What is the initial step performed by FortiGate when handling the first packets of a session?
A. Installation of the session key in the network processor (NP)
B. Data encryption and decryption
C. Security inspections such as ACL, HPE, and IP integrity header checking
D. Offloading the packets directly to the content processor (CP)
Refer to the exhibit, which contains a partial command output.

The administrator has configured BGP on FortiGate. The status of this new BGP
configuration is shown in the exhibit.
What configuration must the administrator consider next?
A. Configure a static route to 100.65.4.1.
B. Configure the local AS to 65300.
C. Contact the remote peer administrator to enable BGP
D. Enable ebgp-enforce-multihop.
An administrator is extensively using VXLAN on FortiGate.
Which specialized acceleration hardware does FortiGate need to improve its performance?
A. NP7
B. SP5
C. 9
D. NTurbo
Refer to the exhibit, which shows the FortiGuard Distribution Network of a FortiGate device.
FortiGuard Distribution Network on FortiGate
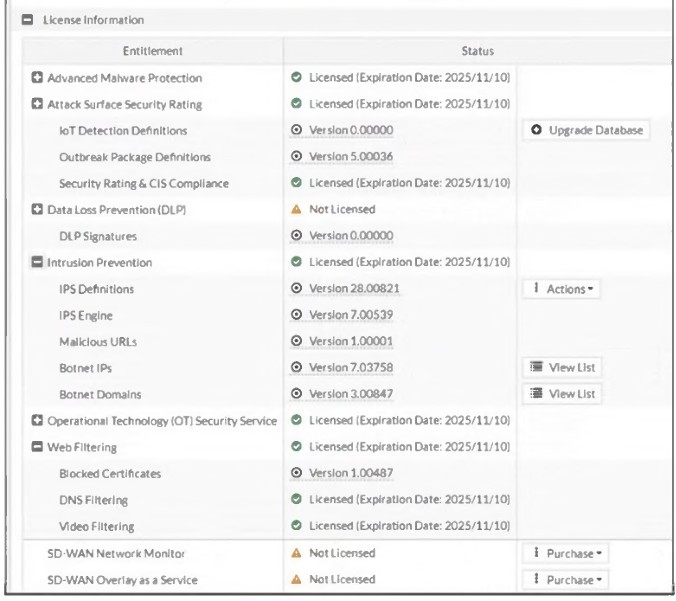
An administrator is trying to find the web filter database signature on FortiGate to resolve
issues with websites not being filtered correctly in a flow-mode web filter profile.
Why is the web filter database version not visible on the GUI, such as with IPS definitions?
A. The web filter database is stored locally, but the administrator must run over CLI diagnose autoupdate versions.
B. The web filter database is stored locally on FortiGate, but it is hidden behind the GUI. It requires enabling debug mode to make it visible.
C. The web filter database is not hosted on FortiGate: FortiGate queries FortiGuard or FortiManager for web filter ratings on demand.
D. The web filter database is only accessible after manual syncing with a valid FDS server using diagnose test update info.
What does the command set forward-domain
A. It configures the interface to prioritize traffic based on the domain ID, enhancing quality of service for specified VLANs.
B. It isolates traffic within a specific VLAN by assigning a broadcast domain to an interface based on the VLAN ID.
C. It restricts the interface to managing traffic only from the specified VLAN, effectively segregating network traffic.
D. It assigns a unique domain ID to the interface, allowing it to operate across multiple VLANs within the same VDOM.
Refer to the exhibit, which contains a partial VPN configuration.

What can you conclude from this VPN IPsec phase 1 configuration?
A. This configuration is the best for networks with regular traffic intervals, providing a balance between connectivity assurance and resource utilization.
B. Peer IDs are unencrypted and exposed, creating a security risk.
C. FortiGate will not add a route to its routing or forwarding information base when the dynamic tunnel is negotiated.
D. A separate interface is created for each dial-up tunnel, which can be slower and more resource intensive, especially in large networks.
Refer to the exhibit, which shows a network diagram showing the addition of site 2 with an
overlapping network segment to the existing VPN IPsec connection between the hub and
site 1.
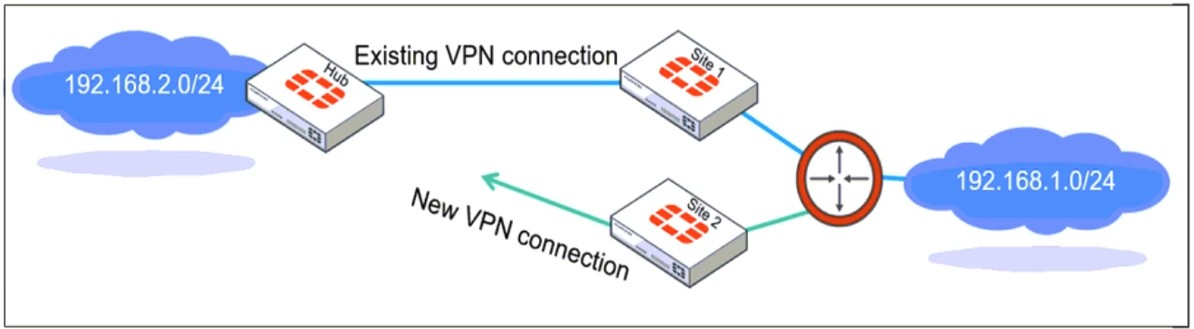
Which IPsec phase 2 configuration must an administrator make on the FortiGate hub to
enable equal-cost multi-path (ECMP) routing when multiple remote sites connect with
overlapping subnets?
