Topic 5, Misc. Questions
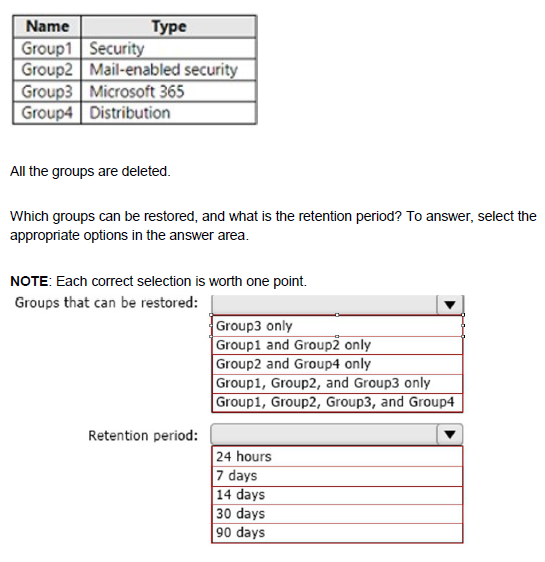
You have a Microsoft 365 E5 subscription that contains the groups shown in the following table.
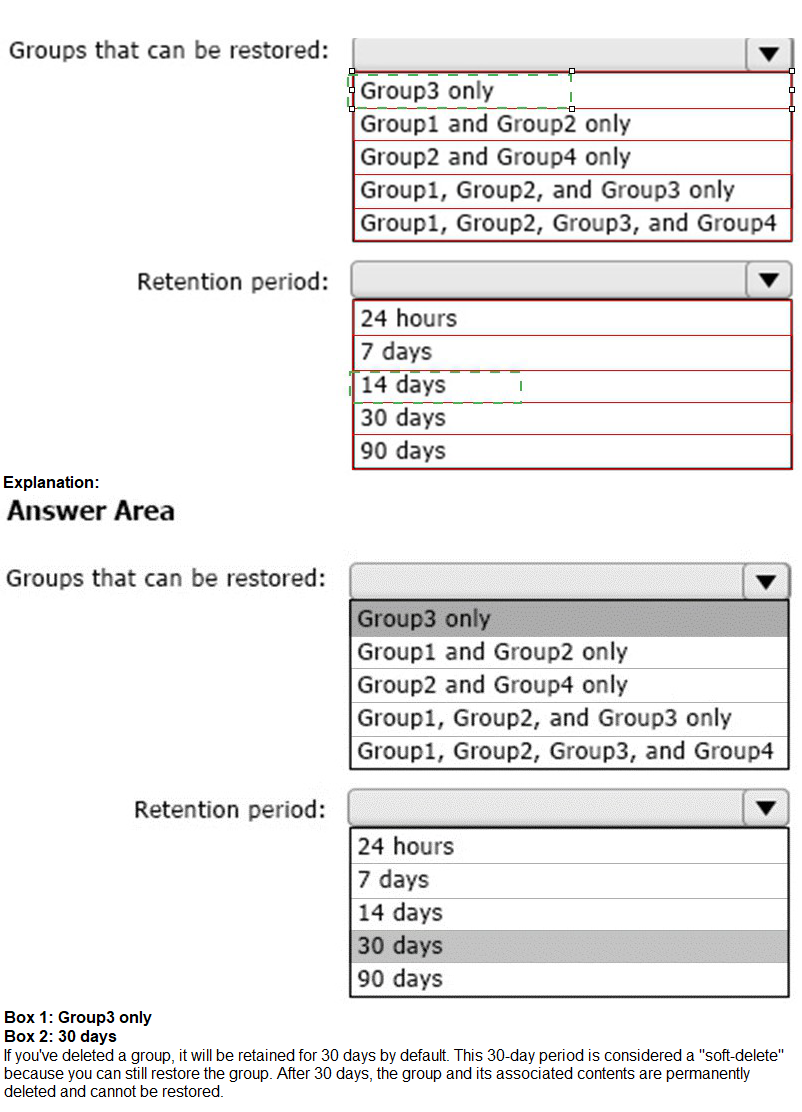
You have a Microsoft 365 tenant.
You create a retention label as shown in the Retention Label exhibit. (Click the Retention Label tab.)
