Topic 2, Contoso Case Study 2
You need to configure GW1 to meet the network security requirements for the P2S VPN users. Which Tunnel type should you select in the Point-to-site configuration settings of GW1?
A. IKEv2 and OpenVPN (SSL)
B. IKEv2
C. IKEv2 and SSTP (SSL)
D. OpenVPN (SSL)
E. SSTP (SSL)
Summary:
This question involves selecting the appropriate Point-to-Site (P2S) VPN tunnel type to meet network security requirements. The key differentiator is the protocol's support for modern authentication and security standards. The solution must prioritize strong, certificate-based authentication and robust encryption protocols.
Correct Option:
A. IKEv2 and OpenVPN (SSL):
This is the correct and most comprehensive choice. Selecting both protocols provides the highest level of client compatibility and security:
IKEv2 offers superior stability, especially when users switch networks (e.g., from Wi-Fi to mobile data). It supports certificate-based authentication, which is a strong security standard.
OpenVPN (SSL) is crucial as it is the only protocol that supports the modern, passwordless-capable Azure AD authentication. It also provides broad client compatibility across various operating systems.
Incorrect Option:
B. IKEv2:
Selecting only IKEv2 is insufficient. It does not support Azure AD authentication, which is often a key security requirement for user-based VPNs. This limits authentication to certificates only and excludes users on operating systems that rely on the OpenVPN client.
C. IKEv2 and SSTP (SSL):
This combination is outdated from a security perspective. SSTP is a legacy protocol that does not support Azure AD authentication and is less performant and transparent than OpenVPN. Modern security best practices favor OpenVPN over SSTP.
D. OpenVPN (SSL):
Using only OpenVPN can meet security requirements if Azure AD authentication is the sole goal. However, it excludes native IKEv2 clients (like macOS and iOS), which provide a more seamless and resilient connection experience, especially for mobile users. Offering both is the best practice.
E. SSTP (SSL):
This is the least desirable option. Relying solely on SSTP prevents the use of modern Azure AD authentication and offers no benefits over the IKEv2/OpenVPN combination. It should be avoided for new deployments where modern security is a requirement.
Reference:
Microsoft Learn: About Point-to-Site VPN protocols - This document compares the supported protocols and explicitly states that OpenVPN is required for Azure AD authentication.
You need to meet the network security requirements for the NSG flow logs.
Which type of resource do you need, and how many instances should you create? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
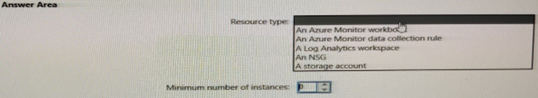
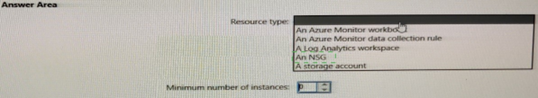
Summary:
This question concerns the infrastructure required to collect and store NSG Flow Logs. NSG Flow Logs are a feature of Azure Network Watcher that capture information about IP traffic flowing through a Network Security Group. The solution requires a destination for the logs and follows a specific resource topology.
Correct Option:
Resource type: A storage account
Minimum number of instances: 1
Explanation of Answers:
A storage account:
This is the correct resource type. By definition, NSG Flow Logs must be written to an Azure Storage Account. This is a mandatory requirement; the logs are stored as blobs within a designated container in the storage account. While a Log Analytics workspace can be used for analyzing flow logs, the primary, raw log data must first be persisted in a storage account.
Minimum number of instances: 1:
You only need one central storage account to collect the NSG Flow Logs from all your NSGs. A single storage account can have multiple containers and can receive diagnostic data from numerous resources across the subscription. There is no requirement to create a separate storage account per NSG or per virtual network. Creating one is the most efficient and manageable approach.
Explanation of Incorrect Resource Types:
An Azure Monitor workflow:
This likely refers to a Logic Apps workflow for automation, which is not the direct destination for NSG flow logs.
An Azure Monitor data collection rule (DCR):
DCRs are used to define how data should be collected for Azure Monitor Agent, primarily for guest OS telemetry. They are not the direct storage target for platform-level NSG Flow Logs.
