Topic 2: Exam Pool B
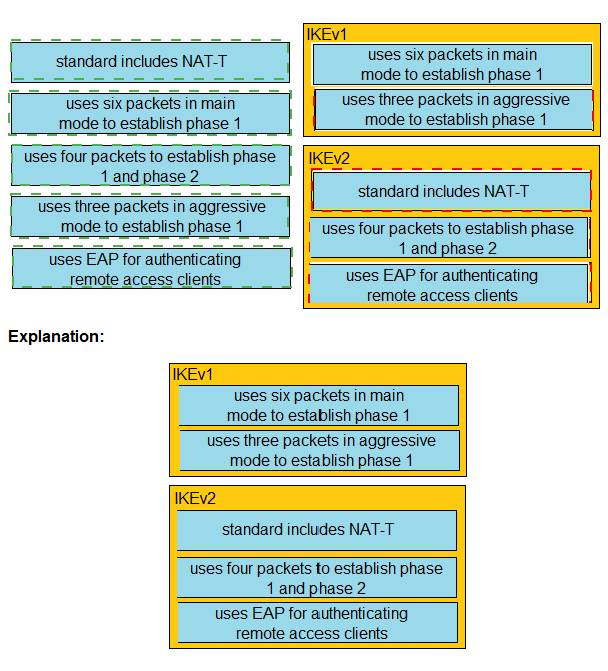
Drag and drop the descriptions from the left onto the correct protocol versions on the right.

What does Cisco AMP for Endpoints use to help an organization detect different families of malware?
A. Ethos Engine to perform fuzzy fingerprinting
B. Tetra Engine to detect malware when me endpoint is connected to the cloud
C. Clam AV Engine to perform email scanning
D. Spero Engine with machine learning to perform dynamic analysis
Explanation
Cisco AMP for Endpoints uses a multi-layered approach with several specialized engines to provide comprehensive protection. Each engine has a specific purpose.
A. Ethos Engine to perform fuzzy fingerprinting:
This is correct. The Ethos Engine is a core component of AMP's detection capability. It uses fuzzy hashing or "fuzzy fingerprinting" to identify malware families. Unlike a traditional MD5 or SHA256 hash, which changes completely if a single bit of the file is altered, fuzzy hashing can identify files that are similar. This allows AMP to detect new variants of a known malware family, even if the attacker has slightly modified the code to evade traditional signature-based detection.
Why the other options are incorrect:
B. Tetra Engine to detect malware when the endpoint is connected to the cloud:
This is incorrect. The Tetra Engine is responsible for static analysis. It performs an initial, quick scan of a file when it is first encountered, checking its characteristics and code against known malicious patterns before it is even executed. Its operation is not dependent on the endpoint's connection state to the cloud.
C. Clam AV Engine to perform email scanning:
This is incorrect. While Cisco Email Security appliances may integrate with or use techniques inspired by open-source tools, ClamAV is not a primary detection engine within the Cisco AMP for Endpoints product. AMP relies on its own proprietary engines (like Ethos, Spero, and Tetra) for endpoint protection.
D. Spero Engine with machine learning to perform dynamic analysis:
This is partially tricky but ultimately incorrect. The Spero Engine is indeed a machine learning model. However, its primary function is static analysis, not dynamic analysis. It classifies files as malicious or clean by examining the file's static properties and code structure without executing it. Dynamic analysis, which involves running a file in a sandboxed environment to observe its behavior, is a separate capability of the AMP ecosystem, often handled by the Threat Grid integration.
Reference:
This information is based on the official architecture of Cisco AMP for Endpoints. The "Engines" are a fundamental part of the product's data sheets and technical documentation.
Cisco AMP for Endpoints Data Sheet: Often references the "multiple detection engines" working in concert.
Cisco AMP Technical Documentation / White Papers: Specifically detail the roles of each engine:
Ethos: Specializes in fuzzy hashing and malware family identification.
Tetra: Provides high-performance static analysis.
Spero: A machine-learning-based static analysis engine.
In summary, the key to this question is associating the "fuzzy fingerprinting" technique, which is essential for detecting malware families and their variants, with the correct engine, which is Ethos.
Which function is the primary function of Cisco AMP threat Grid?
