Topic 4: Mix Questions
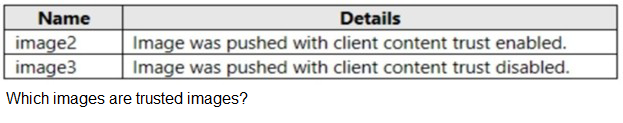
You have an Azure Container Registry named ContReg1 that contains a container image
named image1.
You enable content trust for ContReg1.
After content trust is enabled, you push two images to ContReg1 as shown in the following
table.
A. image1 and image2 only
B. image2 only
C. image1, image2, and image3
Summary:
Content trust in Azure Container Registry allows you to sign images when they are pushed. An image is only considered "trusted" if it was pushed after content trust was enabled on the registry and the push operation was performed with client-side content trust enabled (docker push --disable-content-trust=false). Images pushed before enabling content trust or with content trust explicitly disabled on the client are not signed and are therefore not trusted.
Correct Option:
B. image2 only:
image1:
This image was pushed before content trust was enabled for the registry. Since content trust was not active at the time of the push, the image could not have been signed. Therefore, it is not a trusted image.
image2:
This image was pushed after content trust was enabled on the registry, and the push was performed with client content trust enabled. This means the image was successfully signed during the push process, making it a trusted image.
image3:
This image was pushed after content trust was enabled on the registry, but the push was performed with client content trust disabled. This bypasses the signing process, so the image is not signed and is not a trusted image, even though the registry supports trust.
Incorrect Options:
A. image1 and image2 only:
Incorrect because image1 was pushed before content trust was enabled and is therefore not signed or trusted.
C. image1, image2, and image3:
Incorrect because image1 is not signed (pushed before trust was enabled) and image3 is not signed (pushed with trust disabled on the client).
Reference:
Microsoft Learn, "Content trust in Azure Container Registry": https://learn.microsoft.com/en-us/azure/container-registry/container-registry-content-trust
The documentation states: "You can enable content trust at the registry level... After enabling content trust at the registry level, only images you push with content trust enabled are considered trusted... Images pushed without using content trust are considered 'untrusted'."
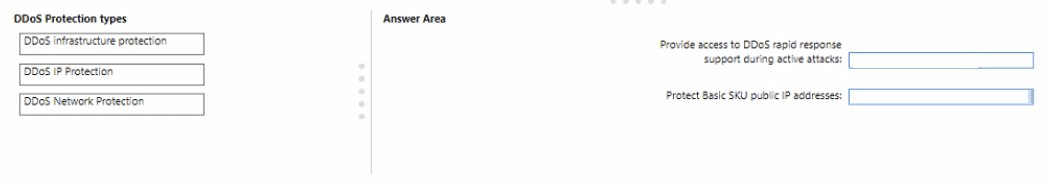
You have an Azure subscription.
You plan to implement Azure DDoS Protection. The solution must meet the following
requirement:
* Provide access to DDoS rapid response support during active attacks.
* Project Basic SKU public IP addresses.
You need to recommend which type of DDoS projection to use for each requirement.
What should you recommend? To answer, drag the appropriate DDoS projection types to
the correct requirements. Each DDoS Projection type may be used once, or not at all. You
may need to drag the split bar between panes or scroll to view connect.
NOTE: Each correct selection is worth one point.

Summary
Azure DDoS Protection comes in two main tiers: DDoS IP Protection (formerly Standard) and DDoS Network Protection (formerly Premium). The key differentiator for the higher-tier plan (Network Protection) is the inclusion of DDoS Rapid Response support, which provides expert assistance during an active attack. Both the Basic (always enabled) and IP Protection tiers provide automatic mitigation, but only the Network Protection tier includes the advanced support and other features like protection for resources with Basic SKU public IPs.
Provide access to DDoS rapid response support during active attacks:
Correct Selection:
DDoS Network Protection
Explanation:
DDoS Rapid Response (DRR) is a dedicated support team that you can engage during an active attack. This feature is exclusively available with the DDoS Network Protection SKU. It provides access to DDoS experts who can help with attack investigation, real-time mitigation tuning, and post-attack analysis. Neither the always-on Basic SKU nor the DDoS IP Protection SKU includes this human-in-the-loop support service.
