Which two third-party tools can an administrator use to deploy FortiClient? (Choose two.)
A. Microsoft Windows Installer
B. Microsoft SCCM
C. Microsoft Active Directory GPO
D. QR code generator
Explanation:
📘 Question Summary
This question evaluates administrators' understanding of enterprise-scale FortiClient deployment strategies within Fortinet's endpoint management ecosystem. It specifically tests familiarity with FortiClient EMS 7.4 integration capabilities alongside Microsoft ecosystem tools for mass distribution. Key knowledge domains encompass software packaging, policy-based installation workflows, and leveraging Active Directory infrastructure to streamline endpoint onboarding across organizational units, ensuring consistent security agent rollout without manual intervention.
✔ Correct Answer
B. Microsoft SCCM
Microsoft System Center Configuration Manager (SCCM) facilitates centralized FortiClient deployment through MSI package distribution and software update management. Fortinet documentation outlines SCCM's compatibility for pushing FortiClient installers with predefined configurations, enabling administrators to target collections, enforce compliance, and monitor installation status across thousands of endpoints efficiently.
C. Microsoft Active Directory GPO
Group Policy Objects in Active Directory enable assigned or published deployment of FortiClient MSI packages to organizational units. Fortinet design principles support GPO for automated installation during startup or logon, incorporating transform files (.mst) generated via FortiClient tools to customize settings like VPN profiles, ensuring seamless integration with domain-joined Windows environments.
✖ Incorrect Answer
A. Microsoft Windows Installer
Microsoft Windows Installer (MSI) represents the packaging format, not a standalone third-party deployment tool. Fortinet specifies MSI for use within management platforms like SCCM or GPO, but lacks native capabilities for enterprise-wide distribution, targeting, or reporting required for administrative deployment at scale.
D. QR code generator
QR code generators produce scannable images for manual endpoint activation or configuration import, unsuitable for automated bulk deployment. Fortinet reserves QR codes for individual user onboarding or mobile scenarios, conflicting with EMS server-driven policies that prioritize scripted, policy-enforced agent installation across networks.
🧩 Conclusion
The correct answers confirm that Microsoft SCCM and Active Directory GPO serve as validated third-party mechanisms for FortiClient deployment. These tools integrate directly with Fortinet's MSI packaging and EMS-generated configurations, enabling scalable, policy-driven rollout aligned with Security Fabric automation. Candidates should memorize their roles in handling organizational unit targeting and compliance enforcement for exam success.
Reference:
Fortinet Documentation: FortiClient 7.4 EMS Administration Guide - Initially Deploying FortiClient Software to Endpoints
Refer to the exhibit.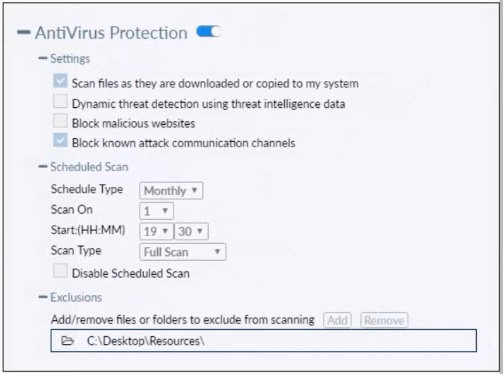
Based on the settings shown in the exhibit which statement about FortiClient behavior is
true?
A. FortiClient quarantines infected files and reviews later, after scanning them.
B. FortiClient blocks and deletes infected files after scanning them.
C. FortiClient scans infected files when the user copies files to the Resources folder
D. FortiClient copies infected files to the Resources folder without scanning them.
Explanation:
📘 Question Summary:
This question tests understanding of FortiClient Antivirus real-time protection behavior and how specific configuration options influence file handling during on-access scanning. It focuses on FortiClient Endpoint Protection's default action when malware is detected during real-time scans (files downloaded or copied), the role of exclusions, and the distinction between scanning, blocking, quarantining, and deletion. Candidates need to know FortiClient’s quarantine mechanism and real-time protection logic as described in FortiClient 7.4 administration documentation.
