Topic 4: Mix Questions
You have an Azure subscription named Subscription1 that is linked to a Microsoft Entra tenant named contoso.com and a resource group named RG1. You create a custom role named Role1 in contoso.com. Where can you use Role1 for permission delegation?
A. contoso.com only
B. contoso.com and RG1 only
C. contoso.com and Subscription 1 only
D. contoso.com. RG1. and Subscription1
You have an Azure subscription that contains a SQL Server on Azure Virtual Machines
instance named SQt1 and a Microsoft Sentinel workspace named Sentinel1.
You need to monitor security incidents on SQL1 by using Sentinel1.
What should you do first?
A. On SQL1, enable SQL1 Server audit.
B. On SQL1. install the Connected Machine agent for Azure Arc-enabled servers.
C. From the Azure portal, create a Log Analytics workspace.
D. From Sentinel1, enable VM insights.
Note: This question is part of a series of questions that present the same scenario. Each
question in the series contains a unique solution that might meet the stated goals. Some
question sets might have more than one correct solution, while others might not have a
correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result,
these questions will not appear in the review screen.
You have an Azure subscription that contains an Azure Kubernetes Service (AKS) cluster
named AKS1 and an Azure container registry named AZCR1.
You need to ensure that AKS1 can deploy container images stored in AZCR1.
Solution: You assign the AcrPush role-based access control (RBAC) role to the systemassigned
managed identity of AKS1.
Does this meet the requirement?
A. Yes
B. No
You have an Azure key vault named KeyVault1 that contains the items shown in the following table.
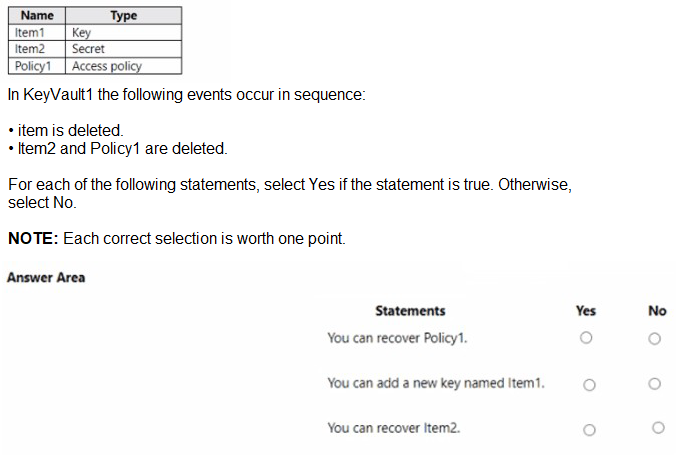
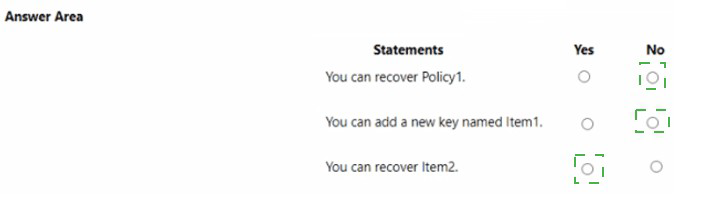
Your company uses Azure DevOps. You need to recommend a method to validate whether the code meets the company’s quality standards and code review standards. What should you recommend implementing in Azure DevOps?
A. branch folders
B. branch permissions
C. branch policies
D. branch locking
You have an Azure subscription that contains the custom roles shown in the following
table.