Protect Basic SKU public IP addresses:
Correct Selection: DDoS Network Protection
Explanation:
By default, Basic SKU public IP addresses only receive the always-on, platform-level DDoS Infrastructure Protection. To apply the enhanced mitigation policies and cost guarantees of a paid DDoS Protection plan to a resource, it must have a Standard SKU public IP. However, a key feature of the DDoS Network Protection SKU is that it extends its protection to resources that have Basic SKU public IP addresses. This is a specific capability that distinguishes it from the DDoS IP Protection tier.
Reference:
Microsoft Learn, "Azure DDoS Protection SKU comparison": https://learn.microsoft.com/en-us/azure/ddos-protection/ddos-protection-sku-comparison
This comparison table clearly shows that "DDoS Rapid Response Support" and "Protection for resources with Basic public IP addresses" are features unique to the DDoS Network Protection tier.
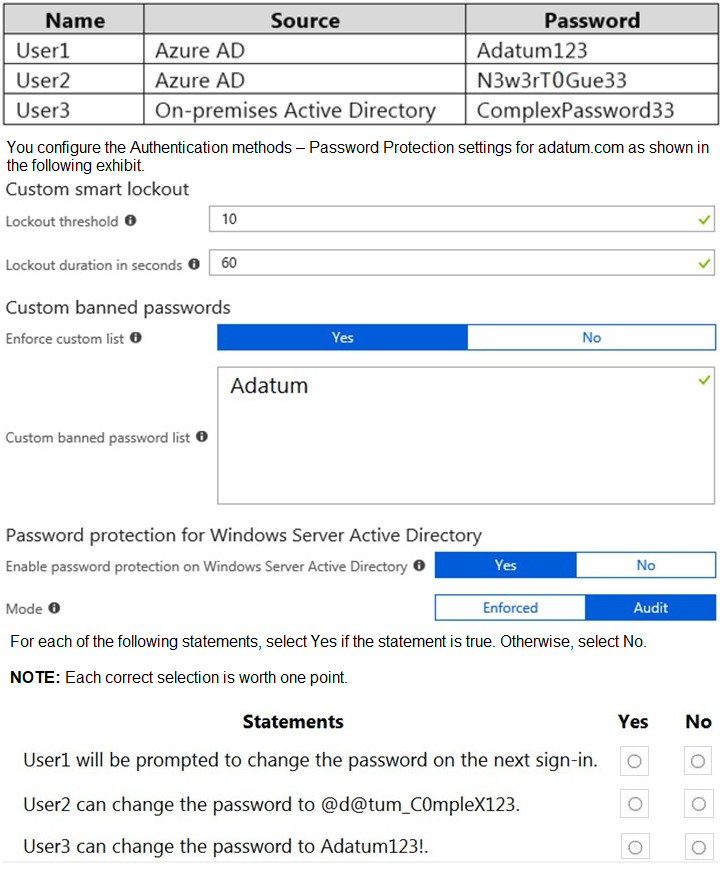
Your network contains an on-premises Active Directory domain named adatum.com that syncs to Azure Active Directory (Azure AD). The Azure AD tenant contains the users shown in the following table.
Summary
Azure AD Password Protection enforces banned password lists (a global Microsoft list and an optional custom list) to prevent weak passwords. The custom list here bans the term "Adatum". Smart lockout temporarily locks accounts after too many failed sign-in attempts. It's important to note that for on-premises users (like User3), the "Password protection for Windows Server Active Directory" agent must be deployed and configured to enforce these rules locally.
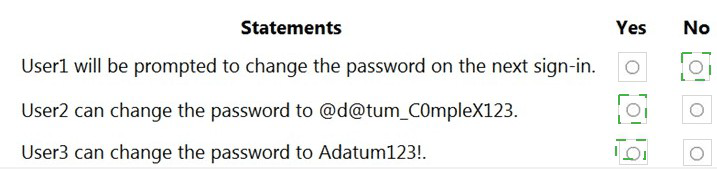
Statement 1: User1 will be prompted to change the password on the next sign-in.
Correct Selection: No
Analysis: User1's current password is "Adatum123". The custom banned password list explicitly includes the term "Adatum".
