Topic 2: Exam Pool B
Which suspicious pattern enables the Cisco Tetration platform to learn the normal behavior
of users?
A.
file access from a different user
B.
interesting file access
C.
user login suspicious behavior
D.
privilege escalation
user login suspicious behavior
Reference: https://www.cisco.com/c/en/us/products/collateral/data-centeranalytics/
tetration-analytics/whitepaper-c11-740380.html
Which feature of Cisco ASA allows VPN users to be postured against Cisco ISE without requiring an inline posture node?
A. RADIUS Change of Authorization
B. device tracking
C. DHCP snooping
D. VLAN hopping
Explanation
This question focuses on the integration between Cisco ASA (handling remote access VPN) and Cisco ISE (handling policy and posture) to enforce security compliance without needing a physical or virtual appliance in the data path.
A. RADIUS Change of Authorization (CoA):
This is the correct answer. Here is the workflow:
A user connects via the ASA VPN.
The ASA forwards the authentication to ISE via RADIUS.
ISE determines that a posture check is required and grants the user a "Quarantine" or limited-access profile.
The Cisco AnyConnect Posture Module on the user's device communicates directly with ISE for the assessment.
If the device becomes compliant, ISE sends a RADIUS Change of Authorization (CoA) message to the ASA.
This CoA packet instructs the ASA to dynamically re-authenticate the user session.
Upon re-authentication, ISE now sees a compliant device and grants the user full network access.
This entire process allows for posture enforcement without requiring an "inline posture node" because the ASA itself acts as the enforcement point, controlled remotely by ISE using CoA.
Why the other options are incorrect:
B. device tracking:
This is a switch feature used to maintain a table of MAC and IP addresses connected to switch ports. It is unrelated to VPN user posture assessment.
C. DHCP snooping:
This is a switch security feature that prevents rogue DHCP servers. It is a Layer 2 security mechanism and has no role in the interaction between an ASA, ISE, and a remote VPN client.
D. VLAN hopping:
This is a network attack technique where an attacker gains unauthorized access to a VLAN other than their own. It is a security vulnerability, not a feature that enables posture assessment.
Reference:
This integration is a standard design in the Cisco Secure Access architecture.
Cisco ISE Administrator Guide: "Configure ASA VPN with ISE Posture": This guide details the steps, which explicitly include configuring ISE to send CoA requests and configuring the ASA to accept them from ISE.
Cisco ASA Configuration Guide: "RADIUS Authorization": The ASA must be configured to support RADIUS CoA packets for this integration to function.
In summary, RADIUS Change of Authorization (CoA) is the standard protocol that allows ISE to dynamically instruct the ASA to change a VPN user's session privileges based on the outcome of a posture assessment, eliminating the need for a separate inline device.
A network administrator is configuring a switch to use Cisco ISE for 802.1X. An endpoint is failing authentication and is unable to access the network. Where should the administrator begin troubleshooting to verify the authentication details?
A. Adaptive Network Control Policy List
B. Context Visibility
C. Accounting Reports
D. RADIUS Live Logs
Explanation:
When an endpoint is failing authentication in an 802.1X scenario, the most direct and detailed source of real-time information is the RADIUS Live Logs.
Let's analyze why this is the correct answer and the role of the other options:
D) RADIUS Live Logs is CORRECT.
The RADIUS Live Logs in Cisco ISE provide a real-time, step-by-step record of every authentication attempt. For a failed authentication, it will show you critical details, such as:
The identity of the endpoint (MAC address, username).
The network access device (switch IP and port) it connected to.
The exact time of the attempt.
The specific failure reason (e.g., "19013 Authentication failed," "User not found in identity store," "Wrong password," "Endpoint failed posture check").
Which specific policy and rule was matched.
This detailed breakdown is the definitive starting point for understanding why the authentication failed.
Why the other options are incorrect for beginning troubleshooting:
A) Adaptive Network Control Policy List is INCORRECT.