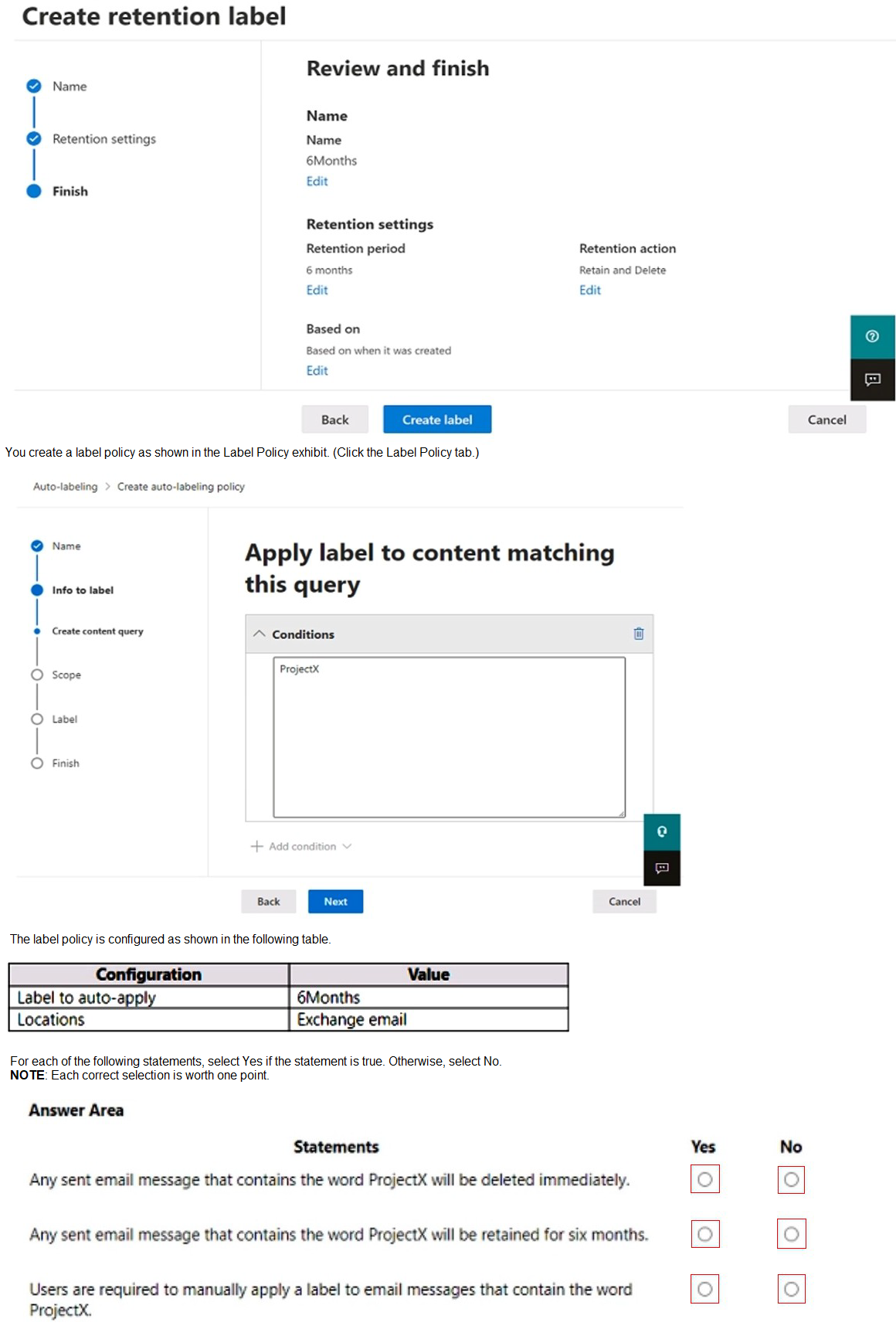
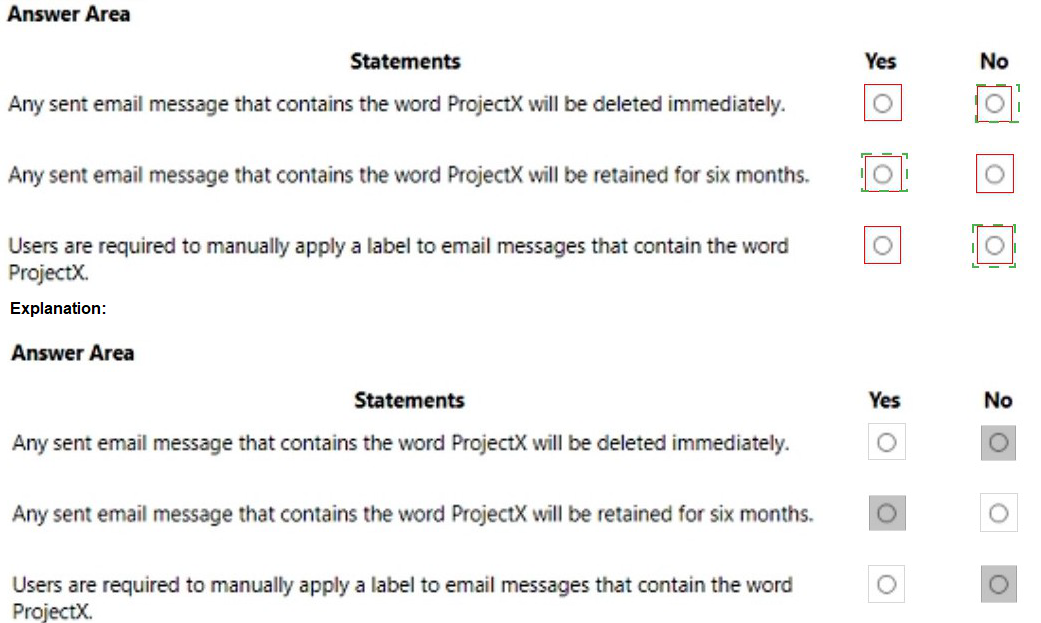
You have a Microsoft 365 subscription. You have a user named User1. You need to ensure that Used can place a hold on all mailbox content. What permission should you assign to User1?
