Topic 2: Exam Pool B
Which type of algorithm provides the highest level of protection against brute-force attacks?
A.
PFS
B.
HMAC
C.
MD5
D.
SHA
SHA
What is a difference between FlexVPN and DMVPN?
A. DMVPN uses IKEv1 or IKEv2, FlexVPN only uses IKEv1
B. DMVPN uses only IKEv1 FlexVPN uses only IKEv2
C.
FlexVPN uses IKEv2, DMVPN uses IKEv1 or IKEv2
D. FlexVPN uses IKEv1 or IKEv2, DMVPN uses only IKEv2
FlexVPN uses IKEv2, DMVPN uses IKEv1 or IKEv2
Correct Answer: C. FlexVPN uses IKEv2, DMVPN uses IKEv1 or IKEv2
This is correct because:
FlexVPN is an IKEv2-only architecture. Its very design and feature set (like stateful failover, client mobility, and simplified configuration) are built directly on top of IKEv2's improvements and new payloads. It is a modern solution that mandates IKEv2.
DMVPN is a protocol-agnostic overlay. Its primary innovation is the use of the Next Hop Resolution Protocol (NHRP) to create dynamic multipoint GRE tunnels. The encryption (IPsec) for these tunnels can be established using the more traditional and widely deployed IKEv1 or the more modern IKEv2.
Detailed Breakdown of Incorrect Options
A. DMVPN uses IKEv1 or IKEv2, FlexVPN only uses IKEv1
This option is incorrect because it reverses the IKEv2 dependency.
Why "DMVPN uses IKEv1 or IKEv2" is correct:
As explained above, this part of the statement is true. DMVPN was originally deployed with IKEv1 and is still commonly used that way. However, Cisco has fully supported and documented DMVPN Phase 3 configurations using IKEv2, leveraging its benefits like better reliability and built-in dead peer detection (DPD).
Why "FlexVPN only uses IKEv1" is catastrophically wrong:
This is the core error. FlexVPN was introduced after IKEv2 was standardized (RFC 5996) and was designed specifically to leverage its advantages. Using IKEv1 with FlexVPN is not just unsupported; it's technically impossible because the FlexVPN configuration commands on Cisco IOS/IOS-XE (e.g., ikev2 profile, ikev2 authorization policy) are exclusive to the IKEv2 protocol stack. FlexVPN would simply not function with IKEv1.
In a Nutshell:
This option takes a true fact about DMVPN and pairs it with a completely inverted and false fact about FlexVPN.
B. DMVPN uses only IKEv1 FlexVPN uses only IKEv2
This option is half-right and half-wrong.
Why "DMVPN uses only IKEv1" is incorrect:
This is an absolute statement ("only") that is false. While IKEv1 was the dominant and initially the only option for many years, DMVPN evolved. Cisco explicitly supports and provides configuration guides for DMVPN with IKEv2. The ability to use IKEv2 provides benefits such as:
MOBIKE Support:
Allows a mobile client to change its IP address (e.g., moving from Wi-Fi to cellular) without tearing down the IPsec tunnel.
Improved Reliability:
IKEv2 has more robust built-in mechanisms for dead peer detection and session resumption.
Simplified NAT Traversal:
IKEv2 handles NAT-T more seamlessly.
Denying that DMVPN can use IKEv2 ignores the last decade of its development and real-world deployments.
Why "FlexVPN uses only IKEv2" is correct: This part is 100% accurate, as previously established. FlexVPN is an IKEv2-native technology.
In a Nutshell:
This option fails because it incorrectly imposes an absolute limitation on DMVPN that does not exist in reality.
D. FlexVPN uses IKEv1 or IKEv2, DMVPN uses only IKEv2
This option is almost entirely backwards.
Why "FlexVPN uses IKEv1 or IKEv2" is incorrect:
This suggests FlexVPN is as flexible as DMVPN regarding the IKE protocol version, which it is not. There is no "IKEv1 profile" or equivalent configuration for a FlexVPN setup. The entire FlexVPN paradigm—from the initial handshake to the advanced features like server-led rekeying and stateful switchover—is dependent on IKEv2-specific exchanges and payloads.
Why "DMVPN uses only IKEv2" is incorrect:
This is the opposite of the truth. While using IKEv2 with DMVPN is a best practice for new deployments, the vast majority of existing DMVPN deployments in the world, and a huge body of historical documentation and training, are based on IKEv1. To claim DMVPN only uses IKEv2 would render a massive number of production networks "non-standard," which is not the case. DMVPN's design is separate from the IKE version used to secure it.
