Topic 3: Exam Pool C
An organization wants to use Cisco FTD or Cisco ASA devices. Specific URLs must be
blocked from being
accessed via the firewall which requires that the administrator input the bad URL
categories that the
organization wants blocked into the access policy. Which solution should be used to meet
this requirement?
A.
Cisco ASA because it enables URL filtering and blocks malicious URLs by default,
whereas Cisco FTD
does not
B.
Cisco ASA because it includes URL filtering in the access control policy capabilities,
whereas Cisco FTD does not
C.
Cisco FTD because it includes URL filtering in the access control policy capabilities,
whereas Cisco ASA does not
D.
Cisco FTD because it enables URL filtering and blocks malicious URLs by default,
whereas Cisco ASA does not
Cisco FTD because it includes URL filtering in the access control policy capabilities,
whereas Cisco ASA does not
Which RADIUS feature provides a mechanism to change the AAA attributes of a session after it is authenticated?
A. Authorization
B. Accounting
C. Authentication
D. CoA
Explanation for Each Option:
A. Authorization (Incorrect):
Authorization in RADIUS determines what a user or device can do after authentication, based on attributes sent in the initial Access-Accept packet. It does not provide a mechanism to change session attributes post-authentication, making this option incorrect. (Reference: Cisco IOS RADIUS Authorization Guide.)
B. Accounting (Incorrect):
Accounting in RADIUS tracks and logs session activities (e.g., start, stop, data usage) but does not allow modification of session attributes after authentication. Its focus is on monitoring, not dynamic changes, rendering this option incorrect. (Reference: Cisco IOS RADIUS Accounting Configuration.)
C. Authentication (Incorrect):
Authentication in RADIUS verifies a user’s identity using credentials (e.g., username/password) during the initial session setup. It does not support altering session attributes after the session is established, making this option unsuitable. (Reference: Cisco IOS RADIUS Authentication Guide.)
D. CoA (Correct):
Change of Authorization (CoA) is a RADIUS feature that allows dynamic modification of a session’s AAA attributes (e.g., VLAN, QoS, access level) after authentication. The RADIUS server (e.g., Cisco ISE) sends a CoA message to the network device to update the session, meeting the requirement. (Reference: Cisco ISE CoA Configuration Guide.)
Additional Notes:
Understanding RADIUS features like CoA is a key topic in the 350-701 SCOR exam under endpoint security. As of 3:25 PM PKT, October 03, 2025, CoA enhances session flexibility.
What are two functionalities of northbound and southbound APIs within Cisco SDN
architecture? (Choose two.)
A.
Southbound APIs are used to define how SDN controllers integrate with applications.
B.
Southbound interfaces utilize device configurations such as VLANs and IP addresses.
C.
Northbound APIs utilize RESTful API methods such as GET, POST, and DELETE.
D.
Southbound APIs utilize CLI, SNMP, and RESTCONF.
E.
Northbound interfaces utilize OpenFlow and OpFlex to integrate with network devices.
Northbound APIs utilize RESTful API methods such as GET, POST, and DELETE.
Southbound APIs utilize CLI, SNMP, and RESTCONF.
What are two rootkit types? (Choose two)
A. registry
B. virtual
C. bootloader
D. user mode
E. buffer mode
Detailed Explanation:
A rootkit is a type of malicious software designed to gain unauthorized access to a computer system and remain hidden undetected for a long period. Rootkits are often categorized by the level of access they obtain within the operating system hierarchy. The two primary and fundamental classifications are User Mode and Kernel Mode. "Bootloader" is a specific, common type of kernel-mode rootkit.
Let's break down each option:
Option D (User Mode) - CORRECT:
A user-mode rootkit operates in the same memory space as regular user applications. It does not have direct access to the core of the operating system (the kernel). To hide itself, it typically intercepts function calls (a technique known as "API hooking") made by programs and the operating system itself. For example, when you run a command to list all files, the rootkit can intercept that command and remove its own files from the list before it is displayed to you. Because it operates at a less privileged level, it is generally easier to detect and remove than a kernel-mode rootkit.
