This sample code is vulnerable to which of the following attacks? Select all that apply.
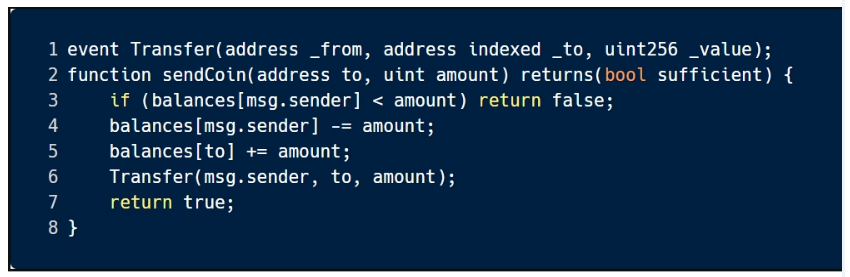
A. Unchecked Return Values
B. Arithmetic
C. Short Address
D. Reentrancy
This sample code is vulnerable to which of the following attacks?
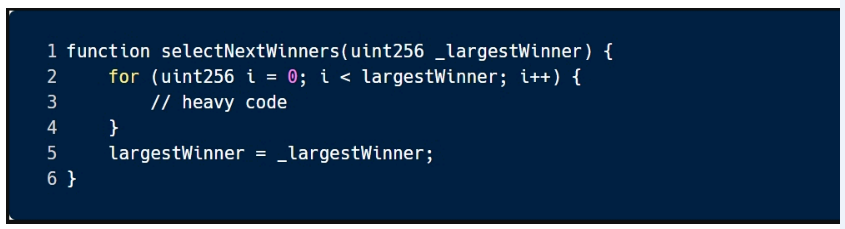
A. Denial of Service
B. Access Control
C. Race Conditions
D. Anthmetic
E. All of the above
The code of smart contracts that are "self-destructed" is no longer visible to the blockchain network
A. True
B. False
In both blockchain and DAG-based distributed ledgers, the trust in all transactions that are part of the ledger Increases as additional transactions are added to the ledger.
A. True
B. False
Which of the following is designed to allow someone to prove they know a secret without revealing it?
A. Confidential Transaction
B. Ring Signature
C. Zero-Knowledge Proof
D. Stealth Address
Which of the following types of attacks are disincentivized in the long-term on blockchains like Bitcoin?
A. Timewarp
B. Double-Spend
C. Selfish Mining
D. SPV Mining
Confidential Transactions prove that inputs and outputs ot a transaction are equal.
A. True
B. False
Which of the following is a takenaway from the pigeocoin/Bitcom Core hack?
A. Importance of scaning code for common vulnerabilities
B. Importance of cryptanalysis of algorithms used
C. Import of system-level analysis
D. Import of a robust change management process
Malware infections of blockchain nodes can compromise the security of the blockchain's consensus algorithm.
A. True
B. False
Which smart contract vulnerability allows an attacker to make a profit off a smart contract cryptocurrency exchange like Bancor?
A. Arithmetic
B. Access Control
C. Race Conditions
D. Reentrancy
Which blockchain security control either risks centralization or permanently divergent chains?
A. Random Neighbor Selection
B. Permissioned Blockchains
C. Checkpoints
D. Private Blockchains
Which smart contract auditing strategy identities which variables in the function can be affected by the person running it?
A. Manual Code Analysis
B. Symbolic Execution
C. Taint Analysis
D. Control Flow Analysis
| Page 2 out of 8 Pages |
| Previous |