Topic 2: Exam Pool B
An engineer needs behavioral analysis to detect malicious activity on the hosts, and is configuring the organization’s public cloud to send telemetry using the cloud provider’s mechanisms to a security device. Which mechanism should the engineer configure to accomplish this goal?
A. mirror port
B. Flow
C. NetFlow
D. VPC flow logs
Explanation for Each Option:
A. mirror port (Incorrect):
A mirror port (e.g., SPAN or port mirroring) is a network switch feature that copies traffic to a monitoring device. It is not a cloud provider mechanism for sending telemetry from a public cloud environment, making it unsuitable for this scenario. (Reference: Cisco Switch SPAN Configuration Guide.)
B. Flow (Incorrect):
"Flow" is a generic term for network traffic data and is not a specific mechanism provided by cloud providers for telemetry. It lacks the context of a standardized cloud telemetry solution, rendering this option incorrect. (Reference: Cisco NetFlow Overview.)
C. NetFlow (Incorrect):
NetFlow is a Cisco-proprietary protocol for collecting IP traffic information, typically implemented on network devices. While some cloud providers may support NetFlow-like features, it is not a native cloud provider mechanism for sending telemetry from a public cloud, making this option incorrect. (Reference: Cisco NetFlow Configuration Guide.)
D. VPC flow logs (Correct):
VPC flow logs, available from cloud providers like AWS, Azure, and Google Cloud, capture information about IP traffic going to and from network interfaces in a Virtual Private Cloud (VPC). Configuring VPC flow logs sends telemetry to a security device (e.g., Cisco Secure Cloud Analytics) for behavioral analysis of host activity, meeting the goal. (Reference: AWS VPC Flow Logs Documentation, Cisco Secure Cloud Analytics Integration.)
Additional Notes:
Configuring cloud telemetry for behavioral analysis is a key topic in the 350-701 SCOR exam under cloud security. As of 4:15 PM PKT, October 03, 2025, VPC flow logs are a standard mechanism.
What is the role of an endpoint in protecting a user from a phishing attack?
A.
Use Cisco Stealthwatch and Cisco ISE Integration
B.
Utilize 802.1X network security to ensure unauthorized access to resources
C.
Use machine learning models to help identify anomalies and determine expected
sending behavior
D.
Ensure that antivirus and anti malware software is up to date
Ensure that antivirus and anti malware software is up to date
Summary
The question focuses on the role of the endpoint itself (the user's device) in protecting against phishing. Phishing attacks often trick users into clicking malicious links or opening infected attachments. While network and email security solutions are the first line of defense, the endpoint's local software is the last line of defense, responsible for detecting and neutralizing malicious payloads that reach the device.
Correct Option:
D. Ensure that antivirus and anti malware software is up to date:
This is the primary direct role of the endpoint. Modern endpoint protection software (like Cisco Secure Endpoint) includes signatures and behavioral analysis to detect and block known phishing payloads, such as malware downloaded from a phishing link or contained in an attachment. Keeping this software updated ensures it can recognize the latest threats, providing crucial on-device protection.
Incorrect Option:
A. Use Cisco Stealthwatch and Cisco ISE Integration:
This describes a network-based security control. Stealthwatch (network traffic analysis) and ISE (access control) work together to detect compromised endpoints and restrict their network access. This is an important security function, but it is not a role performed by the endpoint itself.
B. Utilize 802.1X network security to ensure unauthorized access to resources:
This is a network access control mechanism. 802.1X authenticates a user/device before granting network access. It helps prevent unauthorized devices from connecting but does not directly protect a user from the content of a phishing email they receive after being authenticated.
C. Use machine learning models to help identify anomalies and determine expected sending behavior:
This describes the function of a cloud-based email security gateway (like Cisco Secure Email). This technology scans emails before they reach the user's endpoint to identify and quarantine phishing attempts. The endpoint itself does not perform this large-scale, sender-behavior analysis.
