer to define broad policies at a higher-level parent group (e.g., allowing HTTP traffic) and refine or add specific rules in lower-level nested groups (e.g., restricting HTTP to certain users), tailoring policies to specific firewall subsets.
Benefit: It promotes reusability and consistency across firewalls while enabling granular control. Changes at the parent level automatically propagate to nested groups unless overridden, streamlining policy management.
Reference:
Palo Alto Networks documentation notes, "Nested device groups inherit Security policy rules and objects from parent groups, allowing for layered policy design."
Why Not the Other Options?
B. Inherit IPSec crypto profiles:
Explanation: IPSec crypto profiles (e.g., encryption algorithms, authentication methods) are configured within network templates or template stacks, not device groups. Device groups handle policies (e.g., Security, NAT), while templates manage network and device settings (e.g., IPSec profiles). Nested device groups do not inherit IPSec crypto profiles directly; these are inherited via template stacks.
Why Incorrect:
This is a template-level setting, not a device group benefit.
C. Inherit all Security policy rules and objects:
Explanation: This option suggests inheritance from all levels (e.g., Shared and all parent groups), but nested device groups inherit only from their immediate parent group in the hierarchy, not all groups. They can also inherit from the Shared group independently. The inheritance is selective and hierarchical, not a blanket inheritance of all rules and objects.
Why Incorrect: This overstates the scope of inheritance; it’s limited to the parent group’s rules and objects.
Additional Context:
Nested Device Groups: These are organized in a parent-child hierarchy within Panorama. For example, a parent group might contain baseline Security rules, while a child group adds specific exceptions. The Shared group provides a global baseline.
Configuration Steps:
Navigate to Panorama > Device Groups.
Create a parent device group (e.g., "Global-Policies") and a nested group (e.g., "Regional-Policies").
Define common settings/rules in the Shared group and parent group, then refine in the nested group.
Push the configuration to the firewalls.
Best Practices:
Use nested groups to reflect organizational structure (e.g., regions, departments).
Minimize overrides to maintain consistency.
Test policy inheritance with Panorama > Preview Changes.
PCNSE Exam Relevance:
This question tests your understanding of Panorama’s device group hierarchy and inheritance, a key topic in the PCNSE exam. It requires knowledge of how nested groups enhance configuration management.
Conclusion:
Two benefits of using nested device groups are that they inherit settings from the Shared group (providing a common baseline) and inherit parent Security policy rules and objects (enabling layered policy design), improving efficiency and consistency across multiple firewalls.
References:
Palo Alto Networks Documentation: Panorama Device Groups and Inheritance
Palo Alto Networks Documentation: Nested Device Group Configuration
ExamTopics PCNSE Discussion: Panorama Nested Groups
Which function does the HA4 interface provide when implementing a firewall cluster which contains firewalls configured as active-passive pairs?
A. Perform packet forwarding to the active-passive peer during session setup and asymmetric traffic flow.
B. Perform synchronization of routes, IPSec security associations, and User-ID information.
C. Perform session cache synchronization for all HA cluster members with the same cluster ID.
D. Perform synchronization of sessions, forwarding tables, and IPSec security associations between firewalls in an HA pair.
Explanation:
Why This Option?
1.HA4 Interface Purpose:
The HA4 link (also called the "HA data link") is responsible for synchronizing stateful data between active and passive firewalls in an HA pair.
This includes:
Session information (e.g., TCP/UDP states).
Forwarding tables (for seamless failover).
IPSec security associations (VPN tunnels).
2.Active-Passive HA Workflow:
The active firewall continuously syncs this data to the passive firewall via HA4.
During failover, the passive firewall takes over without dropping sessions.
Why Not Other Options?
A.Packet forwarding is handled by the data plane (data interfaces), not HA4.
B.Routes and User-ID info sync via HA1 (control link), not HA4.
C.HA4 syncs sessions within a pair, not across clusters (cluster ID is irrelevant).
Key HA Links Summary:
HA1: Syncs configs, routes, User-ID (control link).