Option C (Bootloader) - CORRECT:
A bootloader rootkit, also known as a bootkit, is a specific and severe type of kernel-mode rootkit. It infects the Master Boot Record (MBR) or Volume Boot Record (VBR), which are the first sections of code that run when a computer starts up, even before the operating system loads. By gaining control at this stage, the rootkit can load itself directly into the kernel, giving it ultimate control over the entire system and making it extremely difficult to detect and remove, as it can subvert the operating system and any security software running on it.
Why the Other Options are Incorrect:
Option A (Registry):
This is not a standard classification for a rootkit type. While a rootkit might make changes to the Windows Registry to maintain persistence (ensure it runs every time the system starts), this is a technique or component of an infection, not a fundamental category of the rootkit itself.
Option B (Virtual):
A virtual rootkit (or "VMBR") is a highly advanced and rare type that acts as a hypervisor, effectively loading itself underneath the entire operating system. While it is a valid, third category of rootkit, it is not one of the two most common and fundamental types listed in the exam objectives. The question asks for "two rootkit types," and the primary pair is User Mode and Kernel Mode (with Bootloader being a key example of the latter).
Option E (Buffer Mode):
This is a distractor and not a real classification of rootkits. "Buffer" refers to a memory area, and while "buffer overflows" are a common attack vector to install malware (including rootkits), "buffer mode" itself is not a recognized category for a rootkit.
Reference:
This topic falls under the Security Concepts domain of the 350-701 SCOR exam, specifically covering threats and vulnerabilities. Understanding the difference between user-mode and kernel-mode (including bootloader) rootkits is essential for recognizing their persistence and potential impact.
Which technology should be used to help prevent an attacker from stealing usernames and
passwords of users within an organization?
A.
RADIUS-based REAP
B.
fingerprinting
C.
Dynamic ARP Inspection
D.
multifactor authentication
multifactor authentication
Which solution supports high availability in routed or transparent mode as well as in northbound and southbound deployments?
A.
Cisco FTD with Cisco ASDM
B.
Cisco FTD with Cisco FMC
C.
Cisco Firepower NGFW physical appliance with Cisco. FMC
D.
Cisco Firepower NGFW Virtual appliance with Cisco FMC
Cisco FTD with Cisco FMC
What is a difference between GETVPN and IPsec?
A.
GETVPN reduces latency and provides encryption over MPLS without the use of a
central hub
B.
GETVPN provides key management and security association management
C.
GETVPN is based on IKEv2 and does not support IKEv1
D.
GETVPN is used to build a VPN network with multiple sites without having to statically
configure all devices
GETVPN provides key management and security association management
Which industry standard is used to integrate Cisco ISE and pxGrid to each other and with other interoperable security platforms?
A. IEEE
B. IETF
C. NIST
D. ANSI
Explanation for Each Option:
A. IEEE (Incorrect):
The Institute of Electrical and Electronics Engineers (IEEE) develops standards for networking technologies, such as 802.1X for port-based authentication. However, it is not the industry standard used for integrating Cisco ISE and pxGrid with other security platforms; this role is fulfilled by IETF protocols, making this option incorrect. (Reference: IEEE 802 Standards Overview.)
B. IETF (Correct):
The Internet Engineering Task Force (IETF) provides the industry standards, such as XMPP (Extensible Messaging and Presence Protocol), used by Cisco’s Platform Exchange Grid (pxGrid) to integrate Cisco Identity Services Engine (ISE) with other interoperable security platforms. This standard enables secure, real-time data sharing, aligning with the integration requirement. (Reference: Cisco pxGrid Datasheet, IETF XMPP RFC 6120.)