Reference
Cisco Secure Endpoint Data Sheet: https://www.cisco.com/c/en/us/products/security/advanced-malware-protection/endpoint-data-sheet.html (This outlines how the endpoint software provides protection by blocking malware, which is the final payload of many phishing attacks, fulfilling its role as the last line of defense).
In which form of attack is alternate encoding, such as hexadecimal representation, most
often observed?
A.
Smurf
B.
distributed denial of service
C.
cross-site scripting
D.
rootkit exploit
cross-site scripting
Summary
The question asks about an attack type that commonly uses alternate encoding, like hexadecimal, to evade detection. Attackers use encoding to disguise malicious input, making it appear benign to simple security filters. The goal is to obfuscate the payload so that it passes through initial defenses but is still executed correctly by the target application or system.
Correct Option
C. cross-site scripting:
Cross-site scripting (XSS) attacks frequently use alternate encoding to hide malicious scripts. An attacker will encode a script tag or malicious JavaScript using hexadecimal, Unicode, or Base64 to bypass web application firewalls (WAFs) and input validation filters that scan for specific character patterns like <script>. The web browser, however, will decode and execute the script, successfully carrying out the attack.
Incorrect Option
A. Smurf:
A Smurf attack is a specific type of distributed denial-of-service (DDoS) attack that uses ICMP echo request (ping) packets sent to a network's broadcast address. It relies on IP spoofing and network amplification, not on the obfuscation of payload content through character encoding.
B. distributed denial of service:
While DDoS attacks may use various techniques, they primarily focus on overwhelming a target with a massive volume of traffic or connection requests. The packets themselves are typically valid and do not require content obfuscation through encoding to achieve their goal of consuming bandwidth or resources.
D. rootkit exploit:
A rootkit is a type of malware designed to gain privileged access to a system while hiding its presence. While rootkits may use packing or encryption to evade antivirus detection, the act of exploitation (gaining initial access) does not typically rely on alternate character encoding like hexadecimal within the initial attack vector in the same pervasive way that XSS and SQL injection do.
Reference
Cisco Secure Firewall Management Center Documentation: https://www.cisco.com/c/en/us/td/docs/security/firepower/660/configuration/guide/fpmc-config-guide-v660/Introduction_to_Security_Intelligence.html (Cisco security documentation for web application firewalls and intrusion prevention systems details how they are designed to decode and normalize obfuscated inputs, specifically to defend against encoded attacks like XSS).
A Cisco ESA network administrator has been tasked to use a newly installed service to
help create policy based on the reputation verdict. During testing, it is discovered that the
Cisco ESA is not dropping files that have an undetermined verdict. What is causing this
issue?
A.
The policy was created to send a message to quarantine instead of drop
B.
The file has a reputation score that is above the threshold
C.
The file has a reputation score that is below the threshold
D.
The policy was created to disable file analysis
The policy was created to send a message to quarantine instead of drop
Summary
The issue is that the Cisco Email Security Appliance (ESA) is not dropping files with an "undetermined" verdict from a new reputation service (like File Reputation from AMP). An "undetermined" verdict means the service has no record of the file's reputation. The ESA's behavior in this scenario is controlled by a specific policy setting that dictates what action to take when a definitive verdict (malicious or clean) cannot be reached.
Correct Option
A. The policy was created to send a message to quarantine instead of drop:
This is the most likely cause. The administrator likely created a policy for files with an "Undetermined" verdict but configured the action as "Quarantine" (which holds the email) rather than "Drop" (which deletes it). The ESA is functioning as configured; the issue is a mismatch between the desired outcome (dropping) and the configured policy action (quarantining).
Incorrect Option
B. The file has a reputation score that is above the threshold:
Reputation scores are used for files that have a reputation. A score above the "clean" threshold would result in the file being allowed, not dropped. An "undetermined" file, by definition, does not have a score to evaluate against a threshold.
C. The file has a reputation score that is below the threshold:
Similar to option B, this is inapplicable. An "undetermined" verdict means no reputation data exists, so there is no score to be above or below a configured threshold. The system cannot make a score-based decision.