In a Nutshell:
This option completely swaps the characteristics of the two technologies. It assigns FlexVPN's flexibility to DMVPN and DMVPN's IKEv2 capability to FlexVPN.
Exam Tip and Conceptual Takeaway
For the exam, remember this simple analogy:
DMVPN is like a "Framework." It defines how spokes discover each other (NHRP) and how traffic flows (mGRE). You can secure this framework with different "locks"—either the older, reliable lock (IKEv1) or the newer, smarter lock (IKEv2).
FlexVPN is like a "Pre-built Secure Vault." The vault and the lock (IKEv2) are manufactured as a single, integrated system. You cannot take the old lock (IKEv1) and put it on this new vault; it's designed to work only with its native, modern lock.
When configuring ISAKMP for IKEv1 Phase1 on a Cisco IOS router, an administrator
needs to input the
command crypto isakmp key cisco address 0.0.0.0. The administrator is not sure what the
IP addressing in this command issued for. What would be the effect of changing the IP
address from 0.0.0.0 to 1.2.3.4?
A.
The key server that is managing the keys for the connection will be at 1.2.3.4
B.
The remote connection will only be allowed from 1.2.3.4
C.
The address that will be used as the crypto validation authority
D.
All IP addresses other than 1.2.3.4 will be allowed
The remote connection will only be allowed from 1.2.3.4
Explanation for Each Option:
A. The key server that is managing the keys for the connection will be at 1.2.3.4 (Incorrect):
The crypto isakmp key command configures a pre-shared key for IKE authentication, not for designating a key server. Key servers are handled separately in scenarios like GETVPN with commands like crypto gdoi. Changing the address specifies the peer IP for key association, not a key management server role. This option misinterprets the command's purpose in ISAKMP policy. (Reference: Cisco IOS Security Configuration Guide, ISAKMP Pre-Shared Keys section.)
B. The remote connection will only be allowed from 1.2.3.4 (Correct):
The crypto isakmp key
C. The address that will be used as the crypto validation authority (Incorrect):
There is no concept of a "crypto validation authority" in ISAKMP configuration. This command deals with pre-shared keys for peer authentication during IKE negotiation, not certificate authorities or validation entities. Certificate-based auth uses crypto ca commands. Altering the address simply scopes the key to a peer IP, not validation roles. (Reference: Cisco 350-701 SCOR Exam Topics - VPN Technologies; IOS Security Commands Reference.)
D. All IP addresses other than 1.2.3.4 will be allowed (Incorrect):
This inverts the command's behavior. Specifying a particular IP like 1.2.3.4 restricts the pre-shared key to that peer only, denying others using the same key. Using 0.0.0.0 would allow all, but changing to a specific IP enforces strict peer matching for security, preventing unauthorized connections. This option incorrectly describes the restrictive effect. (Reference: Cisco VPN Configuration Guide, IKE Pre-Shared Key Restrictions.)
Additional Notes:
In Cisco IOS, the crypto isakmp key command is crucial for IKEv1 VPN setups, covered in the 350-701 SCOR exam under Secure VPN technologies. 0.0.0.0 is often used for dynamic peers (e.g., road warriors), while specific IPs suit site-to-site. For details, refer to Cisco's IOS Security Configuration Guide (cisco.com, search "crypto isakmp key") and the 350-701 Exam Blueprint (Section 3.0 Security Concepts). Best practice: Use specific IPs for better security. More questions?
Which two features of Cisco Email Security can protect your organization against email threats? (Choose two)
A.
Time-based one-time passwords
B.
Data loss prevention
C.
Heuristic-based filtering
D.
Geolocation-based filtering
E.
NetFlow
Data loss prevention
Geolocation-based filtering
https://www.cisco.com/c/en/us/td/docs/security/esa/esa11-
0/user_guide_fs/b_ESA_Admin_Guide_11_0/b_ESA_Admin_Guide_chapter_00.html
Drag and drop the VPN functions from the left onto the description on the right.