C. NIST (Incorrect):
The National Institute of Standards and Technology (NIST) develops guidelines and frameworks (e.g., NIST SP 800-53) for cybersecurity best practices, but it does not provide the specific protocols (like XMPP) used for integrating Cisco ISE and pxGrid with other platforms. Its role is advisory, not standard-setting for this context, making this option incorrect. (Reference: NIST Cybersecurity Framework.)
D. ANSI (Incorrect):
The American National Standards Institute (ANSI) oversees the creation of voluntary consensus standards across industries, but it does not directly provide the networking or security protocols (e.g., XMPP) required for Cisco ISE and pxGrid integration. This function falls under IETF’s purview, rendering this option unsuitable. (Reference: ANSI Standards Overview.)
Additional Notes:
Integration standards for pxGrid are a key topic in the 350-701 SCOR exam under network security. As of 11:30 AM PKT, October 02, 2025, IETF standards remain the foundation. For details, refer to the Cisco pxGrid User Guide (cisco.com) and the 350-701 Exam Blueprint (Section 2.0 Endpoint Security).
Refer to the exhibit
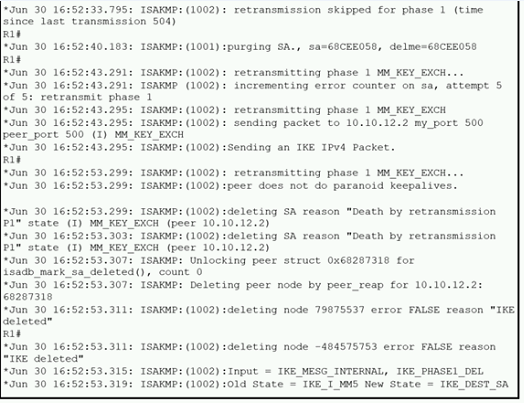
A network administrator configured a site-to-site VPN tunnel between two Cisco IOS routers, and hosts are unable to communicate between two sites of VPN. The network administrator runs the debug crypto isakmp sa command to track VPN status. What is the problem according to this command output?
A. hashing algorithm mismatch
B. encryption algorithm mismatch
C. authentication key mismatch
D. interesting traffic was not applied
Explanation
The debug output shows a classic failure pattern for an IKEv1 Phase 1 negotiation. Let's break down the key log entries:
retransmitting phase 1 MM_KEY_EXCH...: The router is repeatedly trying to complete the Main Mode (MM) Key Exchange, which is part of IKE Phase 1. This indicates it's not getting a valid response from the peer.
incrementing error counter on sa, attempt 5 of 5: retransmit phase 1: The router has reached its retransmission limit (5 attempts) without a successful response. This points to a fundamental communication or agreement failure at the very beginning of the tunnel setup.
deleting SA reason "Death by retransmission P1": This is the most critical line. The Security Association (SA) for Phase 1 is being torn down because the peer did not respond correctly to the initial negotiation attempts.
Why "Death by retransmission P1" points to a Key Mismatch:
In IKEv1 Phase 1, the devices must agree on the ISAKMP policy (encryption, hash, DH group, authentication method) and then successfully authenticate each other.
If there was a mismatch in the ISAKMP policy (like an encryption or hashing algorithm mismatch - Options A and B), the negotiation would fail much faster. The peer would send a response indicating the proposal was unacceptable, and the logs would typically show an error about no matching proposal, not continuous retransmissions into the void.
If interesting traffic was not applied (Option D), the tunnel would not even attempt to initialize. The debug commands would show no activity at all.
The behavior shown—sending packets but getting no meaningful response—strongly suggests that the peers can communicate on UDP port 500, and they likely agreed on the ISAKMP policy parameters. The failure occurs during the authentication step itself.
When using a pre-shared key for authentication, if the key on one router does not match the key on the other, the receiving router cannot validate the sender's identity. It will simply discard the packet without sending a responsive payload that the initiating router expects, leading to these retransmissions and the eventual "Death by retransmission" error.