This is a configuration section where you define authorization policies (what access to grant). You would check this after you know the authentication is successful to see why an endpoint is getting the wrong level of access, not why it's failing to authenticate in the first place.
B) Context Visibility is INCORRECT.
While the Context Visibility service (especially the Endpoints and Network Devices pages) is incredibly useful for gathering information about an endpoint's history and profiling data, it is not the primary tool for real-time authentication debugging. You would use Context Visibility to look up an endpoint's profile or past sessions, but the Live Logs are the source of truth for the current authentication failure.
C) Accounting Reports is INCORRECT.
RADIUS accounting packets are sent after a successful authentication to track session start, stop, and usage data (like data usage). If the endpoint is failing authentication, no accounting session would be established, so these reports would not contain any information about the failure.
Troubleshooting Workflow:
The recommended troubleshooting flow for an 802.1X failure is:
Start with the RADIUS Live Logs to identify the specific error code and failed policy.
Use Context Visibility to investigate the endpoint's profile and history.
Check the Policy Sets and Authentication/Authorization Rules to verify the configuration matches the expected behavior.
Check the switch configuration and logs for any local issues.
Reference:
Cisco ISE Administrator Guide, "Monitoring RADIUS Live Logs":
The official documentation explicitly states that the Live Logs are the "first place to look when you are troubleshooting authentication and authorization issues."
Cisco ISE Troubleshooting Guide:
All standard troubleshooting procedures for network access begin with querying the Live Logs to capture the details of the failed authentication attempt.
An engineer notices traffic interruption on the network. Upon further investigation, it is learned that broadcast packets have been flooding the network. What must be configured, based on a predefined threshold, to address this issue?
A. Bridge Protocol Data Unit guard
B. embedded event monitoring
C. storm control
D. access control lists
Explanation
The problem described is a classic broadcast storm, where broadcast traffic floods the network, consuming all available bandwidth and causing a traffic interruption.
Storm control is a switch feature specifically designed to mitigate this exact issue. It works by monitoring the level of specific traffic types (broadcast, multicast, or unknown unicast) on a switch port. You can configure a predefined threshold (as a percentage of the total bandwidth or a specific packet rate).
When the traffic of the specified type exceeds this threshold, the switch will block that excess traffic on the port for the duration of the storm.
Once the traffic level falls back below the threshold, the port resumes normal operation.
This prevents a single misbehaving device or a network loop from taking down the entire network segment.
Why the other options are incorrect:
A. Bridge Protocol Data Unit (BPDU) guard:
This feature is used in Spanning Tree Protocol (STP) to protect the network topology. It disables a port if it receives a BPDU, preventing unauthorized switches from being connected. It does not monitor or control broadcast flood rates.
B. Embedded Event Manager (EEM):
EEM is a powerful tool for automating responses to specific events on a Cisco device. While you could write a complex EEM script to react to high broadcast levels, it is not the standard, built-in, and direct solution for this problem. Storm control is the dedicated, simple, and effective feature for this specific task.
D. Access Control Lists (ACLs):
ACLs are used for permitting or denying traffic based on Layer 3 (IP addresses) or Layer 4 (ports) information. They are not efficient or designed for rate-limiting a specific type of traffic like broadcast packets based on a bandwidth threshold. Storm control operates at Layer 2 and is the correct tool for this job.
Reference:
Storm control is a fundamental feature covered in Cisco switch configuration guides.
The Cisco IOS Interface and Hardware Component Configuration Guide for storm control states its purpose is to "prevent ports from being disrupted by a broadcast, multicast, or unicast storm" and that it "monitors incoming traffic levels over a 1-second interval and compares the level with a predefined threshold." This directly matches the requirement in the question.