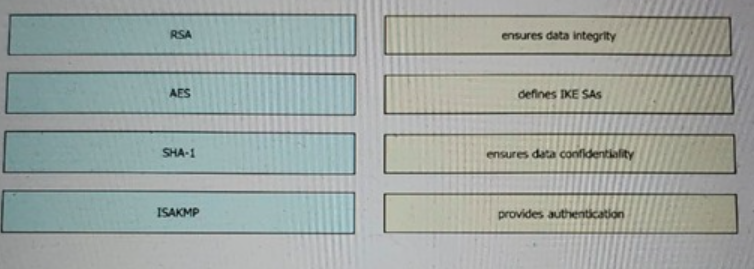
The purpose of message integrity algorithms, such as Secure Hash Algorithm
(SHA-1), ensures data has notbeen changed in transit. They use one way hash functions to determine if data has been changed.SHA-1, which is also known as HMAC-SHA-1 is a
strong cryptographic hashing algorithm, stronger thananother popular algorithm known as
Message Digest 5 (MD5). SHA-1 is used to provide data integrity (toguarantee data has not
been altered in transit) and authentication (to guarantee data came from the source itwas
supposed to come from). SHA was produced to be used with the digital signature
standard.A VPN uses groundbreaking 256-bit AES encryption technology to secure your
online connection againstcyberattacks that can compromise your security. It also offers
robust protocols to combat malicious attacks and reinforce your online identity.IKE SAs
describe the security parameters between two IKE devices, the first stage in establishing
IPSec.
Which risk is created when using an Internet browser to access cloud-based service?
A. misconfiguration of infrastructure, which allows unauthorized access
B. intermittent connection to the cloud connectors
C. vulnerabilities within protocol
D. insecure implementation of API
Explanation
When you use an Internet browser to access a cloud-based service (like Salesforce, Office 365, or Cisco WebEx), the entire interaction is based on web protocols, primarily HTTP/HTTPS, along with TLS for encryption.
C. vulnerabilities within protocol:
This is the most direct and universal risk created by this specific action. The protocols themselves can have inherent vulnerabilities. For example:
Vulnerabilities in the TLS/SSL protocol (e.g., Heartbleed, POODLE) could compromise the encryption protecting your data in transit.
Weaknesses in the HTTP protocol itself or its implementations could be exploited.
The browser's interpretation and execution of these protocols can introduce risks. This option describes a fundamental risk category inherent to using the web as a platform.
Why the other options are incorrect:
A. misconfiguration of infrastructure, which allows unauthorized access:
This is a significant risk in the cloud, but it is a risk created by the cloud service provider or the organization's cloud administrators. It is not a direct risk created by the simple act of an end-user accessing the service via a browser. The user is a consumer of the infrastructure, not the one creating the misconfiguration risk.
B. intermittent connection to the cloud connectors:
This describes a reliability or performance issue, not a security risk. While an intermittent connection can be frustrating and impact availability, it does not directly create a security vulnerability like data theft or unauthorized access.
D. insecure implementation of API:
This is a very important risk in cloud security. However, when a user accesses a service through a standard web browser, they are typically interacting with a web application front-end. The browser consumes the APIs that the web front-end uses, but the risk of an "insecure implementation" lies with the cloud service provider's developers. The act of using the browser doesn't create this risk; it merely exposes the user to it if the provider's implementation is flawed. Option C is a broader and more fundamental category of risk that encompasses the communication channel itself.
Reference
This concept falls under the domain of cloud security and web application security. The risk associated with underlying protocols is a foundational concept.
OWASP Top 10: While not listing "protocol vulnerabilities" as a separate category, many issues (like A09:2021-Security Logging and Monitoring Failures) can be related to how protocols are handled.
Cloud Security Alliance (CSA) Guidance: Highlights threats related to data breaches and insecure interfaces/APIs, which are often exploited through protocol-level weaknesses.
General Web Security Principles: The entire security model of the web is built upon the integrity of protocols like HTTPS/TLS. A vulnerability in these protocols is a systemic risk for every user accessing any cloud service.
In summary, while all options represent potential issues in a cloud ecosystem, the risk that is most directly and universally created by the act of using a web browser is the exposure to vulnerabilities within the web protocols themselves.
Which two kinds of attacks are prevented by multifactor authentication? (Choose two)
A. phishing
B. brute force
C. man-in-the-middle
D. DDOS
E. teardrop
Explanation:
Multi-Factor Authentication adds a critical layer of security by requiring a second (or more) form of verification beyond just a password. This directly mitigates attacks that target the weakness of single-factor (password-only) authentication.
Let's break down why A and B are correct and the others are not:
A) Phishing is CORRECT.
In a phishing attack, a user is tricked into revealing their credentials (username and password) to a fake login page. With MFA enabled, the stolen password alone is useless to the attacker. They would also need to possess the user's second factor (e.g., their phone for a push notification or a hardware token), which they typically cannot obtain through the phishing attack itself.