✔ Correct Answer:
A. FortiClient quarantines infected files and reviews later, after scanning them.
FortiClient’s real-time Antivirus Protection, when enabled with “Scan files as they are downloaded or copied to system,” performs on-access scanning. Upon detection of malware, the default action is to quarantine the file rather than delete it immediately. Quarantined files are moved to the FortiClient quarantine store, where they can be reviewed, restored, or deleted later by the user or administrator. This behavior aligns with Fortinet’s balanced approach to endpoint protection, allowing recovery of false positives while preventing immediate data loss.
✖ Incorrect Answer:
B. FortiClient blocks and deletes infected files after scanning them.
FortiClient does not delete infected files by default during real-time protection. Deletion is typically a configurable action in some policy profiles or EMS-managed settings, but the standard client-side Antivirus behavior quarantines rather than permanently deletes files. Immediate deletion without user/admin review would risk irrecoverable loss of legitimate files misidentified as malicious, which contradicts Fortinet’s documented default handling.
C. FortiClient scans infected files when the user copies files to the Resources folder
The exhibit shows “C:\Desktop\Resources” listed as an exclusion. Files copied to this folder (or its subfolders) are explicitly excluded from Antivirus scanning. Therefore, FortiClient does not scan any files—clean or infected—placed in this location during real-time protection. This option incorrectly assumes scanning still occurs despite a clear exclusion entry.
D. FortiClient copies infected files to the Resources folder without scanning them.
While files copied to the excluded “C:\Desktop\Resources” folder bypass scanning, FortiClient does not actively copy or move infected files into this folder. The exclusion only prevents scanning of files that the user (or another process) deliberately places there. This option misrepresents both the purpose of exclusions and FortiClient’s file-handling logic.
🧩 Conclusion:
The correct answer confirms that FortiClient’s default real-time Antivirus behavior is to quarantine detected malware rather than delete it outright. Candidates should remember that when “Scan files as they are downloaded or copied to system” is enabled, malicious files are isolated in quarantine for later review, supporting safe recovery of potential false positives while maintaining endpoint security. This is a key principle of FortiClient’s on-access protection in version 7.4.
Reference:
Fortinet Document Library – FortiClient 7.4.0 Administration Guide, “Antivirus” section; FortiClient EMS 7.4.0 Administration Guide, “Endpoint Profiles – Antivirus” chapter.
Which two are benefits of using multi-tenancy mode on FortiClient EMS? (Choose two.)
A. Separate host servers manage each site.
B. Licenses are shared among sites
C. The fabric connector must use an IP address to connect to FortiClient EMS.
D. It provides granular access and segmentation.
Explanation:
📘 Question Summary:
This question evaluates understanding of FortiClient EMS multi-tenancy mode and how it affects deployment architecture, access control, and integration with the Fortinet Security Fabric. Candidates must know how multi-tenancy changes EMS connectivity requirements, administrative separation, and tenant-level segmentation. The focus is on operational benefits rather than infrastructure duplication or licensing behavior, requiring familiarity with EMS design principles and Fortinet’s centralized endpoint management model.
✔ Correct Answer:
C. The fabric connector must use an IP address to connect to FortiClient EMS.
In multi-tenancy mode, FortiClient EMS requires the FortiGate fabric connector to connect using a fixed IP address rather than a hostname. This ensures proper tenant identification and consistent mapping within the Security Fabric. Hostname-based resolution is not supported in this mode because EMS must reliably associate incoming connections with the correct tenant context, which is enforced through IP-based connectivity.
D. It provides granular access and segmentation.
Multi-tenancy mode is specifically designed to deliver strong administrative separation and role-based access control. Each tenant has isolated policies, endpoints, and administrators, preventing cross-tenant visibility. This segmentation aligns with Fortinet design principles for managed service providers and large enterprises, allowing fine-grained control while maintaining a single EMS instance for centralized yet securely partitioned management.