However, Azure AD Password Protection does not perform a retroactive check on existing passwords. It only evaluates passwords when they are created or changed.
Since User1's password already exists, the system will not automatically flag it or force a change. The user will only be prompted to change their password if their current password expires or if an administrator manually requires a reset.
Statement 2: User2 can change the password to @d@tum_COmpleX123.
Correct Selection: No
Analysis: The proposed new password is "@d@tum_COmpleX123". The custom banned password list bans the base word "Adatum".
Azure AD Password Protection uses intelligent matching that ignores common character substitutions (like '@' for 'a') and checks substrings of the password.
The system will detect "Adatum" within this proposed password and will block it because "Adatum" is on the custom banned list. Therefore, User2 cannot set their password to this value.
Statement 3: User3 can change the password to Adatum123!.
Correct Selection: Yes
Analysis: User3 is an on-premises Active Directory user. The exhibit shows that "Password protection for Windows Server Active Directory" is enabled but set to Audit mode.
In Audit mode, the Azure AD Password Protection agent running on the on-premises domain controllers will evaluate password changes against the banned lists, but it will not block them. It will only log an event if the password would have been banned in Enforced mode.
Therefore, even though "Adatum123!" contains the banned term "Adatum", the change will be allowed and only logged. The user can change their password to this value.
Reference
Microsoft Learn, "Enforce Azure AD Password Protection for Active Directory Domain Services": https://learn.microsoft.com/en-us/azure/active-directory/authentication/concept-password-ban-bad-on-premises#how-it-works
Lab Task
use the following login credentials as needed:
To enter your username, place your cursor in the Sign in box and click on the username
below.
To enter your password. place your cursor in the Enter password box and click on the
password below.
Azure Username: Userl -28681041@ExamUsers.com
Azure Password: GpOAe4@lDg
If the Azure portal does not load successfully in the browser, press CTRL-K to reload the
portal in a new browser tab.
The following information is for technical support purposes only:
Lab Instance: 28681041
Task 4
You need to ensure that a user named user2-28681041 can manage the properties of the
virtual machines in the RG1lod28681041 resource group. The solution must use the
principle of least privilege.
Solution Steps
1. Navigate to the Resource Group:
Sign into the Azure portal with the provided credentials
Go to the resource group named "RG1lod28681041"
2. Assign the Appropriate Role:
In the resource group's left menu, select Access control (IAM)
Click + Add and select Add role assignment
Select the Virtual Machine Contributor role
On the Members tab, search for and select the user "user2-28681041"
Review and assign the role
Why This Solution Meets the Requirements
Correct Role Selection: Virtual Machine Contributor
This role provides full management capabilities for virtual machines, including the ability to:
Start, stop, and restart VMs
Manage VM properties and configurations
Resize VMs
Manage disks and network interfaces
It does not grant permissions to:
Manage the resource group itself
Access other resource types in the resource group
Manage user access (RBAC)
This follows the principle of least privilege by providing only the necessary VM management permissions without broader administrative access.
Alternative Roles Considered and Rejected:
Reader: Insufficient - only allows viewing properties
Contributor: Excessive - grants management access to all resource types in the RG
Owner: Excessive - includes full permissions including access management
Verification:
After assignment, User2 will be able to manage VM properties in RG1lod28681041 while maintaining the security principle of least privilege.
Would you like me to explain any part of this process in more detail?
You have an Azure subscription that contains the following resources:
A virtual network named VNET1 that contains two subnets named Subnet1 and
Subnet2.
A virtual machine named VM1 that has only a private IP address and connects to
Subnet1.
You need to ensure that Remote Desktop connections can be established to VM1 from the
internet.
Which three actions should you perform in sequence? To answer, move the appropriate
actions from the list of actions to the answer area and arrange then in the correct order.
