Topic 1: Exam Pool A
Which two conditions are prerequisites for stateful failover for IPsec? (Choose two)
A. Only the IKE configuration that is set up on the active device must be duplicated on the standby device; the IPsec configuration is copied automatically
B. The active and standby devices can run different versions of the Cisco IOS software but must be the same type of device.
C. The IPsec configuration that is set up on the active device must be duplicated on the standby device<
D. Only the IPsec configuration that is set up on the active device must be duplicated on the standby device; the IKE configuration is copied automatically.
E. The active and standby devices must run the same version of the Cisco IOS software and must be the same type of device
Explanation:
Stateful failover for IPsec is designed to maintain active VPN sessions during a hardware failure. For this to work seamlessly, the standby device must be an exact replica of the active device, both in configuration and capability.
Let's break down the prerequisites:
C) The IPsec configuration that is set up on the active device must be duplicated on the standby device is CORRECT.
This is an absolute requirement. The standby device must have an identical IPsec configuration (transform sets, crypto maps, access-lists defining interesting traffic, etc.) to be able to take over the encryption/decryption of the existing sessions.
E) The active and standby devices must run the same version of the Cisco IOS software and must be the same type of device is CORRECT.
This ensures compatibility. Running different IOS versions can lead to differences in IPsec or failover implementation, causing the failover to fail. Using the same type of device (e.g., both are Cisco ASA 5506-X or both are ISR 4431 routers) guarantees identical hardware capabilities and performance.
Why the other options are incorrect:
A) Only the IKE configuration that is set up on the active device must be duplicated on the standby device; the IPsec configuration is copied automatically is INCORRECT.
This is backwards and false. The IPsec configuration is not copied automatically; it must be manually duplicated. While IKE (Phase 1) security associations (SAs) can be replicated, the underlying configuration is still required.
B) The active and standby devices can run different versions of the Cisco IOS software but must be the same type of device is INCORRECT.
Different IOS versions are a common source of incompatibility and are strongly discouraged, if not outright unsupported, for stateful failover.
D) Only the IPsec configuration that is set up on the active device must be duplicated on the standby device; the IKE configuration is copied automatically is INCORRECT.
Similar to option A, this is incorrect. Both the IKE and IPsec configurations must be manually duplicated on the standby device for a successful and predictable failover.
Reference:
Cisco ASA Configuration Guide, "Failover for High Availability": The official documentation explicitly lists prerequisites such as "The two units must be the same model," "have the same amount of RAM," and "be in the same operating mode (routed or transparent)." While it allows for different software versions in some very specific scenarios, it strongly recommends the same version to avoid incompatibilities.
Cisco IOS High Availability Configuration Guides: Guides for stateful failover on routers emphasize the need for identical hardware and software for reliable operation.
A network engineer must monitor user and device behavior within the on-premises network. This data must be sent to the Cisco Stealthwatch Cloud analytics platform for analysis. What must be done to meet this requirement using the Ubuntu-based VM appliance deployed in a VMware-based hypervisor?
A. Configure a Cisco FMC to send syslogs to Cisco Stealthwatch Cloud
B. Deploy the Cisco Stealthwatch Cloud PNM sensor that sends data to Cisco Stealthwatch Cloud
C. Deploy a Cisco FTD sensor to send network events to Cisco Stealthwatch Cloud
D. Configure a Cisco FMC to send NetFlow to Cisco Stealthwatch Cloud
Explanation for Each Option:
A. Configure a Cisco FMC to send syslogs to Cisco Stealthwatch Cloud (Incorrect):
Cisco Firepower Management Center (FMC) can generate syslogs for event monitoring, but Stealthwatch Cloud primarily relies on flow data (e.g., NetFlow, IPFIX) rather than syslogs for behavioral analysis. Configuring FMC to send syslogs does not align with Stealthwatch Cloud’s data ingestion requirements, making this option unsuitable. (Reference: Cisco Stealthwatch Cloud Integration Guide.)
