Topic 1: Exam Pool A
Refer to the exhibit.
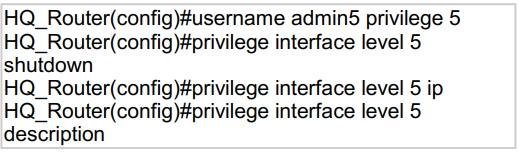
A network administrator configures command authorization for the admin5 user. What is
the admin5 user able to do on HQ_Router after this configuration?
A.
set the IP address of an interface
B.
complete no configurations
C.
complete all configurations
D.
add subinterfaces
complete no configurations
The user “admin5” was configured with privilege level 5. In order
to allow configuration (enter globalconfiguration mode), we must type this
command:(config)#privilege exec level 5 configure terminalWithout this command, this user
cannot do any configuration.Note: Cisco IOS supports privilege levels from 0 to 15, but the
privilege levels which are used by default are privilege level 1 (user EXEC) and level
privilege 15 (privilege EXEC)
Which statement about the configuration of Cisco ASA NetFlow v9 Secure Event Logging is true?
A. To view bandwidth usage for NetFlow records, the QoS feature must be enabled.
B. A sysopt command can be used to enable NSEL on a specific interface.
C. NSEL can be used without a collector configured.
D. A flow-export event type must be defined under a policy.
Explanation
Cisco ASA NetFlow Secure Event Logging (NSEL) is a stateful, high-performance logging mechanism that uses NetFlow v9 to export security events. Its configuration is policy-based.
The core of NSEL configuration involves creating a class-map to identify the traffic you want to monitor and then applying a policy-map that specifies which NetFlow events (e.g., flow create, flow deny, flow teardown) should be exported for that traffic class. Finally, this policy is applied to an interface with a service-policy command.
Therefore, the statement "A flow-export event type must be defined under a policy" is accurate, as the event types (like flow-create, flow-denied) are configured within the class-map and policy-map structure.
Why the other options are incorrect:
A. To view bandwidth usage for NetFlow records, the QoS feature must be enabled.
This is incorrect. NSEL exports event-based data (session starts, stops, denies), not continuous traffic flow data for bandwidth monitoring. Enabling QoS is not a requirement for NSEL to function.
B. A sysopt command can be used to enable NSEL on a specific interface.
This is incorrect. The sysopt command is used for other ASA behaviors (like allowing VPN traffic to bypass access lists). NSEL is enabled and applied to interfaces using the flow-export and service-policy commands, not a sysopt command.
C. NSEL can be used without a collector configured.
This is incorrect. The entire purpose of NSEL is to export flow event records to an external collector. If no collector is configured with the flow-export destination command, the ASA has nowhere to send the NSEL data, rendering the feature non-functional.
Reference:
The configuration steps for NSEL are outlined in the Cisco ASA configuration guide.
As per the Cisco ASA Series CLI Configuration Guide, the steps to configure NSEL include:
(Optional) Create a class-map to identify traffic.
Create a policy-map to define the action and event types.
Within the policy-map, specify the flow-export event-type for the traffic class.
Apply the policy-map globally or to an interface.
This confirms that the flow-export event type is indeed defined within a policy structure.
Which technology must be used to implement secure VPN connectivity among company branches over a private IP cloud with any-to-any scalable connectivity?
A. DMVPN
B. FlexVPN
C. IPsec DVTI
D. GET VPN
Explanation for Each Option:
A. DMVPN (Incorrect):
Dynamic Multipoint VPN (DMVPN) uses a hub-and-spoke or partial mesh topology with IPsec to provide scalable VPN connectivity over public or private networks. While it supports any-to-any connectivity with spoke-to-spoke tunnels, it relies on a hub for initial routing and is less optimized for a private IP cloud requiring full mesh scalability without centralized control, making it less suitable. (Reference: Cisco DMVPN Configuration Guide.)
B. FlexVPN (Incorrect):
FlexVPN is a flexible, standards-based IPsec VPN solution that supports various topologies, including hub-and-spoke and full mesh, using IKEv2. However, it is designed for general-purpose VPNs and does not inherently optimize for a private IP cloud with any-to-any connectivity, requiring additional configuration for scalability, rendering it less ideal than a dedicated solution. (Reference: Cisco FlexVPN Deployment Guide.)