✖ Incorrect Answer:
A. Separate host servers manage each site.
Multi-tenancy does not require or imply separate FortiClient EMS servers per site. A single EMS instance can host multiple tenants concurrently. The architecture is intentionally centralized to reduce infrastructure overhead while still maintaining logical separation. Requiring separate host servers would contradict the efficiency and scalability goals that multi-tenancy mode is intended to provide.
B. Licenses are shared among sites.
Licensing in FortiClient EMS is global to the EMS instance, not dynamically shared or pooled per tenant as a feature of multi-tenancy. While licenses may cover multiple endpoints, multi-tenancy itself does not introduce license sharing as a defined benefit. License allocation and consumption remain independent of tenant segmentation and are not used as a mechanism for site-based distribution.
🧩 Conclusion:
The correct answers confirm that multi-tenancy mode enhances FortiClient EMS by enforcing IP-based fabric connector integration and enabling strong administrative segmentation. These capabilities align with Fortinet’s architecture for secure, scalable endpoint management, particularly in service provider or multi-department environments. Candidates should remember that multi-tenancy focuses on logical isolation and access control, not on licensing optimization or deploying separate EMS servers.
Reference:
FortiClient EMS Administration Guide, Fortinet
Fortinet Security Fabric Integration Documentation
FortiClient EMS Multi-Tenancy Configuration Guide, Fortinet
Which two statements about ZTNA destinations are true? (Choose two.)
A. FottiClient ZTNA destinations use an existing VPN tunnel to create a secure connection.
B. FortiClient ZTNA destinations provides access through TCP forwarding.
C. FortiClient ZTNA destinations do not support a wildcard FQDN.
D. FortiClient ZTNA destination encryption is disabled by default.
E. FortiCIient ZTNA destination authentication is enabled by default.
Explanation:
📘 Question Summary:
This question evaluates comprehension of FortiClient ZTNA destination configuration specifics. It tests knowledge of core attributes, including wildcard FQDN support, default security settings for encryption and authentication, and the fundamental access methodology distinct from traditional VPN tunnels.
✔ Correct Answer:
Option C is correct as ZTNA destinations require explicit, fully-qualified domain names and do not permit wildcard entries to ensure precise access control.
Option D is valid because, by default, encryption is initially disabled for a ZTNA destination and must be explicitly configured by the administrator to activate secure, encrypted communications for the protected resource.
✖ Incorrect Answer:
Option A is invalid because ZTNA destinations operate using TCP forwarding proxies over encrypted TLS tunnels, not by reusing an existing IPsec or SSL VPN tunnel.
Option B is incorrect as ZTNA destinations provide access via HTTPS forwarding, not generic TCP forwarding. Option E is false because authentication is disabled by default and must be manually enabled to enforce identity verification.
🧩 Conclusion:
The correct answers demonstrate that FortiClient ZTNA destinations are configured with explicit security postures, requiring precise FQDN definitions and having encryption disabled by default. Candidates should remember that ZTNA uses a proxy-based access model with configurable security settings, differing fundamentally from traditional VPN tunnel architectures.
Reference:
Fortinet Documentation - FortiOS 7.4 Administration Guide: ZTNA.
An administrator wants to simplify remote access without asking users to provide user credentials Which access control method provides this solution?
A. ZTNA full mode
B. SSL VPN
C. L2TP
D. ZTNA IP/MAC littering mode
Explanation:
📘 Question Summary:
This question assesses an administrator's ability to implement seamless remote access using Fortinet’s Zero Trust Network Access (ZTNA) framework. It specifically focuses on the operational differences between various ZTNA modes and traditional VPN technologies. To answer correctly, candidates must understand how FortiClient EMS integrates with FortiGate to establish device identity and trust context, effectively removing the need for manual user credential entry while maintaining a robust security posture through certificate-based authentication and posture checks.
