While investigating a security event, an analyst finds evidence that a user opened an email
attachment from an unknown source. Shortly after the user opened the attachment, a
group of servers experienced a large amount of network and resource activity. Upon
investigating the servers, the analyst discovers the servers were encrypted by ransomware
that is demanding payment within 48 hours or all data will be destroyed. The company has
no response plans for ransomware.
Which of the following is the NEXT step the analyst should take after reporting the incident
to the management team?
A.
Pay the ransom within 48 hours.
B.
Isolate the servers to prevent the spread.
C.
Notify law enforcement.
D.
Request that the affected servers be restored immediately
Notify law enforcement.
SIMULATION
You are a security analyst tasked with interpreting an Nmap scan output from company’s
privileged network.
The company’s hardening guidelines indicate the following:
There should be one primary server or service per device.
Only default ports should be used
Non-secure protocols should be disabled.
INSTRUCTIONS
Using the Nmap output, identify the devices on the network and their roles, and any open
ports that should be closed.
For each device found by Nmap, add a device entry to the Devices Discovered list, with the
following information:
The IP address of the device
The primary server or service of the device (Note that each IP should by associated with
one service/port only)
The protocol(s) that should be disabled based on the hardening guidelines (Note that
multiple ports may need to be closed to comply with the hardening guidelines)
If at any time you would like to bring back the initial state of the simulation, please click the
Reset All button.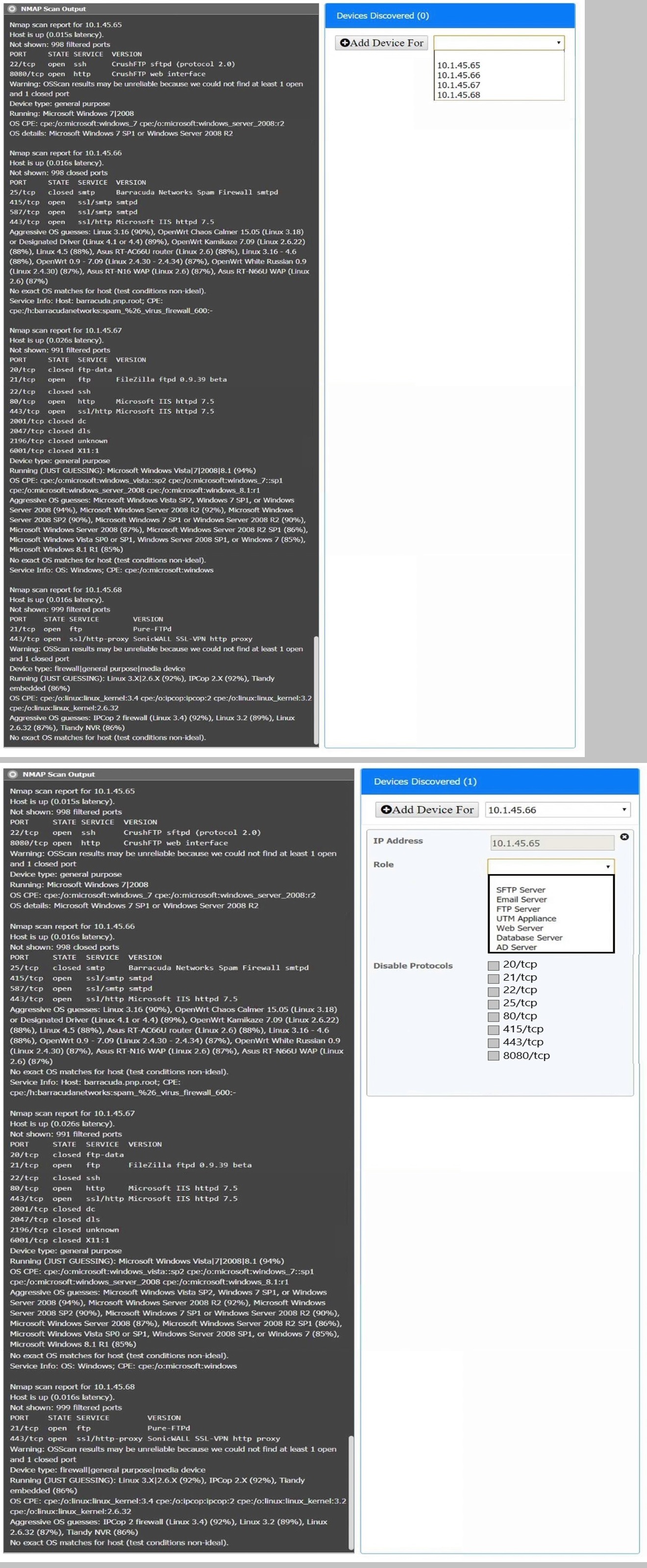
Answer: See explanation below.