D. The policy was created to disable file analysis:
If file analysis were disabled, the ESA would not check the file's reputation at all. The question states that a verdict of "undetermined" is being reached, which proves that the file analysis service is active and working; it just doesn't have data on that specific file.
Reference
Cisco Secure Email Gateway User Guide - File Reputation and Analysis Settings: https://www.cisco.com/c/en/us/support/security/email-security-appliance/products-user-guide-list.html (The official configuration guide explains the policy actions for File Reputation, including the separate configurable actions for Malicious, Clean, and Undetermined verdicts, confirming that the action for "Undetermined" must be explicitly set to "Drop").
Which exfiltration method does an attacker use to hide and encode data inside DNS requests and queries?
A. DNS tunneling
B. DNSCrypt
C. DNS security
D. DNSSEC
Explanation:
DNS tunneling is a well-known technique used by attackers to create a covert communication channel for data exfiltration and command-and-control (C2).
A) DNS tunneling is CORRECT.
This method works by encoding stolen data into the subdomains of DNS queries. For example, instead of a normal query for google.com, malware would generate a query for *encoded_data*.attacker-domain.com. The attacker controls the authoritative DNS server for attacker-domain.com, which receives the encoded data. Responses can also be encoded in the DNS reply (e.g., in a TXT record). Because DNS is a fundamental protocol that is rarely blocked, this technique can often bypass traditional security controls.
Why the other options are incorrect:
B) DNSCrypt is INCORRECT.
DNSCrypt is a security protocol designed to encrypt DNS traffic between a client and a resolver to prevent eavesdropping and man-in-the-middle attacks. It is a defensive technology, not an attack method.
C) DNS security is INCORRECT.
This is a general term for a set of practices and technologies (like those listed below) used to protect the DNS infrastructure. It is the opposite of an exfiltration method.
D) DNSSEC is INCORRECT.
DNSSEC (Domain Name System Security Extensions) is a suite of specifications designed to protect the integrity of DNS data by providing origin authentication and data integrity. It is a security control that helps prevent DNS cache poisoning, not a method for exfiltration.
Reference:
SANS Institute & Cybersecurity Advisories: Numerous whitepapers and alerts detail DNS tunneling as a common data exfiltration technique.
A network administrator is configuring a rule in an access control policy to block certain
URLs and selects the “Chat and Instant Messaging” category. Which reputation score
should be selected to accomplish this goal?
A.
1
B.
3
C.
5
D.
10
5
Summary
This question involves configuring URL filtering on a security appliance like Cisco Umbrella or a Cisco Firepower NGFW. The goal is to block all websites within the "Chat and Instant Messaging" category. The reputation score is a numerical value (typically 1-100) representing a site's perceived risk, but for a straightforward category block, the objective is to block the entire category regardless of the individual reputation of sites within it.
Correct Option
C. 5:
In Cisco's URL filtering system, a reputation score of 5 is classified as "Very Poor" or "High Risk." Selecting this score for the "Chat and Instant Messaging" category means the rule will block any site in that category that has a reputation score of 5 or worse (i.e., higher numerically). Since the administrator's goal is to block the entire category, they would select the highest/worst reputation score available (in this list, 5) to ensure all sites in the category, regardless of their individual standing, are blocked. A site in this category with a "good" reputation (e.g., score of 1) would still be blocked by this rule.
Incorrect Option
A. 1:
A reputation score of 1 represents the "Excellent" or "Trustworthy" category. Configuring a block for sites with a score of 1 or worse would block nearly all internet traffic, including legitimate business sites, which is not the goal. It would not specifically target the "Chat and Instant Messaging" category effectively.
B. 3:
A reputation score of 3 is typically "Medium" or "Suspicious." Selecting this would block sites in the category with a score of 3, 4, and 5, but it would allow sites within the "Chat and Instant Messaging" category that have a "Good" reputation (score of 1 or 2). The requirement is to block the category, not just the risky sites within it.