A. the Information Protection administrator ide from the Azure Active Directory admin center.
B. the eDiscovery Manager tote from the Microsoft 365 compliance center.
C. the Compliance Management role from the Exchange admin center.
D. the User management administrator role from the Microsoft 365 admin center.
Explanation:
To allow a user to place a hold on all mailbox content in Microsoft 365, you must assign them a role that provides eDiscovery and hold management permissions.
The correct role for this is the eDiscovery Manager role, which is managed from the Microsoft 365 Compliance Center (also known as the Microsoft Purview portal). This role allows the user to:
Create and man
age Core eDiscovery or Advanced eDiscovery cases.
Place Content Search Holds or Litigation Holds on mailboxes, SharePoint sites, and OneDrive accounts.
Perform content searches across mailboxes and other data sources.
Export search results for legal or compliance investigations.
When a user is assigned the eDiscovery Manager role, they gain the ability to preserve mailbox content by placing items on hold. Items under hold cannot be permanently deleted by users until the hold is removed, ensuring that content remains available for investigations or audits.
This capability meets the requirement to place a hold on all mailbox content, as requested in the question.
Therefore, Option B is correct — assigning the eDiscovery Manager role enables User1 to create and manage holds on mailboxes through the Microsoft 365 compliance portal.
❌ Why Other Options Are Incorrect:
A. Information Protection Administrator (Azure AD admin center) – Incorrect
The Information Protection Administrator role focuses on sensitivity labels, data classification, and information protection policies (like encryption and DLP). It does not grant permissions to perform eDiscovery searches or place content holds on mailboxes. This role primarily handles information labeling and classification within Microsoft Purview, not legal hold or retention actions.
C. Compliance Management role (Exchange admin center) – Incorrect
The Compliance Management role in the Exchange admin center provides access to retention policies, journal rules, and transport rules, but not eDiscovery holds across Microsoft 365 workloads. It is limited to Exchange Online configurations, not organization-wide content holds that extend to SharePoint, OneDrive, or Teams.
Modern compliance holds are managed centrally from the Microsoft 365 compliance center (Purview) using eDiscovery tools, not from Exchange-specific roles.
D. User Management Administrator (Microsoft 365 admin center) – Incorrect
The User Management Administrator role allows management of user accounts, password resets, and group memberships, but has no compliance or eDiscovery permissions. This role is administrative in nature and does not provide the capability to perform content searches or apply holds on mailboxes.
Technical Insight:
Microsoft 365 includes multiple tools for compliance and legal investigations under the Microsoft Purview (Compliance Center):
eDiscovery (Standard): Used for basic content searches and holds.
eDiscovery (Premium): Offers case management, analytics, and export capabilities.
A user assigned the eDiscovery Manager role can:
Create a Core eDiscovery case.
Add mailboxes or Microsoft 365 locations to the case.
Apply a Content Search Hold to preserve data.
Retrieve and export the content if necessary.
By doing so, User1 can ensure that no mailbox data is deleted, altered, or permanently removed while under hold — meeting compliance or legal retention requirements.
Holds can target:
All mailboxes in the organization.
Specific mailboxes, distribution groups, or keywords.
Additional Microsoft 365 content sources (SharePoint Online, OneDrive for Business, Teams messages, etc.).