Explanation:
10.1.45.65 SFTP Server Disable 8080
10.1.45.66 Email Server Disable 415 and 443
10.1.45.67 Web Server Disable 21, 80
10.1.45.68 UTM Appliance Disable 21
The Chief information Officer (CIO) asks the system administrator to improve email security
at the company based on the following requirements:
* Transaction being requested by unauthorized individuals.
* Complete discretion regarding client names, account numbers, and investment
information.
* Malicious attackers using email to malware and ransomeware.
* Exfiltration of sensitive company information.
The cloud-based email solution will provide anti-malware reputation-based scanning,
signature-based scanning, and sandboxing. Which of the following is the BEST option to
resolve the boar’s concerns for this email migration?
A.
Data loss prevention
B.
Endpoint detection response
C.
SSL VPN
D.
Application whitelisting
Data loss prevention
A security engineer is troubleshooting an issue in which an employee is getting an IP
address in the range on the wired network. The engineer plus another PC into the same
port, and that PC gets an IP address in the correct range. The engineer then puts the
employee’ PC on the wireless network and finds the PC still not get an IP address in the
proper range. The PC is up to date on all software and antivirus definitions, and the IP
address is not an APIPA address. Which of the following is MOST likely the problem?
A.
The company is using 802.1x for VLAN assignment, and the user or computer is in the
wrong group.
B.
The DHCP server has a reservation for the PC’s MAC address for the wired interface.
C.
The WiFi network is using WPA2 Enterprise, and the computer certificate has the wrong
IP address in the SAN field.
D.
The DHCP server is unavailable, so no IP address is being sent back to the PC.
The company is using 802.1x for VLAN assignment, and the user or computer is in the
wrong group.
Given the following log snippet from a web server: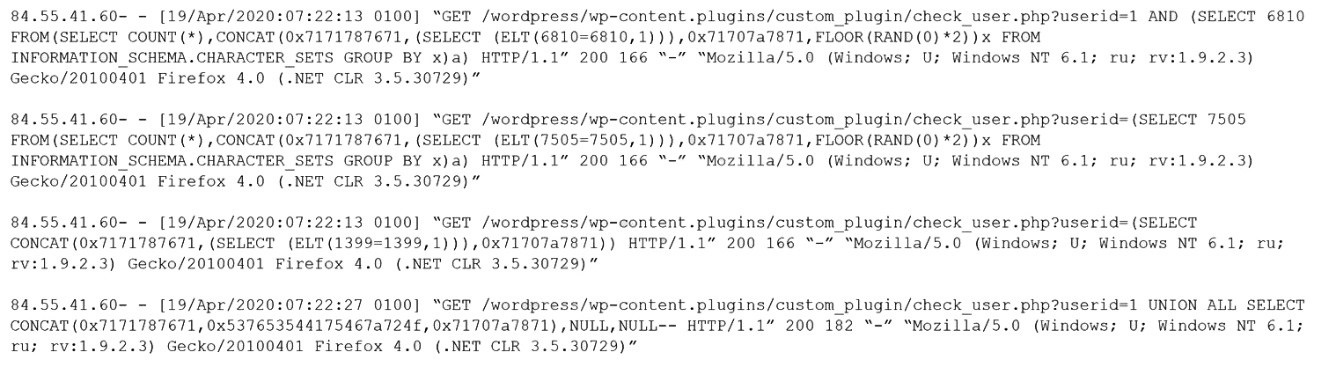
Which of the following BEST describes this type of attack?
