Topic 2: Exam Pool B
Drag and drop the solutions from the left onto the solution's benefits on the right.
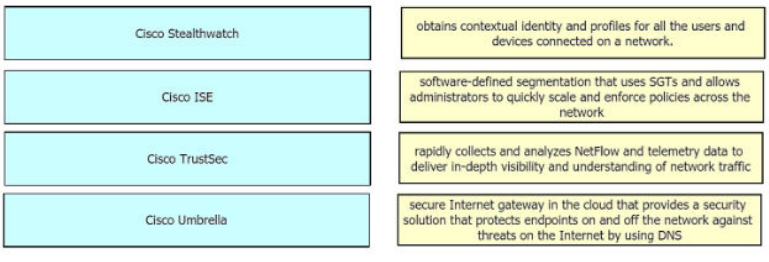
Explanation: Cisco Stealthwatch - rapidly collects and analyzes netflow and telementy
data to deliver in-depth visibility and understanding of network traffic
Cisco ISE – obtains contextual identity and profiles for all users and device
Cisco TrustSec – software defined segmentation that uses SGTs
Cisco Umbrella – secure internet gateway ion the cloud that provides a security solution
Which IPS engine detects ARP spoofing?
A.
Atomic ARP Engine
B.
Service Generic Engine
C.
ARP Inspection Engine
D.
AIC Engine
Atomic ARP Engine
Why is it important to have logical security controls on endpoints even though the users are trained to spot security threats and the network devices already help prevent them?
A. to prevent theft of the endpoints
B. because defense-in-depth stops at the network
C. to expose the endpoint to more threats
D. because human error or insider threats will still exist
Explanation:
Cisco Advanced Malware Protection (AMP) for Endpoints is the solution that provides proactive protection directly on endpoints (like laptops, servers, and mobile devices) and is managed from a central console.
Let's break down why AMP is the correct answer and the role of the other products:
B) AMP is CORRECT.
Cisco AMP for Endpoints is an advanced antivirus and anti-malware solution that is installed directly on endpoints. It provides proactive protection through features like:
Behavioral Monitoring:
Analyzing running processes for malicious activity.
File Reputation & Sandboxing:
Checking files against global threat intelligence and detonating suspicious files in a sandbox.
Retrospective Security:
Continuously monitoring files and can detect and remediate threats after they have initially evaded detection.
All of this is managed from a central cloud-based or on-premises console, giving administrators visibility and control over all protected endpoints from a single pane of glass.
Why the other options are incorrect:
A) NGFW is INCORRECT.
A Next-Generation Firewall (NGFW) is a network-based security appliance. It protects the network perimeter and segments, inspecting traffic as it passes through. It does not provide protection on the endpoint itself and is not used to deploy and manage software on user devices.
C) WSA is INCORRECT.
The Cisco Web Security Appliance (WSA) is a gateway that filters and secures web traffic (HTTP/HTTPS). It protects users from web-based threats by blocking malicious sites and downloads. Like the NGFW, it is a network appliance, not an endpoint protection product.
D) ESA is INCORRECT.
The Cisco Email Security Appliance (ESA) is a gateway that filters and secures email traffic (SMTP). It protects against spam, phishing, and malware delivered via email. It is also a network appliance and does not provide protection on the endpoint or manage endpoint software.
Reference:
Cisco AMP for Endpoints Data Sheet: The official product description highlights its role in "protecting endpoints" and its "centralized management console" for investigation and response.
Cisco Security Portfolio Architecture:The portfolio is divided into Network Security (NGFW, WSA, ESA), Cloud Security, and Endpoint Security (AMP), clearly placing AMP in the role of proactive endpoint protection.
What is a feature of Cisco NetFlow Secure Event Logging for Cisco ASAs?
A.
Multiple NetFlow collectors are supported
B.
Advanced NetFlow v9 templates and legacy v5 formatting are supported
C.
Secure NetFlow connections are optimized for Cisco Prime Infrastructure
D.
Flow-create events are delayed
Advanced NetFlow v9 templates and legacy v5 formatting are supported
What is a language format designed to exchange threat intelligence that can be transported over the TAXII protocol?
A.
STIX
B.
XMPP
C.
pxGrid
D.
SMTP
STIX
TAXII (Trusted Automated Exchange of Indicator Information) is a standard that provides a transport
What is the purpose of the My Devices Portal in a Cisco ISE environment?
A. to register new laptops and mobile devices
B. to request a newly provisioned mobile device
C. to provision userless and agentless systems
D. o manage and deploy antivirus definitions and patches on systems owned by the end user
Explanation:
The My Devices portal is a self-service, web-based portal in Cisco ISE that allows end-users to manage the devices they personally use on the corporate network.
Let's analyze each option:
A) to register new laptops and mobile devices is CORRECT.
This is the primary purpose of the My Devices portal. An employee can log into this portal using their corporate credentials and manually register the MAC addresses of their personal devices, such as a personal laptop, smartphone, tablet, or gaming console. Once registered, ISE can apply the appropriate authorization policy (e.g., a "BYOD" policy) to that device, allowing it onto the network without requiring help desk intervention.