References:
Microsoft Learn –
Assign eDiscovery permissions in the Microsoft Purview compliance portal
Final Summary:
To allow User1 to place holds on mailbox content across Microsoft 365, assign the eDiscovery Manager role in the Microsoft 365 compliance center.
This role provides full access to eDiscovery tools, enabling the creation and management of content holds and searches across all supported data locations.
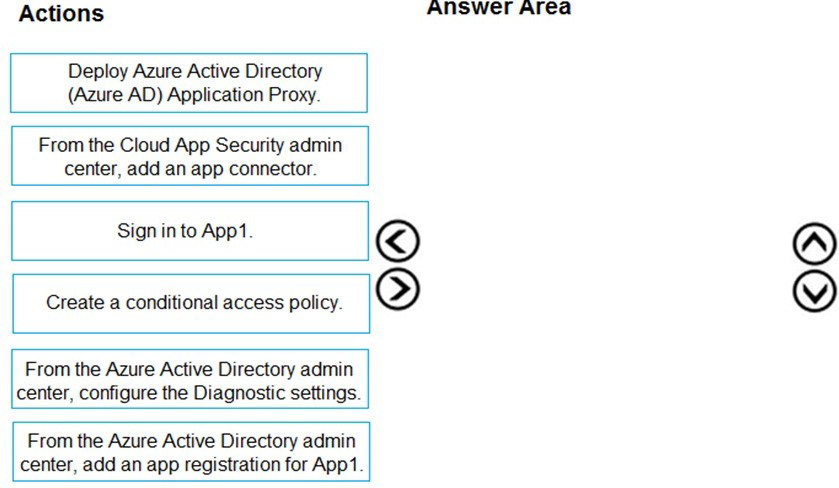
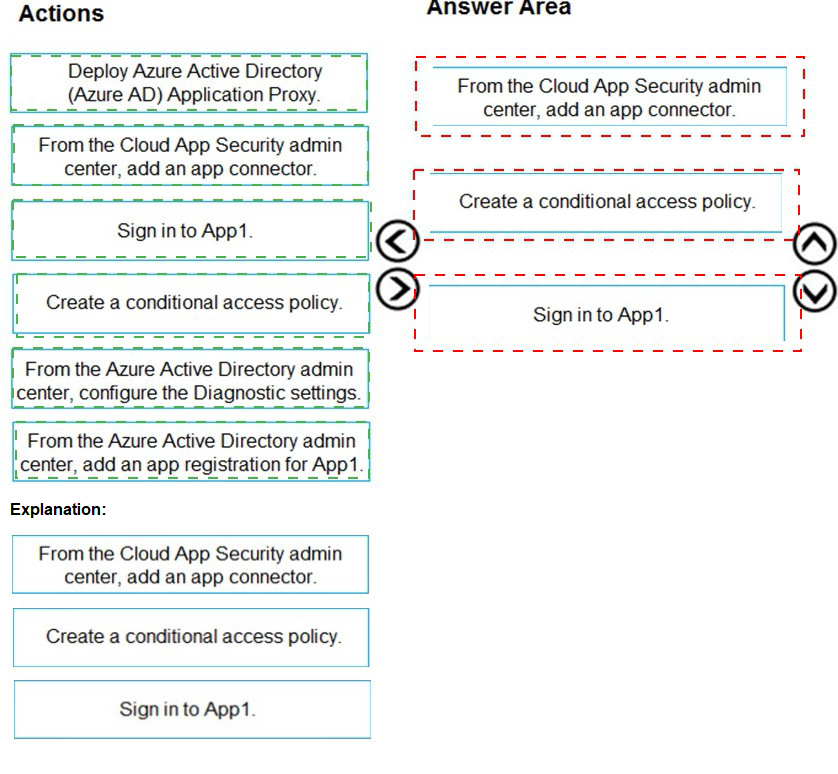
Your company purchases a cloud app named App1.
You need to ensure that you can use Microsoft Cloud App Security to block downloads in App1. App1 supports session controls.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
You have a Microsoft 365 subscription that contains a user named User1.
User1 requires admin access to perform the following tasks:
Manage Microsoft Exchange Online settings.
Create Microsoft 365 groups.
You need to ensure that User1 only has admin access for eight hours and requires approval before the role assignment takes place.
What should you use?
A. zure AD Identity Protection
B. Microsoft Entra Verified ID
C. Conditional Access
D. Azure AD Privileged Identity Management (PJM)
Explanation:
To grant temporary admin access with approval workflow and time-bound role activation, you must use Azure AD Privileged Identity Management (PIM) — now part of Microsoft Entra ID Governance.
User1 needs to:
Manage Exchange Online settings → requires Exchange Administrator role.