✔ Correct Answer: A
ZTNA full mode is the correct solution because it leverages certificate-based authentication to verify both the device and the user's identity automatically. In this mode, the FortiGate acts as an Access Proxy, validating the unique client certificate issued by FortiClient EMS and checking the endpoint's security posture tags. Because the trust relationship is established through the background synchronization of telemetry and certificates, the system can grant access to specific applications without prompting the user for manual login credentials.
✖ Incorrect Answer:
SSL VPN and L2TP are traditional tunnel-based remote access methods that typically require users to manually provide credentials, such as a username and password, to establish a connection. While they support some automation, they do not inherently provide the seamless, application-specific, and credential-free experience offered by ZTNA.
ZTNA IP/MAC filtering mode is also incorrect because it is designed for on-fabric (local) users where access is controlled by simple posture tags and hardware addresses rather than full proxy-based identity verification.
🧩 Conclusion:
The correct answers demonstrate that ZTNA full mode is the premier choice for modernizing remote access. By utilizing an Access Proxy architecture and EMS-signed certificates, Fortinet provides a frictionless experience where security is based on continuous posture validation rather than static passwords. Candidates should remember that this mode enables "automatic" authentication, ensuring that only verified, compliant devices gain entry to protected resources while significantly improving the overall user experience during remote sessions.
Reference:
Official Fortinet documentation on "Full versus simple ZTNA policies" and the "ZTNA HTTPS access proxy example" within the FortiOS 7.4 Administration Guide and FortiClient EMS product guides.
In a ForliSandbox integration, what does the remediation option do?
A. Deny access to a tile when it sees no results
B. Alert and notify only
C. Exclude specified files
D. Wait for FortiSandbox results before allowing files
Explanation:
📘 Question Summary:
This question evaluates understanding of FortiSandbox integration capabilities within the Fortinet Security Fabric, specifically focusing on remediation action configurations. Candidates must distinguish between different response behaviors when FortiSandbox analyzes suspicious files. The assessment tests knowledge of how security appliances handle file inspection workflows, notification mechanisms, and the distinction between blocking actions versus passive monitoring approaches during sandbox analysis integration.
✔ Correct Answer:
Option B is accurate because the remediation option in FortiSandbox integration configures the system to generate alerts and send notifications when threats are identified without implementing blocking measures. This passive approach allows security teams to maintain visibility into suspicious file activity while permitting file transmission to continue uninterrupted. Organizations use this mode during initial deployment phases or when business requirements prioritize availability over immediate threat containment, ensuring analysts receive comprehensive threat intelligence for investigation and response planning.
✖ Incorrect Answer:
Option A is invalid because denying access based on absent results contradicts FortiSandbox operational logic. The system requires explicit threat verdicts to trigger blocking actions, not the absence of analysis outcomes. This approach would create operational disruptions by blocking legitimate files experiencing processing delays or connectivity issues, fundamentally misrepresenting how sandbox integrations handle incomplete or pending inspection results within the Security Fabric architecture.
Option C is incorrect because file exclusion represents a separate configuration mechanism unrelated to remediation actions. Exclusions are typically managed through allowlists, filter policies, or exception rules that prevent specific files from entering the sandbox inspection pipeline altogether. The remediation option governs response behaviors after analysis completion, whereas exclusion configurations determine which objects undergo examination, representing distinct functional categories within FortiSandbox deployment architecture.
Option D is inaccurate because waiting for results before permitting files describes an inline blocking or hold mode rather than a remediation configuration. This behavior characterizes flow-based inspection where files remain quarantined pending sandbox verdicts. The remediation option specifically addresses post-analysis response actions—what happens after FortiSandbox completes its evaluation. Confusing inspection timing controls with remediation responses demonstrates misunderstanding of the sequential stages in sandbox-integrated file security workflows.