D. 10:
This is a distractor. The standard reputation scale for these systems is 1 (best) to 5 (worst). A score of 10 is not part of the standard reputation scoring system used in this context.
Reference
Cisco Umbrella Documentation: Understand Reputation Scores: https://docs.umbrella.com/deployment-umbrella/docs/security-levels-and-reputation-scores (This official documentation explains the reputation score scale of 1 to 5 and how policies block content based on a "block scores of X and above" logic, confirming that selecting the highest score (5) blocks all sites in a category).
What provides the ability to program and monitor networks from somewhere other than the DNAC GUI?
A. NetFlow
B. desktop client
C. ASDM
D. API
Explanation for Each Option:
A. NetFlow (Incorrect):
NetFlow is a network protocol used for collecting and monitoring traffic data to analyze usage and detect anomalies. While it provides visibility into network activity, it is not designed for programming or managing networks remotely, nor does it integrate with Cisco DNA Center (DNAC) for GUI-independent control, making this option incorrect. (Reference: Cisco NetFlow Configuration Guide.)
B. desktop client (Incorrect):
A desktop client typically refers to a local application (e.g., a management tool installed on a workstation) for network configuration or monitoring. However, it does not inherently provide remote programming or monitoring capabilities outside the DNAC GUI without specific integration, and it is less flexible than API-based solutions, rendering this option unsuitable. (Reference: Cisco Network Management Tools.)
C. ASDM (Incorrect):
Adaptive Security Device Manager (ASDM) is a graphical interface for managing Cisco ASA devices. It is a GUI-based tool that requires local or remote access to the device, not a method for programming or monitoring networks outside the DNAC GUI. It lacks the programmatic flexibility needed, making this option incorrect. (Reference: Cisco ASDM User Guide.)
D. API (Correct):
The Cisco DNA Center (DNAC) API provides a programmatic interface to automate, program, and monitor network operations remotely, independent of the DNAC GUI. Using RESTful APIs, administrators can integrate DNAC with external tools or scripts, enabling management from any location with network access, fulfilling the requirement effectively. (Reference: Cisco DNA Center API Documentation.)
Additional Notes:
API usage with DNAC is a key topic in the 350-701 SCOR exam under automation. As of 09:24 AM PKT, October 02, 2025, this capability enhances network programmability. For details, refer to the Cisco DNA Center API Guide (developer.cisco.com) and the 350-701 Exam Blueprint (Section 4.0 Automation).
Which two capabilities does TAXII support? (Choose two)
A.
Exchange
B.
Pull messaging
C.
Binding
D.
Correlation
E.
Mitigating
Exchange
Pull messaging
Summary
TAXII (Trusted Automated eXchange of Indicator Information) is an open protocol application layer standard used for the automated exchange of cyber threat intelligence (CTI) between organizations and systems. It defines how CTI information can be shared via a set of services and message exchanges. It is not an analysis or detection protocol, but a transport mechanism.
Correct Option
A. Exchange:
This is a core capability. TAXII defines specific services for sharing information. The two primary service modes are Collection (a repository from which subscribers can pull data) and Channel (a service for pushing data to subscribers). Both of these are forms of "Exchange."
B. Pull messaging:
This is a fundamental communication style supported by TAXII. In a Collection-based exchange, a TAXII Client can connect to a TAXII Server and "pull" or request threat intelligence data at defined intervals. This is a key method for clients to obtain the latest indicators from a threat intelligence feed.
Incorrect Option
C. Binding:
This is not a capability defined by the TAXII standard. TAXII specifications focus on the data models and service definitions for exchange, not on low-level network bindings.
D. Correlation:
Correlation is the function of a Security Information and Event Management (SIEM) system or an analytics engine. TAXII is solely a transport protocol for moving already-processed intelligence; it does not perform analysis or correlation of data.
E. Mitigating:
Mitigation refers to the actions taken to block or contain a threat (e.g., updating a firewall policy). TAXII is responsible for the delivery of the intelligence that might trigger a mitigation action in another system, but it does not perform the mitigation itself.