A Log Analytics workspace:
While you can send a copy of your NSG Flow Logs to a Log Analytics workspace for advanced querying with KQL, this is an optional, secondary step. The primary and mandatory storage location is always an Azure Storage Account.
A Data:
This is an incomplete and unclear resource type and is not a valid Azure service for this purpose.
Reference:
Microsoft Learn: Introduction to NSG flow logs - This document explicitly states, "NSG flow logs are stored in an Azure storage account."
You are implementing the Virtual network requirements for Vnet6.
What is the minimum number of subnets and service endpoints you should create? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

Summary:
To meet Vnet6’s virtual network requirements, a single dedicated subnet is required to host private endpoints for secure PaaS access (e.g., storage, databases). Private endpoints must reside in their own subnet. Service endpoints are not needed when using private endpoints, as they provide private connectivity via private IPs. Thus, the minimum is one subnet and zero service endpoints.
Correct Option:
Subnets: 1
One subnet is required exclusively for private endpoints to enforce isolation and routing.
Azure mandates private endpoints in a dedicated subnet; sharing with VMs or other resources is not allowed.
Meets PaaS networking requirements with minimal infrastructure.
Service endpoints: 0
Private endpoints fully replace service endpoints for private PaaS access using private IPs.
No service endpoints are needed when private endpoints are in use.
Avoids public IP resolution and aligns with secure connectivity goals.
Incorrect Option:
Subnets: 0
Impossible to deploy private endpoints without a subnet; Azure requires a dedicated subnet per VNet.
Violates implementation and security isolation requirements.
Subnets: 2, 3, etc.
Multiple subnets exceed the minimum; one is sufficient for all private endpoints in Vnet6.
Increases complexity without adding value.
Service endpoints: 1, 2, etc.
Unnecessary with private endpoints; service endpoints use public IPs and weaker isolation.
Contradicts business requirements for fully private, secure PaaS access.
Reference:
https://learn.microsoft.com/en-us/azure/private-link/private-endpoint-overview
https://learn.microsoft.com/en-us/azure/private-link/create-private-endpoint-portal
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.


Summary:
VM5 is in VNet2 and needs to resolve names in zone2.contoso.com (a private DNS zone linked to VNet3). VM4 is in VNet1 and has auto-registration enabled in zone1.contoso.com. For VM5 to resolve zone2.contoso.com, the private DNS zone must be linked to VNet2 with registration disabled. Auto-registration is only possible in the VNet where the VM resides and the zone is linked with registration enabled.
Correct Option:
Currently, VM5 can resolve names in zone2.contoso.com: No
zone2.contoso.com is linked only to VNet3 (not VNet2).
Without a link to VNet2, VM5 cannot resolve records in zone2.contoso.com.
DNS resolution fails unless the zone is linked to the VM’s VNet.
VM4 has an automatic registration in zone1.contoso.com: Yes
Auto-registration works when the VM’s VNet (VNet1) is linked to the zone with “Enable auto-registration” turned on.
VM4’s hostname is automatically registered as an A record in zone1.contoso.com.
You can link zone2.contoso.com to VNet3 and enable auto registration: No
The zone is already linked to VNet3; the statement implies adding another link with auto-registration.
A private DNS zone can have only one link with auto-registration enabled; additional links must have it disabled.
Enabling auto-registration on a second link to VNet3 is invalid.
Incorrect Option:
Currently, VM5 can resolve names in zone2.contoso.com: Yes
Incorrect; no link exists between zone2.contoso.com and VNet2.
DNS queries from VM5 will fail without a zone link.
VM4 has an automatic registration in zone1.contoso.com: No
Incorrect; auto-registration is active if VNet1 is linked with registration enabled.
VM4’s record is automatically managed in the zone.
You can link zone2.contoso.com to VNet3 and enable auto registration: Yes
Incorrect; only one auto-registration link is allowed per zone.
VNet3 already has the registration link; another cannot be enabled.