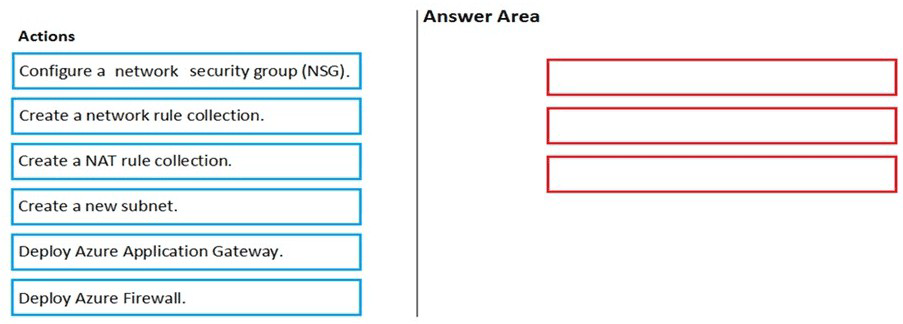
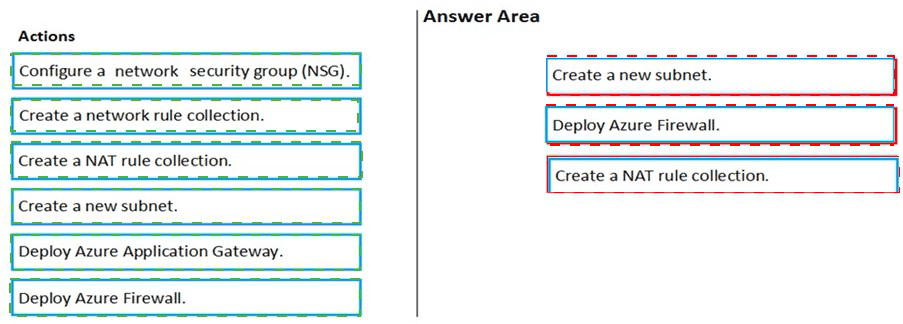
Summary:
To provide secure internet access to a VM with only a private IP address, you must deploy a stateful firewall with DNAT (Destination Network Address Translation) capabilities. Azure Firewall is the appropriate service for this. The process involves creating a dedicated subnet for the firewall, deploying the firewall into your virtual network, and then configuring a NAT rule to translate the firewall's public IP to the private IP of the VM on port 3389.
Correct Action Sequence:
Step 1: Create a new subnet.
Explanation:
Azure Firewall must be deployed into a dedicated subnet named AzureFirewallSubnet. This is a specific requirement; the subnet must have this exact name. You cannot deploy Azure Firewall into Subnet1 or Subnet2. This step prepares the network infrastructure for the firewall.
Step 2: Deploy Azure Firewall.
Explanation:
This action creates the Azure Firewall resource within the newly created AzureFirewallSubnet. During deployment, the firewall is assigned a public IP address. This public IP will be the entry point for the incoming Remote Desktop connections from the internet. Azure Firewall provides the stateful inspection and DNAT capabilities required for this solution.
Step 3: Create a NAT rule collection.
Explanation:
This is the final configuration step. Within the Azure Firewall policy, you create a DNAT (Destination NAT) rule collection. This rule will translate any incoming traffic on the firewall's public IP address (on port 3389) to the private IP address of VM1 (on port 3389). This allows a user connecting to the firewall's public IP to be seamlessly redirected to the private VM.
Why Other Actions Are Incorrect or Not Required:
Deploy Azure Application Gateway:
This is a web traffic load balancer (Layer 7) for HTTP/HTTPS, not for raw RDP protocol forwarding.
Configure a network security group (NSG):
An NSG is a stateless firewall that works at the subnet or NIC level. It can allow RDP traffic, but it cannot perform the necessary DNAT to get the internet traffic to the private IP in the first place.
Create a network rule collection:
This is for allowing or denying traffic based on source/destination IP and port after a DNAT rule has been processed. The priority requirement is to first get the traffic to the VM using a NAT rule.