B. Deploy the Cisco Stealthwatch Cloud PNM sensor that sends data to Cisco Stealthwatch Cloud (Correct):
The Cisco Stealthwatch Cloud Personal Network Monitor (PNM) sensor, deployable as a virtual appliance on an Ubuntu-based VM in a VMware hypervisor, collects user and device behavior data from the on-premises network. It sends this data (e.g., via NetFlow or IPFIX) to Stealthwatch Cloud for advanced analytics, meeting the requirement effectively. (Reference: Cisco Stealthwatch Cloud PNM Deployment Guide.)
C. Deploy a Cisco FTD sensor to send network events to Cisco Stealthwatch Cloud (Incorrect):
Cisco Firepower Threat Defense (FTD) can generate network events and integrate with Stealthwatch, but it requires a Firepower Management Center (FMC) for management and data export. The scenario specifies an Ubuntu-based VM appliance, not FTD, and lacks mention of FMC, making this deployment method incompatible with the given setup. (Reference: Cisco FTD with Stealthwatch Integration.)
D. Configure a Cisco FMC to send NetFlow to Cisco Stealthwatch Cloud (Incorrect):
While FMC can be configured to export NetFlow data from managed FTD devices to Stealthwatch Cloud, this requires an FMC and FTD deployment, not an Ubuntu-based VM appliance as specified. The scenario focuses on the VM-based solution, and FMC/NetFlow setup does not match the described infrastructure, rendering this option incorrect. (Reference: Cisco FMC NetFlow Configuration.)
Additional Notes:
Monitoring user and device behavior with Stealthwatch Cloud is a key topic in the 350-701 SCOR exam under network security. As of 09:39 AM PKT, October 02, 2025, the PNM sensor is tailored for VM deployments. For details, refer to the Cisco Stealthwatch Cloud Deployment Guide (cisco.com) and the 350-701 Exam Blueprint (Section 1.0 Security Concepts).
Which solution stops unauthorized access to the system if a user's password is compromised?
A. VPN
B. MFA
C. AMP
D. SSL
Explanation
The scenario describes a situation where the first line of defense—the password—has already failed. The question asks for a solution that can stop unauthorized access even under this condition.
MFA (Multi-Factor Authentication) requires a user to provide two or more separate forms of evidence (factors) to authenticate. These factors typically are:
Something you know (e.g., a password, which is compromised).
Something you have (e.g., a smartphone app generating a code, a physical token).
Something you are (e.g., a fingerprint or facial recognition).
Even if an attacker has the compromised password, they will be blocked from accessing the system because they cannot provide the second, required factor (e.g., the code from the user's phone). MFA directly addresses the threat of stolen credentials.
Why the other options are incorrect:
A. VPN (Virtual Private Network):
A VPN creates a secure, encrypted tunnel to a network. However, it almost always requires authentication to establish that tunnel. If the user's password is compromised, the attacker can use that same password to authenticate to the VPN and gain access.
C. AMP (Advanced Malware Protection):
AMP is a solution for detecting, blocking, and tracking malware and files. It does not control initial user access to a system or application. It is a threat detection tool, not an access control mechanism.
D. SSL (Secure Sockets Layer):
SSL (and its successor, TLS) is a protocol for encrypting data in transit between a client and a server. It protects the confidentiality of the communication but does nothing to verify the identity of the user once the connection is established. An attacker with a valid password would simply log in over an encrypted SSL/TLS connection.
Reference:
The effectiveness of MFA in mitigating credential-based attacks is a foundational principle in modern cybersecurity.
As outlined in frameworks from NIST (National Institute of Standards and Technology) and promoted by CISA (Cybersecurity and Infrastructure Security Agency), multi-factor authentication is one of the most critical controls to prevent unauthorized access, specifically because it mitigates the risk of stolen or compromised passwords.
How is Cisco Umbrella configured to log only security events?
A.
per policy
B.
in the Reporting settings
C.
in the Security Settings section
D.
per network in the Deployments section
per policy
Explanation for Each Option:
A. per policy (Correct):
Cisco Umbrella allows logging of security events to be configured on a per-policy basis, where administrators can define specific security policies to capture events like malware detections, phishing attempts, or command-and-control (C2) traffic. This granular control ensures only security-related logs are recorded, aligning with the requirement to log only security events, making this the correct approach. (Reference: Cisco Umbrella Admin Guide, Policy Management.)