B) to request a newly provisioned mobile device is INCORRECT.
This describes a procurement or IT fulfillment process, which is typically handled through a different IT service management (ITSM) tool or ticketing system, not the ISE My Devices portal.
C) to provision userless and agentless systems is INCORRECT.
"Userless" devices (like printers, IoT sensors) and "agentless" systems are typically profiled and onboarded automatically by the ISE Profiler service or through administrative configuration, not by end-users in a self-service portal.
D) to manage and deploy antivirus definitions and patches on systems owned by the end user is INCORRECT.
This function is performed by the ISE Posture Service. The Posture service is responsible for checking and enforcing compliance, which can include verifying antivirus status and patch levels. While a non-compliant device might be redirected to a portal where it can download necessary updates, the primary portal for compliance remediation is distinct from the "My Devices" portal used for registration.
Reference:
Cisco ISE Administrator Guide, "My Devices Portals":
The official documentation states, "The My Devices portal enables you to provide a self-service portal for end users to register their own devices (such as personal laptops, tablets, and other mobile devices) and manage them after registration."
Cisco BYOD Design Guides:
These guides consistently present the My Devices portal as the critical user-facing component for a Bring Your Own Device (BYOD) deployment, where users register their personal devices to gain network access.
An organization recently installed a Cisco WSA and would like to take advantage of the
AVC engine to allow the organization to create a policy to control application specific
activity. After enabling the AVC engine, what must be done to implement this?
A.
Use security services to configure the traffic monitor, .
B.
Use URL categorization to prevent the application traffic
C.
Use an access policy group to configure application control settings
D.
Use web security reporting to validate engine functionality
Use an access policy group to configure application control settings
The Application Visibility and Control (AVC) engine
lets you create policies to control application activity on the network without having to fully
understand the underlying technology of each application. You can configure application
control settings in Access Policy groups. You can block or allow applications individually or
according to application type. You can also apply controls to particular application types.
Which two services must remain as on-premises equipment when a hybrid email solution is deployed? (Choose two)
A.
DDoS
B.
antispam
C.
antivirus
D.
encryption
E.
DLP
encryption
DLP
Explanation for Each Option:
A. DDoS (Incorrect):
Distributed Denial-of-Service (DDoS) protection can be effectively managed by cloud-based services, such as those offered by Cisco Umbrella or third-party providers, which mitigate attacks before they reach on-premises infrastructure. In a hybrid email solution, DDoS protection does not need to remain on-premises, as cloud scalability handles this better, making this option incorrect. (Reference: Cisco Secure Email Gateway Deployment Guide.)
B. antispam (Incorrect):
Antispam services are commonly handled by cloud-based email security solutions (e.g., Cisco Secure Email Gateway cloud) in a hybrid setup, where email traffic is filtered before reaching on-premises systems. This allows for real-time updates to spam signatures, reducing the need for on-premises equipment, making this option unnecessary to retain locally. (Reference: Cisco Secure Email Cloud Service Overview.)
C. antivirus (Incorrect):
Antivirus scanning can be offloaded to cloud-based email security services in a hybrid email solution, where emails are scanned for malware before delivery to on-premises servers. Modern cloud platforms provide robust, frequently updated antivirus protection, eliminating the need to maintain this as on-premises equipment, rendering this option incorrect. (Reference: Cisco Secure Email Threat Defense.)
D. encryption (Correct):
Encryption, particularly for email data at rest and in transit, often requires on-premises equipment in a hybrid email solution to ensure compliance with organizational policies or regulatory standards (e.g., HIPAA, GDPR). On-premises key management and encryption appliances allow control over sensitive data, making this a critical service to retain locally. (Reference: Cisco Email Security Appliance Configuration Guide, Encryption Settings.)
E. DLP (Correct):
Data Loss Prevention (DLP) must often remain on-premises in a hybrid email solution to enforce granular policies on sensitive data (e.g., PII, financial records) based on internal compliance requirements. On-premises DLP appliances can inspect and block data exfiltration before it leaves the network, ensuring tighter control than cloud-based DLP alone, making this essential locally. (Reference: Cisco Secure DLP Deployment Guide.)
Additional Notes:
In a hybrid email solution, encryption and DLP are often retained on-premises for compliance and data sovereignty, a topic in the 350-701 SCOR exam under content security. As of 04:47 PM PKT, October 01, 2025, this reflects current best practices. Refer to Cisco Secure Email Gateway documentation (cisco.com) and the 350-701 Exam Blueprint (Section 3.0 Security Concepts) for details. More questions?