C. IPsec DVTI (Incorrect):
IPsec Dynamic Virtual Tunnel Interface (DVTI) provides a per-tunnel interface for IPsec VPNs, offering flexibility for point-to-point or hub-and-spoke designs. It is not optimized for any-to-any scalable connectivity in a private IP cloud, as it lacks the group-based encryption and mesh capabilities needed for efficient branch interconnectivity, making this option incorrect. (Reference: Cisco IPsec DVTI Overview.)
D. GET VPN (Correct):
Group Encrypted Transport VPN (GET VPN) is designed for secure VPN connectivity over a private IP cloud, using group-based encryption to enable any-to-any scalable connectivity among branch sites. It eliminates the need for point-to-point tunnels by leveraging a group key management system, making it ideal for large-scale, mesh-like networks with consistent security policies. (Reference: Cisco GET VPN Configuration Guide.)
Additional Notes:
Implementing GET VPN for branch connectivity is a key topic in the 350-701 SCOR exam under VPN technologies. As of 11:35 AM PKT, October 03, 2025, it excels in private IP cloud deployments.
Which functions of an SDN architecture require southbound APIs to enable communication?
A. SDN controller and the network elements
B. management console and the SDN controller
C. management console and the cloud
D. SDN controller and the cloud
Explanation:
In an SDN architecture, APIs are categorized based on the direction of communication relative to the central SDN controller.
A) SDN controller and the network elements is CORRECT.
The southbound API is the interface that the SDN controller uses to communicate down to the underlying network elements (switches, routers, access points). This API is used to push configuration, routing decisions, and policies to the devices. Examples of southbound APIs include OpenFlow, OpFlex, and NETCONF/YANG. This is the definitive role of the southbound API.
Why the other options are incorrect:
B) management console and the SDN controller is INCORRECT.
This communication path uses the northbound API. The northbound API is how applications and management tools (the "brains" or business logic) talk up to the SDN controller to request network services or pull network state information.
C) management console and the cloud and D) SDN controller and the cloud are INCORRECT.
These are general cloud management or east-west communications and are not specifically defined as "southbound" in the standard SDN model. Communication with the cloud would typically use standard REST APIs or other cloud interfaces, not the southbound API meant for controlling physical/virtual network devices.
SDN API Summary:
Southbound API: Controller → Network Devices (e.g., OpenFlow)
Northbound API: Applications/Management → Controller (e.g., REST API)
East-West API: Communication between multiple controllers (for scalability/redundancy).
Reference:
Cisco Digital Network Architecture (DNA) Center Concepts Guide: Explains the controller's role and how it uses southbound interfaces like NETCONF/YANG and CLI to communicate with network devices.
Open Networking Foundation (ONF) SDN Architecture: The foundational document that defines the SDN layers and the roles of northbound and southbound APIs.
Which VPN technology can support a multivendor environment and secure traffic between sites?
A. SSL VPN
B. GET VPN
C. FlexVPN
D. DMVPN
Explanation for Each Option:
A. SSL VPN (Incorrect):
Secure Sockets Layer (SSL) VPN provides remote access using web browsers or client software, typically for individual users. While it can secure traffic, it is not designed for site-to-site connectivity or multivendor environments, as it relies on proprietary client implementations and lacks broad interoperability with diverse network devices, making it unsuitable for this scenario. (Reference: Cisco SSL VPN Configuration Guide.)
B. GET VPN (Incorrect):
Group Encrypted Transport VPN (GET VPN) is a Cisco-proprietary solution that uses Group Domain of Interpretation (GDOI) for secure multicast and site-to-site communication. However, its reliance on Cisco-specific protocols and devices limits its ability to support a multivendor environment, where interoperability with non-Cisco equipment is required, rendering this option incorrect. (Reference: Cisco GET VPN Deployment Guide.)
C. FlexVPN (Correct):
FlexVPN is a versatile, standards-based VPN solution using IKEv2 (Internet Key Exchange version 2), built on IETF standards. It supports multivendor environments by enabling secure site-to-site traffic between diverse devices (Cisco and non-Cisco) through flexible configuration and interoperability. Its adaptability makes it ideal for securing traffic across heterogeneous networks. (Reference: Cisco FlexVPN Configuration Guide.)