A. automated email encryption
B. applying a real-time URI blacklist
C. automated malware analysis
D. monitoring network traffic
Explanation for Each Option:
A. automated email encryption (Incorrect):
Automated email encryption is a feature provided by solutions like Cisco Secure Email Gateway, which secures email communication. Cisco AMP Threat Grid does not focus on email encryption; its primary role is analyzing malware, making this option unrelated to its core function. (Reference: Cisco Secure Email Gateway Datasheet.)
B. applying a real-time URI blacklist (Incorrect):
Applying a real-time URI blacklist is a capability of Cisco Umbrella, which blocks malicious domains at the DNS layer. AMP Threat Grid, however, is designed for malware analysis, not real-time URL filtering or blacklisting, rendering this option incorrect for its primary purpose. (Reference: Cisco Umbrella Overview.)
C. automated malware analysis (Correct):
The primary function of Cisco AMP Threat Grid is to provide automated malware analysis by executing suspicious files in a virtualized sandbox environment. It identifies malicious behavior, generates threat intelligence, and integrates findings with other Cisco security products, making this its core capability. (Reference: Cisco AMP Threat Grid Datasheet.)
D. monitoring network traffic (Incorrect):
Monitoring network traffic is a function of solutions like Cisco Stealthwatch or Firepower, which analyze flow data for threats. AMP Threat Grid focuses on file-based malware analysis, not real-time network traffic monitoring, making this option misaligned with its primary role. (Reference: Cisco Stealthwatch Datasheet.)
Additional Notes:
AMP Threat Grid’s malware analysis is a key topic in the 350-701 SCOR exam under endpoint security. As of 10:35 AM PKT, October 02, 2025, it remains a critical tool for threat intelligence. For details, refer to the Cisco AMP Threat Grid documentation (cisco.com) and the 350-701 Exam Blueprint (Section 2.0 Endpoint Security).
What is the role of Cisco Umbrella Roaming when it is installed on an endpoint?
A. To protect the endpoint against malicious file transfers
B. To ensure that assets are secure from malicious links on and off the corporate network
C. To establish secure VPN connectivity to the corporate network
D. To enforce posture compliance and mandatory software
Explanation
Cisco Umbrella Roaming is a lightweight module (the Umbrella Roaming Client or the DNS module of the Cisco Secure Client) that is installed on an endpoint (laptop, mobile device). Its primary function is to provide consistent DNS-layer security regardless of the endpoint's physical location.
Here’s how it fulfills the role described in option B:
On the Corporate Network:
The endpoint is protected by the organization's Umbrella policies.
Off the Corporate Network:
When the user connects to a coffee shop Wi-Fi, a home network, or a mobile hotspot, the Umbrella Roaming client continues to enforce the same DNS security policies. It directs all DNS queries through the Cisco Umbrella cloud, which blocks requests to malicious domains, including those used for phishing, malware, and ransomware. This protects the user from clicking on malicious links in emails or websites that would lead to infection, even when the endpoint is not behind the corporate firewall.
Why the other options are incorrect:
A. To protect the endpoint against malicious file transfers:
While Umbrella can block the download of known malicious files by preventing a connection to the host serving them, this is a byproduct of its DNS-layer blocking. It is not a dedicated file-scanning or anti-malware service like Cisco AMP for Endpoints.
C. To establish secure VPN connectivity to the corporate network:
This is the function of the VPN module of the Cisco Secure Client (formerly AnyConnect). While the Umbrella Roaming client and the VPN client can be part of the same client package, they are separate modules with distinct functions. Umbrella Roaming does not create a VPN tunnel.
D. To enforce posture compliance and mandatory software:
This is the function of Cisco ISE (Identity Services Engine) and the Posture module of the Cisco Secure Client. Posture assessment checks for things like antivirus installation, firewall status, and OS patches, which is a different security function than DNS-based web filtering.
Reference:
The purpose of the Umbrella Roaming client is clearly defined in its product documentation.
As per the Cisco Umbrella Administration Guide, the Roaming Client is described as providing "consistent security for your users on and off your network... The roaming computers are protected by your security policies even when they aren’t behind your firewall or connected to your VPN."
This directly confirms that its role is to protect assets from malicious internet destinations, both on and off the corporate network.
A Cisco Firepower administrator needs to configure a rule to allow a new application that has never been seen on the network. Which two actions should be selected to allow the traffic to pass without nspection? (Choose two)
A. permit
B. trust
C. reset
D. allow
E. monitor
Explanation for Each Option:
A. permit (Incorrect):
The "permit" action in Cisco Firepower allows traffic to pass but subjects it to inspection based on security policies (e.g., intrusion prevention, malware scanning). Since the requirement is to allow a new application without inspection, this option does not meet the need, as it involves full policy enforcement. (Reference:
Cisco Firepower Access Control Policy Guide.)