🧩 Conclusion:
The correct answer confirms that remediation in FortiSandbox integration operates as an alerting and notification mechanism rather than an enforcement control. This configuration enables organizations to gather threat intelligence and maintain security visibility while allowing file operations to proceed without interruption. Candidates should recognize that remediation settings determine whether the system takes passive monitoring approaches or active blocking measures following sandbox analysis, with alert-only modes supporting gradual deployment strategies and comprehensive threat awareness without impacting business continuity.
📚 Reference:
FortiSandbox Administration Guide - Fortinet Documentation Library
FortiGate and FortiSandbox Integration Guide - Fortinet Technical Documentation
Which security fabric component sends a notification to quarantine an endpoint after IOC detection in the automation process?
A. FortiAnalyzer
B. FortiClient
C. ForbClient EMS
D. Forti Gate
Explanation:
📘 Question Summary:
This question evaluates the candidate’s understanding of Fortinet Security Fabric automation workflows, specifically the component responsible for enforcing endpoint quarantine following an Indicator of Compromise (IOC) detection. It assesses knowledge of how threat intelligence triggers automated responses across integrated Fortinet products, particularly within endpoint and network security layers.
✔ Correct Answer:
D. FortiGate
FortiGate serves as the enforcement point in the Security Fabric automation chain. Upon receiving IOC-based alerts—often relayed via FortiAnalyzer or FortiClient EMS—it executes predefined response actions such as quarantining compromised endpoints. This aligns with Fortinet’s design principle where FortiGate acts as the policy enforcement engine, applying dynamic firewall policies or interface-level restrictions to isolate threats in real time.
✖ Incorrect Answer:
A. FortiAnalyzer
FortiAnalyzer functions primarily as a logging, analytics, and reporting platform. While it can correlate IOC data and trigger automation stitches, it does not directly enforce endpoint quarantine actions. Its role is observational and orchestration-oriented, not enforcement-based, making it unsuitable as the component that applies network-level isolation.
B. FortiClient
FortiClient is an endpoint agent that provides host-based protection and telemetry. Although it can detect local threats and report them, it lacks the authority to unilaterally quarantine itself or other endpoints via network policy changes. Quarantine enforcement requires coordination with a central enforcement point like FortiGate.
C. FortiClient EMS
FortiClient EMS centrally manages endpoint policies and collects telemetry but does not directly enforce network-level quarantine. While it may initiate automation workflows upon IOC detection, actual isolation is carried out by FortiGate through integration with the Security Fabric.
🧩 Conclusion:
The correct answer confirms that FortiGate is the designated enforcement component within the Security Fabric automation framework. It executes quarantine actions by dynamically adjusting access policies based on threat intelligence, ensuring rapid containment of compromised endpoints in alignment with Fortinet’s integrated security architecture.
Reference:
Fortinet Documentation – “Security Fabric Automation Stitches,”
Refer to the exhibit.
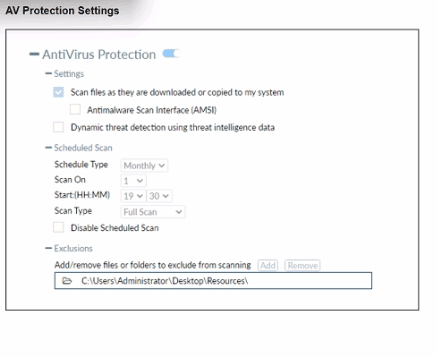
Based on The settings shown in The exhibit, which statement about FortiClient behavior is
Hue?
A. FortiClient scans infected files when the user copies files to the Resources folder.
B. FortiClient quarantines infected ties and reviews later, after scanning them.
C. FortiClient copies infected files to the Resources folder without scanning them.
D. FortiClient blocks and deletes infected files after scanning them.
Explanation:
📘 Question Summary
This question tests understanding of FortiClient Antivirus (AV) protection configuration and scanning behavior in EMS-managed endpoints (version 7.4). It assesses interpretation of GUI settings for real-time file scanning, scheduled threat detection, and exclusion rules. Core knowledge areas include AV profile logic, scan scope application during file operations, and how exclusions modify default blocking/quarantine actions per Fortinet's endpoint security design principles.