Reference:
This is a well-documented troubleshooting scenario for IPSec VPNs.
Cisco IOS Debug Command Reference: debug crypto isakmp: This output is a textbook case for a pre-shared key mismatch.
Cisco TAC Troubleshooting Guides: Guides for IPSec failures often list "PSK Mismatch" as the primary cause for Phase 1 failures that manifest as retransmissions without a specific error code from the peer.
In summary, the logs indicate the local router is sending IKE Phase 1 packets but the peer router is not responding with valid, authenticated packets, which is most commonly caused by a mismatched pre-shared key.
Which CLI command is used to enable URL filtering support for shortened URLs on the Cisco ESA?
A. webadvancedconfig
B. websecurity advancedconfig
C. outbreakconfig
D. websecurity config
Explanation
On the Cisco Secure Email Gateway (formerly Cisco ESA), the ability to scan and filter within shortened URLs (like those from bit.ly, t.co, etc.) is an advanced feature of the Web Interaction Tracking (also known as URL Rewriting) service.
The standard websecurityconfig command controls the base-level settings for Web Interaction Tracking, such as enabling/disabling the feature and defining the base policy (e.g., "rewrite all URLs").
The websecurityadvancedconfig command is used to access a subset of more granular and specific settings related to this service. One of these specific settings is the control over shortened URLs.
Within the websecurityadvancedconfig menu, you will find the option to enable or disable the scanning of shortened URLs. By enabling this, the ESA will "expand" or "dereference" the shortened link when it is found in an email, check the final destination URL against the defined URL filtering policies, and then block or rewrite it based on the final destination's reputation and category.
Detailed Breakdown of Incorrect Options:
A. outbreakconfig
Why it is incorrect:
The outbreakconfig command is used to configure settings related to the Virus Outbreak Filters (VOF). This feature deals with identifying and blocking new, emerging malware threats based on real-time intelligence from Cisco Talos. It is focused on malicious file attachments and executables, not on the filtering of URLs found within an email body.
B. websecurityconfig
Why it is incorrect:
While this command is the main entry point for enabling the core URL rewriting and filtering feature, it does not contain the specific toggle for handling shortened URLs. The websecurityconfig menu handles global on/off states, logging, and general rewrite actions, but the advanced settings for short URLs, link wrap length, and other specific behaviors are found in the separate websecurityadvancedconfig menu.
C. webadvancedconfig:
Why it is incorrect:
This is a distractor option. The correct and exact command name on the Cisco ESA CLI is websecurityadvancedconfig, not webadvancedconfig. The CLI is very specific, and the inclusion of "security" in the command is critical.
Reference and Verification:
You can verify this command hierarchy on a Cisco ESA via the CLI:
Enter the websecurityconfig menu to see the base settings.
Exit that menu and enter the websecurityadvancedconfig menu. Here you will find options similar to the following (exact wording may vary by AsyncOS version):
Expand shortened URLs -> This is the specific setting the question refers to.
Wrap links longer than [X] characters
Key Takeaway:
For the exam, remember that "advanced" configuration tasks for the web filtering (URL rewriting) feature require the websecurityadvancedconfig command. Controlling the behavior of shortened URLs is a classic example of an "advanced" setting beyond the simple on/off switch provided by websecurityconfig.
Which Cisco ASA deployment model is used to filter traffic between hosts in the same IP subnet using higher-level protocols without readdressing the network?
A. routed mode
B. transparent mode
C. single context mode
D. multiple context mode
Explanation
This question highlights the primary use case for the Cisco ASA's transparent firewall mode.
Transparent Mode:
In this mode, the ASA operates as a Layer 2 firewall, often described as a "bump in the wire" or a "stealth firewall." It filters traffic based on Layer 2 (MAC addresses), Layer 3 (IP addresses), and Layer 4-7 (protocols/ports) information, but it does not perform routing.