B. in the Reporting settings (Incorrect):
The Reporting settings in Cisco Umbrella are used to view and customize reports based on logged data, not to configure what events are logged. While you can filter reports to focus on security events, this does not determine the initial logging scope. Logging configuration is policy-driven, not report-driven, making this option incorrect. (Reference: Cisco Umbrella User Guide, Reporting Features.)
C. in the Security Settings section (Incorrect):
The Security Settings section in Cisco Umbrella typically governs general security features like DNS security policies or threat intelligence integration but does not specifically control logging granularity. It sets the security posture, not the logging focus on security events alone, which is managed through policies, rendering this option incorrect. (Reference: Cisco Umbrella Security Configuration.)
D. per network in the Deployments section (Incorrect):
The Deployments section configures how Umbrella is deployed (e.g., via virtual appliances or roaming clients) across networks, but it does not dictate logging specifics like focusing only on security events. Logging configuration is tied to policies applied to those deployments, not the deployment setup itself, making this option incorrect. (Reference: Cisco Umbrella Deployment Guide, Network Configuration.)
Additional Notes:
Configuring Cisco Umbrella to log only security events via policies is a key topic in the 350-701 SCOR exam under content security. As of 04:21 PM PKT, October 01, 2025, this reflects current Umbrella functionality. For detailed guidance, refer to the Cisco Umbrella Administration Guide (umbrella.cisco.com) and the 350-701 Exam Blueprint (cisco.com, Section 3.0 Security Concepts). More questions?
When wired 802.1X authentication is implemented, which two components are required? (Choose two)
A. authentication server: Cisco Identity Service Engine
B. supplicant: Cisco AnyConnect ISE Posture module
C. authenticator: Cisco Catalyst switch
D. authenticator: Cisco Identity Services Engine
E. authentication server: Cisco Prime Infrastructure
Explanation
The 802.1X standard defines a framework for port-based network access control with three primary roles:
A. authentication server:
Cisco Identity Service Engine: This is correct. The authentication server is the central policy decision point. It receives the connection request from the authenticator, validates the credentials provided by the supplicant against an identity store (like Active Directory), and informs the authenticator whether to grant or deny network access. Cisco ISE is the dedicated product that performs this role in a Cisco network.
C. authenticator:
Cisco Catalyst switch: This is correct. The authenticator is the network access device that acts as a gatekeeper. It controls the physical (or logical) port to which the supplicant is connected. The switch's job is to relay authentication messages between the supplicant and the authentication server. Based on the response from the server, it either opens the port (placing it in an authorized state) or keeps it closed. A Cisco Catalyst switch is a classic example of an authenticator in a wired network.
Why the other options are incorrect:
B. supplicant:
Cisco AnyConnect ISE Posture module: This is incorrect. The AnyConnect Posture Module is used for posture assessment, which is a separate security check that can happen after 802.1X authentication. The 802.1X supplicant is the software on the endpoint client device that seeks access to the network. It is typically built into the operating system (e.g., the Windows Wireless Client or the wired 802.1X supplicant) or can be part of the Cisco AnyConnect Network Access Manager (NAM) module, not the Posture module.
D. authenticator:
Cisco Identity Services Engine: This is incorrect. This option confuses the roles. Cisco ISE is the authentication server, not the authenticator. The authenticator is the network device (switch, wireless controller, WLC) that enforces the policy at the access layer.
E. authentication server:
Cisco Prime Infrastructure: This is incorrect. Cisco Prime Infrastructure (PI) is a network management and automation tool. While it can have some integration with ISE for visibility and reporting, it is not an authentication server itself. It does not perform the RADIUS-based authentication, authorization, and accounting (AAA) functions required for 802.1X.
Reference:
This is a fundamental concept in the "Secure Network Access" domain of the SCOR exam and is covered in the official Cisco ISE documentation.
Cisco ISE Architecture Documentation: Clearly defines the three roles of 802.1X: Supplicant (client), Authenticator (network device), and Authentication Server (ISE).
In summary, for a wired 802.1X deployment, you need an authenticator (the switch controlling the port) and an authentication server (ISE making the access decision).