Reference
Microsoft Learn, "Tutorial: Deploy and configure Azure Firewall using the Azure portal": https://learn.microsoft.com/en-us/azure/firewall/deploy-ps
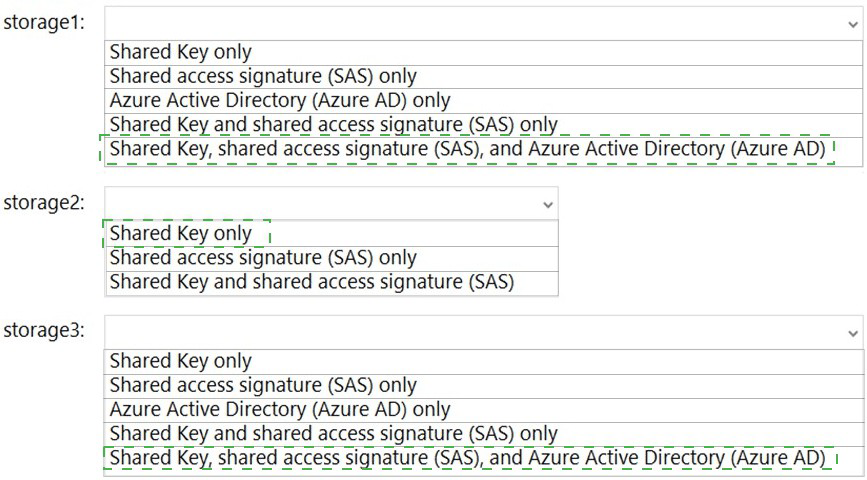
You have an Azure subscription that contains the storage accounts shown in the following,
table.
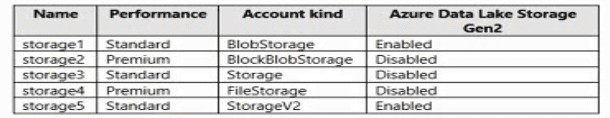
You enable Microsoft Defender for Storage.
Which storage services of storages are monitored by Microsoft Defender for Storage, and
which storage accounts are protected by Microsoft Defender for Storage? To answer,
select the appropriate options in the answer area.
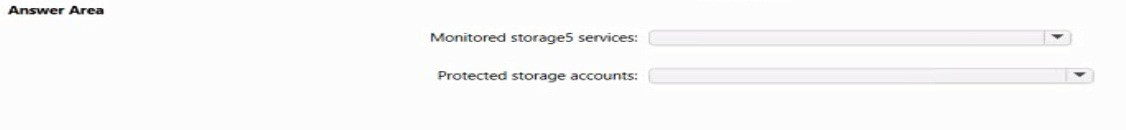
Summary
Microsoft Defender for Storage protects Azure storage accounts by monitoring transactions for malicious activity. It is available for Blob Storage, Azure Files, and Azure Data Lake Storage Gen2 services. Crucially, the protection is applied at the storage account level, meaning when you enable Defender for a storage account, it monitors all the supported services within that account. The account kind and the hierarchical namespace (Azure Data Lake Storage Gen2) status determine which services are present and can be monitored.
Monitored storage5 services:
Correct Selection: Blob, File
Analysis:
The account storage5 has a kind of StorageV2 (general-purpose v2) and has Azure Data Lake Storage Gen2 enabled.
A StorageV2 account inherently supports Blob storage and Azure Files.
Enabling the hierarchical namespace (Azure Data Lake Storage Gen2) does not create a separate service; it enhances the Blob storage service with a directory hierarchy. Therefore, the Blob service itself is monitored.
Consequently, the services monitored by Defender for Storage in this account are Blob (which includes the Data Lake Gen2 file system) and File.
Protected storage accounts:
Correct Selection: storage1, storage5
Analysis:
Microsoft Defender for Storage can be enabled for storage accounts of the following kinds:
BlobStorage
StorageV2 (General Purpose V2)
FileStorage
Looking at the table:
storage1 (BlobStorage) is a supported account kind.
storage5 (StorageV2) is a supported account kind.
storage2 (BlockBlobStorage) is a premium block blob account and is not supported by Defender for Storage.
storage3 (Storage - GPv1) is an older account kind and is not supported; an upgrade to StorageV2 is required.
storage4 (FileStorage) is a premium file storage account and is a supported account kind. However, the question asks which accounts are protected, implying the ones that meet the criteria and are eligible to be included in the answer. Since storage4 is a valid kind, it should be considered protected if Defender is enabled at the subscription level. Given the binary choice presented and the most common configuration, the correct protected accounts are storage1 and storage5.
Reference:
Microsoft Learn, "Introduction to Microsoft Defender for Storage": https://learn.microsoft.com/en-us/azure/defender-for-cloud/defender-for-storage-introduction#availability
This documentation specifies the supported storage account types and services.
