A security architect for a large, multinational manufacturer needs to design and implement
a security solution to monitor traffic.
When designing the solution, which of the following threats should the security architect
focus on to prevent attacks against the network?
A.
Packets that are the wrong size or length
B.
Use of any non-DNP3 communication on a DNP3 port
C.
Multiple solicited responses over time
D.
Application of an unsupported encryption algorithm
Multiple solicited responses over time
An organization is prioritizing efforts to remediate or mitigate risks identified during the
latest assessment. For one of the risks, a full remediation was not possible, but the
organization was able to successfully apply mitigations to reduce the likelihood of impact.
Which of the following should the organization perform NEXT?
A.
Assess the residual risk.
B.
Update the organization’s threat model.
C.
Move to the next risk in the register.
D.
Recalculate the magnitude of impact.
Recalculate the magnitude of impact.
A cybersecurity analyst receives a ticket that indicates a potential incident is occurring.
There has been a large in log files generated by a generated by a website containing a
‘’Contact US’’ form. The analyst must determine if the increase in website traffic is due to a
recent marketing campaign of if this is a potential incident. Which of the following would
BEST assist the analyst?
A.
Ensuring proper input validation is configured on the ‘’Contact US’’ form
B.
Deploy a WAF in front of the public website
C.
Checking for new rules from the inbound network IPS vendor
D.
Running the website log files through a log reduction and analysis tool
Running the website log files through a log reduction and analysis tool
A security analyst is reading the results of a successful exploit that was recently conducted
by third-party penetration testers. The testers reverse engineered a privileged executable.
In the report, the planning and execution of the exploit is detailed using logs and outputs
from the test However, the attack vector of the exploit is missing, making it harder to
recommend remediation’s. Given the following output:
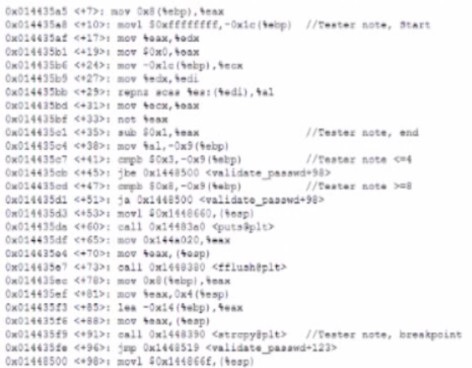
The penetration testers MOST likely took advantage of:
A.
A TOC/TOU vulnerability
B.
A plain-text password disclosure
C.
An integer overflow vulnerability
D.
A buffer overflow vulnerability
A TOC/TOU vulnerability
A company in the financial sector receives a substantial number of customer transaction
requests via email. While doing a root-cause analysis conceding a security breach, the
CIRT correlates an unusual spike in port 80 traffic from the IP address of a desktop used
by a customer relations employee who has access to several of the compromised
accounts. Subsequent antivirus scans of the device do not return an findings, but the CIRT
finds undocumented services running on the device. Which of the following controls would reduce the discovery time for similar in the future.
A.
Implementing application blacklisting
B.
Configuring the mall to quarantine incoming attachment automatically
C.
Deploying host-based firewalls and shipping the logs to the SIEM
D.
Increasing the cadence for antivirus DAT updates to twice daily
Deploying host-based firewalls and shipping the logs to the SIEM
A cybersecurity analyst created the following tables to help determine the maximum budget amount the business can justify spending on an improved email filtering system:
Which of the following meets the budget needs of the business?
A.
Filter ABC
B.
Filter XYZ
C.
Filter GHI
D.
Filter TUV
Filter GHI
A security analyst is reviewing network connectivity on a Linux workstation and examining the active TCP connections using the command line.Which of the following commands would be the BEST to run to view only active Internet
connections?
A.
sudo netstat -antu | grep “LISTEN” | awk ‘{print$5}’
B.
sudo netstat -nlt -p | grep “ESTABLISHED”
C.
sudo netstat -plntu | grep -v “Foreign Address”
D.
sudo netstat -pnut -w | column -t -s $’\w’
E.
sudo netstat -pnut | grep -P ^tcp
sudo netstat -nlt -p | grep “ESTABLISHED”
Reference: https://www.codegrepper.com/code-examples/shell/netstat+find+port
A security analyst is reviewing the following output:
Which of the following would BEST mitigate this type of attack?
A.
Installing a network firewall
B.
Placing a WAF inline
C.
Implementing an IDS
D.
Deploying a honeypot
Installing a network firewall
An organization recently started processing, transmitting, and storing its customers’ credit
card information. Within a week of doing so, the organization suffered a massive breach
that resulted in the exposure of the customers’ information.
Which of the following provides the BEST guidance for protecting such information while it is at rest and in transit?
A.
NIST
B.
GDPR
C.
PCI DSS
D.
ISO
PCI DSS
Reference: https://en.wikipedia.org/wiki/Payment_Card_Industry_Data_Security_Standard
A Chief Information Officer is considering migrating all company data to the cloud to save
money on expensive SAN storage.
Which of the following is a security concern that will MOST likely need to be addressed
during migration?
A.
Latency
B.
Data exposure
C.
Data loss
D.
Data dispersion
Latency
A security engineer at a company is designing a system to mitigate recent setbacks caused
competitors that are beating the company to market with the new products. Several of the
products incorporate propriety enhancements developed by the engineer’s company. The
network already includes a SEIM and a NIPS and requires 2FA for all user access. Which
of the following system should the engineer consider NEXT to mitigate the associated
risks?
A.
DLP
B.
Mail gateway
C.
Data flow enforcement
D.
UTM
DLP
A company’s claims processed department has a mobile workforce that receives a large
number of email submissions from personal email addresses. An employees recently
received an email that approved to be claim form, but it installed malicious software on the
employee’s laptop when was opened.
A.
Impalement application whitelisting and add only the email client to the whitelist for
laptop in the claims processing department.
B.
Required all laptops to connect to the VPN before accessing email.
C.
Implement cloud-based content filtering with sandboxing capabilities.
D.
Install a mail gateway to scan incoming messages and strip attachments before they
reach the mailbox.
Implement cloud-based content filtering with sandboxing capabilities.
| Page 4 out of 17 Pages |
| Previous |