A. Set route-overlap to either use-new or use-old
B. Set net-device to ecmp
C. Set single-source to enable
D. Set route-overlap to allow
An administrator must minimize CPU and RAM use on a FortiGate firewall while also enabling essential security features, such as web filtering and application control for HTTPS traffic. Which SSL inspection setting helps reduce system load while also enabling security features, such as web filtering and application control for encrypted HTTPS traffic?
A. Use full SSL inspection to thoroughly inspect encrypted payloads.
B. Disable SSL inspection entirely to conserve resources.
C. Configure SSL inspection to handle HTTPS traffic efficiently.
D. Enable SSL certificate inspection mode to perform basic checks without decrypting traffic.
Refer to the exhibit, which shows a partial troubleshooting command output.
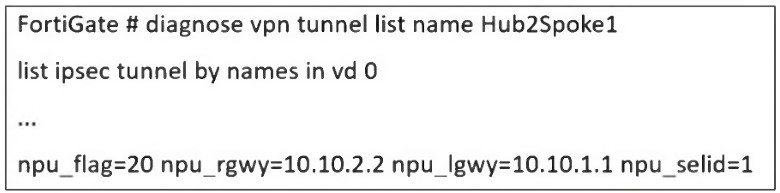
An administrator is extensively using IPsec on FortiGate. Many tunnels show information
similar to the output shown in the exhibit.
What can the administrator conclude?
A. IPsec SAs cannot be offloaded.
B. The two IPsec SAs, inbound and outbound, are copied to the NPU.
C. Only the outbound IPsec SA is copied to the NPU.
D. Only the inbound IPsec SA is copied to the NPU.
What action can be taken on a FortiGate to block traffic using IPS protocol decoders, focusing on network transmission patterns and application signatures?
A. Use the DNS filter to block application signatures and protocol decoders.
B. Use application control to limit non-URL-based software handling.
C. Enable application detection-based SD-WAN rules.
D. Configure a web filter profile in flow mode.
A vulnerability scan report has revealed that a user has generated traffic to the website example.com (10.10.10.10) using a weak SSL/TLS version supported by the HTTPS web server. What can the firewall administrator do to block all outdated SSL/TLS versions on any HTTPS web server to prevent possible attacks on user traffic?
A. Configure the unsupported SSL version and set the minimum allowed SSL version in the HTTPS settings of the SSL/SSH inspection profile.
B. Enable auto-detection of outdated SSL/TLS versions in the SSL/SSH inspection profile to block vulnerable websites.
C. Install the required certificate in the client's browser or use Active Directory policies to block specific websites as defined in the SSL/SSH inspection profile.
D. Use the latest certificate, Fortinet_SSL_ECDSA256, and replace the CA certificate in the SSL/SSH inspection profile.
Refer to the exhibit, which shows the HA status of an active-passive cluster.
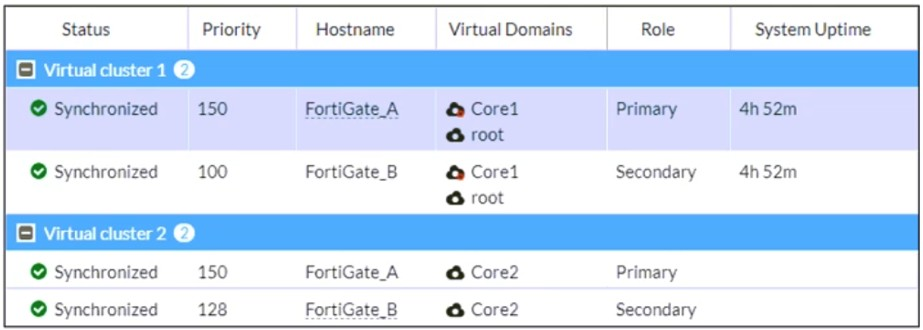
An administrator wants FortiGate_B to handle the Core2 VDOM traffic.
Which modification must the administrator apply to achieve this?
A. The administrator must disable override on FortiGate_A.
B. The administrator must change the priority from 100 to 160 for FortiGate_B.
C. The administrator must change the load balancing method on FortiGate_B.
D. The administrator must change the priority from 128 to 200 for FortiGate_B.
| Page 1 out of 5 Pages |