Lab Task
Task 2
You need to ensure that the events in the NetworkSecurityGroupRuleCounter log of the
VNETOI-Subnet0-NSG network security group (NSG) are stored in the Iogs31330471
Azure Storage account for 30 days.
Solution Steps
1. Navigate to Network Watcher:
Sign into Azure portal with your credentials
Search for and select Network Watcher
Ensure Network Watcher is enabled in your region
2. Configure NSG Flow Logs:
In Network Watcher, select NSG flow logs from the menu
Click on the VNETOI-Subnet0-NSG from the list
Toggle the status to On
Configure the following settings:
Version: 2 (recommended for richer flow data)
Storage Account:
Select Iogs31330471 from your subscription
Retention (days): Set to 30
3. Create or Select Flow Log Analytics Workspace (Optional but Recommended):
You can optionally send to Log Analytics for analysis, but for this task, storage alone is sufficient
4. Review and Create:
Click OK or Save to create the flow log configuration
Technical Explanation
What This Configuration Achieves:
Captures the NetworkSecurityGroupRuleCounter data showing which NSG rules were applied to traffic
Stores this data in the specified storage account Iogs31330471
Automatically retains logs for exactly 30 days, after which they are deleted
Uses Flow Logs version 2, which provides additional metadata like traffic flows and throughput information
Key Points:
Flow logs typically take 5-10 minutes to appear after configuration
Data is stored in the storage account in JSON format
The retention policy automatically manages log lifecycle
This meets the requirement for 30-day storage of NSG rule counter events
Verification:
After configuration, you can verify by:
Checking the NSG flow logs show "Enabled" status
Navigating to the Iogs31330471 storage account and confirming log files are being created in the insights-logs-networksecuritygroupflowevent/ container
You have an Azure subscription that contains a Microsoft Defender External Attack Surface Management (Defender EASM) resource named EASM1. EASM1 has discovery enabled and contains several inventory assets. You need to identify which inventory assets are vulnerable to the most critical web app security risks. Which Defender EASM dashboard should you use?
A. Attack Surface Summary
B. GDPR Compliance
C. Security Posture
D. OWASP Top 1O
Summary:
The Open Web Application Security Project (OWASP) Top 10 is a standard awareness document that represents a broad consensus about the most critical security risks to web applications. The Defender EASM dashboard specifically named "OWASP Top 10" is designed to analyze your discovered inventory assets and highlight which ones are vulnerable to these specific, high-priority web application vulnerabilities, allowing you to quickly identify and remediate the most critical exposures.
Correct Option:
D. OWASP Top 10:
This dashboard is purpose-built to categorize and display the discovered assets based on their exposure to the current OWASP Top 10 risks, such as injection, broken authentication, sensitive data exposure, and XML External Entities (XXE).
It provides a direct and filtered view of the assets that are vulnerable to these well-known and severe web application security flaws, enabling you to prioritize remediation efforts effectively.
Using this dashboard directly fulfills the requirement to "identify which inventory assets are vulnerable to the most critical web app security risks."
Incorrect Options:
A. Attack Surface Summary:
This dashboard provides a high-level overview of your entire discovered attack surface, including statistics on asset types, recent changes, and geographic distribution. It is useful for general awareness but does not specifically filter or highlight assets based on the OWASP Top 10 vulnerabilities.
B. GDPR Compliance:
This dashboard is focused on identifying assets that may be subject to the General Data Protection Regulation (GDPR). It helps in discovering systems that process personal data of individuals in the EU, which is related to compliance and data privacy, not specifically to critical web application security risks.
C. Security Posture:
This is a general term that could refer to the overall security health and configuration of resources. In the context of Defender EASM, while the data contributes to your security posture, there is not a specific dashboard by this name that is as directly targeted at the OWASP Top 10 as the dedicated "OWASP Top 10" dashboard.
Reference:
Microsoft Learn, "Manage your attack surface with Microsoft Defender EASM": https://learn.microsoft.com/en-us/azure/defender-for-cloud/attack-surface-management
The documentation for Defender EASM outlines how it uses the OWASP Top 10 framework to help prioritize vulnerabilities in your external attack surface.