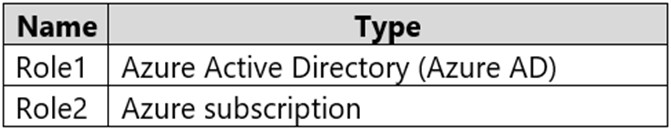
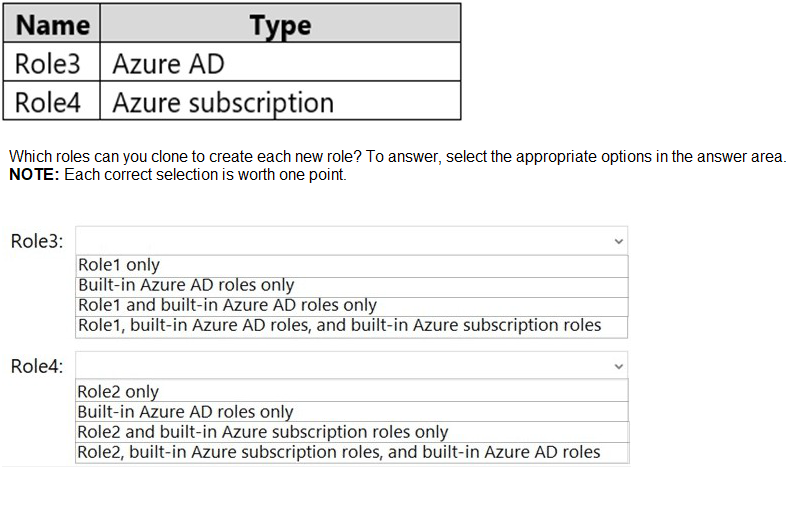
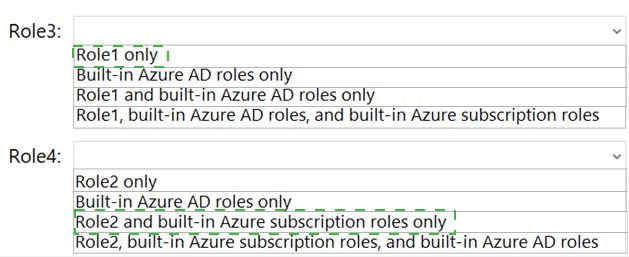
In the Azure portal, you plan to create new custom roles by cloning existing roles. The new
roles will be configured as shown in the following table.
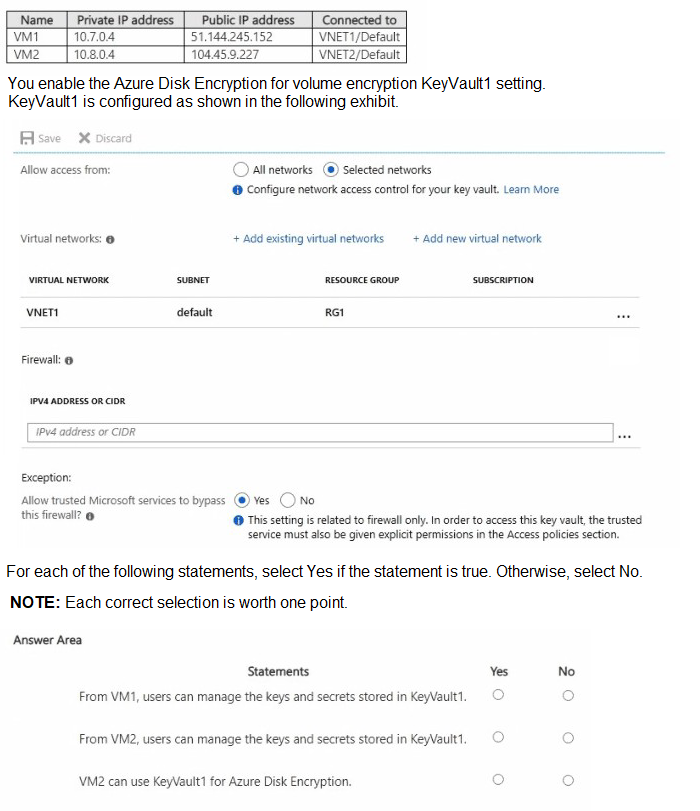
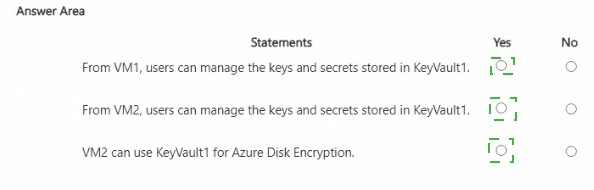
You have an Azure subscription that contains an Azure key vault named KeyVault1 and the virtual machines shown in the following table.