Which two capabilities of Integration APIs are utilized with Cisco DNA center? (Choose two)
A. Automatically deploy new virtual routers
B. Upgrade software on switches and routers
C. Application monitors for power utilization of devices and IoT sensors
D. Connect to Information Technology Service Management Platforms
E. Create new SSIDs on a wireless LAN controller
Explanation for Each Option:
A. Create new SSIDs on a wireless LAN controller (Incorrect):
Creating new SSIDs on a wireless LAN controller is a core function of Cisco Catalyst Center’s Intent APIs, which handle network provisioning tasks like wireless configuration. However, this is part of the northbound Intent APIs for direct network management, not specifically Integration APIs, which focus on external system connectivity rather than device-level operations, making this option incorrect. (Reference: Cisco Catalyst Center Intent API Documentation, Wireless Provisioning.)
B. Connect to ITSM platforms (Correct):
Integration APIs in Cisco Catalyst Center enable connectivity to IT Service Management (ITSM) platforms like ServiceNow, allowing seamless integration for incident, change, and problem management. This westbound capability forwards events and workflows from Catalyst Center to external ITSM systems, enhancing operational efficiency and reducing manual handoffs, aligning with the integration focus. (Reference: Cisco Catalyst Center Platform User Guide, ITSM Integration Flows.)
C. Automatically deploy new virtual routers (Incorrect):
Automatic deployment of virtual routers is handled through Catalyst Center’s automation features, such as templates and workflows via Intent APIs, but not through Integration APIs. These APIs are designed for external integrations, not internal orchestration of device deployment, making this option unrelated to their primary capabilities. (Reference: Cisco Catalyst Center Automation Guide, Device Provisioning.)
D. Upgrade software on switches and routers (Incorrect):
Software upgrades on switches and routers are managed via Catalyst Center’s Software Image Management (SWIM) using Intent APIs, which orchestrate distribution and installation. Integration APIs do not perform this task; they focus on external data exchange and notifications, not direct device maintenance, rendering this option incorrect. (Reference: Cisco Catalyst Center SWIM Documentation.)
E. Third party reporting (Correct):
Integration APIs support third-party reporting by enabling Catalyst Center to share data, events, and analytics with external reporting tools or platforms. This allows for customized dashboards and reports outside the native UI, leveraging integration flows for enhanced visibility and compliance, a key capability of the platform’s open architecture. (Reference: Cisco Catalyst Center Developer Toolkit, Event Notifications and Integrations.)
Additional Notes:
Integration APIs in Cisco Catalyst Center (formerly DNA Center) emphasize westbound connectivity for external ecosystems, as covered in the 350-701 SCOR exam under automation. As of October 02, 2025, this supports hybrid IT operations. For details, refer to the Cisco Catalyst Center Platform User Guide (cisco.com) and the 350-701 Exam Blueprint (Section 4.0 Automation).
Which two statements about a Cisco WSA configured in Transparent mode are true? (Choose two)
A. It can handle explicit HTTP requests.
B. It requires a PAC file for the client web browser.
C. It requires a proxy for the client web browser.
D. WCCP v2-enabled devices can automatically redirect traffic destined to port 80.
E. Layer 4 switches can automatically redirect traffic destined to port 80.
Explanation for Each Option:
A. It can handle explicit HTTP requests (Correct):
In Transparent mode, a Cisco Web Security Appliance (WSA) intercepts HTTP traffic without requiring clients to configure a proxy. It can still process explicit HTTP requests (e.g., those sent directly to a proxy port) by routing them through the appliance, which then applies security policies, making this statement true. (Reference: Cisco WSA Transparent Mode Guide.)
B. It requires a PAC file for the client web browser (Incorrect):
Transparent mode eliminates the need for a Proxy Auto-Config (PAC) file, as traffic is redirected to the WSA without client-side configuration. A PAC file is typically used in Explicit mode to direct browsers to the proxy, so this requirement does not apply, making this option false. (Reference: Cisco WSA Deployment Options.)
C. It requires a proxy for the client web browser (Incorrect):
In Transparent mode, the WSA operates without clients needing to configure a proxy manually. Traffic is redirected via network devices (e.g., WCCP or PBR), bypassing the need for proxy settings in the browser, which is a key difference from Explicit mode, rendering this option incorrect. (Reference: Cisco WSA Configuration Guide, Transparent vs. Explicit.)