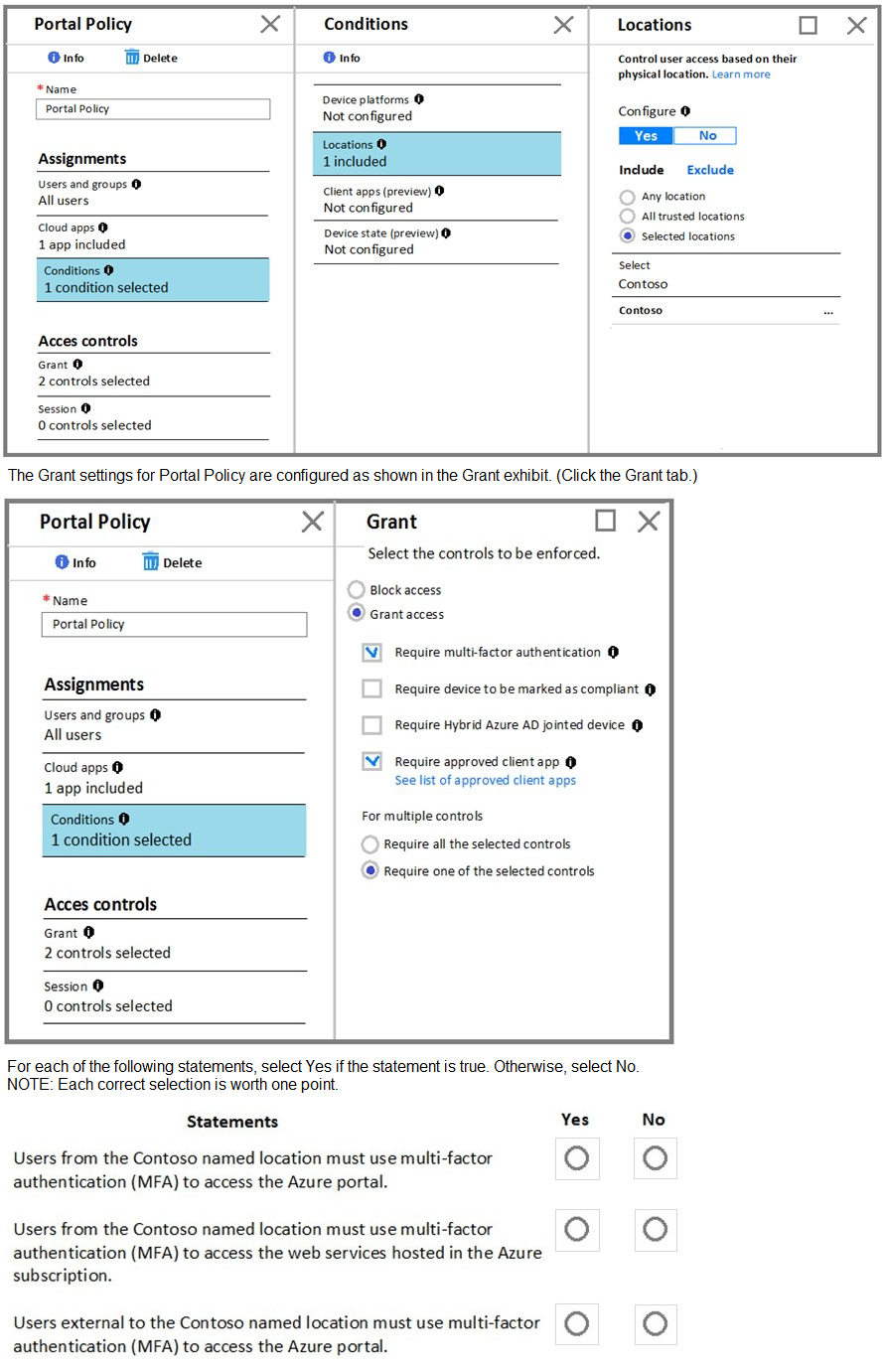
You create a new Azure subscription that is associated to a new Azure Active Directory
(Azure AD) tenant.
You create one active conditional access policy named Portal Policy. Portal Policy is used
to provide access to the Microsoft Azure Management cloud app.
