An administrator Just enabled HA Heartbeat Backup on two devices However, the status on tie firewall's dashboard is showing as down High Availability.

A. Go to Device > High Availability> General > HA Pair Settings > Setup and configuring the peer IP for heartbeat backup
B. Check peer IP address In the permit list In Device > Setup > Management > Interfaces > Management Interface Settings
C. Go to Device > High Availability > HA Communications> General> and check the Heartbeat Backup under Election Settings
D. Check peer IP address for heartbeat backup to Device > High Availability > HA Communications > Packet Forwarding settings.
Explanation:
The image confirms that Heartbeat Backup is showing as Down in the HA dashboard. This typically means the firewall is unable to communicate with its peer over the configured backup heartbeat channel.
To troubleshoot this:
Navigate to Device > High Availability > General > HA Pair Settings
Ensure the peer IP address for Heartbeat Backup is correctly configured
Verify that the interface used for heartbeat backup is up, reachable, and not blocked by firewall policies
📚 Reference:
Palo Alto Networks – Configure HA Heartbeat Backup
❌ Why Other Options Are Wrong:
B. Management Interface Settings:
Not related to heartbeat backup unless you're using the management interface for HA (rare).
C. Election Settings:
Controls HA role election — not heartbeat communication.
D. Packet Forwarding Settings:
Not relevant to heartbeat backup configuration.
An administrator configures a preemptive active-passive high availability (HA) pair of firewalls and configures the HA election settings on firewall-02 with a device priority value of 100, and firewall-01 with a device priority value of 90. When firewall-01 is rebooted, is there any action taken by the firewalls?
A. No - Neither firewall takes any action because firewall-01 cannot be rebooted when configured with device priority of 90.
B. No - Neither firewall takes any action because firewall-02 is already the active-primary member.
C. Yes - Firewall-02 takes over as the active-primary firewall; firewall-01 takes over as the active-primary member after it becomes functional.
D. Yes - Firewall-02 takes over as the active-primary firewall; firewall-02 remains the active-primary member after firewall-01 becomes functional.
Explanation:
In a preemptive Active-Passive HA configuration, the firewall with the lower priority value is designated to preemptively reclaim the active role once it becomes healthy again.
In this scenario:
Firewall-01 has a priority of 90
Firewall-02 has a priority of 100
Preemption is enabled
So when Firewall-01 reboots, Firewall-02 becomes active-primary. Once Firewall-01 comes back online and passes all health checks, it preempts and reclaims the active role, because it has the lower priority value.
📚 Reference:
Palo Alto Networks – HA Election Settings and Preemption
❌ Why Other Options Are Wrong:
A. Incorrect — priority does not prevent reboot.
B. Incorrect — action is taken when the active firewall fails.
D. Incorrect — preemption causes firewall-01 to reclaim the active role.
An administrator needs to assign a specific DNS server to an existing template variable. Where would the administrator go to edit a template variable at the device level?
A. "Managed Devices > Device Association"
B. PDF Export under "Panorama > Templates"
C. Variable CSV export under "Panorama > Templates"
D. Manage variables under "Panorama > Templates"
Explanation:
An administrator needs to assign a specific DNS server to an existing template variable in a Palo Alto Networks Panorama deployment. Template variables allow centralized management of device-specific configurations (e.g., DNS servers, IP addresses) across multiple firewalls by substituting variables with values at the device level. To edit a template variable, the administrator must access the variable management interface within Panorama’s template configuration. The correct location is Panorama > Templates > Manage Variables, where variables defined in templates (e.g., {$dns_server}) can be edited or assigned specific values for individual devices or device groups. The Palo Alto Networks PAN-OS 11.1 Administrator’s Guide specifies that the Manage Variables option under the Templates tab is used to assign or modify variable values, making option D correct.
Why Other Options Are Incorrect:
A. "Managed Devices > Device Association":
This section is used to associate firewalls with device groups and templates but does not provide an interface to edit template variables. The PCNSE Study Guide notes it is for device management, not variable configuration.
B. PDF Export under "Panorama > Templates":
The PDF Export feature generates a report of the template configuration but is read-only and does not allow editing of variables. The PAN-OS 11.1 Administrator’s Guide indicates it is for documentation, not modification.