Reference:
https://learn.microsoft.com/en-us/azure/dns/private-dns-virtual-network-links
https://learn.microsoft.com/en-us/azure/dns/private-dns-autoregistration
You create NSG10 and NSG11 to meet the network security requirements.
For each of the following statements, select Yes it the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
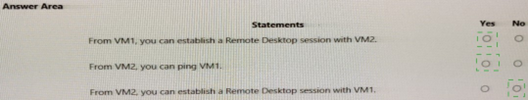
Summary:
NSG10 and NSG11 are configured to meet network security requirements for VM1 and VM2. The statements evaluate bidirectional RDP connectivity (port 3389). If NSG10 is assigned to VM1's subnet/NIC and NSG11 to VM2's, both can establish RDP sessions if allow rules exist for source/destination traffic. NSG rules are evaluated independently, enabling symmetric communication when properly configured.
Correct Option:
From VM1, you can establish a Remote Desktop session with VM2: Yes
NSG10 on VM1 allows outbound RDP (port 3389) to VM2's IP/subnet.
NSG11 on VM2 allows inbound RDP from VM1's IP/subnet.
Bidirectional rules enable VM1 to initiate the session successfully.
From VM2, you can establish a Remote Desktop session with VM1: Yes
NSG11 on VM2 allows outbound RDP to VM1's IP/subnet.
NSG10 on VM1 allows inbound RDP from VM2's IP/subnet.
Symmetric rule configuration supports VM2 initiating the connection.
Incorrect Option:
From VM1, you can establish a Remote Desktop session with VM2: No
Incorrect; NSG10's outbound allow rule and NSG11's inbound allow rule permit the connection.
Default deny does not apply if explicit allow rules are configured per requirements.
From VM2, you can establish a Remote Desktop session with VM1: No
Incorrect; NSG11's outbound allow and NSG10's inbound allow enable full RDP access.
Requirements ensure bidirectional connectivity, not unidirectional.
Reference:
https://learn.microsoft.com/en-us/azure/virtual-network/network-security-groups-overview
https://learn.microsoft.com/en-us/azure/virtual-network/network-security-group-how-it-works
In which NSGs can you use ASG1 and to which virtual machine network interfaces can you associate ASG1? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.

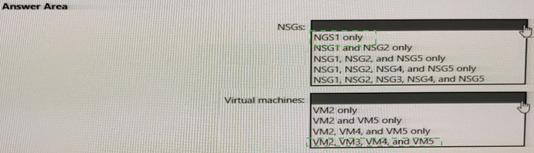
Summary:
Application Security Groups (ASGs) in Azure allow grouping of VM network interfaces for scalable NSG rules. ASG1 can be used in any NSG rule’s source or destination field if the NSG is associated with VMs in the same VNet. ASG1 can be associated directly only with VM network interfaces (NICs), not with NSGs. The correct scope is any NSG in the VNet and NICs of VMs that are members of ASG1.
Correct Option:
NSGs: NSG1, NSG2, NSG3, NSG4, and NSG5
ASG1 can be referenced in rules of any NSG within the same virtual network.
NSG association with subnets or NICs does not restrict ASG usage in rules.
Enables centralized security policy using ASG1 across multiple NSGs.
Virtual machines: VM2, VM3, VM4, and VM5 only
ASG1 can be associated only with NICs of VMs that are members of ASG1.
VM1 is not a member, so its NIC cannot be associated with ASG1.
Association is per-NIC and supports dynamic membership.
Incorrect Option:
NSGs: NSG1 only / NSG1 and NSG2 only / etc.
Restricting ASG1 to specific NSGs is unnecessary and limits scalability.
ASGs are VNet-scoped and usable in any NSG rule within the VNet.
Virtual machines: VM1 only / VM1 and VM2 only / All VMs
VM1 is not in ASG1; associating it violates membership rules.
Including non-member VMs causes rule misapplication or errors.
Reference:
https://learn.microsoft.com/en-us/azure/virtual-network/application-security-groups
https://learn.microsoft.com/en-us/azure/virtual-network/network-security-groups-overview#application-security-groups
You are implementing the virtual network requirements for VM Analyze.