D. DMVPN (Incorrect):
Dynamic Multipoint VPN (DMVPN) is a Cisco-developed solution that uses NHRP (Next Hop Resolution Protocol) and IPsec for dynamic site-to-site VPNs. While effective for Cisco environments, its reliance on Cisco-specific features (e.g., NHRP) limits multivendor support, as non-Cisco devices may not fully integrate, making it less suitable for this requirement. (Reference: Cisco DMVPN Design Guide.)
Additional Notes:
FlexVPN’s multivendor support is a key topic in the 350-701 SCOR exam under VPN technologies. As of 09:35 AM PKT, October 02, 2025, it remains a robust choice for heterogeneous environments. For details, refer to the Cisco FlexVPN Configuration Guide (cisco.com) and the 350-701 Exam Blueprint (Section 3.0 Security Concepts).
An engineer needs a solution for TACACS+ authentication and authorization for device administration.
The engineer also wants to enhance wired and wireless network security by requiring users and endpoints to use 802.1X, MAB, or WebAuth. Which product meets all of these requirements?
A.
Cisco Prime Infrastructure
B.
Cisco Identity Services Engine
C.
Cisco Stealthwatch
D.
Cisco AMP for Endpoints
Cisco Identity Services Engine
Which two endpoint measures are used to minimize the chances of falling victim to phishing and social engineering attacks? (Choose two)
A. Patch for cross-site scripting.
B. Perform backups to the private cloud.
C. Protect against input validation and character escapes in the endpoint.
D. Install a spam and virus email filter.
E. Protect systems with an up-to-date antimalware program
Explanation
The question focuses on endpoint measures to minimize the chances of falling victim to phishing and social engineering. This means we are looking for controls that are implemented on or directly protect the end-user device (laptop, desktop).
D. Install a spam and virus email filter:
This is a primary defense against phishing. A robust email security gateway (like Cisco Secure Email) acts as the first line of defense by filtering incoming emails. It blocks spam, identifies and quarantines phishing emails based on known signatures, heuristics, and reputation, and scans attachments for viruses before they even reach the user's inbox. This directly reduces the user's exposure to the attack vector.
E. Protect systems with an up-to-date antimalware program:
This is a crucial last line of defense on the endpoint itself. If a user is tricked by a social engineering attack and clicks a malicious link or opens a infected attachment, the antimalware (or next-generation antivirus) software is designed to detect, block, and quarantine the malicious payload (e.g., ransomware, trojan, keylogger) from executing. Keeping it updated ensures it has the latest signatures and behavioral models to recognize new threats.
Detailed Breakdown of Incorrect Options
A. Patch for cross-site scripting.
Why it is incorrect:
Cross-site scripting (XSS) is a vulnerability found in web applications, not on endpoints. Patching for XSS is the responsibility of web developers and server administrators. While an XSS vulnerability on a trusted website could be used in a social engineering attack, the act of patching it is not an endpoint measure. It is a server-side or application-level security control.
B. Perform backups to the private cloud.
Why it is incorrect:
Performing regular backups is an excellent disaster recovery and business continuity practice. It helps you recover after a successful attack (like ransomware deployed via phishing). However, it does nothing to minimize the chances of falling victim to the attack in the first place. It is a reactive measure, not a preventive one.
C. Protect against input validation and character escapes in the endpoint.
Why it is incorrect:
Similar to option A, this describes a defense against application-level vulnerabilities like SQL Injection and XSS. Input validation is a coding practice performed by software developers to secure their applications. It is not a security control that is implemented on a standard user endpoint like a laptop. The endpoint is the client making requests, not the server validating them.
Summary and Reference:
To protect endpoints from phishing and social engineering, a defense-in-depth strategy is used:
At the Network/Email Perimeter (Option D): Use secure email gateways to filter out malicious emails.
On the Endpoint Itself (Option E): Use modern antimalware/endpoint protection platforms (like Cisco Secure Endpoint) to stop threats that bypass the perimeter controls.
User Training: While not listed in the options, security awareness training is the third critical pillar, teaching users how to identify and report suspicious emails.
Reference:
Best practices from organizations like CISA (Cybersecurity and Infrastructure Security Agency) and the SANS Institute consistently recommend email filtering and antivirus/antimalware solutions as foundational technical controls for mitigating the risk of phishing.
On which part of the IT environment does DevSecOps focus?
A.
application development
B.
wireless network
C.
data center
D.
perimeter network
application development
What is a required prerequisite to enable malware file scanning for the Secure Internet Gateway?