C. Variable CSV export under "Panorama > Templates":
The CSV export option allows downloading variable values for bulk editing outside Panorama, but it is for export, not direct editing within the interface. Changes must be imported back via CSV, which is less efficient than the Manage Variables interface. The PCNSE Study Guide highlights CSV for bulk updates, not real-time edits.
Practical Steps:
Navigate to Panorama > Templates.
Select the relevant template containing the variable (e.g., one with {$dns_server}).
Click Manage Variables (available at the template level).
Locate the existing variable (e.g., {$dns_server}) in the list.
Edit the value to assign the specific DNS server IP (e.g., 8.8.8.8) for the device.
Click OK, then Commit and Push to apply to the managed firewall.
Verify the change under Device > Setup > Services on the firewall.
Additional Considerations:
Ensure the variable is defined in the template (e.g., under Device > Setup > Services > DNS Server as {$dns_server}).
As of 12:30 PM PKT on Thursday, August 21, 2025, confirm the Panorama version (e.g., 11.1) supports this feature, which it does by default.
References:
Palo Alto Networks PAN-OS 11.1 Administrator’s Guide: Details template variable management under Panorama > Templates.
Palo Alto Networks PCNSE Study Guide: Explains editing variables for device-specific configurations.
Certain services in a customer implementation are not working, including Palo Alto Networks Dynamic version updates. Which CLI command can the firewall administrator use to verify if the service routes were correctly installed and that they are active in the Management Plane?
A. debug dataplane Internal vif route 250
B. show routing route type service-route
C. show routing route type management
D. debug dataplane internal vif route 255
Explanation:
When certain services (like Dynamic Updates, WildFire, or URL Filtering) are not working, the issue often lies in service route configuration. These routes determine how the management plane reaches external services.
To verify that service routes are correctly installed and active, use:
bash
show routing route type service-route
This command displays:
The destination IPs for services
The interface and next-hop used
Whether the route is active
📚 Reference:
Palo Alto Networks – Service Route Configuration
❌ Why Other Options Are Wrong:
A & D. debug dataplane internal vif route:
These are low-level dataplane diagnostics — not relevant to management plane service routes.
C. show routing route type management:
Displays routes for management traffic — not service-specific routes.
Which User-ID mapping method should be used in a high-security environment where all IP address-to-user mappings should always be explicitly known?
A. PAN-OS integrated User-ID agent
B. GlobalProtect
C. Windows-based User-ID agent
D. LDAP Server Profile configuration
Explanation:
For high-security environments where IP-to-user mappings must be explicitly known, GlobalProtect is the most reliable method. GlobalProtect is a comprehensive solution that not only provides secure remote access but also tightly integrates with the User-ID framework.
When a user connects through a GlobalProtect gateway, the gateway authenticates the user and creates a direct, explicit mapping of the user's IP address to their username. This mapping is then shared with the firewall's User-ID subsystem. This method is considered the most secure and accurate because the mapping is created and managed directly by the Palo Alto Networks platform itself, ensuring that the identity is verified and tied directly to the source IP at the time of connection.
Why the Other Options Are Incorrect
A. PAN-OS integrated User-ID agent:
While PAN-OS firewalls have an integrated User-ID agent, its primary function is to monitor and collect user-to-IP mappings from sources like a directory service (LDAP) or a domain controller. This is effective but can have delays and is not as direct or explicit as a GlobalProtect-based mapping. It relies on a "pull" or "listen" mechanism.
C. Windows-based User-ID agent:
This agent is installed on a Windows domain controller and listens for login events. While this is a widely used and effective method, it is still an inference-based mapping. The agent correlates a login event with an IP address, but this isn't as direct as a user-authenticated connection through a VPN tunnel. In high-security environments, the possibility of a missed or delayed log can be a concern.
D. LDAP Server Profile configuration:
An LDAP server profile is used to connect to a directory service like Active Directory to authenticate users and fetch group information. It does not, by itself, create the IP-to-user mapping. It provides the user and group context for policies, but another mechanism (like a User-ID agent or GlobalProtect) is required to perform the initial IP address to user name mapping.