HA2: Heartbeat/hello packets (optional backup).
HA3: Management sync (optional).
HA4: Session/forwarding table/IPSec SA sync (data link).
Reference:
Palo Alto HA Admin Guide:
"HA4 ensures stateful sync of sessions, forwarding tables, and IPSec SAs for hitless failover."
Information Security is enforcing group-based policies by using security-event monitoring
on Windows User-ID agents for IP-to-User mapping in the network. During the rollout,
Information Security identified a gap for users authenticating to their VPN and wireless
networks.
Root cause analysis showed that users were authenticating via RADIUS and that
authentication events were not captured on the domain controllers that were being
monitored Information Security found that authentication events existed on the Identity
Management solution (IDM). There did not appear to be direct integration between PANOS
and the IDM solution.
How can Information Security extract and learn iP-to-user mapping information from
authentication events for VPN and wireless users?
A. Add domain controllers that might be missing to perform security-event monitoring for VPN and wireless users.
B. Configure the integrated User-ID agent on PAN-OS to accept Syslog messages over TLS.
C. Configure the User-ID XML API on PAN-OS firewalls to pull the authentication events directly from the IDM solution
D. Configure the Windows User-ID agents to monitor the VPN concentrators and wireless controllers for IP-to-User mapping.
Explanation:
1: Problem restated
Goal: Enforce group-based policies (needs accurate IP-to-User mapping).
Current setup: Using Windows User-ID agent monitoring domain controller security logs.
Gap: VPN + Wireless logins are via RADIUS → auth events not on DCs, but instead on the Identity Management (IDM) solution.
IDM does not have a direct PAN-OS integration.
So, how do we get User-ID mappings from IDM into PAN-OS?
2: Methods for IP-to-User Mapping
PAN-OS supports multiple methods:
Windows security event logs (via User-ID agent).
Syslog parsing from external auth sources (RADIUS, NAC, wireless controllers, VPN concentrators, IDM, etc.).
XML API (push mappings into PAN-OS).
Captive Portal / GlobalProtect.
👉 In this case: IDM generates syslog auth events → The right approach is to configure Syslog Listener in PAN-OS User-ID agent to accept those syslog messages.
3: Analyze the Options
A. Add domain controllers that might be missing to perform security-event monitoring for VPN and wireless users.
❌ Wrong. Auth events are not on DCs at all (root cause already confirmed).
B. Configure the integrated User-ID agent on PAN-OS to accept Syslog messages over TLS.
✅ Correct. PAN-OS User-ID agent (built-in or external) can parse syslog messages from IDM, extract username ↔ IP, and populate User-ID mappings. This solves the issue directly.
C. Configure the User-ID XML API on PAN-OS firewalls to pull the authentication events directly from the IDM solution.
❌ Wrong direction. PAN-OS does not “pull” from IDM via XML API — instead, third-party systems push mappings via XML API.
D. Configure the Windows User-ID agents to monitor the VPN concentrators and wireless controllers for IP-to-User mapping.
❌ Not possible in this case. Those devices authenticate through IDM, not directly exposing logs. Windows User-ID agents can’t just “monitor” VPN controllers unless they emit Windows events (which they don’t).
🔹 Key Takeaways for PCNSE
If auth logs don’t hit the DCs, use Syslog integration to feed mappings.
PAN-OS can parse syslog login events from IDM, RADIUS servers, wireless controllers, NAC, etc.
XML API is push-only — third-party system pushes mappings to PAN-OS, not PAN-OS pulling.
📖 Reference:
Configure User Mapping Using Syslog Senders
“A firewall or User-ID agent can monitor syslog messages from authentication systems to learn IP-to-username mappings.”
With the default TCP and UDP settings on the firewall, what will be the identified application in the following session?