Which two request of REST API are valid on the Cisco ASA Platform? (Choose two)
A.
put
B.
options
C.
gets
D.
push
E.
connect
put
gets
The ASA REST API gives you programmatic access to
managing individual ASAs through a Representational State Transfer (REST) API. The API allows external clients to perform CRUD (Create, Read, Update, Delete) operations on ASA resources; it is based on the HTTPS protocol and REST methodology.All API requests are sent over HTTPS to the ASA, and a response is returned.Request StructureAvailable request methods are:GET – Retrieves data from the specified object.PUT – Adds the supplied information to the specified object; returns a 404 Resource Not Found error if the object does not exist.POST – Creates the object with the supplied
information.DELETE – Deletes the specified object
Reference: https://www.cisco.com/c/en/us/td/docs/security/asa/api/qsg-asa-api.html
What is a functional difference between a Cisco ASA and a Cisco IOS router with Zonebased policy firewall?
A. The Cisco ASA denies all traffic by default whereas the Cisco IOS router with Zone- Based Policy Firewall starts out by allowing all traffic, even on untrusted interfaces
B. The Cisco IOS router with Zone-Based Policy Firewall can be configured for high availability, whereas the Cisco ASA cannot
C. The Cisco IOS router with Zone-Based Policy Firewall denies all traffic by default, whereas the Cisco ASA starts out by allowing all traffic until rules are added
D. The Cisco ASA can be configured for high availability whereas the Cisco IOS router with Zone-Based Policy Firewall cannot
Explanation:
This difference stems from their core security philosophies: the ASA is a purpose-built firewall, while the ZBFW is a security feature added to a multi-function router.
A) is CORRECT.
Cisco ASA (Stateful Firewall):
Operates on the principle of "implicit deny." By default, all traffic flowing through the ASA is blocked unless an explicit access-list rule permits it. This is a fundamental characteristic of a dedicated firewall—it assumes everything is a threat until explicitly allowed.
Cisco IOS Router with ZBFW:
Operates on the principle of "implicit permit" for traffic within a zone, but implicit deny for traffic moving between zones. However, the critical detail is that interfaces are not assigned to any zone by default. If an interface is not a member of a security zone, there are no restrictions on traffic to/from that interface. This is why the statement "starts out by allowing all traffic, even on untrusted interfaces" is accurate for the initial, unconfigured state.
Why the other options are incorrect:
B) The Cisco IOS router with Zone-Based Policy Firewall can be configured for high availability, whereas the Cisco ASA cannot is INCORRECT. This is factually false. The Cisco ASA has robust, long-standing high-availability capabilities using failover pairs (Active/Standby or Active/Active). While IOS routers can also be configured for high availability (e.g., with HSRP/VRRP and stateful failover for the firewall), the ASA is certainly capable of it.
C) The Cisco IOS router with Zone-Based Policy Firewall denies all traffic by default, whereas the Cisco ASA starts out by allowing all traffic until rules are added is INCORRECT. This is the exact opposite of the truth. As explained above, the ASA denies by default, and the unconfigured ZBFW allows traffic on interfaces not assigned to a zone.
D) The Cisco ASA can be configured for high availability whereas the Cisco IOS router with Zone-Based Policy Firewall cannot is INCORRECT. As stated for option B, both platforms can be configured for high availability. This is not a functional difference between them.
Reference:
Cisco ASA Configuration Guide, "Information About ASA Access Rules":
Explicitly states, "By default, the ASA allows no traffic to pass through it unless it is explicitly permitted by an access rule."
Cisco IOS Security Configuration Guide:
Zone-Based Policy Firewall, "Default Policy": Explains that "The default policy between zones is deny," but crucially notes that "If an interface is not a member of a zone, any traffic to or from that interface is allowed." This is the "default-allow" behavior for unassigned interfaces that the question references.
An organization has noticed an increase in malicious content downloads and wants to use
Cisco Umbrella to prevent this activity for suspicious domains while allowing normal web
traffic. Which action will accomplish this task?
A.
Set content settings to High
B.
Configure the intelligent proxy
C.
Use destination block lists
D.