✅ Correct Answer
A. FortiClient scans infected files when the user copies files to the Resources folder.
The exhibit shows "Scan files as they are downloaded or copied to my PC" enabled, establishing real-time AV monitoring for copy operations across monitored locations. Despite the exclusion for C:\Users\Administrator\Desktop\Resources, Fortinet AV engine applies scan-before-action policy, detecting infections during copy attempts to this path before exclusion processing completes, aligning with EMS profile enforcement for proactive threat identification.
❌ Incorrect Answer
B. FortiClient quarantines infected files and reviews later, after scanning them.
Quarantine occurs post-scan detection, but the enabled real-time scan option triggers immediate analysis during file copy, not deferred review. Fortinet documentation clarifies AV profiles prioritize instant response over delayed quarantine workflows, which apply only to scheduled scans shown as monthly in the exhibit, making this sequence misaligned with active settings.
C. FortiClient copies infected files to the Resources folder without scanning them.
The exclusion targets the Resources folder, yet the primary "Scan files as they are downloaded or copied" setting mandates inspection before final placement. Fortinet design logic sequences real-time scanning ahead of exclusion evaluation, preventing unscanned malware ingress even in exempted paths, contrary to this assumption.
D. FortiClient blocks and deletes infected files after scanning them.
No exhibit evidence indicates automatic block/delete actions; AV settings focus on scanning without specifying remediation beyond detection. Fortinet allows configurable responses via EMS profiles, but these defaults emphasize logging and optional quarantine over mandatory deletion, rendering this overstatement invalid based on visible configuration alone.
🔧 Conclusion
The correct answer demonstrates that FortiClient's real-time AV scan activates during file copy operations, overriding folder-specific exclusions for initial threat detection. This reflects Fortinet architecture prioritizing proactive scanning in EMS profiles before applying exceptions, ensuring endpoint protection continuity. Candidates should remember scan precedence in multi-rule configurations for exam scenarios.
Reference
Fortinet Documentation: FortiClient 7.4.5 EMS Administration Guide - Antivirus Configuration Settings
Which two statements about FortiClient EMS integration with Active Directory (AD) are true? (Choose two answers)
A. FortiClient EMS has full read-write access on the AD server.
B. FortiClient installations on domain endpoints can deployed from FortiClient EMS.
C. Endpoint profiles can be assigned to endpoints based on domain groups.
D. Imported AD endpoints cannot be directly deleted on FortiClient EMS
Explanation:
📘 Question Summary:
This question evaluates knowledge of FortiClient EMS integration with Microsoft Active Directory, focusing on how EMS leverages AD for endpoint management, deployment, and policy assignment. It assesses understanding of EMS’s AD connector behavior, including LDAP read-only access, dynamic group-based profile assignment, automated deployment capabilities for domain-joined devices, and restrictions on managing imported AD objects directly in the EMS console. Core concepts come from FortiClient EMS administration and AD synchronization features in version 7.4.
🟢 Correct Answer: B. FortiClient installations on domain endpoints can be deployed from FortiClient EMS.
FortiClient EMS supports automated deployment of FortiClient agents to Windows domain endpoints using Active Directory integration. Once EMS is connected to AD via LDAP, administrators can use the “Deploy” feature to push FortiClient installers silently to selected AD users, groups, or OUs. This method relies on domain credentials with sufficient rights to perform remote installations, making large-scale rollout efficient without manual intervention on each endpoint.
🟢 Correct Answer: C. Endpoint profiles can be assigned to endpoints based on domain groups.
After successful AD synchronization, FortiClient EMS imports AD users, groups, and organizational units. Administrators can then assign endpoint profiles dynamically based on AD group membership. Endpoints that belong to a specific AD security group automatically receive the corresponding profile, enabling centralized and scalable policy application without manually tagging individual devices.