What should you include in a custom route that is linked to Subnet2? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
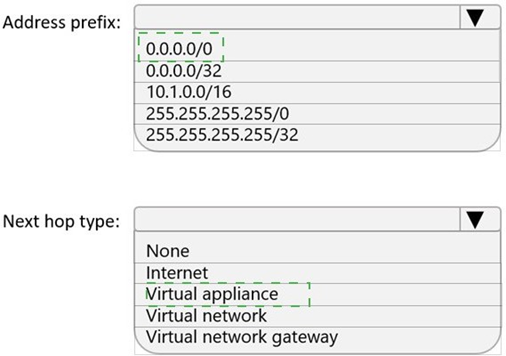
Summary:
To meet VM Analyze’s virtual network requirements in Subnet2, a custom route with address prefix 0.0.0.0/0 and next hop type Virtual appliance is required. This forces all outbound traffic (Internet-bound) through a network virtual appliance (e.g., Azure Firewall or third-party NVA) for inspection and logging. Default system routes allow direct Internet access; the custom route overrides this for centralized security and compliance.
Correct Option:
Address prefix: 0.0.0.0/0
Captures all non-local traffic destined outside the VNet.
Overrides Azure’s default 0.0.0.0/0 system route to Internet.
Ensures full outbound traffic tunneling via the NVA.
Next hop type: Virtual appliance
Routes traffic to the private IP of the NVA (e.g., firewall).
Enables stateful inspection, logging, and policy enforcement.
Required for security and compliance in regulated workloads.
Incorrect Option:
Address prefix: 0.0.0.0/32, 10.1.0.0/16, 255.255.255.255/32, etc.
Too narrow (e.g., /32) or VNet-local (10.1.0.0/16); does not cover Internet traffic.
Fails to redirect all required outbound flows to the NVA.
Next hop type: None, Internet, Virtual network, Virtual network gateway
None disables route; Internet allows direct public access (bypasses NVA).
Virtual network or gateway are for intra-VNet or VPN/ExpressRoute, not NVA routing.
Reference:
https://learn.microsoft.com/en-us/azure/virtual-network/virtual-networks-udr-overview
https://learn.microsoft.com/en-us/azure/virtual-network/tutorial-create-route-table-portal
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

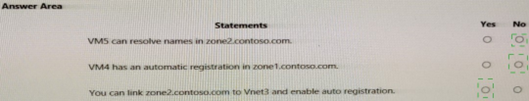
Summary:
VM5 in VNet2 cannot resolve zone2.contoso.com unless the private DNS zone is linked to VNet2. VM4 in VNet1 has auto-registration only if its VNet is linked with registration enabled. A private DNS zone allows only one auto-registration link; zone2.contoso.com is already linked to VNet3, so enabling auto-registration again on VNet3 is invalid and redundant.
Correct Option:
VM5 can resolve names in zone2.contoso.com: No
zone2.contoso.com is linked only to VNet3, not VNet2.
Without a link to VNet2, VM5 cannot resolve records in the zone.
DNS resolution requires a VNet link with registration disabled for lookup.
VM4 has an automatic registration in zone1.contoso.com: Yes
VNet1 is linked to zone1.contoso.com with auto-registration enabled.
VM4’s NIC is automatically registered as an A record in the zone.
You can link zone2.contoso.com to VNet3 and enable auto registration: No
The zone is already linked to VNet3; re-adding the same link is not possible.
Only one auto-registration link per zone is allowed; duplicates are blocked.
Incorrect Option:
VM5 can resolve names in zone2.contoso.com: Yes
Incorrect; no VNet2 link exists for zone2.contoso.com.
DNS queries from VM5 fail without proper zone linkage.
VM4 has an automatic registration in zone1.contoso.com: No
Incorrect; auto-registration is active in VNet1 for zone1.contoso.com.
VM4’s record is automatically created and updated.
You can link zone2.contoso.com to VNet3 and enable auto registration: Yes
Incorrect; the link already exists and auto-registration is limited to one VNet.