Configure application block lists
Configure the intelligent proxy
How is ICMP used an exfiltration technique?
A. by flooding the destination host with unreachable packets
B. by sending large numbers of ICMP packets with a targeted hosts source IP address using an IP broadcast address
C. by encrypting the payload in an ICMP packet to carry out command and control tasks on a compromised host
D. by overwhelming a targeted host with ICMP echo-request packets
Explanation:
Data exfiltration is the unauthorized transfer of data from a compromised computer. Attackers need a covert channel to send stolen data out, and ICMP (Internet Control Message Protocol) can be manipulated for this purpose.
C) is CORRECT.
This describes the technique of ICMP Tunneling.
The Method:
Normal ICMP packets (like ping requests and replies) have a Data or Payload section. This section is intended for diagnostic information. An attacker can install malware that takes stolen data (e.g., credit card numbers, keylogs), encrypts or encodes it, and places it into the payload section of ICMP packets.
Bypassing Security:
Because many firewalls and early-generation IDS systems are configured to allow ICMP traffic (for network troubleshooting), this malicious data stream can often pass through undetected, unlike a direct file transfer over a standard port which would be blocked.
Command and Control (C2):
The same technique can be used in reverse to send commands to the compromised host, making ICMP a two-way communication channel for the attacker.
Why the other options are incorrect:
A) by flooding the destination host with unreachable packets is INCORRECT.
This describes a Denial-of-Service (DoS) attack, such as a Smurf or Flood attack, which aims to make a resource unavailable, not to steal data.
B) by sending large numbers of ICMP packets with a targeted hosts source IP address using an IP broadcast address is INCORRECT.
This is a description of the Smurf attack, which is another type of Denial-of-Service attack. It uses IP broadcast addresses to amplify traffic and overwhelm the spoofed victim.
D) by overwhelming a targeted host with ICMP echo-request packets is INCORRECT.
This is a description of a straightforward ICMP Flood attack, which is also a Denial-of-Service technique. The goal is to consume bandwidth and resources, not to exfiltrate data.
Reference:
SANS Institute & Cybersecurity Advisories:
Numerous security whitepapers and alerts detail the use of ICMP tunneling (and other protocol tunneling like DNS) as a common tactic for data exfiltration and establishing covert C2 channels.
MITRE ATT&CK Framework:
The framework categorizes this technique under T1095 - Non-Application Layer Protocol, which includes using protocols like ICMP for communication that avoids typical application-layer security controls.
Refer to the exhibit.
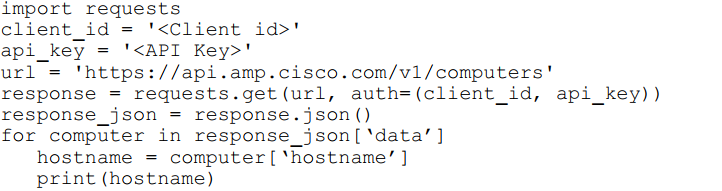
What will happen when the Python script is executed?
A.
The hostname will be translated to an IP address and printed
B.
The hostname will be printed for the client in the client ID field
C.
The script will pull all computer hostnames and print them
D.
The script will translate the IP address to FODN and print it
The script will pull all computer hostnames and print them
After a recent breach, an organization determined that phishing was used to gain initial access to the network before regaining persistence. The information gained from the phishing attack was a result of users visiting known malicious websites. What must be done in order to prevent this from happening in the future?
A. Modify an access policy
B. Modify identification profiles
C. Modify outbound malware scanning policies
D. Modify web proxy settings
Explanation
The problem statement is very specific: "users visiting known malicious websites." The primary defense mechanism against this specific action is a web proxy or web security gateway (like Cisco Umbrella or the Cisco Web Security Appliance - WSA).
A web proxy can be configured with policies that block access to websites based on their reputation and category. "Known malicious websites" would fall into a category like "Malware," "Phishing," or "Newly Seen Domains," which can be explicitly blocked. Modifying the web proxy settings is the direct action needed to prevent users from successfully connecting to these sites in the future.