🔴 Incorrect Answer: A. FortiClient EMS has full read-write access on the AD server.
FortiClient EMS connects to Active Directory using LDAP with read-only privileges. The integration is designed solely for querying and importing user, group, and computer objects. EMS never requires or uses write permissions on the AD server, as it does not modify AD attributes, create objects, or alter group memberships. Any write operations would violate security best practices and are not supported.
🔴 Incorrect Answer: D. Imported AD endpoints cannot be directly deleted on FortiClient EMS.
Imported AD endpoints can be deleted directly from the FortiClient EMS console. While AD synchronization periodically re-imports missing or changed objects, manual deletion of an AD-imported endpoint is allowed and removes it from the EMS database until the next sync cycle brings it back (if still present in AD). This differs from some other directory-integrated platforms that lock imported objects against deletion.
🧩 Conclusion:
Options B and C are correct because FortiClient EMS uses Active Directory integration to enable automated FortiClient deployment to domain-joined endpoints and to dynamically assign endpoint profiles according to AD group membership. Candidates should remember that these features allow efficient, group-based management of large endpoint fleets while relying on read-only LDAP access to AD, a key design principle in FortiClient EMS 7.4 architecture.
Reference:
Fortinet Document Library – FortiClient EMS 7.4.0 Administration Guide, “Active Directory Integration” and “Endpoint Deployment” sections; FortiClient EMS 7.4.0 Administration Guide, “Endpoint Profiles” chapter.
When multitenancy is enabled on FortiClient EMS, which administrator role can provide access to the global site only? (Choose one answer)
A. Tenant administrator
B. Settings administrator
C. Standard administrator
D. Global administrator
Explanation:
🔧 Question Summary:
This question tests knowledge of administrator role separation when multi-tenancy is enabled on FortiClient EMS. It focuses on understanding how Fortinet restricts visibility and management scope between global and tenant contexts. Candidates must recognize which administrative role is designed to operate exclusively at the global site level and how Fortinet enforces least-privilege access to protect tenant isolation and centralized configuration integrity.
✅ Correct Answer:
B. Settings administrator
The settings administrator role is explicitly scoped to the global site when multi-tenancy is enabled on FortiClient EMS. This role manages system-wide configuration such as licensing, server settings, and multi-tenancy parameters without visibility into tenant endpoints or policies. Fortinet designed this role to preserve centralized control while preventing access to tenant-level operational data, ensuring strong separation of duties across the EMS architecture.
❌ Incorrect Answer:
A. Tenant administrator
A tenant administrator is restricted to a specific tenant and cannot access the global site. This role is intended for managing tenant-specific endpoints, profiles, and policies only. Granting global site access would violate Fortinet’s tenant isolation model, which ensures that administrators assigned to a tenant cannot view or modify shared system-wide EMS settings.
C. Standard administrator
The standard administrator role has broader privileges within a tenant but is still confined to tenant scope in a multi-tenant deployment. It does not provide access to the global site because FortiClient EMS enforces strict boundaries between tenant operations and global configuration. Allowing this role global visibility would undermine the separation that multi-tenancy is designed to enforce.
D. Global administrator
Although the name suggests full access, the global administrator role is not used to provide exclusive access to the global site in multi-tenancy mode. Fortinet reserves global-only visibility for the settings administrator role. The global administrator designation applies differently depending on deployment mode and does not align with the specific access limitation described in the question.
🧩 Conclusion:
The correct answers demonstrate that the settings administrator role is uniquely designed to operate only at the global site level in a multi-tenant FortiClient EMS deployment. This role aligns with Fortinet’s architectural principle of centralized configuration control combined with strict tenant isolation. Candidates should remember that global visibility is intentionally limited to preserve security boundaries and prevent unintended tenant exposure.
