You have configured an application control profile, set peer-to-peer traffic to Block under
the Categories tab, and applied it to the firewall policy. However, your peer-to-peer traffic
on known ports is passing through the FortiGate without being blocked.
What FortiGate settings should you check to resolve this issue?
A. FortiGuard category ratings
B. Application and Filter Overrides
C. Network Protocol Enforcement
D. Replacement Messages for UDP-based Applications
Refer to the exhibit, which shows a partial configuration from the remote authentication
server.
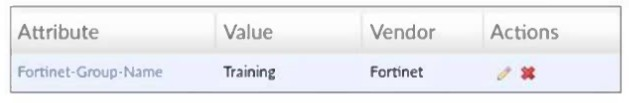
Why does the FortiGate administrator need this configuration?
A. To set up a RADIUS server Secret.
B. To authenticate Any FortiGate user groups.
C. To authenticate and match the Training OU on the RADIUS server.
D. To authenticate only the Training user group.
Refer to the exhibit, which contains a RADIUS server configuration.
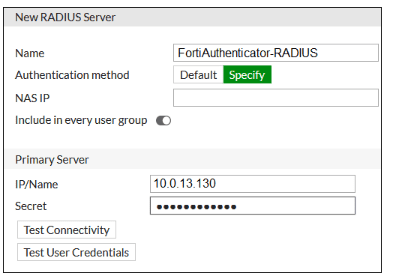
An administrator added a configuration for a new RADIUS server. While configuring, the
administrator enabled Include in every user group.
What is the impact of enabling Include in every user group in a RADIUS configuration?
A. This option places the RADIUS server, and all users who can authenticate against that server, into every FortiGate user group.
B. This option places the RADIUS server, and all users who can authenticate against that server, into every RADIUS group.
C. This option places all users into every RADIUS user group, including groups that are used for the LDAP server on FortiGate.
D. This option places all FortiGate users and groups required to authenticate into the RADIUS server, which, in this case, is FortiAuthenticator.
Refer to the exhibit.
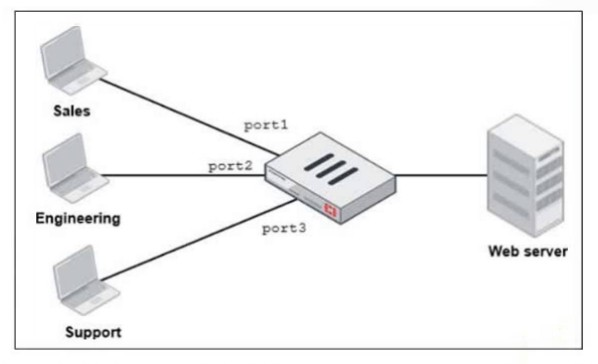
FortiGate has two separate firewall policies for Sales and Engineering to access the same
web server with the same security profiles.
Which action must the administrator perform to consolidate the two policies into one?
A. Create an Aggregate interface that includes port1 and port2 to create a single firewall policy.
B. Select port1 and port2 subnets in a single firewall policy.
C. Replace port1 and port2 with the any interface in a single firewall policy.
D. Enable Multiple Interface Policies to select port1 and port2 in the same firewall policy.
Refer to the exhibit.
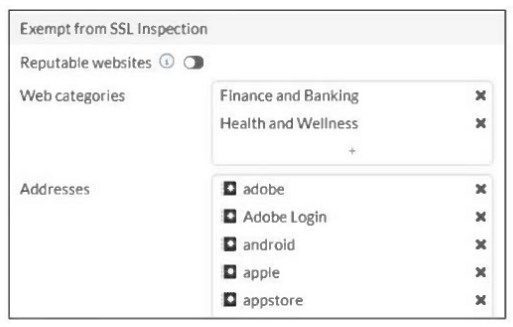
The predefined deep-inspection and custom-deep-inspection profiles exclude some web
categories from SSL inspection, as shown in the exhibit.
For which two reasons are these web categories exempted? (Choose two.)
A. The FortiGate temporary certificate denies the browser’s access to websites that use HTTP Strict Transport Security.
B. These websites are in an allowlist of reputable domain names maintained by FortiGuard.
C. The resources utilization is optimized because these websites are in the trusted domain list on FortiGate.
D. The legal regulation aims to prioritize user privacy and protect sensitive information for these websites.
Refer to the exhibits.
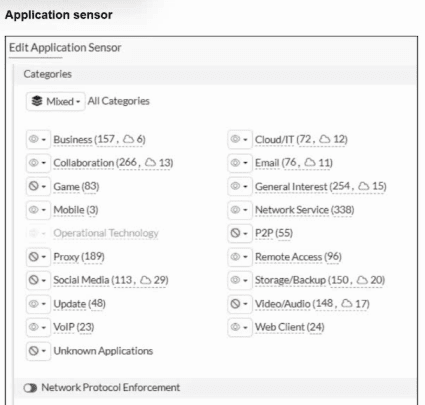
You have implemented the application sensor and the corresponding firewall policy as
shown in the exhibits.