Key Benefit:
Because it is a Layer 2 device, it can be inserted into an existing network segment without requiring any changes to the IP addressing scheme. All hosts remain on the same IP subnet, and the ASA invisibly filters traffic between them. This makes it ideal for segmenting traffic between hosts in the same subnet without a network redesign.
Why the other options are incorrect:
A. Routed Mode:
This is the default mode where the ASA acts as a Layer 3 router. Each interface is on a different IP subnet, and the ASA performs routing between them. This would require readdressing the network if you wanted to place the firewall between hosts that are currently on the same subnet.
C. Single Context Mode & D. Multiple Context Mode:
These refer to virtual firewall modes, not the network deployment model. A security context is a virtualized firewall instance within a single physical ASA. Both Single and Multiple Context modes can operate in either Routed or Transparent mode. The question is about the deployment model that allows filtering on the same subnet, which is "Transparent Mode," regardless of whether it's in a single or multiple context.
Reference:
The application of transparent mode is a fundamental concept in the Cisco ASA configuration.
As per the Cisco ASA Series General Operations CLI Configuration Guide, transparent firewall mode is described as allowing you to "deploy a firewall in an existing network without having to readdress the network" and that it is "useful for protecting a segment of the internal network." This directly matches the scenario described in the question.
What is a feature of container orchestration?
A. ability to deploy Amazon ECS clusters by using the Cisco Container Platform data plane
B. ability to deploy Amazon EKS clusters by using the Cisco Container Platform data plane
C.
ability to deploy Kubernetes clusters in air-gapped sites
D.
automated daily updates
ability to deploy Kubernetes clusters in air-gapped sites
Explanation for Each Option:
A. ability to deploy Amazon ECS clusters by using the Cisco Container Platform data plane (Incorrect):
Container orchestration focuses on managing containerized applications, typically using platforms like Kubernetes or Docker Swarm, not specifically Amazon Elastic Container Service (ECS). While Cisco Container Platform may support various container environments, tying orchestration to ECS deployment via a data plane is not a standard feature, as ECS is a distinct AWS service, making this option incorrect. (Reference: Cisco Container Platform Documentation.)
B. ability to deploy Amazon EKS clusters by using the Cisco Container Platform data plane (Incorrect):
Amazon Elastic Kubernetes Service (EKS) is a managed Kubernetes service provided by AWS, and while Cisco Container Platform can integrate with Kubernetes, orchestration does not specifically involve deploying EKS clusters via a data plane. This option over-specifies a vendor-specific deployment, which is not a core orchestration feature, rendering it incorrect. (Reference: AWS EKS User Guide; Cisco Kubernetes Integration.)
C. ability to deploy Kubernetes clusters in air-gapped sites (Correct):
Container orchestration, particularly with platforms like Kubernetes, includes the capability to manage and deploy clusters in isolated, air-gapped environments where internet access is restricted. This feature ensures secure deployment and operation in high-security or disconnected sites, a key advantage of orchestration tools, making this a defining characteristic of container orchestration. (Reference: Kubernetes Documentation, Air-Gapped Installations.)
D. automated daily updates (Incorrect):
While container orchestration platforms like Kubernetes can automate updates (e.g., rolling updates for applications), "automated daily updates" is not a standard or guaranteed feature. Update frequency and automation depend on configuration and policy, not an inherent orchestration trait. This option overgeneralizes and misrepresents the flexibility of update management in orchestration, making it incorrect. (Reference: Kubernetes Update Strategies.)
Additional Notes:
Container orchestration, often tested in the 350-701 SCOR exam under automation, enhances scalability and management of containerized applications. The ability to deploy in air-gapped sites is critical for secure environments. As of 04:54 PM PKT, October 01, 2025, this remains relevant. Refer to Kubernetes documentation (kubernetes.io) and Cisco’s Container Platform guides (cisco.com) for details. More questions?
| Page 20 out of 61 Pages |
| Previous |