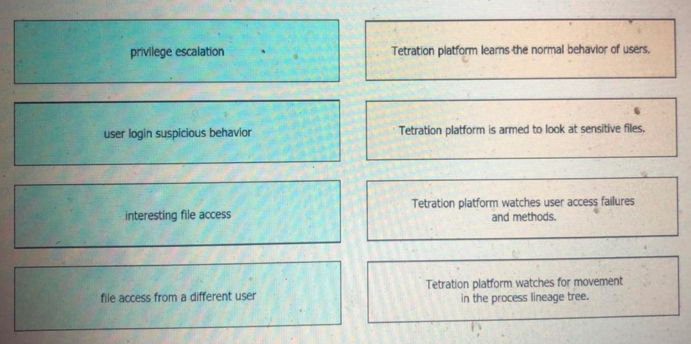
Drag and drop the suspicious patterns for the Cisco Tetration platform from the left onto the
correct definitions on the right.

Which Cisco product is open, scalable, and built on IETF standards to allow multiple
security products from
Cisco and other vendors to share data and interoperate with each other?
A. Advanced Malware Protection
B. Platform Exchange Grid
C. Multifactor Platform Integration
D. Firepower Threat Defense
Explanation for Each Option:
A. Advanced Malware Protection (Incorrect):
Cisco Advanced Malware Protection (AMP) is a comprehensive solution focused on detecting, preventing, and responding to malware across endpoints, networks, and cloud environments. While effective for malware defense, it is not designed as an open, scalable platform built on IETF standards for interoperability and data sharing among multiple security products from Cisco and other vendors, making this option incorrect. (Reference: Cisco AMP Datasheet.)
B. Platform Exchange Grid (Correct):
The Cisco Platform Exchange Grid (pxGrid) is an open and scalable security information exchange platform built on IETF standards, such as XMPP. It enables multiple Cisco and third-party security products to share contextual data and interoperate, facilitating integrated threat defense and automated responses across a diverse ecosystem, aligning with the described requirements. (Reference: Cisco pxGrid Documentation.)
C. Multifactor Platform Integration (Incorrect):
Multifactor Platform Integration is not a recognized Cisco product or feature. It may be a misnomer for multifactor authentication (MFA) solutions like Cisco Duo, which focus on user authentication rather than providing an open, scalable framework for data sharing and interoperability among various security products, making this option incorrect. (Reference: Cisco Duo Overview.)
D. Firepower Threat Defense (Incorrect):
Cisco Firepower Threat Defense (FTD) is a next-generation firewall and intrusion prevention system that integrates with other Cisco security tools. However, it is a standalone product focused on network security, not an open, IETF-standard-based platform designed for data sharing and interoperability across multiple vendors’ security products, rendering this option incorrect. (Reference: Cisco FTD Configuration Guide.)
Additional Notes:
Cisco pxGrid, covered in the 350-701 SCOR exam under network security and integration, enhances ecosystem interoperability. As of 04:56 PM PKT, October 01, 2025, it remains a cornerstone of Cisco’s security architecture. For details, refer to the Cisco pxGrid User Guide (cisco.com) and the 350-701 Exam Blueprint (Section 1.0 Security Concepts). More questions?
A network administrator needs to find out what assets currently exist on the network. Thirdparty
systems need to be able to feed host data into Cisco Firepower. What must be
configured to accomplish this?
A.
a Network Discovery policy to receive data from the host
B.
a Threat Intelligence policy to download the data from the host
C.
a File Analysis policy to send file data into Cisco Firepower
D.
a Network Analysis policy to receive NetFlow data from the host
a Network Discovery policy to receive data from the host
You can configure discovery rules to tailor the discovery of host
and application data to your needs.The Firepower System can use data from NetFlow
exporters to generate connection and discovery events, and to add host and application
data to the network map.A network analysis policy governs how traffic is decoded and
preprocessed so it can be further evaluated, especially for anomalous traffic that might
signal an intrusion attempt -> Answer D is not correct.
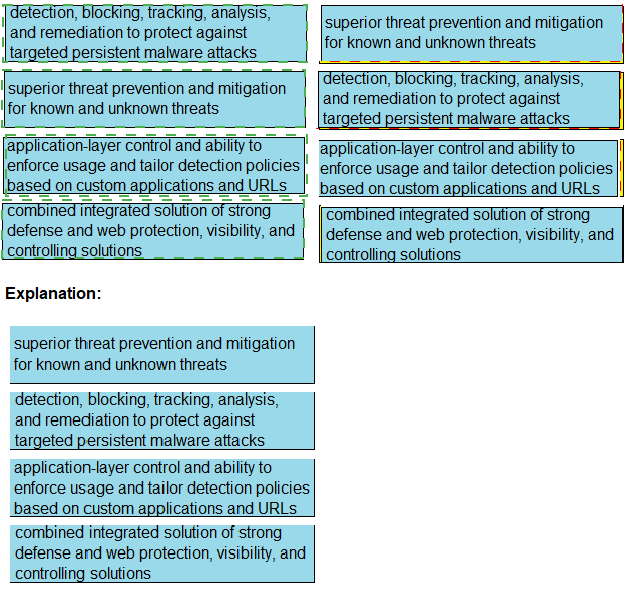
Drag and drop the capabilities from the left onto the correct technologies on the right.

Text, chat or text message
Description automatically generated
| Page 5 out of 61 Pages |
| Previous |