D. WCCP v2-enabled devices can automatically redirect traffic destined to port 80 (Correct):
Web Cache Communication Protocol (WCCP) version 2, when enabled on network devices (e.g., routers or switches), can transparently redirect HTTP traffic (port 80) to the WSA. This automation is a standard feature of Transparent mode, allowing seamless traffic interception without client involvement, making this statement true. (Reference: Cisco WCCP Configuration Guide.)
E. Layer 4 switches can automatically redirect traffic destined to port 80 (Incorrect):
While some Layer 4 switches support traffic redirection (e.g., via PBR or WCCP), this is not a universal feature and depends on specific switch capabilities and configuration. WCCP is more commonly associated with routers, and the statement’s generality lacks precision for Transparent mode, making it less accurate than option D. (Reference: Cisco Switching Fundamentals, Layer 4 Features.)
Additional Notes:
Configuring WSA in Transparent mode is a key topic in the 350-701 SCOR exam under content security. As of 10:15 AM PKT, October 02, 2025, this remains a standard deployment method. For details, refer to the Cisco WSA Administration Guide (cisco.com) and the 350-701 Exam Blueprint (Section 3.0 Security Concepts)
What is the intent of a basic SYN flood attack?
A.
to solicit DNS responses
B.
to exceed the threshold limit of the connection queue
C.
to flush the register stack to re-initiate the buffers
D.
to cause the buffer to overflow
to exceed the threshold limit of the connection queue
Explanation for Each Option:
A. to solicit DNS responses (Incorrect):
A SYN flood attack is a type of denial-of-service (DoS) assault that targets the TCP three-way handshake process by sending a flood of SYN (synchronize) packets to a target server without completing the connection with an ACK (acknowledgment) packet. This creates a backlog of half-open connections, overwhelming the server’s resources. Soliciting DNS responses, however, is characteristic of a different attack type known as a DNS amplification attack, where an attacker spoofs the source IP address to send DNS queries, leveraging open DNS resolvers to flood the victim with large response packets. Since a SYN flood focuses on exhausting TCP connection resources rather than exploiting DNS protocols, this option is fundamentally incorrect and unrelated to the mechanics of a SYN flood attack. (Reference: Cisco 350-701 SCOR Exam Topics - Denial-of-Service Attacks; Cisco Secure Network Fundamentals.)
B. to exceed the threshold limit of the connection queue (Correct):
The primary intent of a basic SYN flood attack is to overwhelm the target system’s TCP connection queue, which manages incoming connection requests. The attack initiates this by sending a massive volume of SYN packets, each triggering the server to allocate resources for a potential connection. Without receiving the corresponding ACK packets to complete the handshake, these half-open connections accumulate, quickly surpassing the queue’s threshold limit. This resource exhaustion prevents the server from accepting legitimate connections, effectively denying service to valid users. This aligns with the attack’s goal of disrupting availability, a core concept in network security covered extensively in the Cisco 350-701 SCOR exam. (Reference: Cisco Secure Firewall DoS Mitigation Guide; RFC 4987 - TCP SYN Flooding Attacks and Common Mitigations.)
C. to flush the register stack to re-initiate the buffers (Incorrect):
This option appears to misinterpret the technical target of a SYN flood attack. Flushing a register stack or re-initiating buffers suggests a low-level hardware or software memory management issue, typically associated with buffer overflow exploits or processor-specific attacks. A SYN flood, however, operates at the network layer, targeting the TCP/IP stack’s connection queue rather than CPU registers or application buffers. There is no mechanism in a SYN flood that aims to manipulate register stacks or reset buffers; its focus is solely on clogging the connection queue with incomplete handshakes. This makes the option a misrepresentation of the attack’s intent and execution. (Reference: Cisco IOS Security Fundamentals - DoS Attack Mitigation; OWASP Application Security Testing Guide.)
D. to cause the buffer to overflow (Incorrect):
A buffer overflow attack involves sending excessively large or malformed data to an application or system to overwrite memory buffers, potentially allowing arbitrary code execution. In contrast, a SYN flood attack does not aim to overflow application buffers but rather to saturate the operating system’s TCP connection queue with half-open connections. While both are DoS techniques, their methods and targets differ: buffer overflows exploit software vulnerabilities, whereas SYN floods exploit protocol design. Confusing these concepts misaligns with the attack’s network-level focus, rendering this option incorrect. (Reference: OWASP Top Ten 2021 - A04: Insecure Design; Cisco 350-701 Exam Blueprint - Security Concepts.)