Create Microsoft 365 Groups → requires Groups Administrator or User Administrator role.
You want:
Just-in-time (JIT) access for 8 hours
Approval before activation
These requirements are only supported by PIM, which allows:
Time-limited role assignments
Approval workflows
MFA enforcement
Just-in-time elevation
Audit logging
❌ Why Other Options Are Incorrect:
A. Azure AD Identity Protection:
Focuses on risk-based conditional access and identity risk detection (e.g., risky sign-ins). It does not manage role assignments or approvals.
B. Microsoft Entra Verified ID:
Used for decentralized identity verification (e.g., issuing/verifying credentials). It does not control admin roles or access duration.
C. Conditional Access:
Controls access to apps based on conditions (e.g., location, device compliance), but does not manage admin role assignments or approvals.
📘 References:
Privileged Identity Management in Microsoft Entra ID
PIM Role Activation Settings
Microsoft Entra ID Governance Overview
You have a Microsoft 365 subscription.
From Microsoft 365 Defender, you create a role group named US eDiscovery Managers by copying the eDiscovery Manager role group.
You need to ensure that the users in the new role group can only perform content searches of mailbox content for users in the United States.
Solution: From Windows PowerShell, you run the New-complianceSecurityFilter cmdlet with the appropriate parameters.
Does this meet the goal?
A. Yes
B. No
Explanation:
The solution meets the goal. The New-ComplianceSecurityFilter cmdlet is the correct and intended tool to create role-based scoping for compliance-related tasks, such as Content Search and eDiscovery.
Here’s a detailed breakdown of why this solution works:
Understanding the Problem:
By default, members of the "eDiscovery Manager" role group can perform content searches across the entire organization. The goal is to restrict their permissions so they can only search mailboxes belonging to users in the United States.
How the Solution Works:
The New-ComplianceSecurityFilter cmdlet is specifically designed to apply filters to compliance roles.
You can create a filter that links to the "US eDiscovery Managers" role group.
The filter's parameters would specify the scope of their access. In this case, you would use the -Filter parameter with a condition like "Location -eq 'United States'" or, more technically, you would target a specific list of US users or a -Region parameter if applicable in your directory structure.