B. trust (Correct):
The "trust" action in Cisco Firepower allows traffic to pass through the device without any inspection, bypassing security checks like intrusion prevention or file analysis. This is suitable for a new application that has never been seen, ensuring traffic flows without interference, aligning with the requirement. (Reference:Cisco Firepower Trust Rule Configuration.)
C. reset (Incorrect):
The "reset" action terminates the connection by sending a TCP reset to both the client and server, blocking the traffic. This is the opposite of allowing the new application to pass, making it unsuitable for the administrator’s goal of enabling traffic flow. (Reference: Cisco Firepower Rule Actions Documentation.)
D. allow (Incorrect):
The "allow" action permits traffic but applies default inspection based on the access control policy, including potential deep packet inspection or threat detection. This does not satisfy the requirement to pass traffic without inspection, as it involves some level of security processing, rendering this option incorrect. (Reference: Cisco Firepower Access Control Basics.)
E. monitor (Correct):
The "monitor" action allows traffic to pass through Cisco Firepower while enabling logging and monitoring without enforcing blocking or inspection rules. Combined with "trust," it ensures the new application’s traffic flows without inspection while still providing visibility, meeting the dual requirement effectively. (Reference: Cisco Firepower Monitor Rule Configuration.)
Additional Notes:
Configuring Firepower rules is a key topic in the 350-701 SCOR exam under network security. As of 12:00 PM PKT, October 02, 2025, trust and monitor actions support new application handling. For details, refer to the Cisco Firepower Configuration Guide (cisco.com) and the 350-701 Exam Blueprint (Section 1.0 Security Concepts).
Refer to the exhibit.

An engineer configured wired 802.1x on the network and is unable to get a laptop to authenticate.
Which port configuration is missing?
A. authentication open
B. dotlx reauthentication
C. cisp enable
D. dot1x pae authenticator
Explanation:
The configuration shows several 802.1X-related commands, but it is missing the fundamental command that enables the 802.1X protocol on the port.
Let's break down the configuration and the role of the missing command:
D) dot1x pae authenticator is CORRECT.
The command dot1x pae authenticator is what tells the switch port to act as the Port Access Entity (PAE) for 802.1X. The PAE is the component responsible for enforcing authentication on the port. Without this command, the switch will not initiate the 802.1X process with the connecting device, even though other parameters like authentication port-control auto are set. This is a very common oversight.
Why the other options are incorrect:
A) authentication open is INCORRECT.
The authentication open command is used in WebAuth (centralized web authentication) scenarios, not for standard 802.1X machine authentication. It is not required for this configuration.
B) dot1x reauthentication is INCORRECT.
The dot1x reauthentication command enables periodic reauthentication of the client. While it's a good practice, it is not required for the initial authentication to occur. Its absence would not prevent the first authentication attempt.
C) cisp enable is INCORRECT.
The cisp enable command is used to enable the Cisco Inter-Switch Link Protocol (CISL) for VTP, which is completely unrelated to 802.1X authentication. This is a distractor.
Reference:
Cisco IOS Security Command Reference, "dot1x pae": The official documentation states this command is used to "enable 802.1X authentication on the port" and specifies the role of the port (authenticator, supplicant, or both).
Cisco 802.1X Configuration Guides: The configuration examples for enabling 802.1X consistently show the dot1x pae authenticator command as a necessary step to activate the protocol on an interface.
In which situation should an Endpoint Detection and Response solution be chosen versus an Endpoint Protection Platform?
A. when there is a need for traditional anti-malware detection
B. when there is no need to have the solution centrally managed
C. when there is no firewall on the network
D. when there is a need to have more advanced detection capabilities
Explanation
This question tests your understanding of the evolution and different roles of endpoint security solutions.
Endpoint Protection Platform (EPP) is a preventative solution. It's the modern evolution of traditional antivirus. Its primary goal is to block known threats at the point of entry. It does this using signatures, heuristics, and machine learning to stop malware from executing. It focuses on the question: "Can I prevent this bad thing from happening?"