Additional Notes:
A SYN flood is a classic denial-of-service technique that leverages the TCP handshake process to exhaust server resources, a critical topic in the Cisco 350-701 SCOR exam under the network security domain. Mitigation strategies include SYN cookies, which allow servers to handle connections without reserving resources until the handshake completes, and rate-limiting inbound SYN packets. As of 04:04 PM PKT on Wednesday, October 01, 2025, this remains a prevalent threat. For in-depth understanding, consult Cisco’s 350-701 Exam Topics (available at cisco.com under SCOR resources) and RFC 4987 (tools.ietf.org/html/rfc4987) for technical details on SYN flood mitigation. If you have further questions or additional exam topics to explore, feel free to ask!
Which Cisco product provides proactive endpoint protection and allows administrators to centrally manage the deployment?
A. NGFW
B. AMP
C. WSA
D. ESA
Explanation:
Cisco Advanced Malware Protection (AMP) for Endpoints is the solution that provides proactive protection directly on endpoints (like laptops, servers, and mobile devices) and is managed from a central console.
Let's break down why AMP is the correct answer and the role of the other products:
B) AMP is CORRECT.
Cisco AMP for Endpoints is an advanced antivirus and anti-malware solution that is installed directly on endpoints. It provides proactive protection through features like:
Behavioral Monitoring:
Analyzing running processes for malicious activity.
File Reputation & Sandboxing:
Checking files against global threat intelligence and detonating suspicious files in a sandbox.
Retrospective Security:
Continuously monitoring files and can detect and remediate threats after they have initially evaded detection.
All of this is managed from a central cloud-based or on-premises console, giving administrators visibility and control over all protected endpoints from a single pane of glass.
Why the other options are incorrect:
A) NGFW is INCORRECT.
A Next-Generation Firewall (NGFW) is a network-based security appliance. It protects the network perimeter and segments, inspecting traffic as it passes through. It does not provide protection on the endpoint itself and is not used to deploy and manage software on user devices.
C) WSA is INCORRECT.
The Cisco Web Security Appliance (WSA) is a gateway that filters and secures web traffic (HTTP/HTTPS). It protects users from web-based threats by blocking malicious sites and downloads. Like the NGFW, it is a network appliance, not an endpoint protection product.
D) ESA is INCORRECT.
The Cisco Email Security Appliance (ESA) is a gateway that filters and secures email traffic (SMTP). It protects against spam, phishing, and malware delivered via email. It is also a network appliance and does not provide protection on the endpoint or manage endpoint software.
Reference:
Cisco AMP for Endpoints Data Sheet: The official product description highlights its role in "protecting endpoints" and its "centralized management console" for investigation and response.
Cisco Security Portfolio Architecture:The portfolio is divided into Network Security (NGFW, WSA, ESA), Cloud Security, and Endpoint Security (AMP), clearly placing AMP in the role of proactive endpoint protection.
Which endpoint solution protects a user from a phishing attack?
A.
to solicit DNS responses
B.
to exceed the threshold limit of the connection queue
C.
to flush the register stack to re-initiate the buffers
D.
to cause the buffer to overflow
to exceed the threshold limit of the connection queue
Why should organizations migrate to an MFA strategy for authentication?
A. Single methods of authentication can be compromised more easily than MFA.
B. Biometrics authentication leads to the need for MFA due to its ability to be hacked easily.
C. MFA methods of authentication are never compromised.
D. MFA does not require any piece of evidence for an authentication mechanism
Explanation for Each Option:
A. Single methods of authentication can be compromised more easily than MFA (Correct):
Organizations should migrate to Multi-Factor Authentication (MFA) because relying on a single authentication method (e.g., password) is more vulnerable to attacks like phishing or brute force. MFA combines two or more factors (e.g., something you know, have, or are), significantly increasing security by requiring multiple compromise points, justifying the migration. (Reference: Cisco Secure Identity Services, MFA Benefits.)