You have an Azure subscription named Sub1 that contains the Azure key vaults shown in the following table:
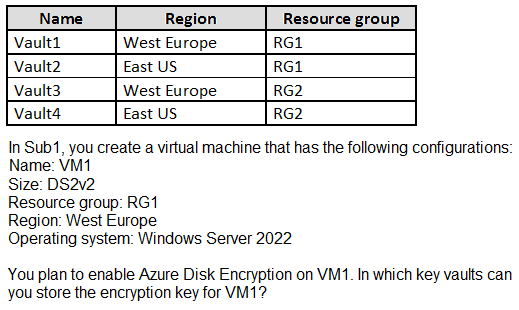
A. Vault1 or Vault3 only
B. Vault1, Vault2, Vault3, or Vault4
C. Vault1 only
D. Vault1 or Vault2 only
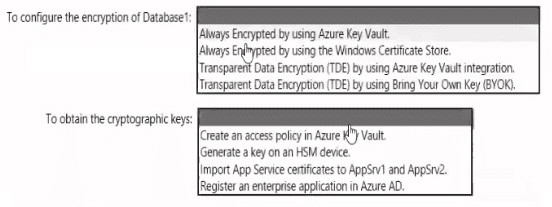
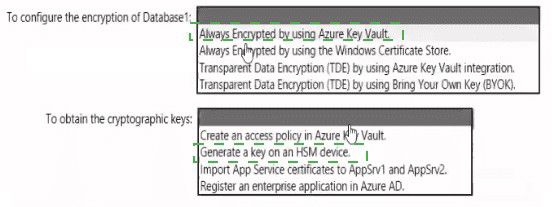
You have an Azure subscription that contains the following resources:
• An Azure key vault
• An Azure SQL database named Database1
• Two Azure App Service web apps named AppSrv1 and AppSrv2 that are configured to
use system-assigned managed identities and access Database1
You need to implement an encryption solution for Database1 that meets the following
requirements:
• The data in a column named Discount in Database1 must be encrypted so that only
AppSrv1 can decrypt the data.
• AppSrv1 and AppSrv2 must be authorized by using managed identities to obtain
cryptographic keys.
How should you configure the encryption settings fa Database1 To answer, select the
appropriate options in the answer area.
NOTE: Each correct selection is worth one point
You have an Azure virtual machine named VM1.
From Azure Security Center, you get the following high-severity recommendation: “Install
endpoint protection solutions on virtual machine”.
You need to resolve the issue causing the high-severity recommendation.
What should you do?
A. Add the Microsoft Antimalware extension to VM1.
B. Install Microsoft System Center Security Management Pack for Endpoint Protection on VM1.
C. Add the Network Watcher Agent for Windows extension to VM1.
D. Onboard VM1 to Microsoft Defender Advanced Threat Protection (Microsoft Defender ATP).
You have a Microsoft 365 tenant that uses an Azure Active Directory (Azure AD) tenant
The Azure AD tenant syncs to an on-premises Active Directory domain by using an
instance of Azure AD Connect.
You create a new Azure subscription
You discover that the synced on-premises user accounts cannot be assigned rotes in the
new subscription.
You need to ensure that you can assign Azure and Microsoft 365 roles to the synced Azure
AD user accounts.
What should you do first?
A. Change the Azure AD tenant used by the new subscription.
B. Configure the Azure AD tenant used by the new subscription to use pass-through authenticate
C. Configure the Azure AD tenant used by the new subscription to use federated authentication.
D. Configure a second instance of Azure AD Connect.
You have an Azure subscription that is linked to a Microsoft Entra tenant. The tenant uses
Microsoft Entra ID Protection.
You have 2,000 users that are each assigned a Microsoft Entra ID P2 license.
You plan to use Azure Monitor to generate an alert when a workload identity that is using
leaked credentials is detected.
You need to configure the Diagnostic setting to support the planned alert. The solution
must minimize administrative effort.
Which log category should you collect, and to
which destination should you send the logs? To answer, select the appropriate options in
the answer area.
NOTE: Each correct selection is worth one point.


| Page 5 out of 42 Pages |
| Previous |