Azure prevents enabling auto-registration on duplicate or existing links.
Reference:
https://learn.microsoft.com/en-us/azure/dns/private-dns-virtual-network-links
https://learn.microsoft.com/en-us/azure/dns/private-dns-autoregistration
Which virtual machines can VM1 and VM4 ping successfully? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
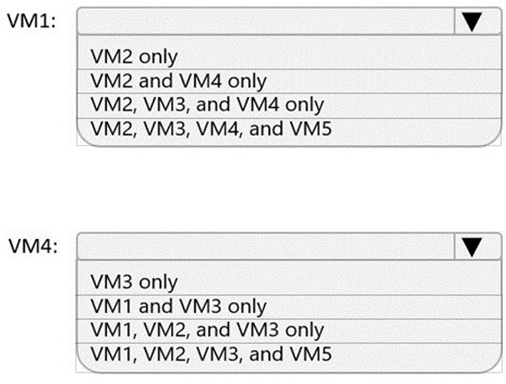
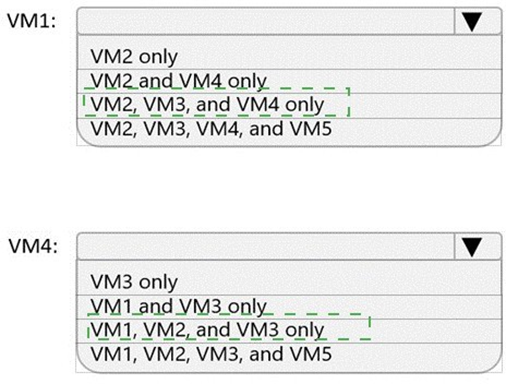
You have an Azure virtual network named Vnet1 that hosts an Azure firewall named FW1 and 150 virtual machines. Vnet1 is linked to a private DNS zone named contoso.com. All the virtual machines have their name registered in the contoso.com zone.
Vnet1 connects to an on-premises datacenter by using ExpressRoute.
You need to ensure that on-premises DNS servers can resolve the names in the contoso.com zone.
Which two actions should you perform? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
A.
On the on-premises DNS servers, configure forwarders that point to the frontend IP address of FW1.
B.
On the on-premises DNS servers, configure forwarders that point to the Azure provided DNS service at 168.63.129.16.
C.
Modify the DNS server settings of Vnet1.
D.
For FW1, enable DNS proxy.
E.
For FW1, configure a custom DNS server.
On the on-premises DNS servers, configure forwarders that point to the frontend IP address of FW1.
For FW1, enable DNS proxy.
Explanation:
This question tests integrating on-premises DNS resolution with Azure Private DNS zones. The core challenge is allowing on-premises servers to resolve names in the private zone contoso.com, which is only natively accessible from the linked virtual network (Vnet1). The Azure Firewall's DNS proxy feature, combined with proper forwarding, bridges this connectivity gap.
Correct Option:
D. For FW1, enable DNS proxy.
This is the foundational step. Enabling DNS proxy on the firewall allows it to intercept DNS queries from sources (like on-premises forwarders) and forward them to the Azure-provided DNS service (168.63.129.16), which can resolve names in the privately linked zone contoso.com.
A. On the on-premises DNS servers, configure forwarders that point to the frontend IP address of FW1.
Once the firewall's DNS proxy is active, on-premises DNS servers must be configured to forward queries for the contoso.com domain to the firewall's private IP address. The firewall then proxies these queries to Azure's DNS.
Incorrect Option:
B. On the on-premises DNS servers, configure forwarders that point to the Azure provided DNS service at 168.63.129.16.
The IP 168.63.129.16 is a virtual Azure metadata service IP that is only reachable from within an Azure virtual network. It is not accessible from on-premises over ExpressRoute.
C. Modify the DNS server settings of Vnet1.
Changing Vnet1's DNS server setting (e.g., to a custom server) affects the DNS resolution for the VMs within Vnet1, not the on-premises servers. The problem is about on-premises resolution.