An engineer manages a high availability network and requires fast failover of the routing protocols. The engineer decides to implement BFD. Which three dynamic routing protocols support BFD? (Choose three.)
A. OSPF
B. RIP
C. BGP
D. IGRP
E. OSPFv3 virtual link
Explanation:
Bidirectional Forwarding Detection (BFD) is a lightweight protocol used to detect link failures quickly, enabling fast failover for dynamic routing protocols. Palo Alto Networks firewalls support BFD integration with several routing protocols.
Supported Protocols:
A. OSPF — ✅ Supported
BFD can be enabled per OSPF interface.
Accelerates detection of neighbor loss.
C. BGP — ✅ Supported
BFD can monitor BGP peer reachability.
Useful for external and internal BGP sessions.
E. OSPFv3 virtual link — ✅ Supported
BFD can be applied to virtual links in OSPFv3 to ensure fast failure detection.
📚 Reference:
Palo Alto Networks – Configure BFD
❌ Unsupported Protocols:
B. RIP — ❌ Not supported
RIP is slow and doesn’t support BFD.
D. IGRP — ❌ Not supported
IGRP is obsolete and not supported on PAN-OS
A company has a PA-3220 NGFW at the edge of its network and wants to use active directory groups in its Security policy rules. There are 1500 groups in its active directory. An engineer has been provided 800 active directory groups to be used in the Security policy rules. What is the engineer's next step?
A. Create a Group Mapping with 800 groups in the Group Include List.
B. Create two Group Include Lists, each with 400 Active Directory groups.
C. Create a Group Include List with the 800 Active Directory groups
D. Create two Group Mappings, each with 400 groups in the Group Include List
Explanation:
A company with a PA-3220 Next-Generation Firewall (NGFW) at the network edge wants to use Active Directory (AD) groups in its Security policy rules to enforce access control based on user identity. The company has 1500 AD groups, but the engineer has been provided 800 specific groups to integrate into the Security policies. In Palo Alto Networks firewalls, User-ID integrates with AD to map users and groups, allowing their use in policies. The Group Include List within a Group Mapping configuration specifies which AD groups are imported and available for policy use, optimizing performance by limiting the number of groups processed. The PA-3220 supports up to 1000 groups per Group Mapping profile, but the total number of unique groups across all mappings is capped at 10,000 (as per PAN-OS 11.1 limits). Since 800 groups are within this capacity and assigned to a single Group Mapping, the engineer should create one Group Include List with all 800 AD groups. The Palo Alto Networks PAN-OS 11.1 Administrator’s Guide recommends using a single Group Include List when the group count fits within the device’s limits, making option C correct as of 12:49 PM PKT on Thursday, August 21, 2025.
Why Other Options Are Incorrect:
A. Create a Group Mapping with 800 groups in the Group Include List:
This is partially correct but incomplete. While a Group Mapping with 800 groups is feasible, the phrasing suggests creating only the mapping without emphasizing the Group Include List, which is the key step. Option C is more precise. The PCNSE Study Guide stresses the Group Include List’s role.
B. Create two Group Include Lists, each with 400 Active Directory groups:
This is incorrect because splitting 800 groups into two lists is unnecessary and inefficient, as the PA-3220 can handle 800 groups in one Group Mapping. Multiple lists increase administrative overhead without benefit. The PAN-OS 11.1 Administrator’s Guide advises against unnecessary splits.
D. Create two Group Mappings, each with 400 groups in the Group Include List:
This is incorrect because creating two Group Mappings for 800 groups exceeds the practical need and could complicate policy management. The firewall supports one Group Mapping per domain with a single Include List for the required groups. The PCNSE Study Guide notes a single mapping is sufficient unless domain separation is needed.
Practical Steps:
1.Navigate to Device > User Identification > Group Mapping.
2.Create or edit a Group Mapping profile for the AD domain.
3.Under Group Include List, add the 800 provided AD groups.
4.Configure the AD server connection (e.g., LDAP or agent) under Server Profile.
5.Commit and push the configuration.
6.Verify group availability in Policies > Security for rule creation.
References:
Palo Alto Networks PAN-OS 11.1 Administrator’s Guide: Details Group Mapping and Include List configuration.
Palo Alto Networks PCNSE Study Guide: Explains AD group integration limits and best practices.