When a member of the "US eDiscovery Managers" group runs a Content Search, the filter is automatically applied in the background. The search results will only include content from the mailboxes defined in the filter's scope, effectively limiting them to US users.
Why This is the Correct Approach:
This method does not change the fundamental permissions of the role group (they still have the "Compliance Search" and "Case Management" roles).
Instead, it adds a security boundary that transparently filters all their search queries, perfectly meeting the requirement of providing access only to a specific subset of data.
Reference:
Microsoft Documentation:
New-Compliance Security Filter
The official documentation for this cmdlet states its purpose is to "create compliance security filters that define which mailboxes your eDiscovery managers can search." This aligns directly with the goal of the scenario.
Key Takeaway:
When you need to restrict the scope of data that a user with compliance permissions (like Content Search, eDiscovery, or Audit Log access) can see or search, you use Compliance Security Filters via the *-ComplianceSecurityFilter PowerShell cmdlets. This is a more precise and secure method than trying to split permissions by creating new role groups alone.
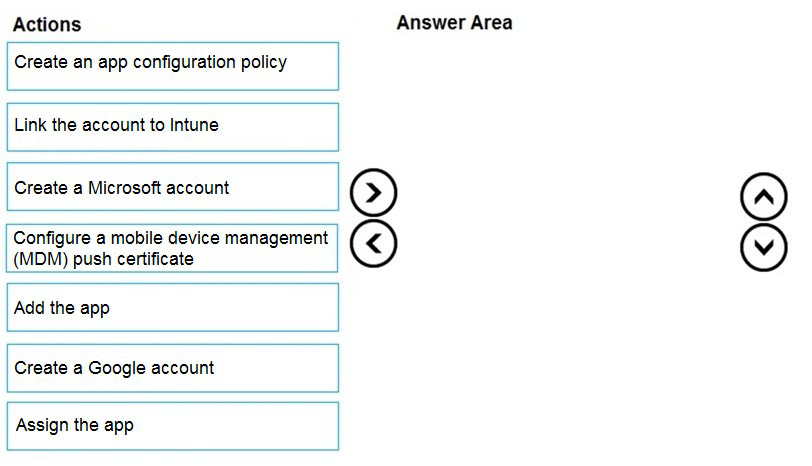
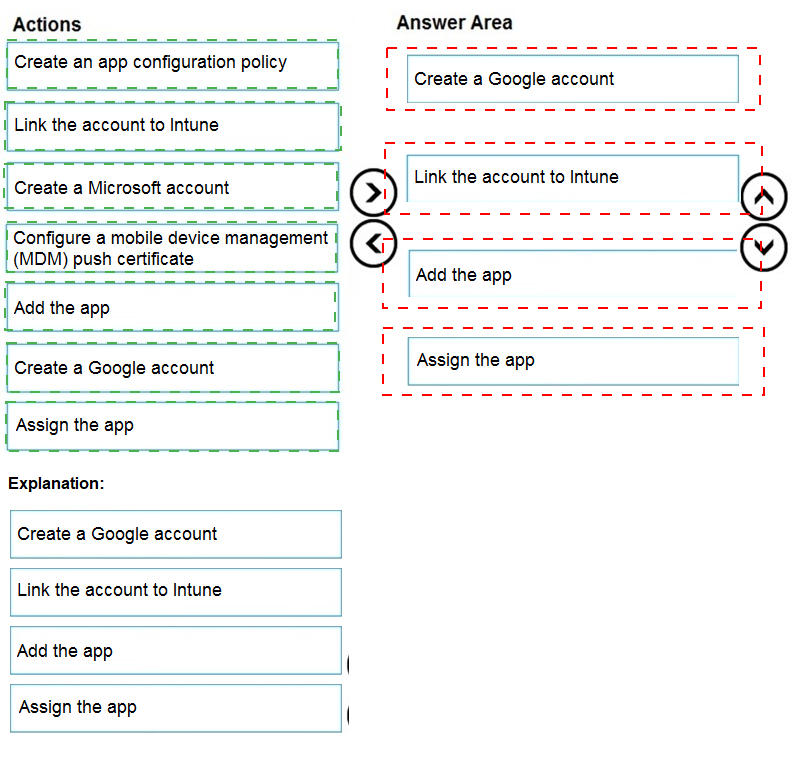
You have a Microsoft 365 E5 tenant that contains 500 Android devices enrolled in Microsoft Intune. You need to use Microsoft Endpoint Manager to deploy a managed Google Play app to the devices.
Which four actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
You have a Microsoft 365 tenant that contains devices enrolled in Microsoft Intune. The devices are configured as shown in the following table.
You plan to perform the following device management tasks in Microsoft Endpoint
Manager:
Deploy a VPN connection by using a VPN device configuration profile.
Configure security settings by using an Endpoint Protection device configuration profile.
You support the management tasks.
What should you identify? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
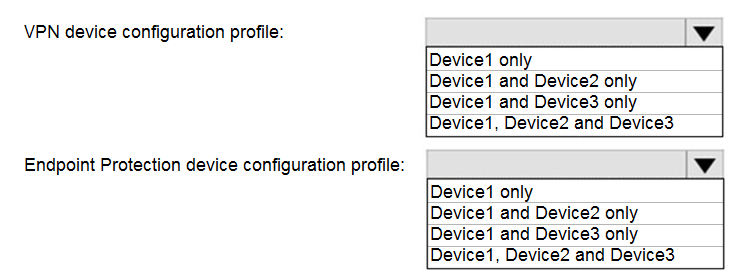
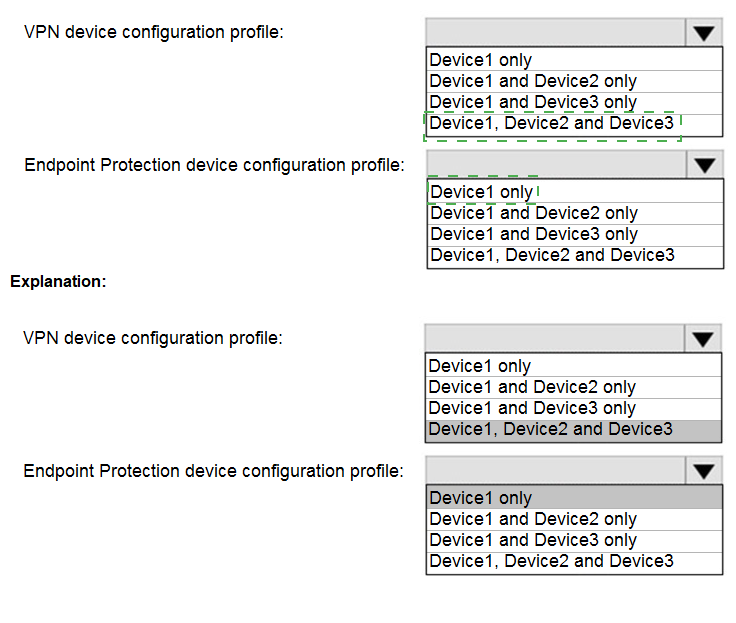
Explanation:
You have an Azure AD tenant and a Microsoft 365 E5 subscription. The tenant contains the users shown in the following table.