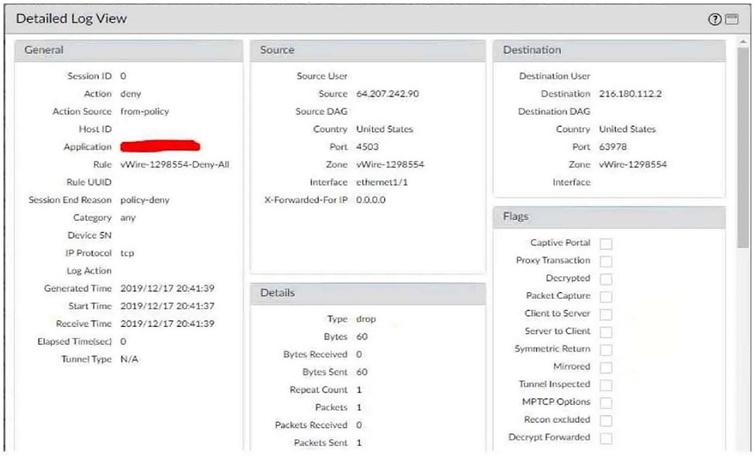
A. Incomplete
B. unknown-tcp
C. Insufficient-data
D. not-applicable
Explanation:
Why:
The log shows Action: deny and Session End Reason: policy-deny. When traffic is blocked by policy before App-ID can inspect payload, the firewall can’t identify an application and logs it as not-applicable. This is exactly how PAN-OS behaves when a session is denied on the first packet(s)—no app match is attempted, so the Application field is not-applicable.
Why the others are wrong
A. Incomplete → Used when the TCP 3-way handshake didn’t complete or completed with no identifiable data; typically seen on allowed sessions that later age out/reset, not on immediate policy denies.
B. unknown-tcp → Requires a completed handshake and payload that doesn’t match any App-ID; again, not a policy-deny on first packet.
C. Insufficient-data→ Handshake finished and there was some data, but not enough to identify an app; not the case for a policy-denied sess
An existing log forwarding profile is currently configured to forward all threat logs to Panorama. The firewall engineer wants to add syslog as an additional log forwarding method. The requirement is to forward only medium or higher severity threat logs to syslog. Forwarding to Panorama must not be changed. Which set of actions should the engineer take to achieve this goal?
A. 1- Open the current log forwarding profile.
2. Open the existing match list for threat log type.
3. Define the filter.
4. Select the syslog forward method.
B. 1. Create a new log forwarding profile.
2. Add a new match list for threat log type.
3. Define the filter.
4. Select the Panorama and syslog forward methods.
C. 1. Open the current log forwarding profile.
2. Add a new match list for threat log type.
3. Define the filter.
4. Select the syslog forward method.
D. 1. Create a new log forwarding profile.
2. Add a new match list for threat log type.
3. Define the filter.
4. Select the syslog forward method.
Explanation:
To achieve the goal of forwarding only medium or higher severity threat logs to a new destination (syslog) while maintaining the existing forwarding to Panorama, the engineer should follow these steps:
1.Open the existing log forwarding profile.
The current profile is already configured to send all threat logs to Panorama. Since you want to keep this configuration, you should modify the existing profile rather than create a new one.
2.Add a new match list for the threat log type.
Log forwarding profiles use a series of "match lists" to define different forwarding rules based on log type and filters. You need to create a new match list specifically for the syslog forwarding.
3.Define the filter.
Within the new match list, you must specify a filter. The filter should be set to capture logs with a severity of "medium" or higher. The filter expression would look something like (severity geq medium).
4.Select the syslog forward method.
For this new match list, you should select the syslog server as the forwarding destination. The existing match list for Panorama will continue to function independently, forwarding all logs as configured.
What does the User-ID agent use to find login and logout events in syslog messages?
A. Syslog Server profile
B. Authentication log
C. Syslog Parse profile
D. Log Forwarding profile
Explanation:
Why This Option?
1.User-ID Agent Syslog Processing:
The User-ID agent monitors syslog messages (e.g., from Active Directory, VPN servers) to extract login/logout events.