Why the other options are incorrect:
A. Modify an access policy:
Access policies (like those on a firewall or in Cisco ISE) typically control if a user can reach a network segment or the internet at all, based on identity, device, location, etc. They are generally not granular enough to inspect and block specific malicious websites based on dynamic URL categorization.
B. Modify identification profiles:
Identification profiles are used in systems like Cisco ISE to define how to identify users and devices on the network (e.g., via MAC address, 802.1X, etc.). This is about who is on the network, not where they are allowed to go on the internet.
C. Modify outbound malware scanning policies:
This is a good security practice, but it is a reactive measure. Malware scanning inspects files as they are being downloaded. The goal here is to prevent the initial contact with the malicious site altogether, which stops the attack before any file download or exploit attempt can even occur. Blocking access at the DNS or URL level via a web proxy is more proactive.
Reference:
This defense-in-depth strategy is a core principle of the Cisco Secure Internet Gateway (SIG) and solutions like Cisco Umbrella.
The official documentation for Cisco Umbrella states that its primary function is to "block requests to malicious destinations before a connection is ever established" using a vast database of categorized and malicious domains. Implementing or modifying such a solution directly addresses the root cause described in the scenario.
A mall provides security services to customers with a shared appliance. The mall wants separation of management on the shared appliance. Which ASA deployment mode meets these needs?
A. routed mode
B. transparent mode
C. multiple context mode
D. multiple zone mode
Explanation for Each Option:
A. Routed mode (Incorrect):
Routed mode configures the Cisco ASA as a Layer 3 device, performing routing and NAT functions while inspecting traffic between interfaces. It does not provide separation of management on a shared appliance, as all configurations are managed in a single context without virtualization. This mode is suitable for standard firewall deployments but fails to meet the requirement for isolated customer management. (Reference: Cisco ASA Configuration Guide, Routed Mode Overview, cisco.com.)
B. Transparent mode (Incorrect):
Transparent mode operates the ASA as a Layer 2 bridge, allowing traffic to pass without changing IP addresses, ideal for insertion without network reconfiguration. However, it does not support separation of management on a shared appliance, as it maintains a single configuration context. This mode focuses on stealthy deployment but cannot isolate management for multiple customers, making it unsuitable. (Reference: Cisco ASA Transparent Mode Guide, cisco.com.)
C. Multiple context mode (Correct):
Multiple context mode virtualizes a single Cisco ASA into multiple independent firewalls, each with its own security policies, configurations, and management interfaces. This enables the mall to provide isolated security services to customers on a shared appliance while maintaining separation of management, ensuring compliance and security isolation. It meets the need for multi-tenancy on one device. (Reference: Cisco ASA Multiple Context Mode Configuration Guide, cisco.com; Web search result and .)
D. Multiple zone mode (Incorrect):
Multiple zone mode is not a recognized deployment mode for Cisco ASA. ASA supports routed, transparent, and multiple context modes, but no "multiple zone mode" exists in official documentation. This may confuse with zone-based firewall policies in other Cisco products, but it does not apply to ASA for separating management on a shared appliance, rendering this option invalid. (Reference: Cisco ASA Deployment Modes Overview, cisco.com.)
Additional Notes:
Multiple context mode is a key feature in the 350-701 SCOR exam under network security, enabling multi-tenancy for service providers like malls. As of October 02, 2025, this mode supports up to a model-dependent number of contexts (e.g., up to 250 on high-end ASAs).
An organization is using Cisco Firepower and Cisco Meraki MX for network security and
needs to centrally
manage cloud policies across these platforms. Which software should be used to accomplish this goal?
A.
Cisco Defense Orchestrator
B.
Cisco Secureworks
C.
Cisco DNA Center
D.
Cisco Configuration Professional
Cisco Defense Orchestrator
| Page 6 out of 61 Pages |
| Previous |