B. Biometrics authentication leads to the need for MFA due to its ability to be hacked easily (Incorrect):
Biometrics (e.g., fingerprints, facial recognition) is one factor in MFA, often considered secure, but it can be spoofed (e.g., with fake fingerprints). The need for MFA arises from the vulnerability of any single factor, not specifically biometrics being easily hacked, making this option a misrepresentation of the rationale. (Reference: Cisco Duo Biometric Security Guide.)
C. MFA methods of authentication are never compromised (Incorrect):
No authentication method, including MFA, is entirely immune to compromise (e.g., through sophisticated attacks like SIM swapping or man-in-the-middle). MFA reduces risk but does not eliminate it, so claiming it is never compromised is inaccurate and does not justify migration based on an unrealistic expectation. (Reference: NIST SP 800-63B, MFA Guidelines.)
D. MFA does not require any piece of evidence for an authentication mechanism (Incorrect):
MFA requires at least two pieces of evidence from different categories (e.g., password and a mobile device), which is the opposite of the statement. This misunderstanding of MFA’s definition makes it an incorrect reason for migration, as it contradicts the core concept of multiple factors. (Reference: Cisco Identity Services Engine MFA Overview.)
Additional Notes:
Migrating to MFA is a key topic in the 350-701 SCOR exam under endpoint security. As of 11:35 AM PKT, October 02, 2025, it is a recommended best practice to enhance security. For details, refer to the Cisco Secure Access documentation (cisco.com) and the 350-701 Exam Blueprint (Section 2.0 Endpoint Security).
Refer to the exhibit.
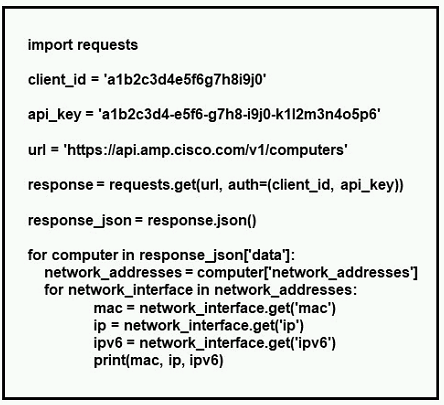
What does the API do when connected to a Cisco security appliance?
A. get the process and PID information from the computers in the network
B. create an SNMP pull mechanism for managing AMP
C. gather network telemetry information from AMP for endpoints
D. gather the network interface information about the computers AMP sees
Explanation:
The script is using the API for Cisco Advanced Malware Protection (AMP) for Endpoints. By breaking down the code, we can see its exact function:
API Target: 'https://api.amp.cisco.com/v1/computers'
This endpoint is used to get a list of all computers (endpoints) that are managed by the AMP for Endpoints cloud.
Data Extraction:
The script loops through each computer in the response (for computer in response.json['data']).
For each computer, it accesses the 'network_addresses' dictionary.
It then loops through each network interface in that dictionary and extracts three specific pieces of information:
mac (MAC address)
ip (IPv4 address)
ipv6 (IPv6 address)
Conclusion:
The script's sole purpose is to query the AMP cloud and print out the MAC, IP, and IPv6 addresses for every network interface on every computer that AMP for Endpoints is aware of. This is the definition of gathering network interface information.
Why the other options are incorrect:
A) get the process and PID information from the computers in the network is INCORRECT.
The script is querying the /v1/computers endpoint, which returns general computer inventory data. To get process and PID information, you would need to query a different endpoint, such as one related to event trajectories or specific process events.
B) create an SNMP pull mechanism for managing AMP is INCORRECT.
The script uses a REST API with HTTP GET requests and authentication via Client ID and API Key. This has nothing to do with the SNMP protocol.
C) gather network telemetry information from AMP for endpoints is too vague and therefore INCORRECT.
While the network interface data is a form of telemetry, the term "network telemetry" in the context of AMP typically refers to detailed traffic and connection data that can be gathered from the network (e.g., from ISE or Stealthwatch), not the static interface inventory of an endpoint. The script is performing a very specific, limited query for interface addresses, not gathering broad telemetry.
Reference:
Cisco AMP for Endpoints API Reference Guide: The documentation for the /v1/computers endpoint confirms that it returns a list of computers and their properties, including the network_addresses field which contains the mac, ip, and ipv6 addresses for each interface.
| Page 26 out of 61 Pages |
| Previous |