To interpret these events, it uses a Syslog Parse Profile, which defines:
Patterns (regex) to match syslog messages.
Fields to extract (e.g., username, IP address).
2.Configuration:
Profiles are configured under:
Device > User Identification > User-ID Agents > [Agent] > Syslog Parse Profile.
Predefined profiles exist for common sources (e.g., Cisco ASA, Windows Security Logs).
Why Not Other Options?
A.Syslog Server profile is for receiving syslog, not parsing.
B.Authentication log is a log type, not a parsing tool.
D.Log Forwarding profile sends logs, doesn’t parse them.
Reference:
Palo Alto User-ID Agent Guide:
"Syslog Parse Profiles map raw syslog messages to IP-user mappings for User-ID."
An engineer decides to use Panorama to upgrade devices to PAN-OS 10.2. Which three platforms support PAN-OS 10.2? (Choose three.)
A. PA-220
B. PA-800 Series
C. PA-5000 Series
D. PA-500
E. PA-3400 Series
Explanation:
Analysis:
PAN-OS 10.2 Support: The compatibility of firewall platforms with a specific PAN-OS version depends on Palo Alto Networks’ hardware and software end-of-life (EOL) policies. PAN-OS 10.2 was released around March 2022, and its support status as of August 2025 would be based on the standard 5-year support period from the initial release date, unless extended or superseded by newer versions (e.g., PAN-OS 11.x).
Upgrade via Panorama: Panorama can push software updates to managed firewalls, but the target platform must be listed as supported for the specified version in the official compatibility matrix or EOL announcements.
Relevant Platforms: The options provided are PA-220, PA-800 Series, PA-5000 Series, PA-500, and PA-3400 Series. We need to identify which three of these are supported for PAN-OS 10.2.
Evaluation of Options:
A. PA-220:
Status: The PA-220 was supported for PAN-OS 10.2 at its release, but an End-of-Sale (EOS) announcement was made on August 1, 2022, with the last supported OS listed as 10.2.x. As of August 2025, support may have ended or be nearing its end (typically 5 years from EOS or first release), but during the active support period, it was compatible. Given the question’s focus on an upgrade to 10.2, it is considered supported if the upgrade occurs within the support window.
Likelihood: Supported, assuming the upgrade is within the support timeline.
B. PA-800 Series:
Status: The PA-800 Series (e.g., PA-820, PA-850) is listed as supporting PAN-OS 10.2 in the compatibility matrix. These platforms are mid-range firewalls designed for branch offices and have ongoing support for 10.2 as of its release date, with no EOL indicated by August 2025 for this version.
Likelihood: Supported.
C. PA-5000 Series:
Status: The PA-5000 Series (e.g., PA-5050, PA-5060) supported PAN-OS 10.2 at its release. However, this series is older, with an EOS announced around 2018, and the last supported OS was likely PAN-OS 9.1 or 10.0, depending on hardware EOL dates. By 2025, support for 10.2 on this series is unlikely unless extended, but during the 10.2 release period, it was compatible.
Likelihood: Marginally supported, but likely phased out by 2025; however, it was supported at 10.2’s release.
D. PA-500:
Status: The PA-500 is an older platform with an EOS announced on October 31, 2018, and the last supported OS was PAN-OS 8.1. PAN-OS 10.2 is not supported on this hardware due to its age and limited capabilities, as confirmed by EOL documentation.
Likelihood: Not supported.
E. PA-3400 Series:
Status: The PA-3400 Series (e.g., PA-3410, PA-3440) was introduced around 2022 and is designed to support newer PAN-OS versions, including 10.2. This series is explicitly listed as compatible with PAN-OS 10.2 in the release notes and datasheets from that period, with ongoing support as of 2025.
Likelihood: Supported.
Selection of Three Platforms:
Based on the compatibility matrix and EOL data up to August 2025, the platforms that support PAN-OS 10.2 include PA-220, PA-800 Series, and PA-3400 Series. The PA-5000 Series may have been supported at 10.2’s release but is likely past its support window by 2025, and the PA-500 is definitively unsupported. Since the question focuses on an upgrade to 10.2 via Panorama, we assume the intent is to identify platforms supported at the time of 10.2’s availability, adjusted for current context.