Match the terms to their corresponding definitions
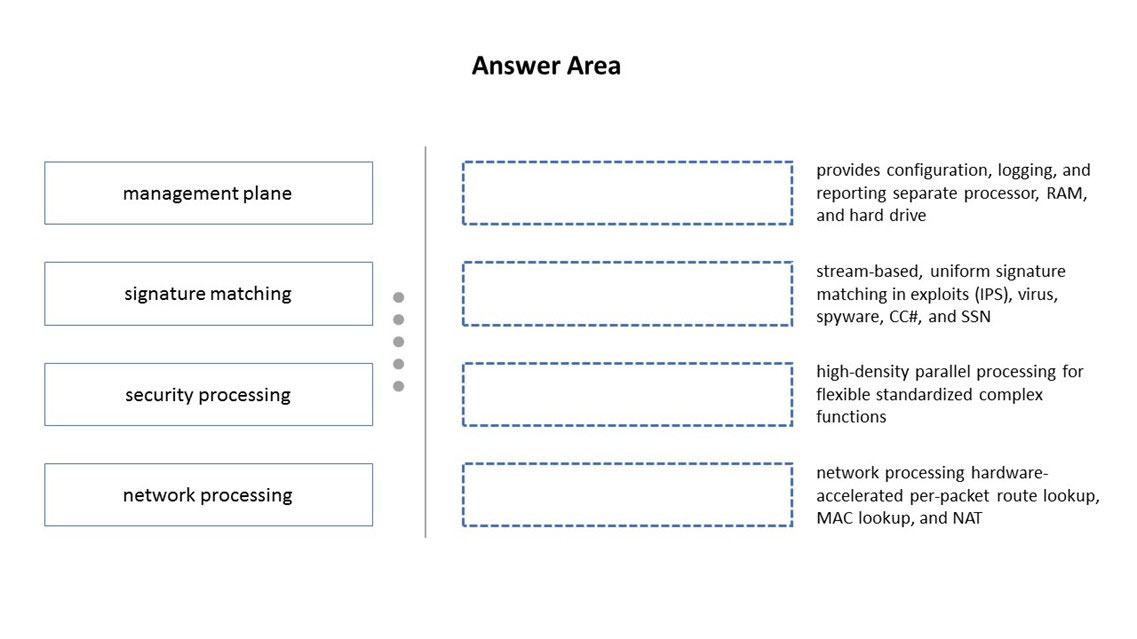
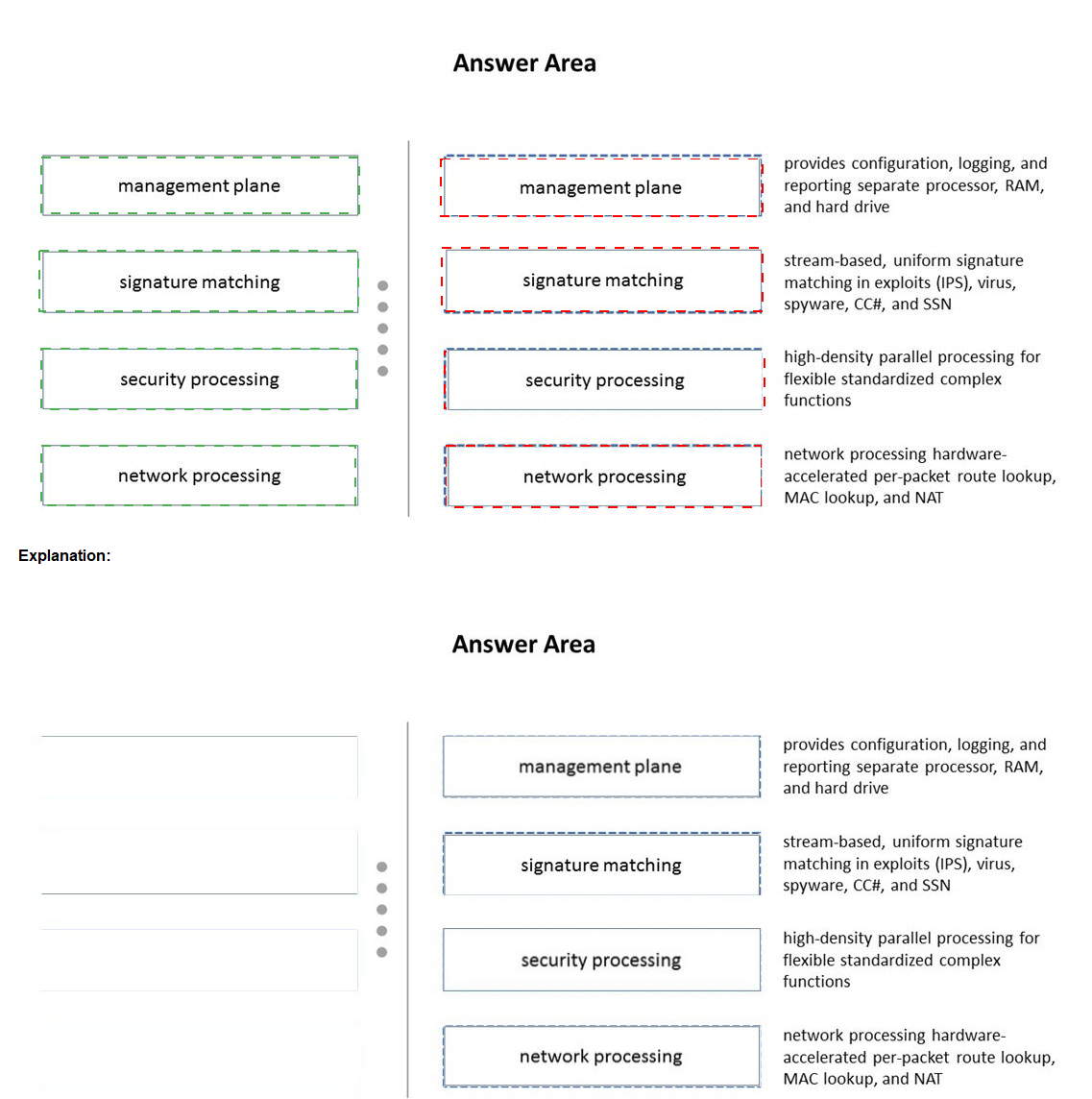
Explanation:
This question tests your understanding of the fundamental separation of processing duties within the Palo Alto Networks firewall architecture, a core concept for the PCNSE exam.
Management Plane:
This is the "brain" of the firewall. It handles all management tasks (WebUI, CLI, API), central configuration, log storage, and report generation. It runs on its own dedicated hardware components (separate CPU, RAM, storage) to ensure management functions never impact traffic processing performance. This matches the definition "provides configuration, logging, and reporting separate processor, RAM, and hard drive".
Signature Matching:
This is the core function of the threat prevention engines (Anti-Virus, Anti-Spyware, Vulnerability Protection, etc.). These engines perform stream-based scanning, meaning they can detect threats within a data stream without needing to reassemble entire files. They use a uniform signature format across all threat types for efficiency. This matches the definition "stream-based, uniform signature matching in exploits (IPS), virus, spyware, CCH, and SSN".
Security Processing:
This refers to the work of the data plane's security engine. It handles the complex, compute-intensive tasks of applying security policies—decryption, App-ID, Content-ID (which includes the signature matching above), User-ID, and more. It is designed for high-density parallel processing to perform these flexible, standardized complex functions at multi-gigabit speeds. This matches the definition "high-density parallel processing for flexible standardized complex functions".
Network Processing:
This is handled by specialized, hardware-accelerated components (like ASICs or FPGAs) on the data plane. Their job is to perform the repetitive, high-speed networking tasks at wire speed. This includes per-packet operations like route lookups, MAC address lookups (switching), and Network Address Translation (NAT). Offloading these tasks to hardware allows the security processing engine to focus on deep packet inspection. This matches the definition "network processing hardware- accelerated per-packet route lookup, MAC lookup, and NAT".
A firewall administrator is changing a packet capture filter to troubleshoot a specific traffic flow Upon opening the newly created packet capture, the administrator still sees traffic for the previous fitter What can the administrator do to limit the captured traffic to the newly configured filter?