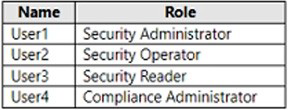
You plan to implement Microsoft Defender for Endpoint.
You verify that role-based access control (RBAC) is turned on in Microsoft Defender for Endpoint.
You need to identify which user can view security incidents from the Microsoft 365 Defender portal.
Which user should you identify?
A. User1
B. User2
C. User3
D. User4
Explanation:
With RBAC enabled in Microsoft Defender for Endpoint, access to the Microsoft 365 Defender portal (security.microsoft.com) for viewing security incidents is controlled by assigned permissions. Security incidents are aggregated in the Incidents & alerts section, and read access requires at least Security Reader permissions across relevant workloads (e.g., Defender for Endpoint).
User1 (Security Administrator): Can view and manage security incidents, as this Entra ID role grants full read/write access to security data in the Defender portal, including incidents, alerts, and investigations.
Why Other Options Are Incorrect:
B. User2 (Security Operator): Can view and remediate incidents but is typically for operational tasks; however, in standard Entra RBAC mappings, it may not grant full incident visibility without additional Defender-specific roles (e.g., Viewer).
C. User3 (Security Reader): Has read-only access to security data but lacks explicit permissions to view aggregated incidents in the Defender portal under RBAC; limited to basic alerts/devices.
D. User4 (Compliance Administrator): Focused on compliance/eDiscovery; no access to security incidents or Defender for Endpoint data.
References:
Map Microsoft Defender XDR Unified RBAC permissions – Details Entra roles like Security Administrator granting incident access.
Assign roles and permissions – Security Reader has read-only access but notes limitations on incidents/devices.
You need to notify the manager of the human resources department when a user in the department shares a file or folder from the departments Microsoft SharePoint Online site. What should you do?
A. From the SharePoint Online site, create an alert.
B. From the SharePoint Online admin center, modify the sharing settings.
C. From the Microsoft 365 Defender portal, create an alert policy.
D. From the Microsoft Purview compliance portal, create a data loss prevention (DLP) policy.
Explanation:
To automatically notify someone (in this case, the HR manager) whenever a user shares a file or folder from SharePoint Online, the best solution is to create an alert policy in the Microsoft 365 Defender portal.
An alert policy monitors user and admin activities across Microsoft 365 services, including SharePoint Online, OneDrive for Business, Exchange Online, and Teams. You can configure a policy to trigger alerts when specific actions occur — such as file sharing, permission changes, or access to sensitive content — and send notifications to designated recipients.
How it works:
The alert policy watches for specific activity events (e.g., “Shared file externally” or “Shared file internally”).
When an activity matches the defined condition, the policy automatically:
Generates an alert in the Microsoft 365 Defender portal.
Sends an email notification to selected recipients (such as the HR manager).
The alert includes event details such as the user who shared the file, the target file or folder, the time of action, and whether sharing was internal or external.
This meets the exact requirement in the question: notify the HR manager when a file or folder is shared.
Configuration steps
Go to the Microsoft 365 Defender portal: https://security.microsoft.com
.
In the left pane, select Alerts → Alert policies → New alert policy.
Set the following:
Activity: “Shared file, folder, or site externally or internally.”
Service: SharePoint Online.
Users to monitor: Users in the HR department (or the HR SharePoint site).
Recipients: HR manager email address.
Severity and category as needed.
Save and enable the policy.
Once enabled, any time someone in HR shares a document, the manager receives an immediate alert notification.
Why Option C Is Correct
Provides real-time monitoring of sharing events.
Allows customized email notifications to specific users or administrators.
Integrates with the Microsoft 365 unified audit log, ensuring all sharing actions are captured.
Specifically designed for security and compliance alerts across Microsoft 365 workloads.
Thus, creating an alert policy in the Microsoft 365 Defender portal fulfills the requirement effectively.
❌ Why Other Options Are Incorrect
A. From the SharePoint Online site, create an alert – Incorrect
A SharePoint site alert (created through “Alert Me” in a document library) only notifies users about content changes like file edits, deletions, or additions.
It does not monitor or report sharing actions. Alerts at the site or library level can notify when an item is modified but not when a user shares a file with someone.
B. From the SharePoint Online admin center, modify the sharing settings – Incorrect
Modifying sharing settings controls who can share and how sharing occurs (e.g., allowing or blocking external sharing). It does not send notifications when sharing events happen.