Final Three: A. PA-220, B. PA-800 Series, and E. PA-3400 Series are the most consistent choices, reflecting a mix of supported platforms from the release period onward.
Conclusion:
The three platforms that support PAN-OS 10.2 for an upgrade via Panorama are PA-220, PA-800 Series, and PA-3400 Series. This selection aligns with the compatibility data and the question’s focus on an upgrade scenario.
References:
Palo Alto Networks Documentation: PAN-OS 10.2 Compatibility Matrix
Palo Alto Networks Documentation: Hardware End-of-Life Dates
ExamTopics PCNSE Discussion: PAN-OS Version Support
A new firewall has the Threat Prevention subscription, but the Antivirus does not appear in Dynamic Updates. What must occur to have Antivirus signatures update?
A. An Antivirus license is needed first, then a Security profile for Antivirus needs to be created.
B. An Antivirus license must be obtained before Dynamic Updates can be downloaded or installed.
C. An Advanced Threat Prevention license is required to see the Dynamic Updates for Antivirus.
D. Install the Application and Threats updates first, then refresh the Dynamic Updates.
Explanation:
1: Recall how Antivirus (AV) updates work
Palo Alto Antivirus signatures (for malware, spyware, C2 traffic) are part of the Threat Prevention subscription.
They are not tied to a separate “Antivirus license” (that doesn’t exist as a standalone).
AV updates depend on Application & Threats content being installed first, because the engine relies on the App-ID/Threat framework to identify traffic.
👉 So if you install Applications and Threats updates, then refresh Dynamic Updates, the Antivirus section appears.
2: Analyze the options
A. An Antivirus license is needed first…
❌ Wrong. There is no separate Antivirus license. Antivirus is included in Threat Prevention.
B. An Antivirus license must be obtained…
❌ Same as A — no such license exists.
C. An Advanced Threat Prevention license is required…
❌ Wrong. ATP (formerly Threat Prevention Cloud/ML-based inline detection) is a different subscription. Antivirus signatures are still part of Threat Prevention.
D. Install the Application and Threats updates first, then refresh the Dynamic Updates.
✅ Correct. This is the required step to make the Antivirus option appear in Dynamic Updates.
🔹 Key Takeaway (for PCNSE)
Threat Prevention subscription includes Antivirus, Anti-Spyware, Vulnerability, and DNS signatures.
No standalone AV license.
Antivirus updates require App+Threats content installed first, otherwise they won’t show.
📖 Reference:
Palo Alto Networks — Content and Threat Signatures
“You must install Applications and Threats content before Antivirus updates can be downloaded.”
When configuring explicit proxy on a firewall, which interface should be selected under the Listening interface option?
A. ingress for the outgoing traffic to the internet
B. Loopback for the proxy
C. Firewall management
D. ingress for the client traffic
Explanation:
Why This Option?
1.Explicit Proxy Basics:
Clients must explicitly configure their browser/OS to use the firewall as a proxy.
The firewall listens on a specific interface for incoming client proxy requests.
2.Listening Interface:
This should be the ingress interface where client traffic arrives (e.g., internal LAN interface).
Clients send HTTP/HTTPS requests directly to this interface’s IP and proxy port (e.g., 8080).
Why Not Other Options?
A.Internet egress is irrelevant—clients don’t send requests there.
B.Loopback is for high availability or complex routing, not client proxy traffic.
C.Management interface is for admin access, not proxy services.
Configuration Example:
If clients are on ethernet1/1, set Listening Interface = ethernet1/1.
Clients point their proxy settings to ethernet1/1’s IP:port.
Reference:
Palo Alto Explicit Proxy Guide:
"The listening interface is where clients direct their explicit proxy requests."
| Page 4 out of 27 Pages |
| Previous |