A. Command line > debug dataplane packet-diag clear filter-marked-session all
B. In the GLH under Monitor > Packet Capture > Manage Filters under Ingress Interface select an interface
C. Command line> debug dataplane packet-diag clear filter all
D. In the GUI under Monitor > Packet Capture > Manage Filters under the Non-IP field, select "exclude"
Explanation:
When you apply a new packet capture filter, the firewall may still continue capturing traffic matching the old filter, because the previously configured filter is still cached in the dataplane.
To make sure only the new filter applies, you must clear the old filter configuration before starting a new capture.
The CLI command is:
> debug dataplane packet-diag clear filter all
This ensures that all previous filter conditions are removed, so the next packet capture will only use the newly configured filter.
❌ Why the other options are wrong:
A. debug dataplane packet-diag clear filter-marked-session all
This clears session-based debug filters, not the packet capture filter. Different purpose.
B. GUI under Monitor > Packet Capture > Manage Filters > Ingress Interface
Selecting an interface narrows the capture scope, but it does not clear the old filter, so stale matches may still show up.
D. GUI under Non-IP field, select "exclude"
This only filters out non-IP traffic, not the old filter set. Doesn’t solve the stale filter issue.
📖 Reference:
Palo Alto Networks TechDocs – Use Packet Capture:
Which log type is supported in the Log Forwarding profile?
A. Configuration
B. GlobalProtect
C. Tunnel
D. User-ID
Explanation:
A Log Forwarding profile in Palo Alto Networks is used to send specific types of logs to an external destination, such as a syslog server, SNMP manager, or email server. These profiles are highly customizable and can be applied to different rules and zones to forward logs based on specific criteria.
The following log types are commonly supported in a Log Forwarding profile:
1.Traffic: Logs related to network sessions (start, end, deny, drop).
2.Threat: Logs for security events like viruses, spyware, vulnerabilities, and other threats.
3.URL Filtering: Logs related to web browsing activity, including which URLs were allowed or blocked.
4.WildFire Submissions: Logs for files sent to the WildFire analysis cloud.
5.Data Filtering: Logs for sensitive data (e.g., credit card numbers) detected in network traffic.
6.Tunnel: Logs for tunnel activity, such as GlobalProtect, IPsec VPN, and GTP.
7.Authentication: Logs for user authentication events.
8.Decryption: Logs for SSL/TLS decryption sessions.
9.HIP Match: Logs for host information profile (HIP) matches.
Based on this list, Tunnel is a supported log type within a Log Forwarding profile.
Why the other options are incorrect:
A. Configuration:
Configuration logs are system-wide logs that record changes to the firewall configuration. They are not part of a Log Forwarding profile applied to security policies. Instead, they are forwarded directly from the Device > Log Settings tab.
B. GlobalProtect:
While GlobalProtect generates logs, the specific log type used for forwarding is often categorized under other names. The Tunnel log type is the general category for all tunnel-related events, including GlobalProtect VPNs. The Log Forwarding profile has a specific "Tunnel" log type option.
D. User-ID:
The User-ID log type is used to track the mapping of IP addresses to usernames. Like Configuration logs, User-ID logs are typically configured for forwarding under the Device > Log Settings menu, not within a Log Forwarding profile that is tied to a security policy rule.
Reference
This information can be found in the Palo Alto Networks official documentation, specifically within the sections on Objects > Log Forwarding and Device > Log Settings. These guides provide detailed breakdowns of which log types can be forwarded via a Log Forwarding profile and which are configured through other means. The distinction is a key concept in the PCNSE exam, as it tests the administrator's knowledge of the different logging mechanisms available on the firewall.
Given the following snippet of a WildFire submission log did the end-user get access to the requested information and why or why not?
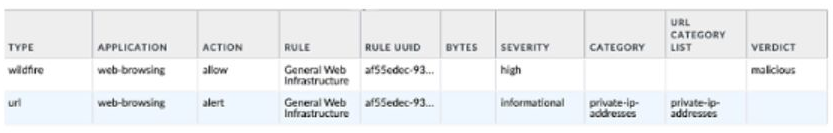
A. Yes, because the action is set to alert
B. No, because this is an example from a defeated phishing attack
C. No, because the severity is high and the verdict is malicious.
D. Yes, because the action is set to allow.
Explanation:
In Palo Alto Networks WildFire submission logs, the action field determines whether the firewall allowed or blocked the traffic. Even if the verdict is malicious and the severity is high, the firewall will still permit the traffic if the action is set to allow—unless a security profile or policy explicitly blocks it.