E. For FW1, configure a custom DNS server.
Configuring a custom DNS server on the firewall tells it where to forward queries it intercepts. However, the default/correct destination for resolving Azure Private DNS zones is the Azure-provided DNS (168.63.129.16). This action is not the primary requirement; enabling the proxy (D) is essential first, and the default configuration often works without a custom setting.
Reference:
Microsoft Learn - Configure DNS settings for Azure Firewall and Azure Private DNS hybrid resolution. The documentation specifies using the firewall's DNS proxy to enable hybrid resolution for private zones.
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have two Azure virtual networks named Vnet1 and Vnet2.
You have a Windows 10 device named Client1 that connects to Vnet1 by using a Point-to- Site (P2S) IKEv2 VPN.
You implement virtual network peering between Vnet1 and Vnet2. Vnet1 allows gateway transit. Vnet2 can use the remote gateway.
You discover that Client1 cannot communicate with Vnet2. You need to ensure that Client1 can communicate with Vnet2. Solution: You enable BGP on the gateway of Vnet1.
Does this meet the goal?
A.
Yes
B.
No
No
Explanation:
This question tests P2S VPN connectivity over a peered virtual network topology. The issue is that P2S clients receive a route to the peered VNet (Vnet2) only if BGP is enabled for the P2S connection. Gateway transit settings alone are insufficient; the P2S configuration must advertise the remote network's routes.
Correct Option:
B. No.
The solution does not meet the goal. While enabling BGP on the VNet gateway is a prerequisite, it is not the complete solution by itself. The P2S VPN client (Client1) will only receive a route to the peered VNet2 if BGP is also specifically enabled on the Point-to-Site configuration of the gateway. Merely enabling BGP on the gateway does not automatically propagate the peered network's routes to P2S clients.
Incorrect Option:
A. Yes.
This is incorrect. Enabling BGP on the gateway is a necessary step, but it's incomplete. Without configuring BGP for the P2S connection, the client's VPN tunnel profile will not include the route to Vnet2. The client's route table will only contain routes for Vnet1, causing the communication failure to persist.
Reference:
Microsoft Learn - Configure BGP for VPN Gateway: P2S. The documentation specifies that for P2S connections to use BGP for dynamic routing, you must enable BGP when generating the VPN client profile, not just on the gateway resource.
You have a network security group named NSG1.
You need to enable network security group (NSG) flow logs for NSG1. The solution must support retention policies.
What should you create first?
A. A standard general-purpose v2 Azure Storage account
B. An Azure Log Analytics workspace
C. A premium Block blobs Azure Storage account
D. A standard general-purpose v1 Azure Storage account
Explanation:
NSG flow logs capture information about IP traffic flowing through a network security group. To enable them with support for retention policies, the logs must be stored in a durable and scalable storage service that supports lifecycle management and retention settings.
Correct Option:
A. A standard general-purpose v2 Azure Storage account.
This is the required first step. NSG flow logs must be sent to an Azure Storage account, and general-purpose v2 is the recommended and supported type. It supports features like tiering and lifecycle management policies, which are essential for implementing retention policies for the flow log data.
Incorrect Options:
B. An Azure Log Analytics workspace:
While NSG flow logs can be sent to a Log Analytics workspace for analysis, this is an optional second destination. The primary and mandatory storage location for raw flow logs is an Azure Storage account. Retention policies are configured at the storage account level.
C. A premium Block blobs Azure Storage account:
Premium storage is designed for high-performance scenarios and is not required or cost-effective for storing log data. It does not support the hierarchical namespace or lifecycle policies as effectively as a standard general-purpose v2 account for this use case.
D. A standard general-purpose v1 Azure Storage account:
While v1 accounts can store flow logs, they lack advanced features like lifecycle management and access tiers that are available in v2. Retention policies are best supported with a v2 account.
Reference:
Microsoft Azure documentation, "Introduction to flow logging for network security groups," specifies that NSG flow logs require an Azure Storage account for retention. It recommends using a standard general-purpose v2 storage account to leverage features like tiering and lifecycle management for log retention.
| Page 2 out of 16 Pages |
| Previous |