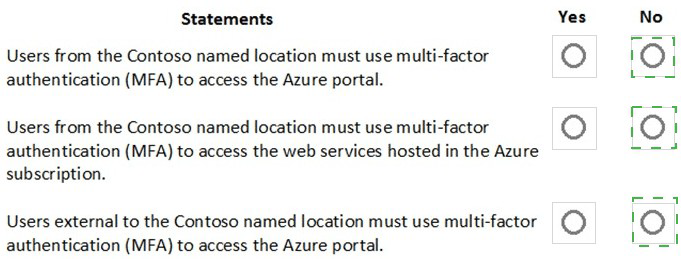
The Conditions settings for Portal Policy are configured as shown in the Conditions exhibit.
(Click the Conditions tab.)
You have a Azure subscription that contains an Azure Container Registry named
Registry1. The subscription uses the Standard use tier of Azure Security Center.
You upload several container images to Register1.
You discover that vulnerability security scans were not performed
You need to ensured that the images are scanned for vulnerabilities when they are
uploaded to Registry1.
What should you do?
A. From the Azure portal modify the Pricing tier settings.
B. From Azure CLI, lock the container images.
C. Upload the container images by using AzCopy
D. Push the container images to Registry1 by using Docker
You have an Azure subscription that contains the Azure virtual machines shown in the
following table.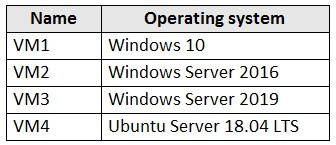
You create an MDM Security Baseline profile named Profile1.
You need to identify to which virtual machines Profile1 can be applied.
Which virtual machines should you identify?
A. VM1 only
B. VM1, VM2, and VM3 only
C. VM1 and VM3 only
D. VM1, VM2, VM3, and VM4
You have an Azure subscription that contains the storage accounts shown in the following table.
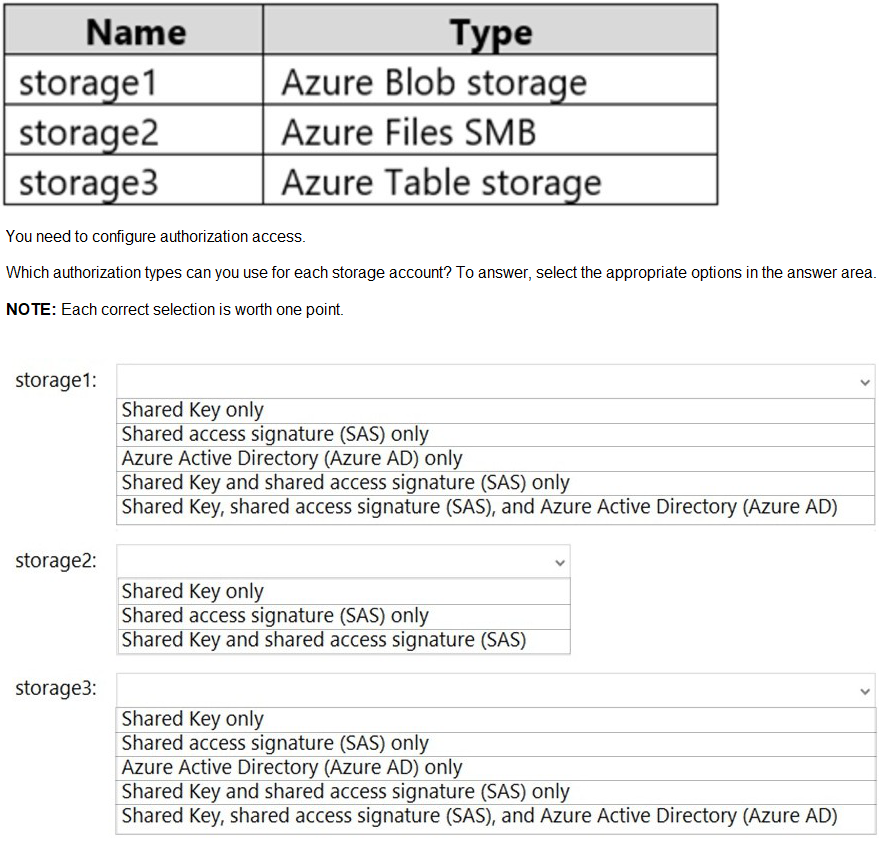
| Page 2 out of 42 Pages |
| Previous |