Endpoint Detection and Response (EDR) is a detective and responsive solution. It operates on the assumption that some advanced threats will inevitably bypass preventative controls (like an EPP). EDR continuously monitors endpoint activity (processes, network connections, file changes, etc.), records this data, and uses advanced analytics, behavioral analysis, and threat intelligence to identify suspicious activities that indicate a breach. It focuses on the questions: "Has something bad already gotten in? What did it do? How do I find and remove it?"
Therefore, you choose an EDR solution specifically when you need to go beyond basic prevention and require advanced capabilities to detect, investigate, and respond to sophisticated, evasive, or ongoing attacks that have bypassed your first line of defense.
Detailed Breakdown of Incorrect Options
B. When there is a need for traditional anti-malware detection
Why it is incorrect:
This is the exact opposite of the correct logic. If your primary need is traditional anti-malware detection (blocking viruses, worms, and known ransomware), then an Endpoint Protection Platform (EPP) is the appropriate choice. EPPs are built for this purpose. Choosing an EDR solely for this would be overkill and would underutilize its core strengths. In fact, most modern EDR solutions are now bundled with or built upon a strong EPP foundation.
C. When there is no need to have the solution centrally managed
Why it is incorrect:
Both EPP and EDR solutions are almost exclusively centrally managed. A central management console is a critical feature for both, allowing security teams to set policies, deploy updates, and view the security status of all endpoints. EDR, in particular, is highly dependent on central management because its value comes from correlating data from all endpoints to detect lateral movement and coordinated attacks. A non-centrally managed EDR would be virtually useless.
D. When there is no firewall on the network
Why it is incorrect:
While having a firewall is a fundamental network security control, its absence is not the deciding factor between EPP and EDR. Both EPP and EDR provide host-based security on the endpoint itself, which is a different layer of defense (host-based vs. network-based). If there is no network firewall, you have a significant security gap that neither EPP nor EDR is designed to fill. You would need both a network firewall and an appropriate endpoint solution. The choice between EPP and EDR is based on the type of threats you need to address on the endpoint, not the presence or absence of a network control.
Reference and Modern Context:
Gartner Definitions:
Gartner, a leading IT research firm, clearly distinguishes these categories. They define EPP as a solution "to prevent file-based malware, detect malicious activity, and provide the investigation and remediation capabilities needed to respond to dynamic security incidents." They define EDR as a solution "that records endpoint-system-level behaviors... and provides the ability to search, discover, and investigate those behaviors for signs of malicious activity."
The Market Trend:
XDR: The market is now converging towards Extended Detection and Response (XDR), which integrates EPP, EDR, and other security controls (like email, network, and cloud) into a single, unified platform for even more advanced threat detection and response.
Key Takeaway:
For the exam, remember this simple analogy:
EPP is like a lock on your door – it keeps most common intruders out.
EDR is like a security camera and alarm system – it tells you when someone has picked the lock, broken a window, and is now moving through your house. You choose the cameras and alarms when you need that advanced level of detection and investigation.
Which command enables 802.1X globally on a Cisco switch?
A.
dot1x system-auth-control
B.
dot1x pae authenticator
C.
authentication port-control aut
D.
aaa new-model
dot1x system-auth-control
An engineer wants to automatically assign endpoints that have a specific OUI into a new endpoint group. Which probe must be enabled for this type of profiling to work?
A.
NetFlow
B.
NMAP
C.
SNMP
D.
DHCP
NMAP
http://www.network-node.com/blog/2016/1/2/ise-20-profiling
Drag and drop the Firepower Next Generation Intrusion Prevention System detectors from
the left onto the correct definitions on the right.

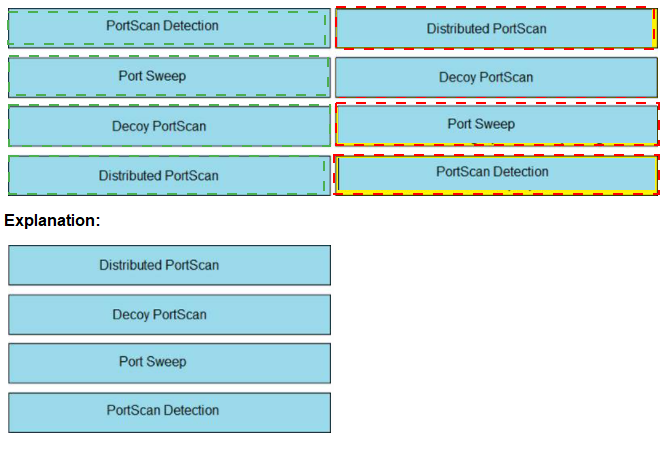
A picture containing table
Description automatically generated
What is a benefit of performing device compliance?