B) Brute force is CORRECT.
In a brute force attack, an attacker uses automated tools to try many different password combinations until they find the correct one. MFA effectively neutralizes this attack. Even if the attacker correctly guesses the password through brute force, they cannot complete the login without the second factor, making the attack impractical.
Why the other options are incorrect:
C) Man-in-the-middle (MITM) is INCORRECT.
While MFA can make a MITM attack more difficult, it does not inherently prevent it. In a sophisticated real-time MITM attack, the attacker can intercept the user's password and the one-time code from the second factor as they are entered, and then immediately use both to authenticate to the real service. Modern MFA solutions like FIDO2/WebAuthn are designed to resist these attacks, but traditional TOTP or SMS-based MFA can be vulnerable.
D) DDoS (Distributed Denial-of-Service) is INCORRECT.
A DDoS attack aims to overwhelm a service's resources (like a web server) to make it unavailable. MFA is an authentication mechanism and has no bearing on the network volume or resource exhaustion that characterizes a DDoS attack.
E) Teardrop is INCORRECT.
A teardrop attack is a very old type of Denial-of-Service attack that exploits fragmentation reassembly bugs in operating systems. It is unrelated to user authentication and is prevented by modern OS patches and network security devices, not MFA.
Reference:
NIST Special Publication 800-63B - Digital Identity Guidelines: This standard strongly recommends the use of multi-factor authentication to mitigate credential-based attacks like phishing and brute-forcing.
Cisco Duo Security & MFA Best Practices: Cisco's own documentation for its Duo MFA product consistently highlights protection against "stolen passwords" and "credential stuffing" (a form of brute force) as primary benefits.
Drag and drop the steps from the left into the correct order on the right to enable
AppDynamics to monitor an EC2 instance in Amazon Web Services

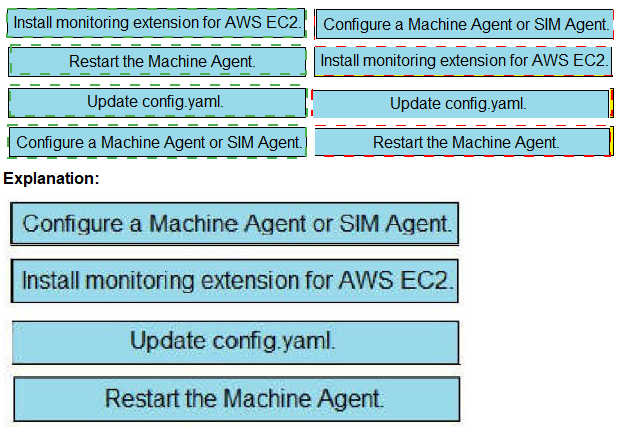
Graphical user interface, text, application, email
Description automatically generated
Refer to the exhibit.
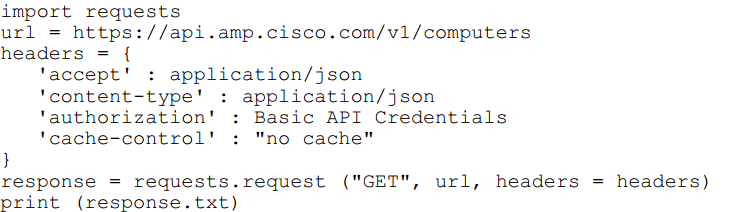
What will happen when this Python script is run?
A. The compromised computers and malware trajectories will be received from Cisco AMP
B. The list of computers and their current vulnerabilities will be received from Cisco AMP
C. The compromised computers and what compromised them will be received from Cisco AMP
D. The list of computers, policies, and connector statuses will be received from Cisco AMP
Explanation
This Python script is making a GET request to the Cisco Advanced Malware Protection (AMP) for Endpoints API. Let's break down the specific API endpoint being called:
The URL is: https://api.amp.cisco.com/v1/computers
According to the official Cisco AMP for Endpoints API Documentation, the /v1/computers endpoint is used to "Get a list of computers."
The data returned by this API call includes a list of all computers registered to the account, and for each computer, it provides a wealth of information, including:
The computer's hostname, operating system, and network addresses.
The policy currently applied to the computer.
The connector (AMP agent) status (e.g., online, offline).
The last time the connector communicated with the AMP cloud.
The script will print this list of computers and their associated data.