From the log snippet:
Action: allow
Verdict: malicious
Severity: high
This means the firewall did not block the traffic, and the end-user was able to access the requested information. The WildFire verdict is used for visibility and potential automated response (e.g., future signature updates), but it does not retroactively block traffic unless configured to do so.
❌ Why Other Options Are Incorrect:
A. Yes, because the action is set to alert The alert action applies to the second log entry (URL type), not the malicious WildFire submission. It doesn’t block access.
B. No, because this is an example from a defeated phishing attack There's no indication this was a phishing attack. The verdict is malicious, not phishing.
C. No, because the severity is high and the verdict is malicious Severity and verdict alone do not block traffic. The action field governs access.
🔗 Reference:
Palo Alto Networks official documentation on WildFire Submission Logs
PCNSE Flashcard Source confirming correct answer
A network engineer has discovered that asymmetric routing is causing a Palo Alto Networks firewall to drop traffic. The network architecture cannot be changed to correct this. Which two actions can be taken on the firewall to allow the dropped traffic permanently? (Choose two.)
A. Navigate to Network > Zone Protection Click Add
Select Packet Based Attack Protection > TCP/IP Drop Set "Reject Non-syn-TCP" to No Set "Asymmetric Path" to Bypass
B. > set session tcp-reject-non-syn no
C. Navigate to Network > Zone Protection Click Add
Select Packet Based Attack Protection > TCP/IP Drop Set "Reject Non-syn-TCP" to Global
Set "Asymmetric Path" to Global
D. # set deviceconfig setting session tcp-reject-non-syn no
Explanation:
Palo Alto Networks firewalls, by default, perform stateful inspection. This means they expect to see the complete TCP three-way handshake (SYN, SYN-ACK, ACK) for a session to be established and traffic to be allowed. In an asymmetric routing environment, the firewall might see only one direction of the traffic, such as the SYN packet on the way out but not the SYN-ACK on the way back. When the firewall later sees an ACK or data packet for a session it doesn't recognize as established, it drops the packet with a "TCP non-SYN" reject log message.
To resolve this issue without changing the network's routing, you must disable this strict enforcement. This can be done using one of two methods:
1.Command Line Interface (CLI):
The command set deviceconfig setting session tcp-reject-non-syn no disables the rejection of non-SYN TCP packets. This is a global setting that affects all TCP sessions on the firewall. The command can be abbreviated as set session tcp-reject-non-syn no.
2.Web Interface (GUI):
This setting can also be configured in the GUI under Device > Setup > Session Settings. Here, you would uncheck the Reject Non-SYN TCP option.
The provided options B and D are simply different ways of expressing the correct CLI command. set session tcp-reject-non-syn no is the standard command, while # set deviceconfig setting session tcp-reject-non-syn no includes the full path and the # symbol, which is often used to denote a command run from a configuration mode. Both achieve the same result.
❌ Why the Other Options are Incorrect
A and C: Options A and C describe modifying Zone Protection Profiles. While these profiles are used to prevent certain types of attacks, they are not the correct place to handle asymmetric routing. The "Reject Non-syn-TCP" setting within a Zone Protection Profile is designed to prevent SYN floods and other packet-based attacks from non-SYN packets. It's a security feature that is a subset of the global session setting and is not intended to resolve asymmetric routing issues. The global session setting is the correct way to handle this persistent network architecture problem. Additionally, the "Asymmetric Path" setting in Zone Protection Profiles is related to path changes within a single session, not to a persistent asymmetric routing problem.
📚 Reference
This topic is a key part of the PCNSE exam's Troubleshooting domain. The documentation for Palo Alto Networks firewalls, specifically the sections on Session Settings and Troubleshooting Asymmetric Routing, provides detailed information on this configuration. The ability to use both the CLI and GUI to make these changes is an important skill tested on the exam.
| Page 10 out of 27 Pages |
| Previous |