A. Enable IP Layer enforcement
B. Activate the Advanced Malware Protection license
C. Activate SSL decryption.
D. Enable Intelligent Proxy.
Explanation:
Cisco Secure Internet Gateway (SIG) uses a proxy-based architecture to perform deep inspection of traffic. The "Intelligent Proxy" is the core component that enables this.
Let's break down the process and why the other options are not the direct prerequisite:
D) Enable Intelligent Proxy is CORRECT.
To scan the contents of a file for malware, the SIG must be able to intercept and inspect the file as it is being downloaded. The Intelligent Proxy is the feature that performs this function. It acts as an explicit, forward proxy for web traffic, allowing it to:
Cache and Buffer Files:
It can hold the entire file as it is being downloaded.
Perform Deep Inspection:
Once the file is fully buffered, it can be scanned by the Advanced Malware protection (AMP) engine.
Block or Allow:
Based on the scan result, the proxy can block the download or allow it to proceed to the user.
Without the Intelligent Proxy enabled, the SIG would be limited to URL filtering and basic security intelligence (blocking based on reputation), but it could not perform actual file content scanning for malware.
Why the other options are incorrect:
A) Enable IP Layer enforcement is INCORRECT.
IP Layer enforcement is a method for routing traffic to the SIG cloud. It is an alternative to the proxy-based method (Tunnel/Explicit Proxy). While it can be used, it is not a prerequisite for malware scanning. The prerequisite is the scanning mechanism itself (the proxy), not the routing method used to get the traffic to the cloud.
B) Activate the Advanced Malware Protection license is INCORRECT, but it is a tricky distractor.
While you absolutely need an AMP license to use the malware scanning feature, the license alone does not enable the scanning. The functional prerequisite is enabling the Intelligent Proxy, which is the component that performs the scan. The license grants you the right to use it.
C) Activate SSL decryption is INCORRECT.
SSL decryption is highly recommended for effective security, as most modern malware is delivered over encrypted HTTPS connections. However, it is not a strict prerequisite for malware file scanning. The Intelligent Proxy can still scan files downloaded over unencrypted HTTP connections without SSL decryption. For HTTPS, you need both the Intelligent Proxy and SSL decryption to be effective.
Reference:
Cisco Secure Internet Gateway (SIG) Administration Guide:
The documentation on configuring malware scanning explicitly states that the "Intelligent Proxy must be enabled" for file scanning features like AMP and File Reputation to function. It describes the proxy as the engine that buffers and inspects files.
Cisco SIG Design Guide:
These guides explain the architecture, showing that web traffic must pass through the Intelligent Proxy for full content inspection, including malware analysis.
Which benefit does DMVPN provide over GETVPN?
A.
DMVPN supports QoS, multicast, and routing, and GETVPN supports only QoS.
B.
DMVPN is a tunnel-less VPN, and GETVPN is tunnel-based.
C.
DMVPN supports non-IP protocols, and GETVPN supports only IP protocols
D.
DMVPN can be used over the public Internet, and GETVPN requires a private network
DMVPN can be used over the public Internet, and GETVPN requires a private network
Refer to the exhibit.
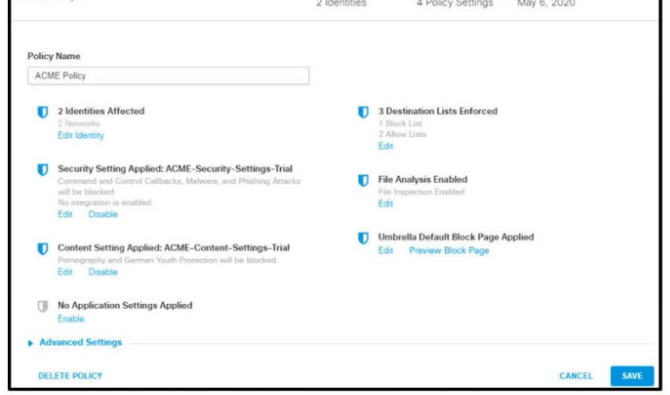
How does Cisco Umbrella manage traffic that is directed toward risky domains?
A.
Traffic is proximed through the intelligent proxy.
B.
Traffic is managed by the security settings and blocked
C.
Traffic is managed by the application settings, unhandled and allowed
D.
Traffic is allowed but logged.