Reference
OASIS CTI TC Documentation - TAXII Specification: https://www.oasis-open.org/committees/tc_home.php?wg_abbrev=cti (The official TAXII specification from OASIS defines the concepts of "Services," "Collections," and "Poll" (pull) requests, which directly correspond to the capabilities of Exchange and Pull Messaging).
What features does Cisco FTDv provide over ASAv?
A. Cisco FTDv runs on VMWare while ASAv does not
B. Cisco FTDv provides 1GB of firewall throughput while Cisco ASAv does not
C. Cisco FTDv runs on AWS while ASAv does not
D. Cisco FTDv supports URL filtering while ASAv does not
Explanation
This question highlights the fundamental difference between the two virtual firewall offerings from Cisco: the legacy ASA-based platform and the modern Firepower Threat Defense platform.
Cisco ASAv (Adaptive Security Virtual Appliance):
This is the virtual version of the classic Cisco ASA firewall. Its primary features are stateful firewall inspection, VPN (Site-to-Site and Remote Access), and basic networking services. It operates primarily at the network and transport layers (L3-L4). It does not have integrated, advanced threat-focused capabilities like URL Filtering, IPS, or Advanced Malware Protection (AMP) within its own image.
Cisco FTDv (Firepower Threat Defense virtual):
This is the virtual version of the modern Cisco Firepower Threat Defense software. It is a consolidated, next-generation firewall (NGFW) platform that integrates several security functions into a single image. Crucially, this includes:
Detailed Breakdown of Incorrect Options
A. Cisco FTDv runs on VMWare while ASAv does not
Why it is incorrect:
This is false. Both the Cisco ASAv and the Cisco FTDv are supported on multiple hypervisors, including VMware ESXi, Microsoft Hyper-V, KVM, and various public clouds like AWS, Azure, and Google Cloud. The virtualization platform is not a differentiating factor.
B. Cisco FTDv provides 1GB of firewall throughput while Cisco ASAv does not
Why it is incorrect:
This is misleading and incorrect. Throughput is determined by the licensed "instance size" or "throughput tier" for both virtual appliances. Both the ASAv and FTDv come in multiple performance tiers (e.g., 100Mbps, 1Gbps, 10Gbps). You can license an ASAv for 1Gbps of stateful firewall throughput, and you can license an FTDv for the same. The performance is a function of the license and the underlying host resources, not an inherent limitation of one platform over the other in this context.
C. Cisco FTDv runs on AWS while ASAv does not
Why it is incorrect:
This is false. Both the Cisco ASAv and the Cisco FTDv are officially supported and available as Amazon Machine Images (AMIs) in the AWS Marketplace. They are both designed for deployment in public cloud environments.
Reference:
This information is clearly outlined in the data sheets and feature guides for both the Cisco ASAv and Cisco FTDv on Cisco's official website.
Exam Tip:
When comparing ASAv vs. FTDv, always think "Traditional Stateful Firewall" vs. "Consolidated Next-Generation Firewall." The presence of application-layer controls like URL Filtering, IPS, and AMP is the definitive differentiator that FTDv provides.
The Cisco ASA must support TLS proxy for encrypted Cisco Unified Communications
traffic. Where must the
ASA be added on the Cisco UC Manager platform?
A.
Certificate Trust List
B.
Endpoint Trust List
C.
Enterprise Proxy Service
D.
Secured Collaboration Proxy
Certificate Trust List
Refer to the exhibit.
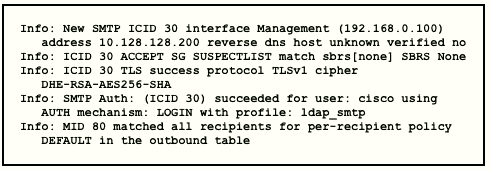
Which type of authentication is in use?
A.
LDAP authentication for Microsoft Outlook
B.
POP3 authentication
C.