A.
SQL injection
B.
Cross-site scripting
C.
Brute-force
D.
Cross-site request forgery
Cross-site request forgery
A host on a company’s network has been infected by a worm that appears to be spreading
via SMB. A security analyst has been tasked with containing the incident while also
maintaining evidence for a subsequent investigation and malware analysis.
Which of the following steps would be best to perform FIRST?
A.
Turn off the infected host immediately.
B.
Run a full anti-malware scan on the infected host.
C.
Modify the smb.conf file of the host to prevent outgoing SMB connections.
D.
Isolate the infected host from the network by removing all network connections
Isolate the infected host from the network by removing all network connections
An enterprise is deploying APIs that utilize a private key and a public key to ensure the
connection string is protected. To connect to the API, customers must use the private key.Which of the following would BEST secure the REST API connection to the database while
preventing the use of a hard-coded string in the request string?
A.
Implement a VPN for all APIs.
B.
Sign the key with DSA.
C.
Deploy MFA for the service accounts.
D.
Utilize HMAC for the keys
Utilize HMAC for the keys
Reference: https://eclipsesource.com/blogs/2016/07/06/keyed-hash-messageauthentication-
code-in-rest-apis/
A Chief Information Officer (CIO) wants to implement a cloud solution that will satisfy the
following requirements:
Support all phases of the SDLC.
Use tailored website portal software.
Allow the company to build and use its own gateway software.
Utilize its own data management platform.
Continue using agent-based security tools.
Which of the following cloud-computing models should the CIO implement?
A.
SaaS
B.
PaaS
C.
MaaS
D.
IaaS
IaaS
Reference: https://www.bmc.com/blogs/saas-vs-paas-vs-iaas-whats-the-difference-andhow-
to-choose/
A software house is developing a new application. The application has the following
requirements:
Reduce the number of credential requests as much as possible
Integrate with social networks
Authenticate users
Which of the following is the BEST federation method to use for the application?
A.
WS-Federation
B.
OpenID
C.
OAuth
D.
SAML
SAML
Reference: https://auth0.com/blog/how-saml-authentication-works/
A small company recently developed prototype technology for a military program. The
company’s security engineer is concerned about potential theft of the newly developed,
proprietary information.
Which of the following should the security engineer do to BEST manage the threats
proactively?
A.
Join an information-sharing community that is relevant to the company.
B.
Leverage the MITRE ATT&CK framework to map the TTR.
C.
Use OSINT techniques to evaluate and analyze the threats.
D.
Update security awareness training to address new threats, such as best practices for
data security.
Update security awareness training to address new threats, such as best practices for
data security.
Company A acquired Company . During an audit, a security engineer found Company B’s the two environments until Company B's infrastructure could be integrated into Company
A’s security program.
Which of the following risk-handling techniques was used?
A.
Accept
B.
Avoid
C.
Transfer
D.
Mitigateenvironment was inadequately patched. In response, Company A placed a firewall between
Mitigateenvironment was inadequately patched. In response, Company A placed a firewall between
Reference: https://www.pivotpointsecurity.com/blog/risk-tolerance-in-business/
A disaster recovery team learned of several mistakes that were made during the last
disaster recovery parallel test. Computational resources ran out at 70% of restoration of
critical services.
Which of the following should be modified to prevent the issue from reoccurring?
A.
Recovery point objective
B.
Recovery time objective
C.
Mission-essential functions
D.
Recovery service level
Recovery time objective
Reference: https://www.nakivo.com/blog/disaster-recovery-in-cloud-computing
| Page 6 out of 17 Pages |
| Previous |