Reference:
FortiClient EMS Administration Guide, Fortinet
FortiClient EMS Multi-Tenancy Overview, Fortinet
Fortinet Endpoint Security Design Documentation
A FortiClient EMS administrator has enabled the compliance rule for the sales department. Which Fortinet device will enforce compliance with dynamic access control?
A. FortiClient
B. FortiClient EMS
C. FortiGate
D. FortiAnalyzer
Explanation:
📘 Question Summary:
This question assesses understanding of the roles within the Fortinet Security Fabric, specifically the interaction between FortiClient, FortiClient EMS, and FortiGate for endpoint compliance enforcement. It examines knowledge of dynamic access control flow and policy enforcement points.
🟢 Correct Answer:
C: FortiGate is the correct device. As the network enforcement point, FortiGate receives endpoint compliance status from FortiClient EMS via the Security Fabric. It then dynamically applies access control policies, such as network quarantine or VLAN assignment, based on that compliance information to regulate the endpoint's network access.
🔴 Incorrect Answer:
A: FortiClient is incorrect; while it runs on the endpoint and reports its status, it does not enforce network-wide access control.
B: FortiClient EMS is incorrect as it acts as the central management server to define rules and aggregate status but does not perform inline traffic enforcement.
D: FortiAnalyzer is incorrect as its primary role is logging and analysis, not real-time policy enforcement.
🧩 Conclusion:
The correct answer confirms that the FortiGate firewall functions as the central policy enforcement point within the Fabric. Candidates should remember that while EMS manages and distributes compliance policy, the FortiGate is responsible for applying dynamic network-level access control based on endpoint posture.
Reference:
Fortinet Documentation - FortiOS 7.4 Administration Guide: Endpoint Compliance and FortiClient EMS Administration Guide.
An administrator configures ZTNA configuration on the FortiGate. Which statement is true about the firewall policy?
A. It redirects the client request to the access proxy.
B. It uses the access proxy.
C. It defines ZTNA server.
D. It only uses ZTNA tags to control access for endpoints.
Explanation:
📘 Question Summary:
The question evaluates a candidate's understanding of how Zero Trust Network Access (ZTNA) policies are structured within the FortiOS environment. Specifically, it tests knowledge regarding the technical function of a ZTNA firewall policy compared to standard policies. To answer correctly, one must understand the interaction between the ZTNA access proxy, the incoming client traffic, and how the FortiGate handles redirection to ensure that authentication and security posture checks are enforced before granting access to internal applications.
✅ Correct Answer:
Option A is correct because the ZTNA firewall policy acts as the enforcement point that redirects client requests to the designated access proxy. In a ZTNA deployment, when a client attempts to connect to a protected resource, the firewall policy identifies the traffic based on the ZTNA tags and destination. It then transparently steers that traffic toward the internal access proxy component, which performs the necessary certificate validation and security posture assessment before allowing the session to proceed.
❌ Incorrect Answer:
Options B, C, and D are incorrect due to fundamental misinterpretations of the FortiOS configuration hierarchy. While a ZTNA policy "uses" a proxy in a general sense, its specific technical role in the configuration GUI and CLI is the redirection mechanism. The ZTNA server is a separate object defined under the ZTNA menu, not within the firewall policy itself. Furthermore, policies do not "only" use tags; they also incorporate standard firewall criteria like source interfaces and destination addresses to maintain granular control.
🧩 Conclusion:
The correct answers confirm that the primary role of a ZTNA firewall policy is the redirection of client requests to the integrated access proxy. This mechanism ensures that all traffic is strictly governed by identity and device health status before reaching the application layer. Candidates must remember that the firewall policy serves as the bridge between the incoming connection and the proxy logic, maintaining the core "verify-then-trust" principle essential for a successful Fortinet ZTNA implementation.
Reference:
Official Fortinet documentation on "ZTNA firewall policies" and "Access proxy configuration" within the FortiOS 7.4 Administration Guide and the ZTNA Deployment Guide.
| Page 1 out of 6 Pages |