SMTP relay server authentication
D.
external user and relay mail authentication
external user and relay mail authentication
Reference: https://www.cisco.com/c/en/us/support/docs/security/email-securityappliance/
118844-technoteesa-00.htmlThe exhibit in this Qshows a successful TLS
connection from the remote host (reception) in the mail log.
A Cisco ESA administrator has been tasked with configuring the Cisco ESA to ensure there are no viruses before quarantined emails are delivered. In addition, delivery of mail from known bad mail servers must be prevented. Which two actions must be taken in order to meet these requirements? (Choose two)
A. Use outbreak filters from SenderBase
B. Enable a message tracking service
C. Configure a recipient access table
D. Deploy the Cisco ESA in the DMZ
E. Scan quarantined emails using AntiVirus signatures
Explanation
Let's break down the requirements from the question and map them to the correct ESA features.
Requirement 1:
"Ensure there are no viruses before quarantined emails are delivered."
By default, the ESA scans messages for viruses as they arrive using the Anti-Virus scanning engines (like Sophos or McAfee). Messages that are clean are delivered; messages with viruses are typically dropped or quarantined.
However, the requirement specifies ensuring no viruses "before quarantined emails are delivered." This implies a scenario where messages are placed in a quarantine queue for other reasons (e.g., policy quarantines, suspected spam) and must be re-scanned before a user or administrator releases them.
How is this achieved?
Answer E:
Scan quarantined emails using AntiVirus signatures. The ESA has a specific feature called "Virus Outbreak Filter" or "Retrospective Anti-Virus" (depending on the version). This feature can be configured to periodically re-scan messages that are already in the quarantine. If a new virus signature is downloaded after a message was quarantined, this scan will detect the now-identified virus and take action (like deleting the message), ensuring it is never delivered to the user's inbox, even if released from quarantine.
Requirement 2:
"Delivery of mail from known bad mail servers must be prevented."
This is a classic case for reputation-based filtering. The ESA needs to make a decision about an incoming connection before it accepts the entire email message. This is efficient and prevents wasted resources.
How is this achieved?
Answer A:
Use outbreak filters from SenderBase. SenderBase (Cisco's security intelligence network) maintains a massive, real-time database of IP addresses and their reputation scores. "Outbreak Filters" use this data. When an email server connects to the ESA, the ESA can immediately query SenderBase. If the connecting IP is on a known bad list (e.g., a known source of spam, malware, or part of a botnet), the ESA can block the connection outright, preventing the message from ever being delivered.
Detailed Breakdown of Incorrect Options
B. Enable a message tracking service
Why it is incorrect:
Message tracking is a reporting and troubleshooting feature. It allows an administrator to search for a specific message and see its path through the ESA (accepted, scanned, quarantined, delivered, etc.). It is a reactive tool used for diagnosis and has no proactive role in blocking viruses or bad senders.
C. Configure a recipient access table
Why it is incorrect:
A Recipient Access Table (RAT) is used to control inbound routing and acceptance based on the recipient's email address. It answers the question, "Is this recipient valid and which mail policy should apply?" It does not scan for virus content or make decisions based on the reputation of the sending server's IP address.
D. Deploy the Cisco ESA in the DMZ
Why it is incorrect:
While it is a common and recommended network design to place the ESA in a DMZ, this is a deployment topology, not a specific configuration action to meet the functional requirements. An ESA placed anywhere on the network edge can be configured with Anti-Virus and SenderBase filters. The physical or logical location does not, by itself, fulfill the tasks of virus scanning and sender reputation blocking.
Summary and Reference
To block known bad servers:
You use SenderBase/IP Reputation filtering (A). This is a first-line defense that stops threats before they enter your system.
To ensure quarantined messages are virus-free before release: You enable retrospective Anti-Virus scanning on the quarantine (E). This is a safety net that catches new threats that were unknown at the time of initial delivery.
Reference:
These features are core components of the Cisco ESA and are documented in the "Anti-Spam and Antivirus" and "Reputation Filtering and Outbreak Filters" sections of the Cisco Email Security Appliance Administration Guide.
| Page 2 out of 61 Pages |
| Previous |