A. Verification of the latest OS patches
B. Device classification and authorization
C. Providing multi-factor authentication
D. Providing attribute-driven policies
Explanation:
Device compliance (or posture assessment) is the process of checking an endpoint's "health" against a set of security policies before granting it network access. The result of this check becomes a powerful attribute that can be used for dynamic policy enforcement.
D) Providing attribute-driven policies is CORRECT.
This is the primary benefit. Once a device's compliance state is determined (e.g., "Compliant," "Non-Compliant," "Out-of-Date"), this information is used as an attribute in authorization policies. This allows you to create granular, attribute-driven policies such as:
IF Device Compliance = Compliant THEN grant access to the Corporate Network VLAN.
IF Device Compliance = Non-Compliant THEN grant access only to the Remediation VLAN.
This enables dynamic and automated network access control based on the real-time security state of the device.
Why the other options are incorrect:
A) Verification of the latest OS patches is INCORRECT.
This is an example of a check that is performed during the compliance process, not the ultimate benefit. Verifying patches is a means to an end; the benefit is using that verification result to enforce a policy.
B) Device classification and authorization is INCORRECT.
Device classification (profiling) is a separate function that identifies what type of device it is (e.g., Windows laptop, iPhone). Authorization is the act of granting access. Compliance is a specific check that provides an input for authorization, but it is not the same as classification.
C) Providing multi-factor authentication is INCORRECT.
Multi-factor authentication (MFA) is a separate security control used to verify a user's identity. It is not related to checking the compliance state of a device.
Reference:
Cisco ISE Administrator Guide, "Posture Service": The documentation explains that the goal of posture assessment is to "assess the state of an endpoint" and then "make an authorization decision based on the endpoint's compliance," which is the definition of an attribute-driven policy.
A network engineer is configuring DMVPN and entered the crypto isakmp key cisc0380739941 address 0.0.0.0 command on hostA. The tunnel is not being established to hostB. What action is needed to authenticate the VPN?
A. Change isakmp to ikev2 in the command on hostA.
B. Enter the command with a different password on hostB.
C. Enter the same command on hostB.
D. Change the password on hostA to the default password.
Explanation
The command crypto isakmp key cisc0380739941 address 0.0.0.0 configures a pre-shared key (PSK) for the Phase 1 (ISAKMP) tunnel establishment in a DMVPN network.
C. Enter the same command on hostB:
This is correct. For two IPSec peers to successfully authenticate each other using a pre-shared key, they must both be configured with the identical key. The address 0.0.0.0 part of the command means this key is used for any peer, regardless of its IP address. Therefore, for hostA and hostB to form a tunnel, hostB must have the exact same command (crypto isakmp key cisc0380739941 address 0.0.0.0) in its configuration. The tunnel is failing because hostB is likely configured with a different key or no key at all.
Why the other options are incorrect:
A. Change isakmp to ikev2 in the command on hostA:
This is incorrect. The command syntax crypto isakmp key is the correct way to configure a pre-shared key for IKEv1. While IKEv2 is more modern and has advantages, the problem described is not the version of IKE but the fundamental lack of a matching key on the peer. Changing to IKEv2 on one side without also configuring a matching key on the other side would still result in a failure.
B. Enter the command with a different password on hostB:
This is the opposite of what is required. Using a different password on hostB would guarantee that the authentication fails, as the two peers would be presenting different shared secrets.
D. Change the password on hostA to the default password:
This is incorrect. There is no "default password" for ISAKMP pre-shared keys. They are explicitly configured by the administrator for security. Using a default, even if one existed, would be a major security risk.
Reference:
This is a fundamental principle of IPSec VPN configuration, covered in both the SCOR 350-701 exam blueprint and the ENCOR 350-401 exam.
Cisco IOS Command Reference for crypto isakmp key: The documentation states that the key must match for the peers to establish a secure connection.
IPSec VPN Fundamentals: The Internet Key Exchange (IKE) protocol, which uses ISAKMP, requires that both parties can prove they know the same pre-shared secret to authenticate the tunnel setup.
In summary, the core rule for pre-shared keys in IPSec is symmetry: both peers must be configured with the exact same key. The solution is to apply the identical crypto isakmp key command to the other peer (hostB).
| Page 9 out of 61 Pages |
| Previous |