Which two factors can you observe from these configurations? (Choose two.)
A. YouTube search is allowed based on the Google Application and Filter override settings.
B. YouTube access is blocked based on Excessive-Bandwidth Application and Filter override settings.
C. Facebook access is allowed but you cannot play Facebook videos based on Video/Audio category filter settings.
D. Facebook access is blocked based on the category filter settings.
Refer to the exhibit, which shows an SD-WAN zone configuration on the FortiGate GUI.
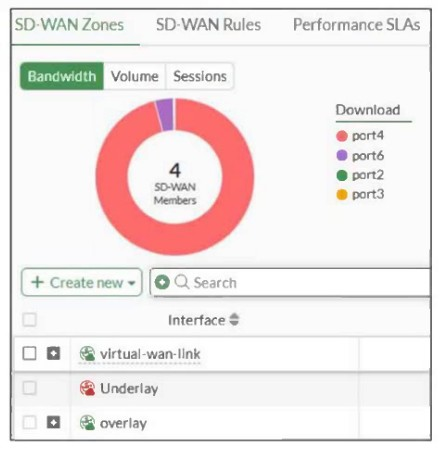
Based on the exhibit, which statement is true?
A. The Underlay zone is the zone by default.
B. The Underlay zone contains no member.
C. port2 and port3 are not assigned to a zone.
D. The virtual-wan-link and overlay zones can be deleted.
Which two statements about the Security Fabric rating are true? (Choose two.)
A. A license is required to obtain an executive summary in the Security Rating section.
B. The root FortiGate provides executive summaries of all the FortiGate devices in the Security Fabric.
C. The Security Posture category provides PCI compliance results.
D. Security Rating Insights are available only in the Security Rating page.
Refer to the exhibit.
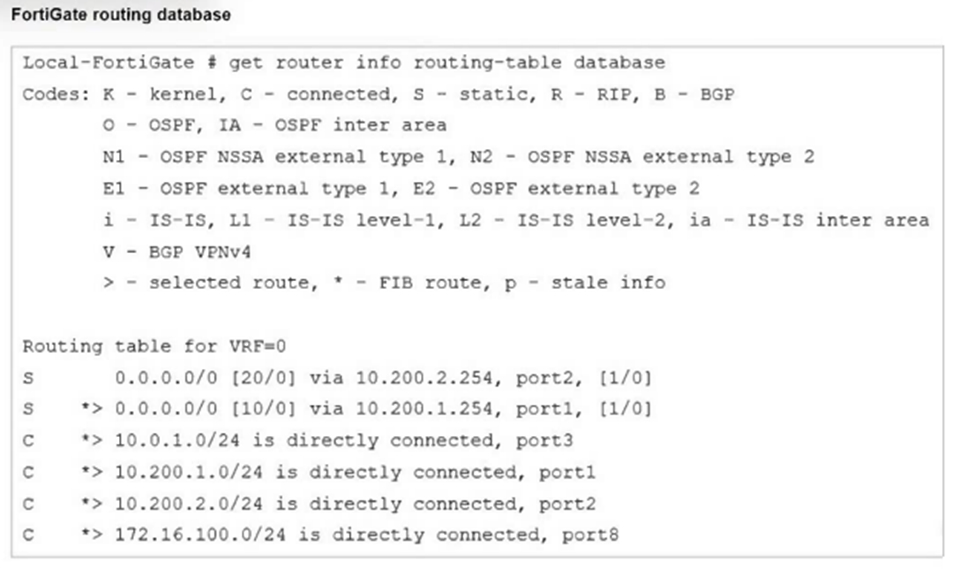
Which two statements are true about the routing entries in this database table? (Choose
two.)
A. All of the entries in the routing database table are installed in the FortiGate routing table.
B. The port2 interface is marked as inactive.
C. Both default routes have different administrative distances.
D. The default route on port2 is marked as the standby route.
Which statement correctly describes NetAPI polling mode for the FSSO collector agent?
A. The collector agent uses a Windows API to query DCs for user logins.
B. NetAPI polling can increase bandwidth usage in large networks.
C. The NetSessionEnum function is used to track user logouts.
D. The collector agent must search Windows application event logs.
Which three pieces of information does FortiGate use to identify the hostname of the SSL server when SSL certificate inspection is enabled? (Choose three.)
A. The host field in the HTTP header.
B. The server name indication (SNI) extension in the client hello message.
C. The subject alternative name (SAN) field in the server certificate.
D. The subject field in the server certificate.
E. The serial number in the server certificate.
You are encountering connectivity problems caused by intermediate devices blocking
IPsec traffic.
In which two ways can you effectively resolve the problem? (Choose two.)
A. You should use the protocol IKEv2.
B. You can use SSL VPN tunnel mode to prevent problems with blocked ESP and UDP ports (500 or 4500).
C. You can configure a hub-and-spoke topology with SSL VPN tunnels to bypass blocked UDP ports.
D. You can turn on fragmentation to fix large certificate negotiation problems.
| Page 1 out of 6 Pages |