Why the other options are incorrect:
A. The compromised computers and malware trajectories will be received from Cisco AMP:
The script calls the general computer listing endpoint (/v1/computers), not an endpoint specific to compromises or investigations (like /v1/events). It will return data for all computers, not just compromised ones.
B. The list of computers and their current vulnerabilities will be received from Cisco AMP:
While the computer list is correct, the AMP for Endpoints API does not provide vulnerability management data.
Vulnerability scanning is the function of a different product, like Cisco Secure Endpoint (formerly AMP for Endpoints) does not include a vulnerability database.
C. The compromised computers and what compromised them will be received from Cisco AMP:
Similar to option A, this describes a more specific investigative query. The general /v1/computers endpoint does not filter for or return detailed causality data about compromises.
Reference:
The official Cisco AMP for Endpoints API Reference for the GET /v1/computers endpoint confirms that it returns a "list of computers," and the sample JSON response includes fields for hostname, policy, and connector_guid (which is used to check status), aligning perfectly with option D.
An engineer must force an endpoint to re-authenticate an already authenticated session without disrupting the endpoint to apply a new or updated policy from ISE. Which CoA type achieves this goal?
A. Port Bounce
B. CoA Terminate
C. CoA Reauth
D. CoA Session Query
Explanation
A Change of Authorization (CoA) is a RADIUS mechanism that allows a policy server like Cisco ISE to dynamically change the authorization for an active, authenticated session. The "CoA Reauth" type is specifically designed for the scenario described.
Here's how it works:
The Situation:
An endpoint is already authenticated on the network. ISE needs to apply a new policy to this session (e.g., the endpoint's posture state changed, its profile was updated, or an administrator modified its access rights).
The Action:
ISE sends a CoA Reauth request to the network access device (NAD) like a switch or wireless controller.
The Result:
The NAD receives this request and silently forces the endpoint to go through the authentication process again. This is typically done by sending a new EAP-Request/Identity frame to the endpoint.
The Benefit:
The endpoint re-authenticates. During this new authentication, ISE re-evaluates all policies and issues a new authorization result based on the latest information. This all happens without disconnecting the endpoint or causing a noticeable network outage. The user might see a brief "checking for network connectivity" message, but their IP address and active TCP sessions are generally preserved.
This makes "CoA Reauth" the ideal tool for applying policy changes to existing sessions in a non-disruptive manner.
Detailed Breakdown of Incorrect Options:
A. Port Bounce:
Why it is incorrect:
A Port Bounce CoA is a very disruptive action. It effectively performs a "shutdown / no shutdown" on the switch port to which the endpoint is connected. This will completely disconnect the endpoint from the network, causing all active sessions to drop. The user would have to wait for the port to come back up and for their device to re-associate and obtain a new IP address (if using DHCP). This is the opposite of "without disrupting the endpoint."
B. CoA Terminate:
Why it is incorrect:
A CoA Terminate command is explicitly used to end the user's session immediately. It instructs the NAD to tear down the authenticated session and remove the endpoint from the network. Like Port Bounce, this is a disruptive action that logs the user off, which violates the requirement of the task.
D. CoA Session Query:
Why it is incorrect:
A CoA Session Query is not used to change authorization or force re-authentication. Its purpose is purely informational. ISE sends this request to the NAD to ask for a snapshot of the current state of a specific session (e.g., its IP address, session timeout, data usage). It is a read-only operation that does not modify the session or apply any new policy.
Reference and Key Context:
RFC 5176: The standard for "Dynamic Authorization Extensions to Remote Authentication Dial In User Service (RADIUS)" defines these CoA messages.
Cisco ISE Administration Guide: The use of CoA Reauth is detailed in sections discussing session management, profiling, and posture remediation.
An engineer has been tasked with implementing a solution that can be leveraged for securing the cloud users, data, and applications. There is a requirement to use the Cisco cloud native CASB and cloud cybersecurity platform. What should be used to meet these requirements?
A.
Cisco Umbrella
B.
Cisco Cloud Email Security
C.
Cisco NGFW
D.
Cisco Cloudlock
Cisco Cloudlock
Which two features of Cisco DNA Center are used in a Software Defined Network solution?
(Choose two)
A.
accounting
B.
assurance
C.
automation
D.
authentication
E.
encryption
assurance
automation
https://www.cisco.com/c/en/us/products/collateral/cloud-systemsmanagement/
dna-center/nb-06- cisco-dna-center-aag-cte-en.html
| Page 8 out of 61 Pages |
| Previous |