This option manages permissions and restrictions, not alerts or monitoring.
D. From the Microsoft Purview compliance portal, create a DLP policy – Incorrect
A Data Loss Prevention (DLP) policy monitors content for sensitive information (like credit card numbers or personal data) and prevents it from being shared or leaked.
DLP can restrict sharing or block access but it does not generate notifications for general file-sharing activities unless sensitive data is involved.
In this scenario, the goal is to notify the HR manager whenever any sharing occurs, not to block or classify sensitive data.
References
Microsoft Learn –
Create and manage alert policies in the Microsoft 365 Defender portal
Your company has a Microsoft E5 tenant.
The company must meet the requirements of the ISO/IEC 27001:2013 standard.
You need to assess the company’s current state of compliance.
What should you use?
A. eDiscovery
B. Information governance
C. Compliance Manager
D. Data Subject Requests (DSRs)
Explanation:
Microsoft Compliance Manager is the dedicated tool within the Microsoft 365 compliance center designed specifically for this purpose: assessing and managing your organization's compliance with regulatory standards and data protection laws.
Here’s why it is the correct choice:
Purpose-Built for Compliance Assessment: Compliance Manager provides a compliance score and a detailed dashboard that helps you assess your current compliance posture against various standards, including ISO/IEC 27001:2013.
Pre-built Assessments: It includes pre-configured templates for common regulations and standards. You can select the ISO 27001 assessment template, which will list all the required controls from the standard.
Shared Responsibility Model: It clearly delineates Microsoft's actions to implement controls (which you get automatically) and the improvement actions that your organization must perform. This allows you to see exactly where your company stands in meeting the requirements of the standard.
Why the other options are incorrect:
A. eDiscovery:
This is a tool for identifying, holding, and exporting content for legal cases and investigations. It is not used for broad compliance assessment against international standards.
B. Information governance:
This is a set of features (like retention labels and policies) used to manage the lifecycle of your data (how long to keep it, when to delete it). While crucial for meeting specific aspects of a standard, it is not a tool for performing an overall compliance assessment.
D. Data Subject Requests (DSRs):
This refers to the process of finding and acting on personal data in response to requests from individuals (like the "right to be forgotten" under GDPR). It is a specific action for data privacy regulations, not a tool for assessing overall compliance with ISO 27001.
Reference:
Microsoft Docs: Microsoft Compliance Manager
The documentation states: "Compliance Manager can help you throughout your compliance journey... assess your compliance posture by providing a risk-based compliance score... [and] built-in templates for common regional and industry standards, such as ISO 27001."
Key Takeaway:
When you need to measure, track, and assess your organization's adherence to a specific compliance standard or regulation, you use Compliance Manager.
You have a Microsoft 365 tenant.
You plan to implement Endpoint Protection device configuration profiles.
Which platform can you manage by using the profile?
A. Ubuntu Linux
B. macOS
C. iOS
D. Android
Explanation:
An Endpoint Protection device configuration profile in Microsoft Intune is specifically designed to manage core operating system security features. The available settings are platform-specific.
Here’s a breakdown of what this profile type manages and why macOS is the correct answer:
macOS: The Endpoint Protection profile for macOS allows you to configure a wide range of native macOS security settings, including:
macOS Firewall settings (incoming connections, stealth mode).
Gatekeeper (allowing apps downloaded from specific locations).
FileVault disk encryption.
Password policies (like complexity and expiration).
Why the other options are incorrect:
A. Ubuntu Linux:
Intune does not have a dedicated "Endpoint Protection" profile type for Linux distributions like Ubuntu. Linux device management in Intune is primarily focused on compliance policies and custom configuration profiles (using scripts or settings catalogs), not a pre-defined, consolidated Endpoint Protection template.
C. iOS:
For iOS (and iPadOS), security settings like passcode requirements and device restrictions are configured using a Device Restrictions profile, not an "Endpoint Protection" profile. The "Endpoint Protection" profile type is not available for the iOS platform in Intune.
D. Android:
Similar to iOS, core security settings for Android Enterprise devices are managed through Device Restrictions profiles or dedicated Device Owner profiles. The "Endpoint Protection" profile type is not used for Android.
Reference:
Microsoft Docs: Endpoint protection settings for macOS in Intune
This documentation explicitly lists the settings you can configure using an Endpoint Protection profile for macOS, confirming it is the intended platform for this specific profile type.
Key Takeaway:
The "Endpoint Protection" device configuration profile in Intune is primarily for configuring native OS security features on Windows 10/11 and macOS devices. For mobile platforms like iOS and Android, you use Device Restrictions profiles.
| Page 1 out of 26 Pages |