Traffic is managed by the security settings and blocked
Explanation:
The key to this question is understanding the distinction between different blocking and inspection methods within Cisco Umbrella. The configuration shows that specific security settings are enabled.
Let's analyze the provided configuration:
The policy applies "ACME-Security-Settings-Trial", which includes protection against "Malware, and Phishing Attacks".
Crucially, it also shows that "File Analysis Enabled" is active.
Here's why A is the correct answer:
A) Traffic is proxied through the intelligent proxy is CORRECT.
For Umbrella to perform File Analysis, it must do more than just block a domain at the DNS level. When a request is made to a domain categorized as risky (but not definitively malicious enough for a simple DNS block), Umbrella's Intelligent Proxy is triggered. This service:
Intercepts the HTTP/HTTPS connection to the risky domain.
Can buffer and inspect the files being downloaded in real-time.
Uses advanced sandboxing and analysis to determine if the file is malicious.
Will only block the transfer if the file is confirmed to be malicious.
This provides a much higher level of security than a simple block page, as it allows for the inspection of potentially unknown threats.
Why the other options are incorrect:
B) Traffic is managed by the security settings and blocked.
This is partially true but incomplete. Umbrella does use security settings to block traffic at the DNS layer for known-bad domains. However, for "risky" domains that require file analysis, a simple block is not the action taken; instead, the traffic is proxied for deeper inspection. The presence of "File Analysis Enabled" indicates the more advanced proxying action.
C) Traffic is managed by the application settings, unhandled and allowed.
This is INCORRECT. The policy clearly has security settings applied to handle this traffic. "Unhandled and allowed" would be the default behavior if no policy matched, which is not the case here.
D) Traffic is allowed but logged.
This is INCORRECT. While logging occurs, the primary action for risky domains with file analysis enabled is not simple "allowance." It is active inspection via the proxy, which may still result in the content being blocked if it's found to be malicious.
Reference:
Cisco Umbrella Administration Guide, "File Inspection": The official documentation explains that when file inspection is enabled, "Umbrella uses a proxy to inspect files for threats as they are being downloaded."
Cisco Umbrella Data Sheet, "Intelligent Proxy": This feature is described as providing "full transaction inspection for risky requests" that goes beyond DNS-layer security.
Which two application layer preprocessors are used by Firepower Next Generation Intrusion Prevention System? (Choose two)
A. packet decoder
B. SIP
C. modbus
D. inline normalization
E. SSL
Explanation for Each Option:
A. packet decoder (Incorrect):
The packet decoder is a lower-layer preprocessor in the Firepower Next Generation Intrusion Prevention System (NGIPS), responsible for parsing raw packets into a structured format. It operates below the application layer, making it unsuitable as an application layer preprocessor. (Reference: Cisco Firepower Preprocessor Overview.)
B. SIP (Correct):
The Session Initiation Protocol (SIP) preprocessor in Firepower NGIPS operates at the application layer, analyzing SIP traffic (e.g., VoIP calls) to detect anomalies or attacks. It normalizes and inspects SIP messages, qualifying it as an application layer preprocessor. (Reference: Cisco Firepower SIP Preprocessor Guide.)
C. modbus (Incorrect):
The Modbus preprocessor in Firepower NGIPS handles industrial control system protocols at the application layer but is not a standard or commonly emphasized application layer preprocessor in the context of NGIPS. It is more specific to ICS environments, making it less relevant here. (Reference: Cisco Firepower ICS Preprocessors.)
D. inline normalization (Incorrect):
Inline normalization is a preprocessing function that standardizes packet data (e.g., TCP/IP headers) to ensure consistent analysis, operating at the network or transport layer, not the application layer. It is not an application-specific preprocessor, rendering this option incorrect. (Reference: Cisco Firepower Normalization Guide.)
E. SSL (Correct):
The SSL preprocessor in Firepower NGIPS operates at the application layer, inspecting and decrypting SSL/TLS traffic to detect encrypted threats. It analyzes application-layer data within SSL sessions, making it a valid application layer preprocessor. (Reference: Cisco Firepower SSL Inspection Guide.)
Additional Notes:
Understanding NGIPS preprocessors is a key topic in the 350-701 SCOR exam under network security. As of 3:21 PM PKT, October 03, 2025, SIP and SSL are critical for application-layer analysis.
| Page 19 out of 61 Pages |
| Previous |